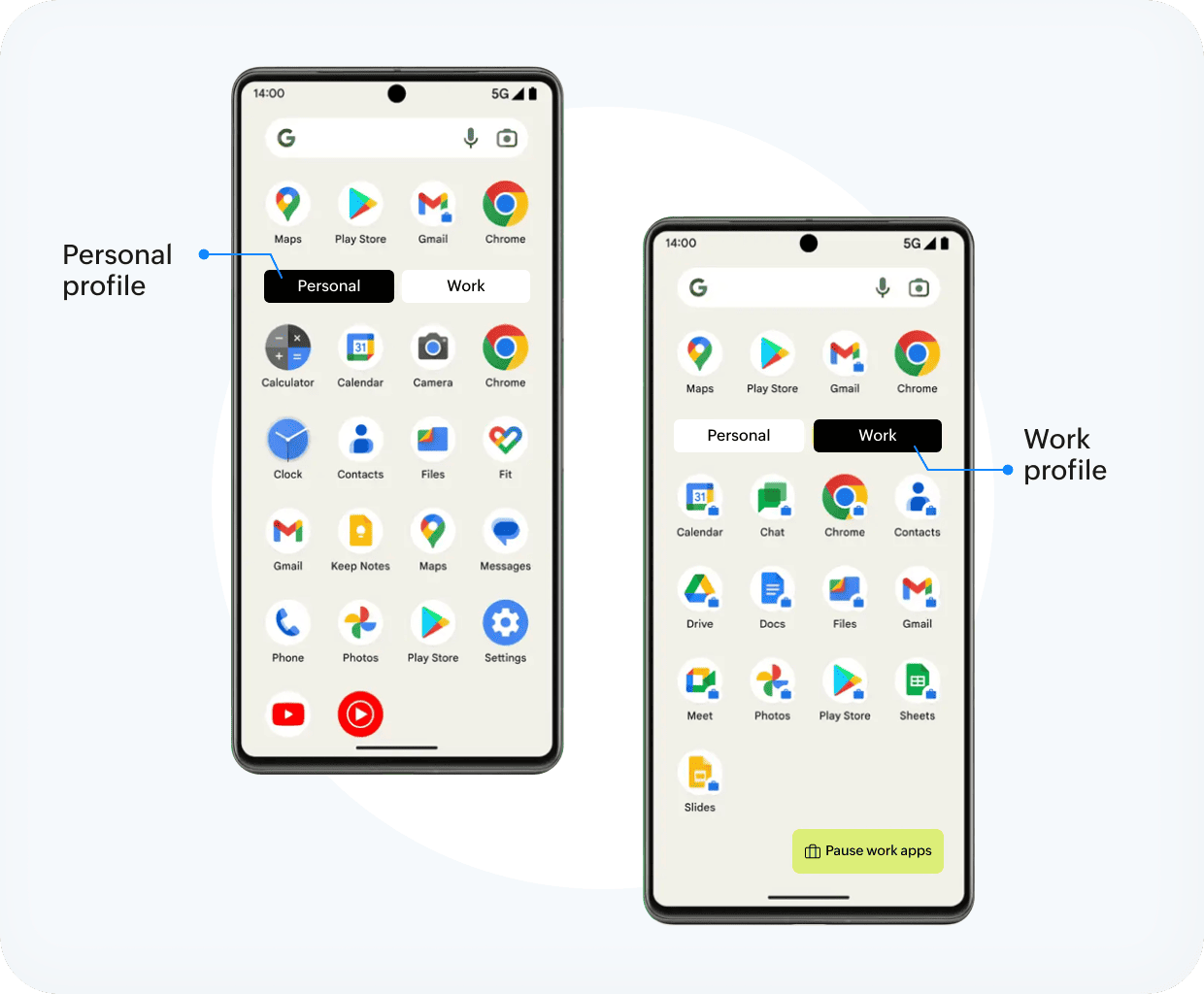
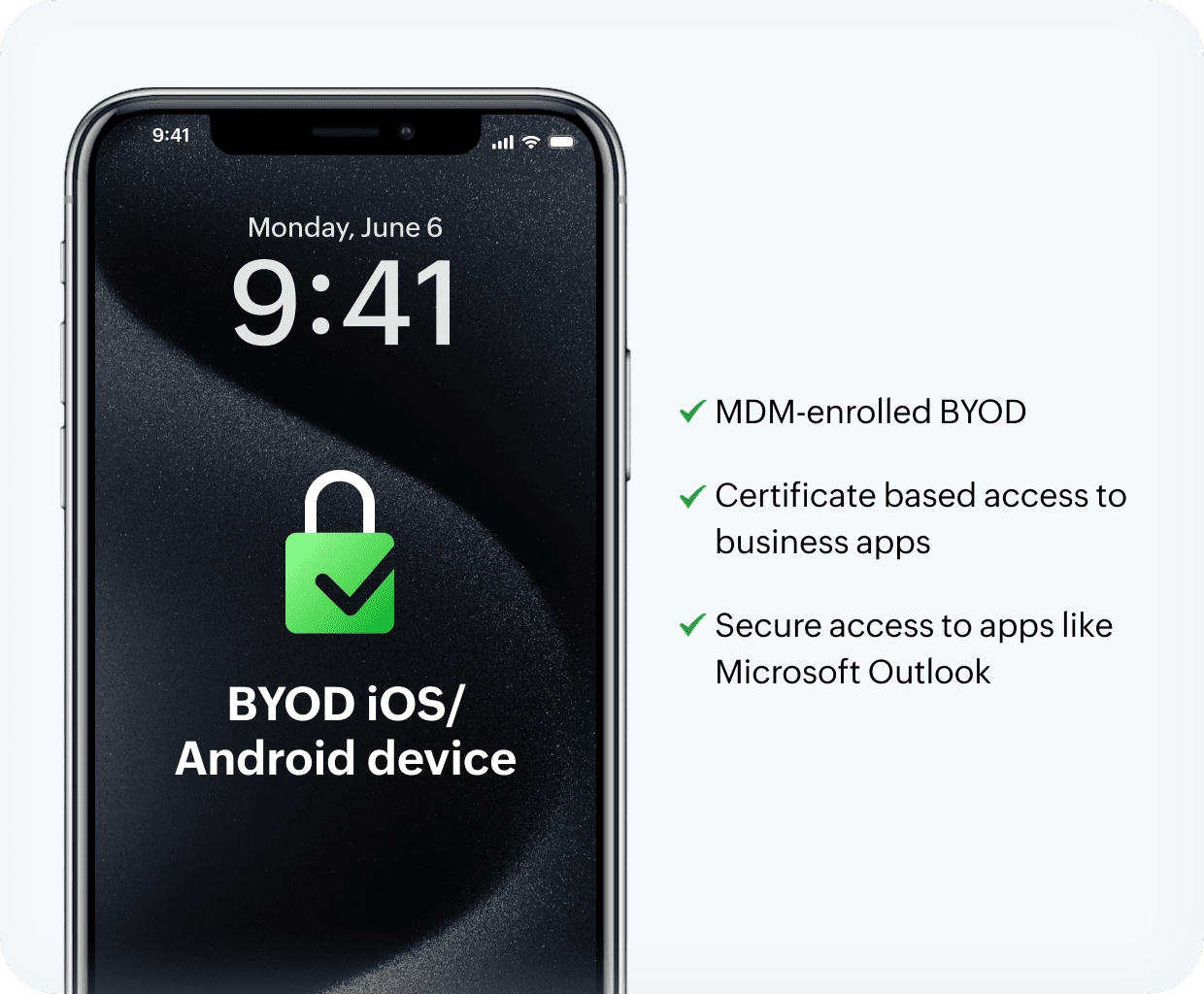
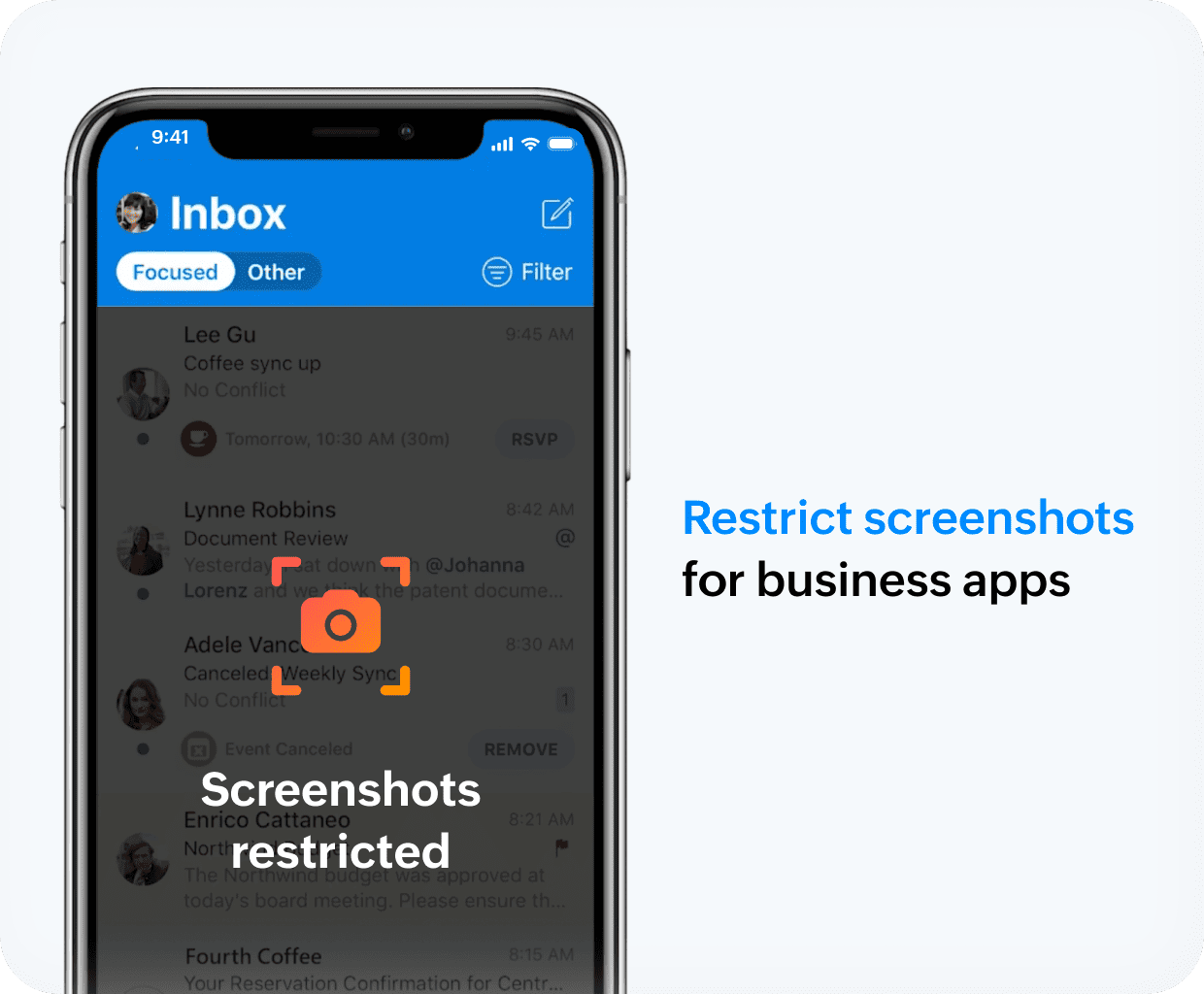
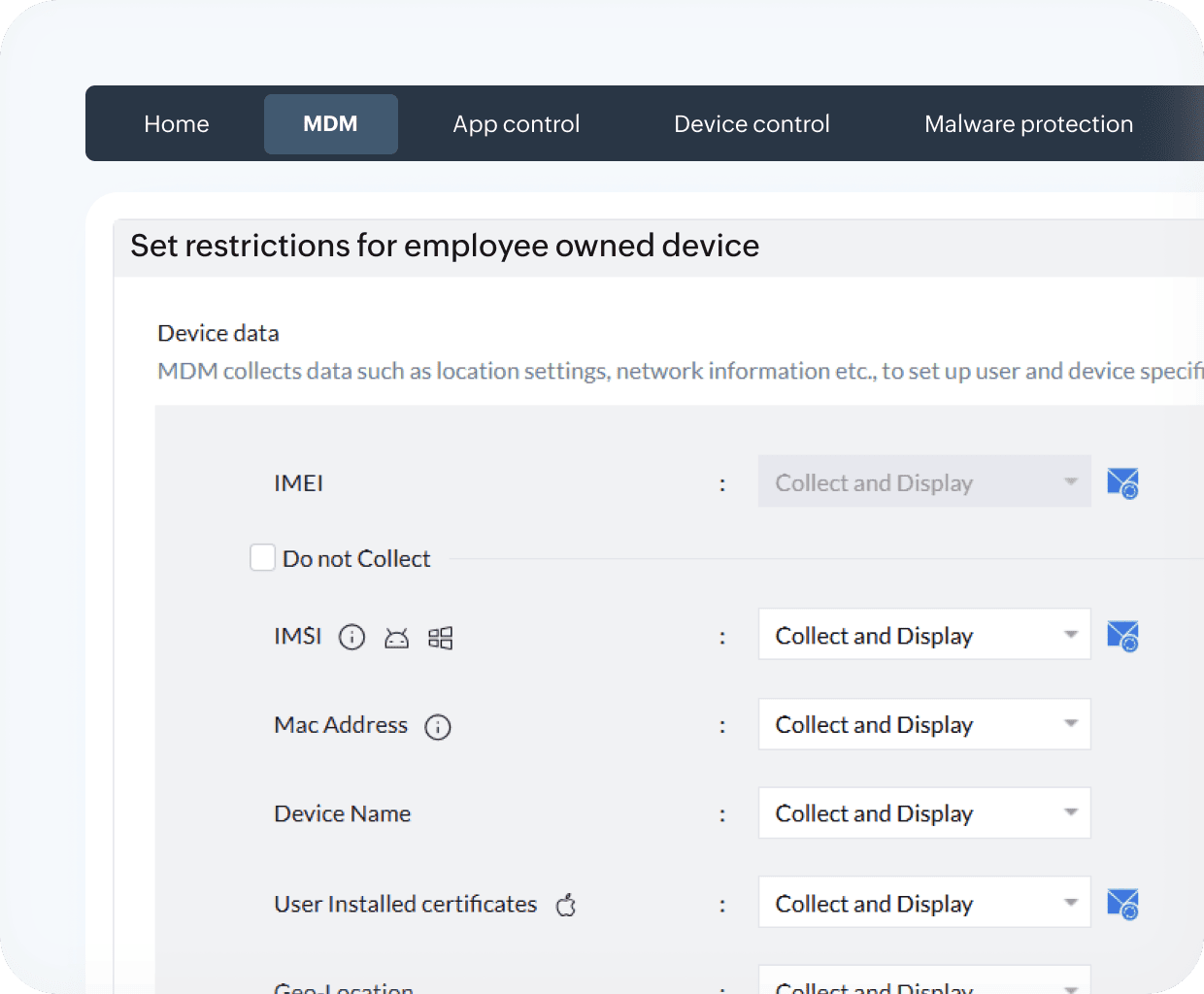
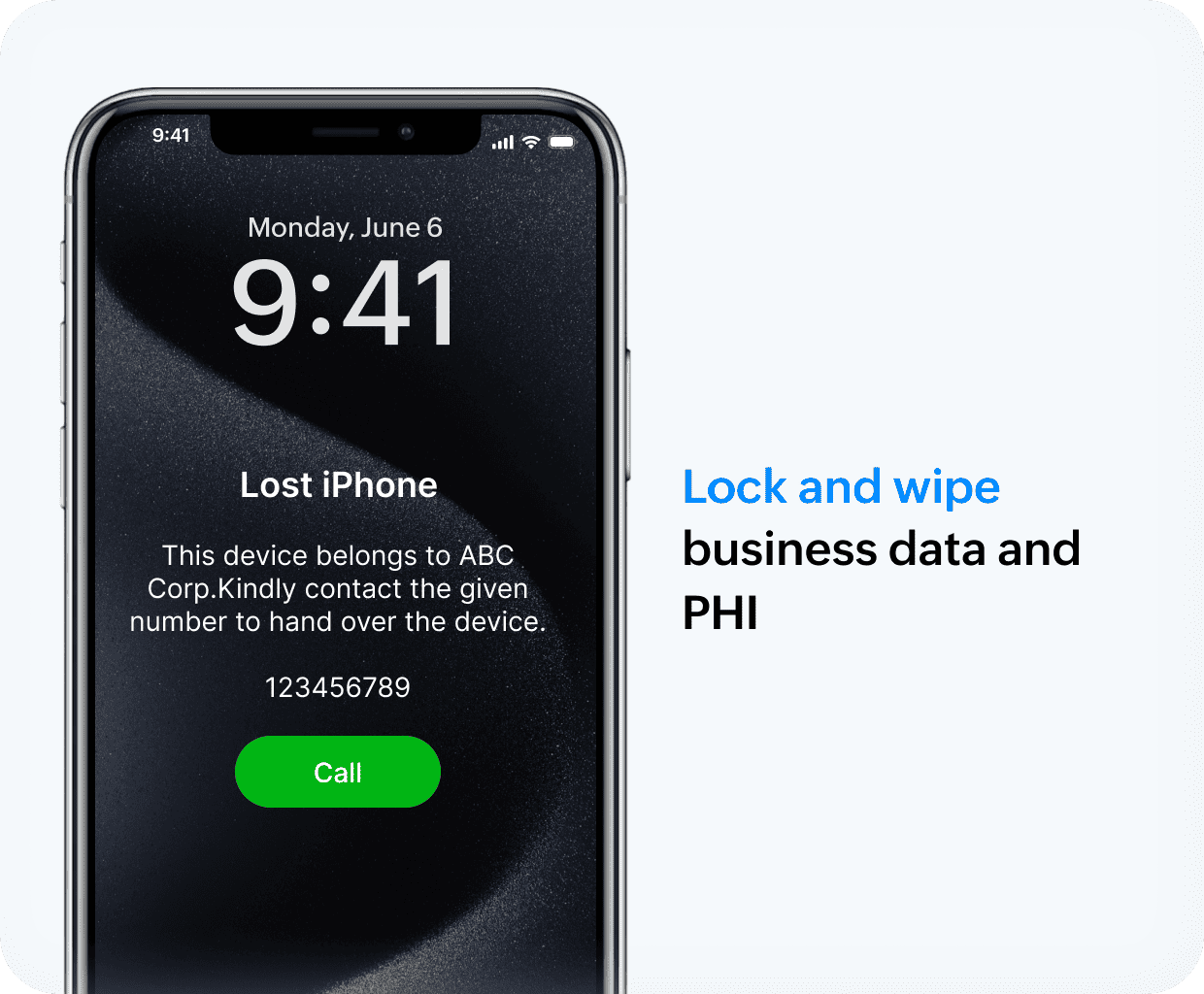
Manage BYOD without violating physician privacy
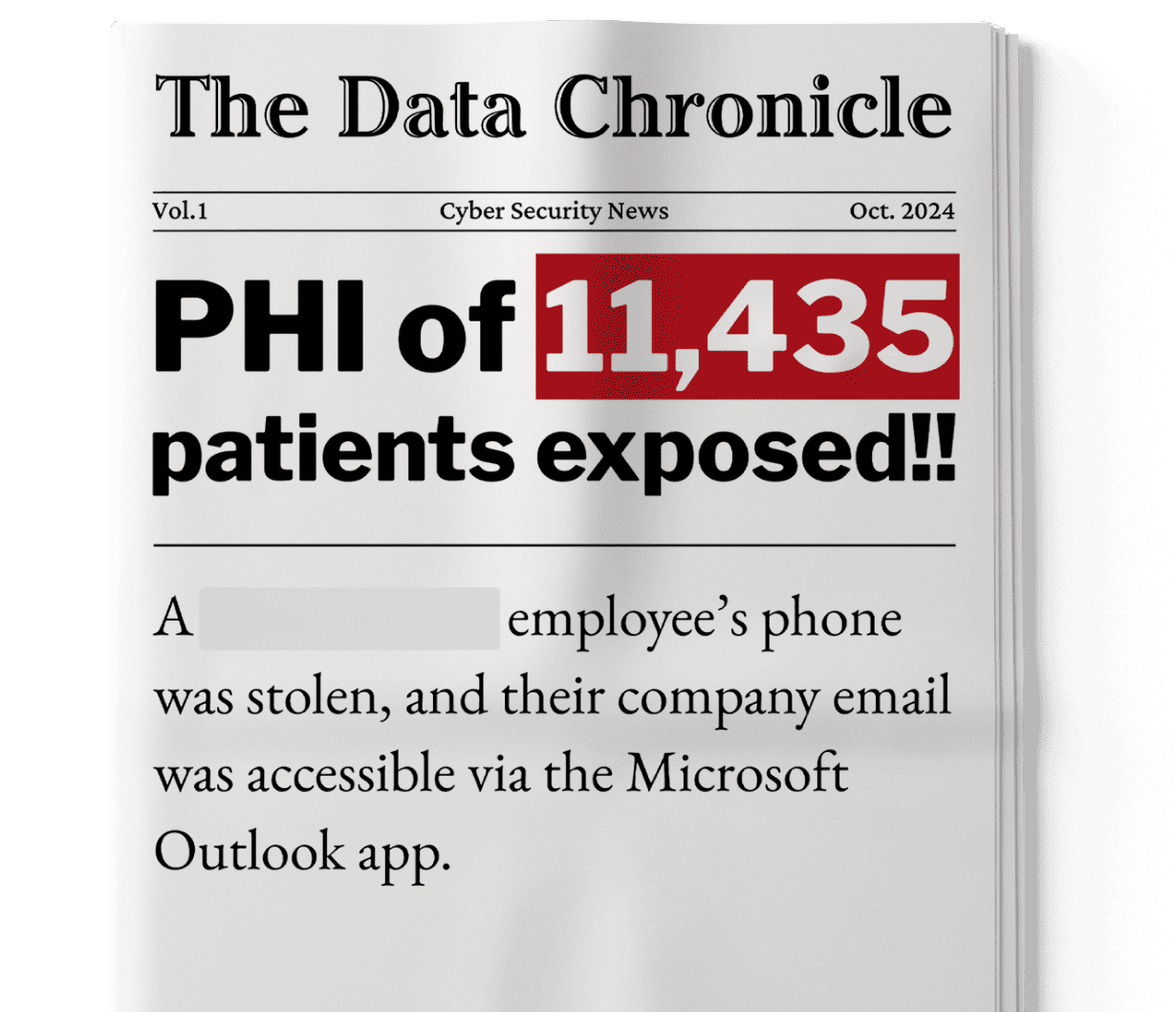
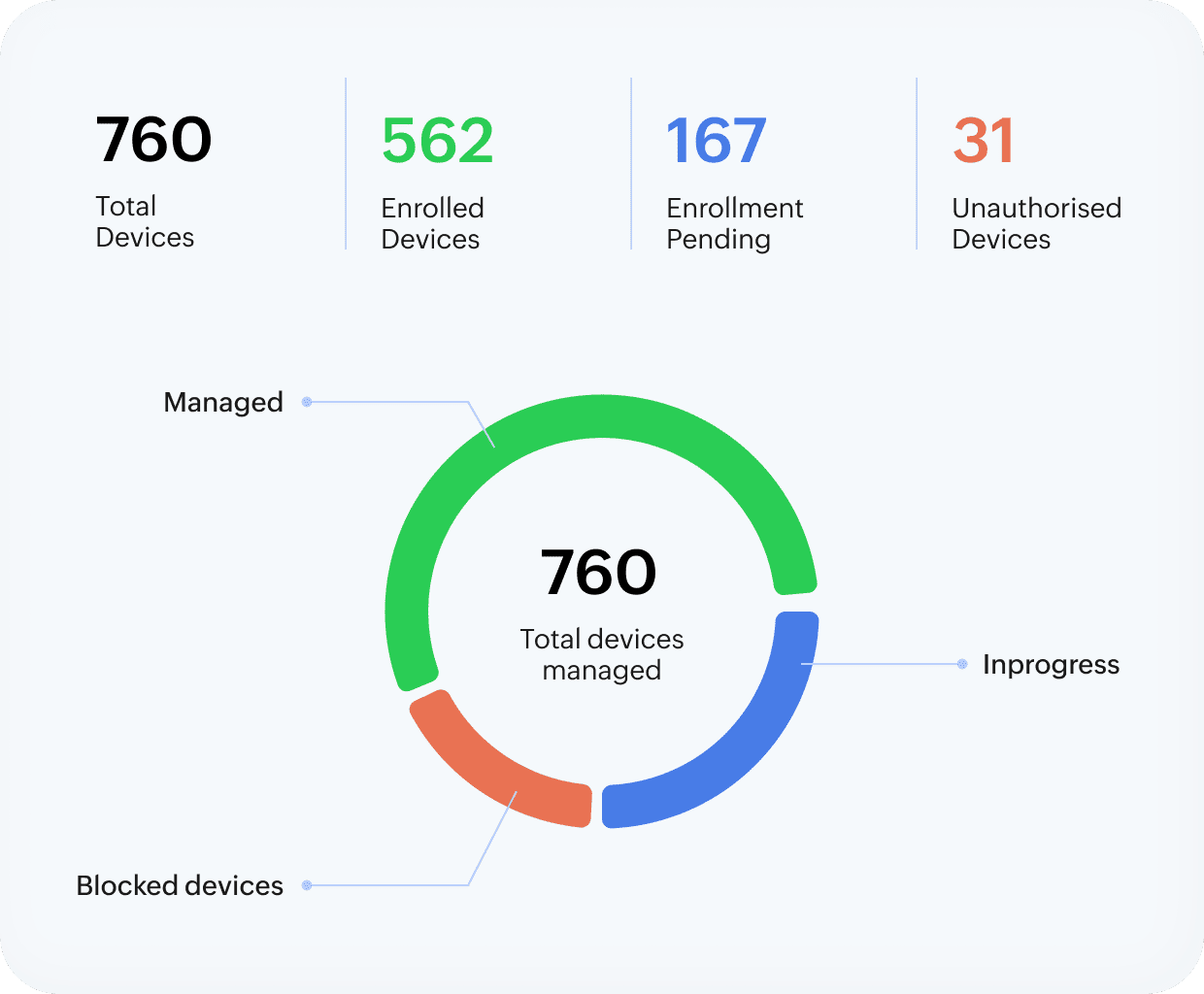
Stolen personal devices could act as gateways to organizational apps like Outlook and potentially expose PHI. With the Digital Health Most Wired National Trends 2024 suggesting increased adoption of BYOD across healthcare organizations, the lines separating security and privacy are thin without Endpoint Central.