Spot hidden anomalies, trace an attacker's path across devices, and identify attack patterns within seconds.
When it comes to detecting security threats, event logs play a crucial role as they hold important security information. Log360's event correlation module correlates disparate security events and identifies threat patterns across your network. Log360 strings isolated security events together to identify indicators of an attack. With quick, accurate alerts, you can take a proactive stance to prevent damage to your network data and resources.
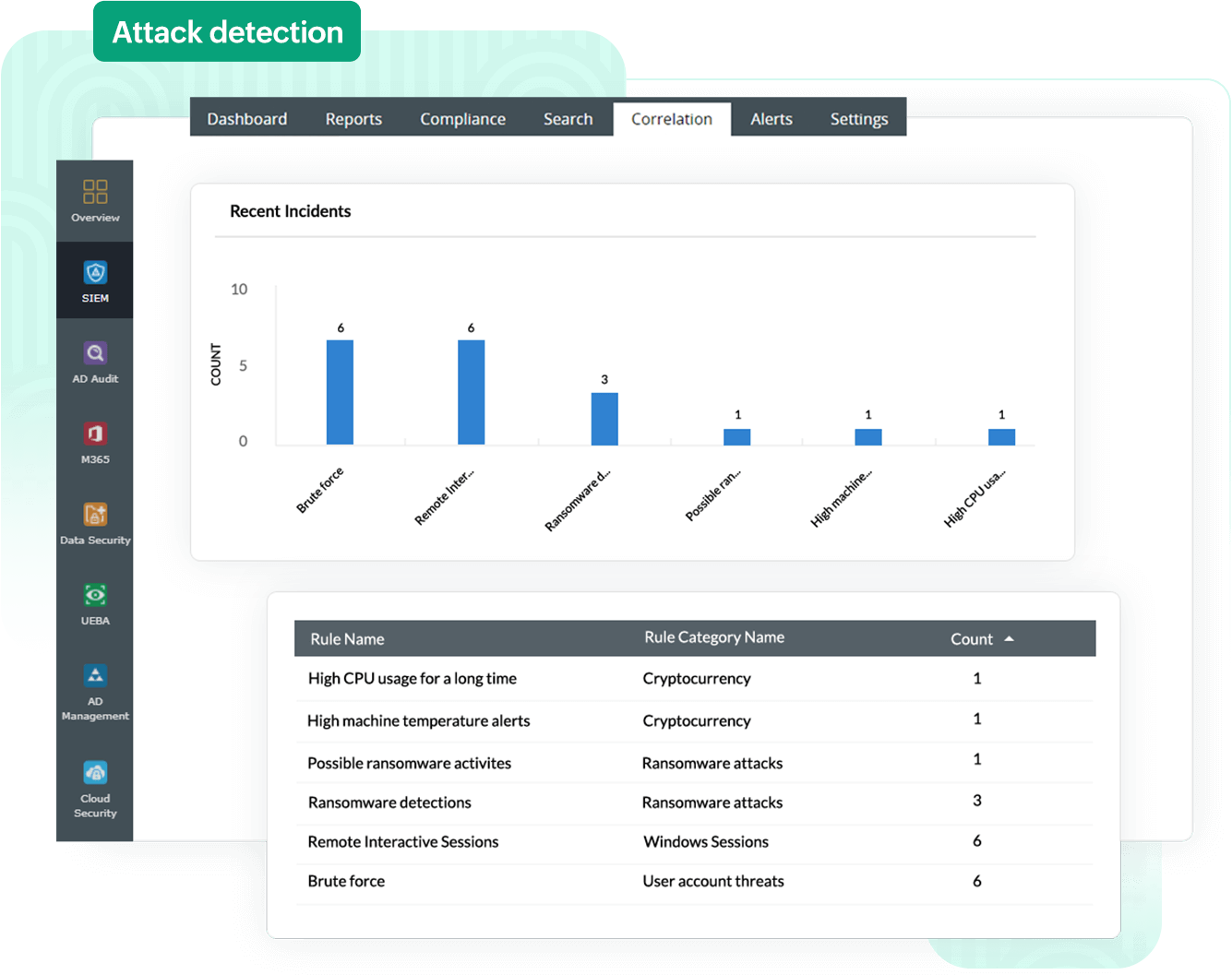
With Log360's intuitive correlation dashboard, you can view a summary of all detected security threats, including ransomware attacks, file integrity threats, and database threats and web server threats, web server threats, malicious use of command line tools, suspicious process spawning, and exploitation of built-in binary tools and utilities. You can gain insights into recent incidents, improve investigations, and resolve issues quickly.
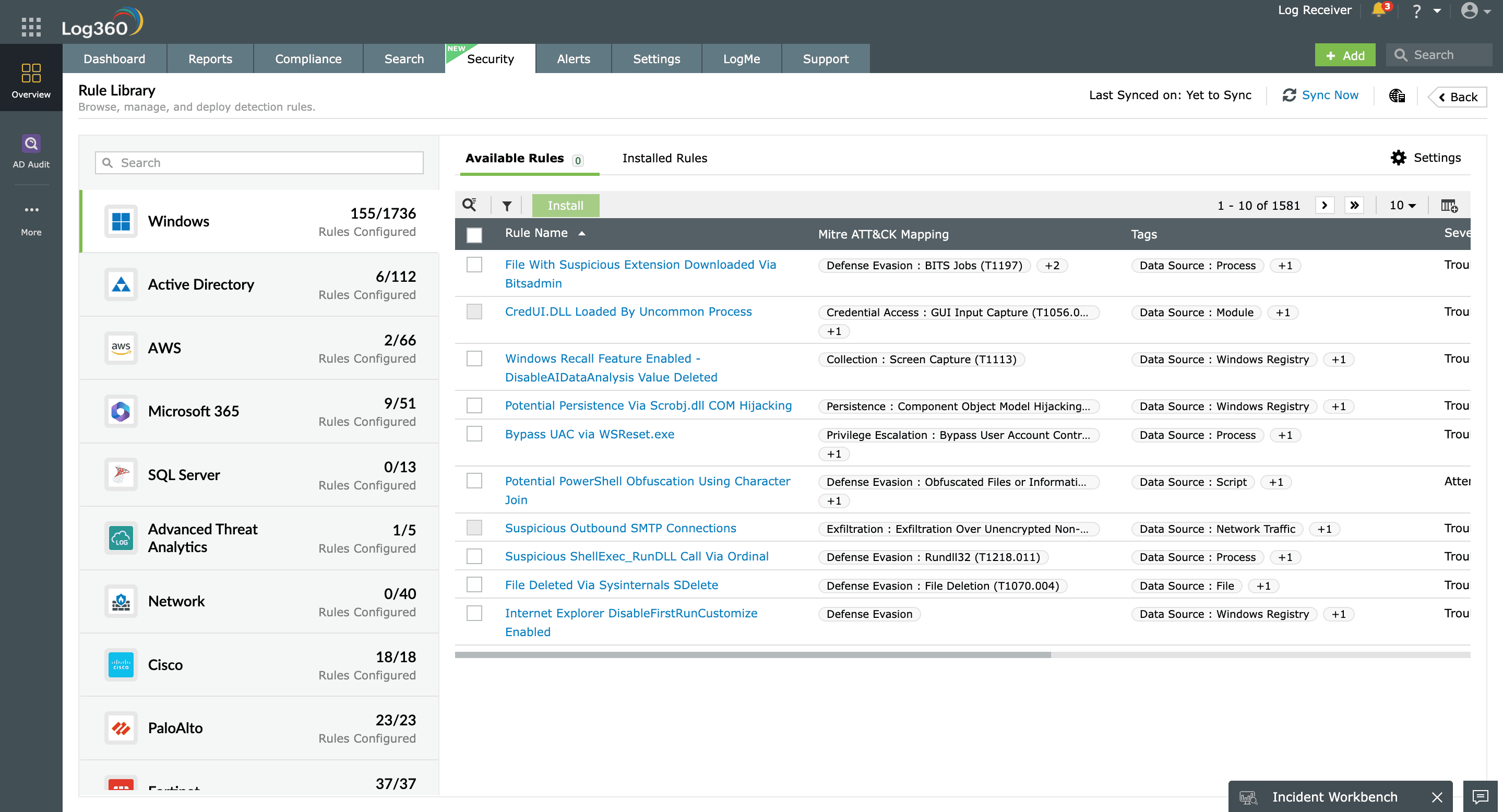
Log360's event correlation engine has over 80 predefined correlation rules for:
You can also create your own correlation rules, and clone and edit the predefined rules based on your requirements with the custom rule builder.
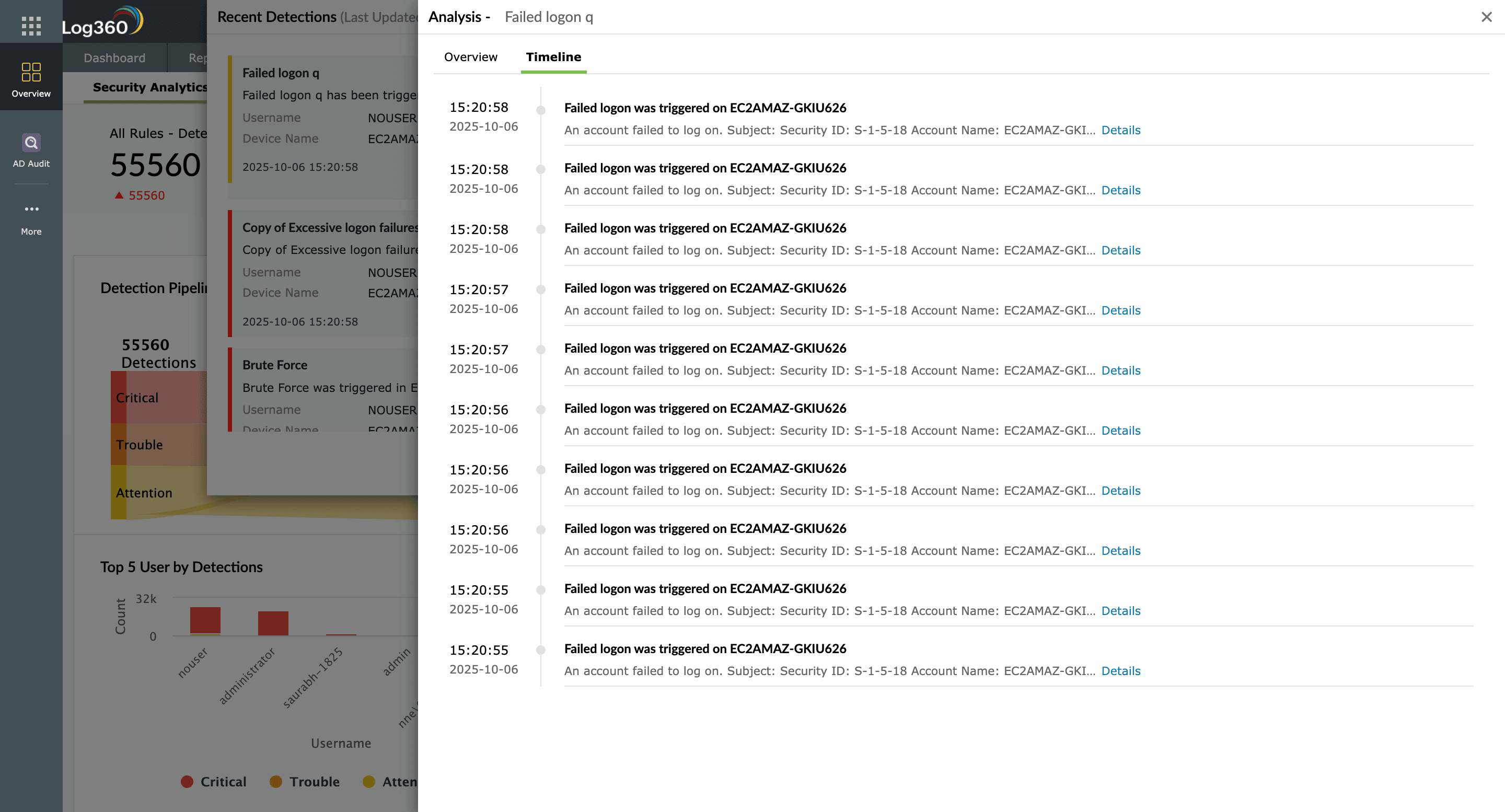
Navigate a detailed event timeline for each detected incident and drill down to raw log contents to get in-depth information on compromised accounts, infected devices, and more. Investigate cyberattacks, like brute-force attempts and cryptocurrency mining, by viewing the event history with sequential security events.
Leverage centralized event log collection where you can analyze log data from different sources across your network.
Get email and SMS alerts when a security incident is detected.
Log360's incident management console helps you manage security incidents with ease. By configuring incident workflows, you can automate incident response.
You will receive an email with the event correlation resource kit shortly.
This white paper is a great introduction to the concept of event correlation and explains exactly how it works as well as how it fits within the overall security strategy of your organization.
Our network security handbook explains the practical applications of event correlation and provides you with a few useful introductory use cases.
Learn about cryptocurrency and cryptojacking. How does illegal cryptomining affect organizations, and how can event correlation help? Our infographic will tell you more.
Event correlation in SIEM helps security teams identify and prioritize security incidents from different sources, providing a more comprehensive view of the overall security landscape.
In a typical IT environment, a large number of events and logs are generated across various systems and applications. Many of these events may appear harmless or insignificant when viewed in isolation. However, when these seemingly unrelated events are analyzed and correlated together, they may indicate a potential security threat.
The network log data is collected and analyzed with predefined rules and algorithms to detect anomalies, complex attack patterns, or any other indicators of compromise (IoCs). By detecting patterns and anomalies across various data sources, event correlation enhances the effectiveness of threat detection, reduces false positives, and enables faster response to potential security threats.
Event correlation is the process of identifying relationships between events. Event correlation works by collecting data from network traffic, endpoint devices, application devices, and much more. By analyzing this data, patterns of suspicious activity can be identified and correlated with other events to determine potential security threats.
Even correlation reduces false positives by filtering normal system behavior from abnormal behavior, minimizing unnecessary alerts and aiding in effective threat mitigation. While the process of collecting and correlating huge volumes of log data is highly complex and time-consuming, the benefits are substantial. It enables organizations to respond swiftly to emerging security incidents.
For instance, if an employee accesses a system at an unusual time and engages in unauthorized file transfers, event correlation can promptly trigger actions like blocking that particular IP address and isolating the system for mitigation.