- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
In today's data-driven world, organizations face increasing challenges in protecting confidential data stored in a database and ensuring its integrity. Database auditing plays a crucial role in addressing these challenges by providing a comprehensive approach to database activity monitoring.
ManageEngine EventLog Analyzer provides database activity monitoring for Microsoft SQL, MySQL, Oracle and IBM DB2 applications. The solution helps you gain instant alerts and ready-made reports of database activity to prove compliance with stringent IT regulatory mandates.
Here's how EventLog Analyzer helps you proactively audit database activity logs
Securely collect and store the audit logs
EventLog Analyzer serves as a centralized platform for managing and monitoring database audit logs. This tool collects, consolidates, and analyzes audit data from various database platforms, providing a unified view of database activities. It enables you to monitor changes to the database server, unauthorized user activities, access to sensitive data, SQL injection attempts, and denial-of-service attacks. EventLog Analyzer compresses and encrypts log files to utilize disk space optimally and ensure protection from tampering.
Use case: Ensure compliance with PCI DSS norms by encrypting database logs.
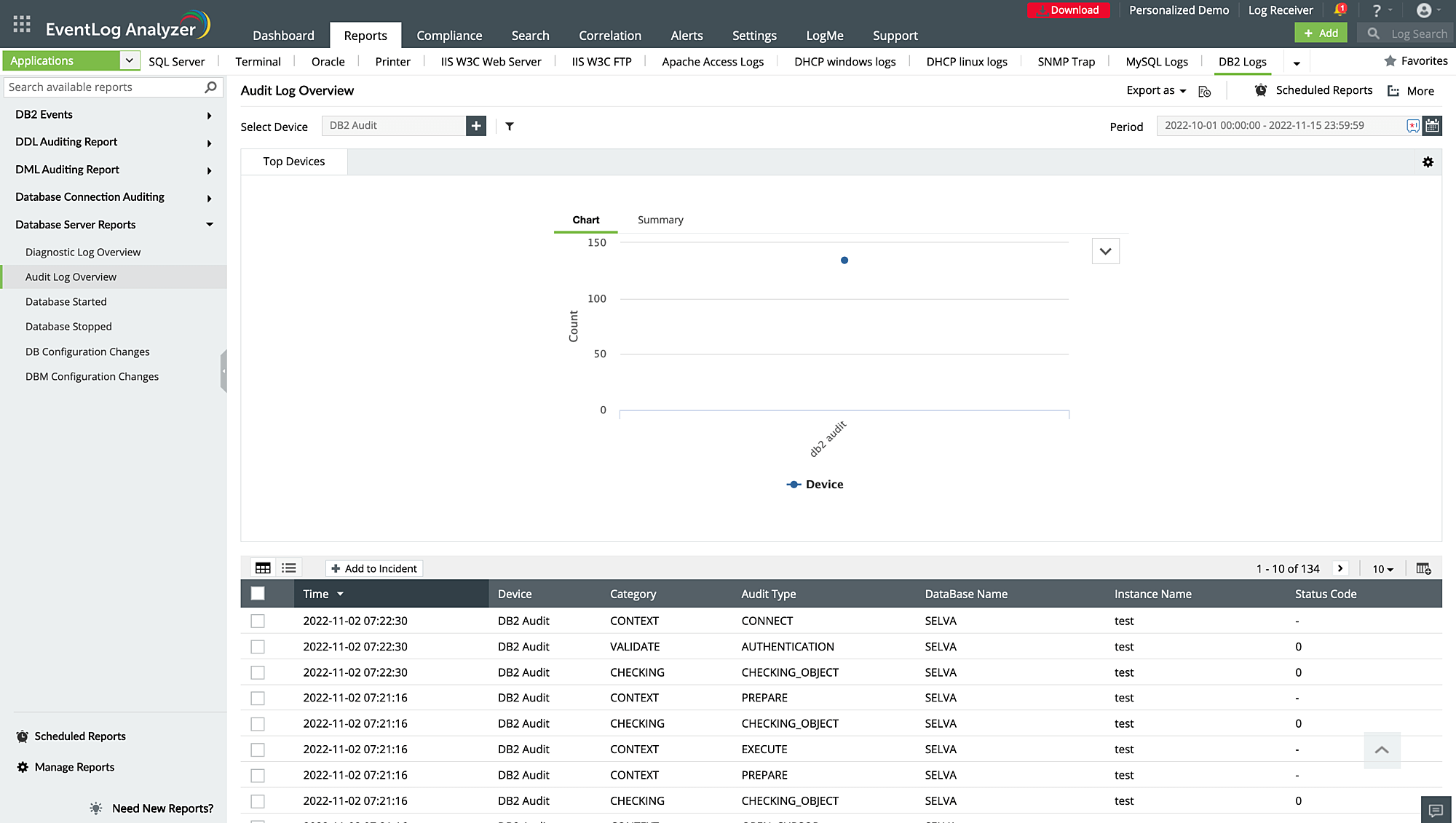
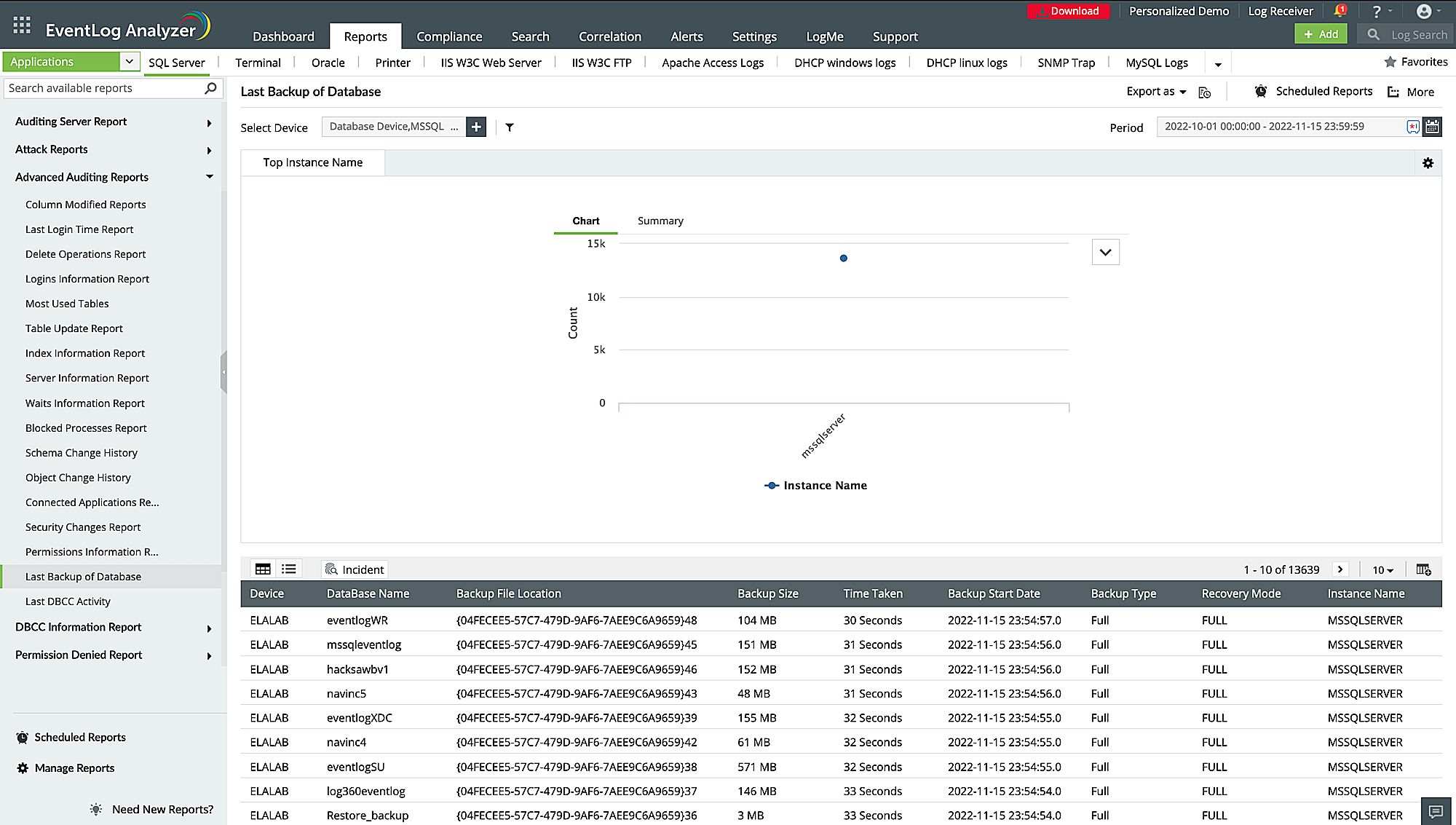
Carry out database activity monitoring
With EventLog Analyzer's database auditing reports, you can easily monitor changes to tables, changes in user permissions, server logons, and several other security events. The solution provides numerous intuitive dashboards to monitor database activity for Microsoft SQL Server, MySQL, Oracle, and DB2.
The solution also maintains a record of user access to the database, tracking who accessed the database, the actions performed, and the time of the activity. The solution's data definition language and data manipulation language change auditing report helps monitor data definition language changes (such as create, alter, drop) and data manipulation language changes (such as select, insert, delete, and update) to database schema.
Use case: Track admin activity.
Real-time alerting on critical events
EventLog Analyzer's alerting feature notifies you of critical database events in real time through email or SMS. Choose from a range of prebuilt alerts to notify you of a critical database change, or a change in access permissions such as anomalies in user activities, unauthorized user accesses, attempted security breaches, access to confidential data, and more. With these proactive alerts, you can swiftly respond to potential threats and take necessary actions to maintain the security of your database environment.
Use case: Detect unauthorized database access from a defined IP source
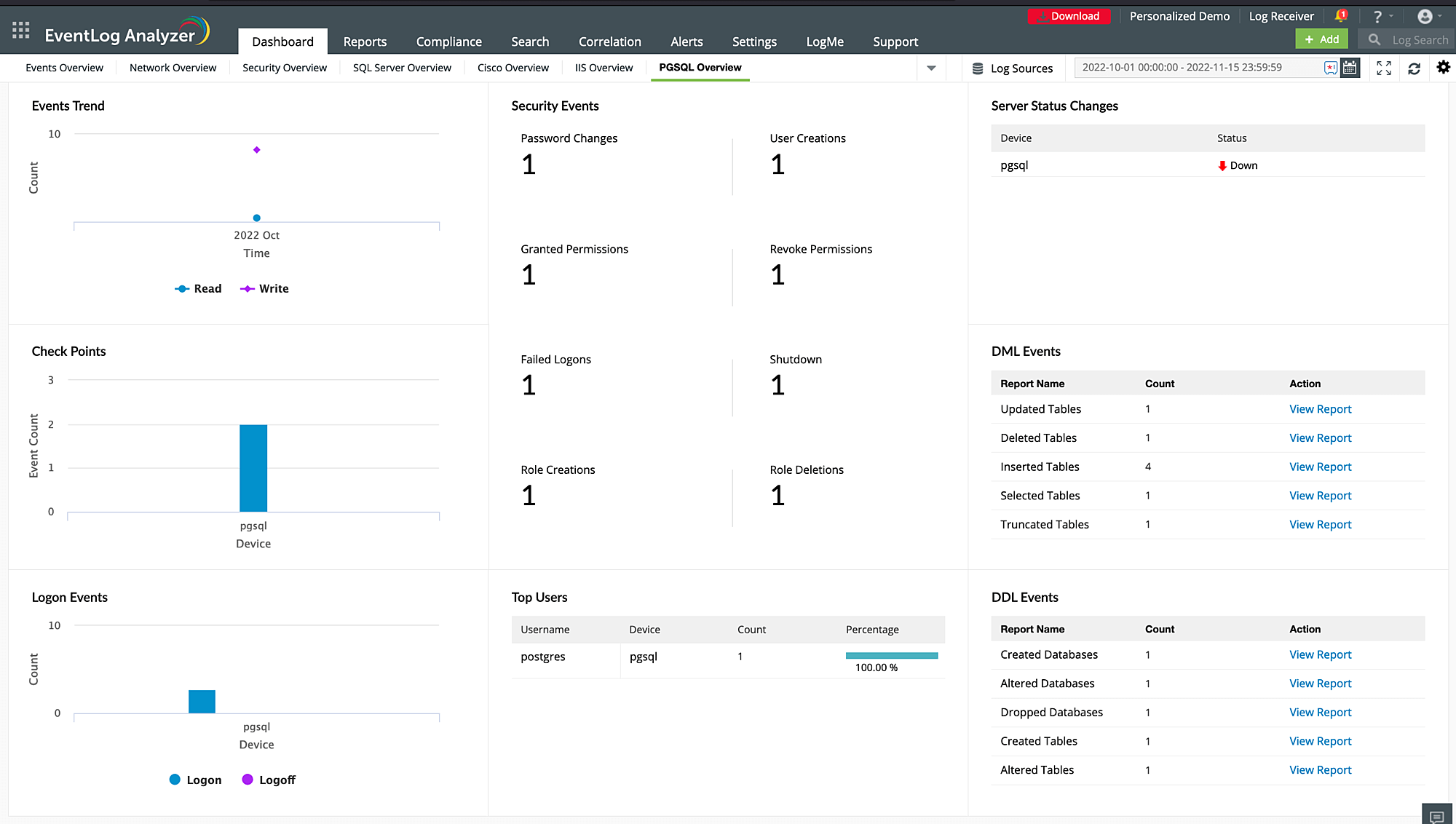
Detect external threats to databases
Leverage EventLog Analyzer's capabilities to detect external threats to your databases. The powerful correlation engine can help you correlate network activity with database activity to pinpoint threats and reduce false alarms. Mitigate application security attacks with reports and real-time alerts. The database connection auditing report helps you get information about the connection established and connection terminated. You can also detect potential security risks, such as attempts to exfiltrate sensitive data, or find vulnerabilities in the application.
Use case: Detect suspicious SQL backup activity.
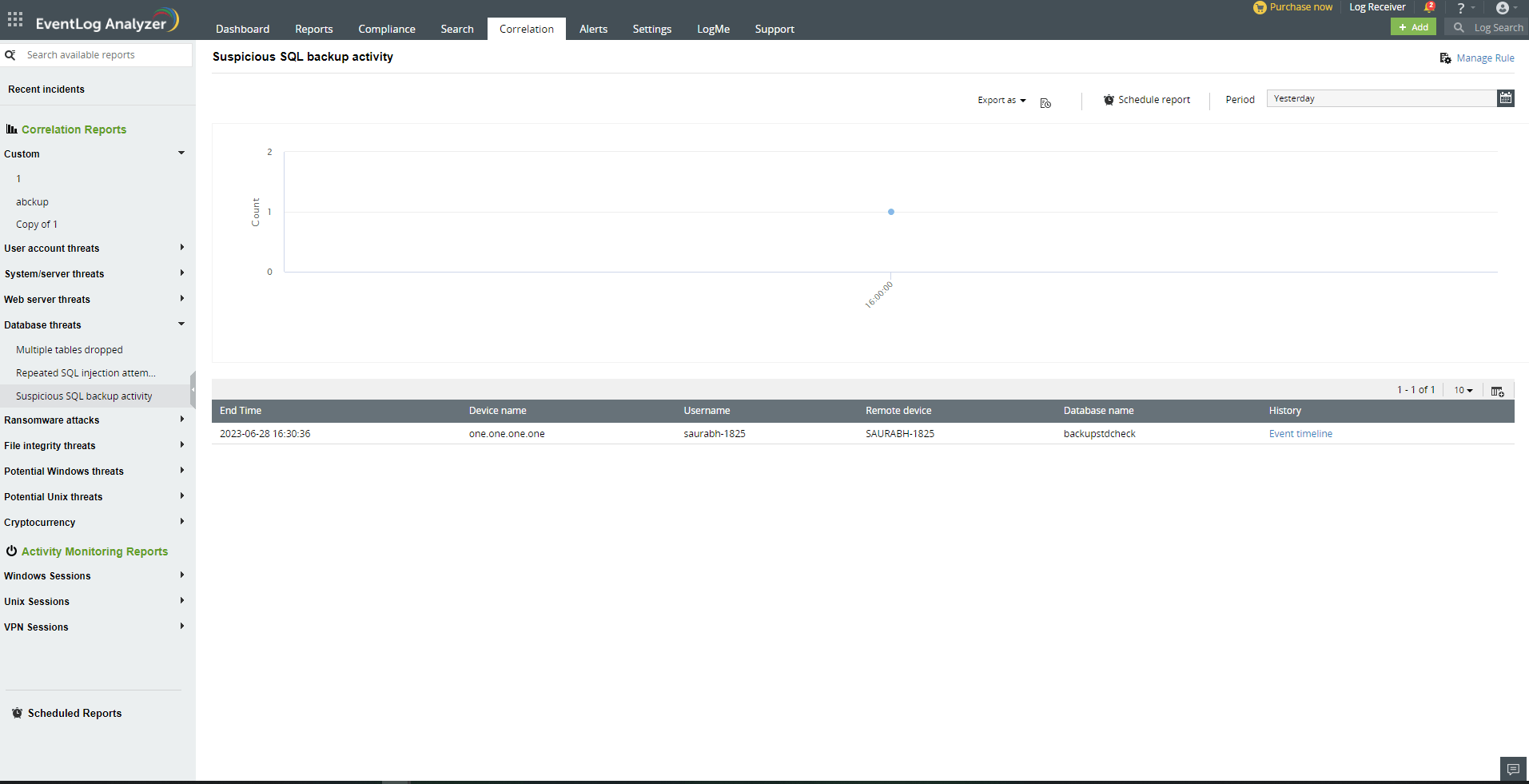
Detect suspicious insider activity
Protect your organization's sensitive data from malicious insiders by continuously monitoring internal threats to your databases. EventLog Analyzer audits database records for actionable insights on user actions to detect and mitigate security threats from malicious threat actors. It comes with a powerful correlation engine that can associate network events with database events to detect suspicious activity. The plethora of prebuilt correlation rules can alert you to unauthorized database access, suspicious backup activity, and more.
Use case: Get notified of multiple user actions performed on databases.
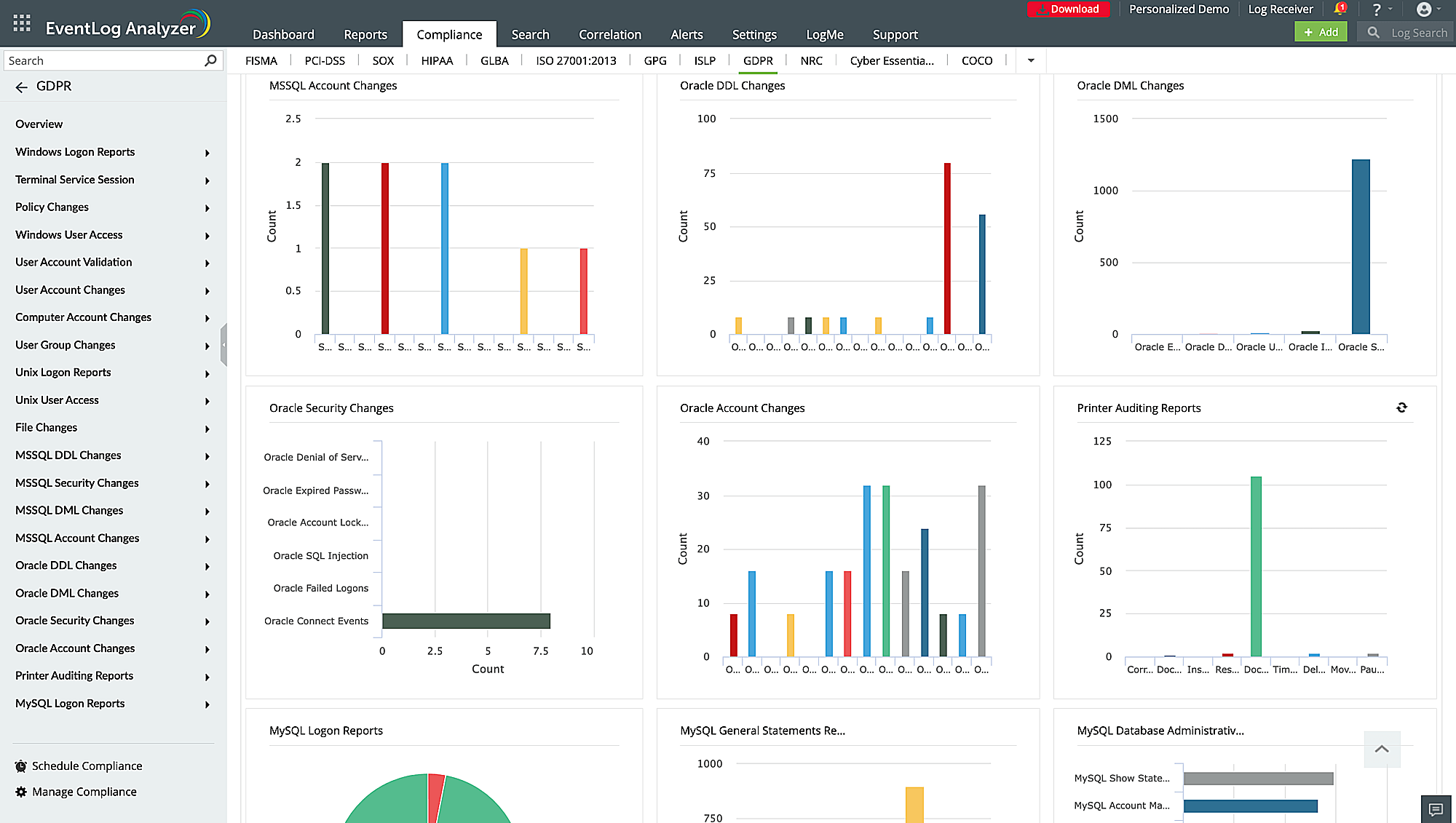
Ensure compliance with data privacy regulations
Breeze through compliance audits with integrated compliance management. Auditing enables organizations to monitor and track access to sensitive data stored in databases. By collecting, archiving, and storing logs on a database, you can leverage the power of historical event review, traceability, forensic analysis, and incident response. This proactive approach enhances overall security, facilitates compliance requirements, and enables effective mitigation of security incidents. You can generate out of the box prebuilt compliance reports to meet stringent IT regulatory mandates such as the GDPR, GLBA, FISMA, PCI DSS, SOX , CCPA, and more.
Other solutions offered by EventLog Analyzer
Microsoft SQL server monitoring
Secure your MS-SQL servers from threats and receive prompt alerts on suspicious events, account lockouts, and altered databases.
Oracle database auditing
Audit and track user access and Oracle Database server activities to identify unauthorized access attempts.
Web server auditing
Proactively monitor web server logs from applications like Microsoft IIS server, Apache server, and Nginx server with ease.
Network device monitoring
Effortlessly monitor network perimeter devices, such as firewalls, switches, routers, IDSs, and IPSs and ensure robust protection against intrusions.
5 reasons to choose EventLog Analyzer as your database monitoring tool
1. Log visualization
The solution visualizes database and other network events with intuitive charts and graphs to help you easily search and identify suspicious attack pattern.
2. Privileged user activity auditing
EventLog Analyzer provides you with detailed audit trails and reports and alerts you when privileges are being misused.
3. File integrity monitoring
The solution's FIM capability helps you get detailed insights on file permission changes like new file created, existing files modified, renamed, or deleted.
4. Advanced threat analytics
EventLog Analyzer has access to international threat feeds like STIX/TAXII, and AlienVault OTX which helps detect and prevent threats interacting with your database.
5. Log forensic analysis
The solution's powerful log search engine effectively investigates and search through raw logs, and helps in identifying the root cause of a data breach.
Frequently asked questions
Database activity monitoring (DAM) refers to the auditing of database activities, such as database access and modifications, in real time. By correlating network logs with database logs, DAM tools analyze and report on database activity, provide evidence for breach investigations, and alert on suspicious events. With the real-time insights offered by DAM tools, you'll be better prepared to ensure the confidentiality and integrity of your database.
Using EventLog Analyzer as your database activity monitoring tool, you can effectively monitor and audit all database activities with minimal effort.
Database auditing ensures that appropriate security measures are in place to prevent unauthorized copies of sensitive data, SQL injection, privilege abuse, account lockouts, or data breaches. It also helps spot insider threats, database anomalies, identity theft, and more. By detecting these activities promptly, organizations can take immediate action to prevent potential breaches and mitigate risks. Periodically auditing your organization's sensitive data stored on the database helps ensure all business critical data are safe and secure from the hands of intruders.
Listed below are some of the common database attacks and how EventLog Analyzer helps you mitigate them:
- SQL injection: Attackers inject malicious SQL queries to manipulate the database. EventLog Analyzer mitigates SQL injection attacks by monitoring and analyzing database logs, detecting suspicious SQL statements, unusual input patterns, and unauthorized commands.
- Privilege Escalation: Attackers gain unauthorized privileged access to a system, allowing them to view sensitive data, or compromise the system integrity. EventLog Analyzer sends real-time alerts when there are changes in user privileges or unusual activities from privileged users.
- Denial of Service(DoS): Attackers prevent the intended user from accessing the computer system or network resources. EventLog Analyzer constantly monitors for unusual network traffic to detect DoS attacks.
- Unauthorized Access: An unauthorized user gains access to a database. EventLog Analyzer keeps an eye out for failed login attempts, changes in database configuration, and helps mitigate them.
Every organization needs a database activity monitoring tool like EventLog Analyzer to proactively audit the database logs. To perform database activity monitoring, several technologies like memory scraping, network sniffing, and database audit logs are combined. Correlating database logs with these tools helps monitor and detect unauthorized access to confidential data. This also safeguards your database servers from internal and external security threats.