The usage of browsers is ubiquitous in every organization and as of January 2020, Google Chrome has ascendancy over other browsers with a whopping 68 percent market share. Each browser encompasses multiple extensions or add-ons, and plug-ins, so as to augment the browser functionalities and enhance user experience. Here are a couple of reasons why users install browser extensions:
However, though the world of browser extensions is efficacious beyond question, it can prove to be harmful and is capable of putting an organization in jeopardy. Extensions can snoop on your browsing and capture personally identifiable information. Of all the browsers, Chrome has a thriving extension ecosystem and there’s probably an extension for almost everything you would want to do. That said, Google recently removed and disabled over 500 malicious extensions, and this isn’t the first occurrence.
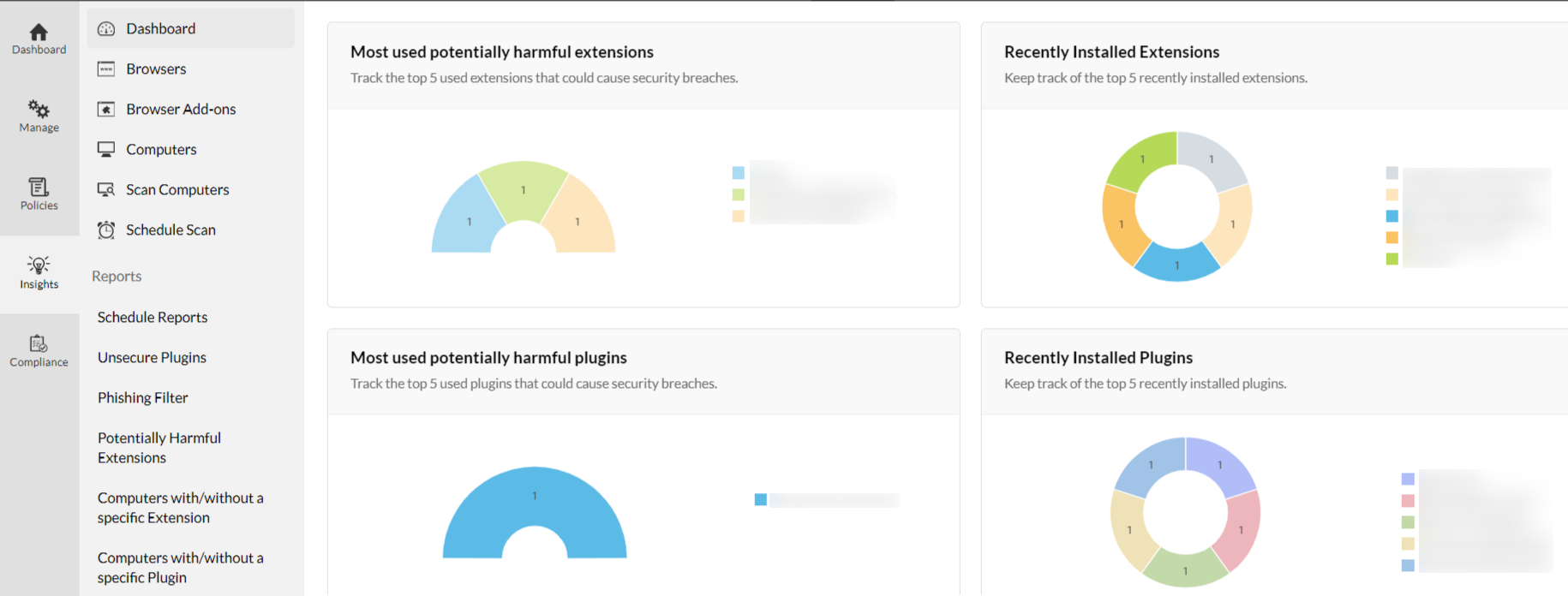
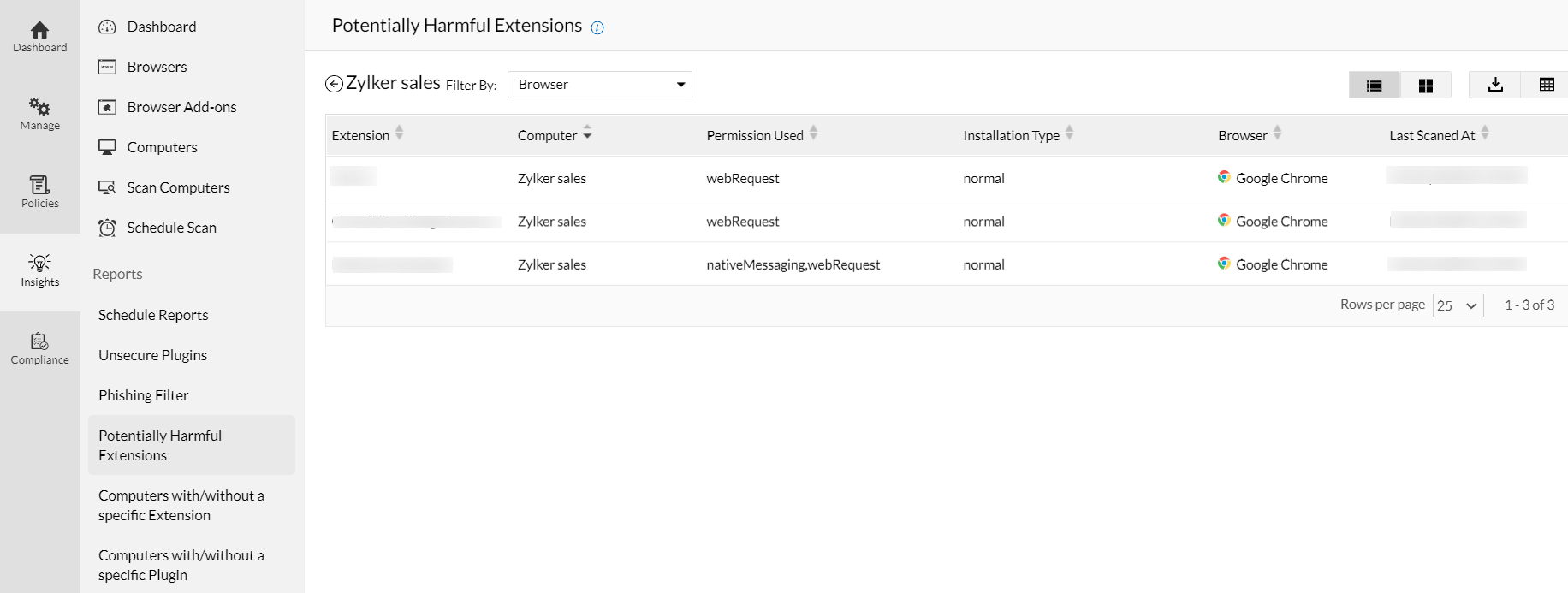
Each browser extension requires a certain degree of permission for optimum usage. At the time of installation, the necessary permissions are granted by the end users without scrutinization. Since these extensions procure access to the end user’s browsing data and classified information, it becomes a walk in the park for cybercriminals to exploit these extensions to exfiltrate sensitive data. Browser extensions are inherently weak in terms of security, and to top all this, lack of visibility over the installed extensions, and the permissions they possess, make it impossible for IT administrators to control them.
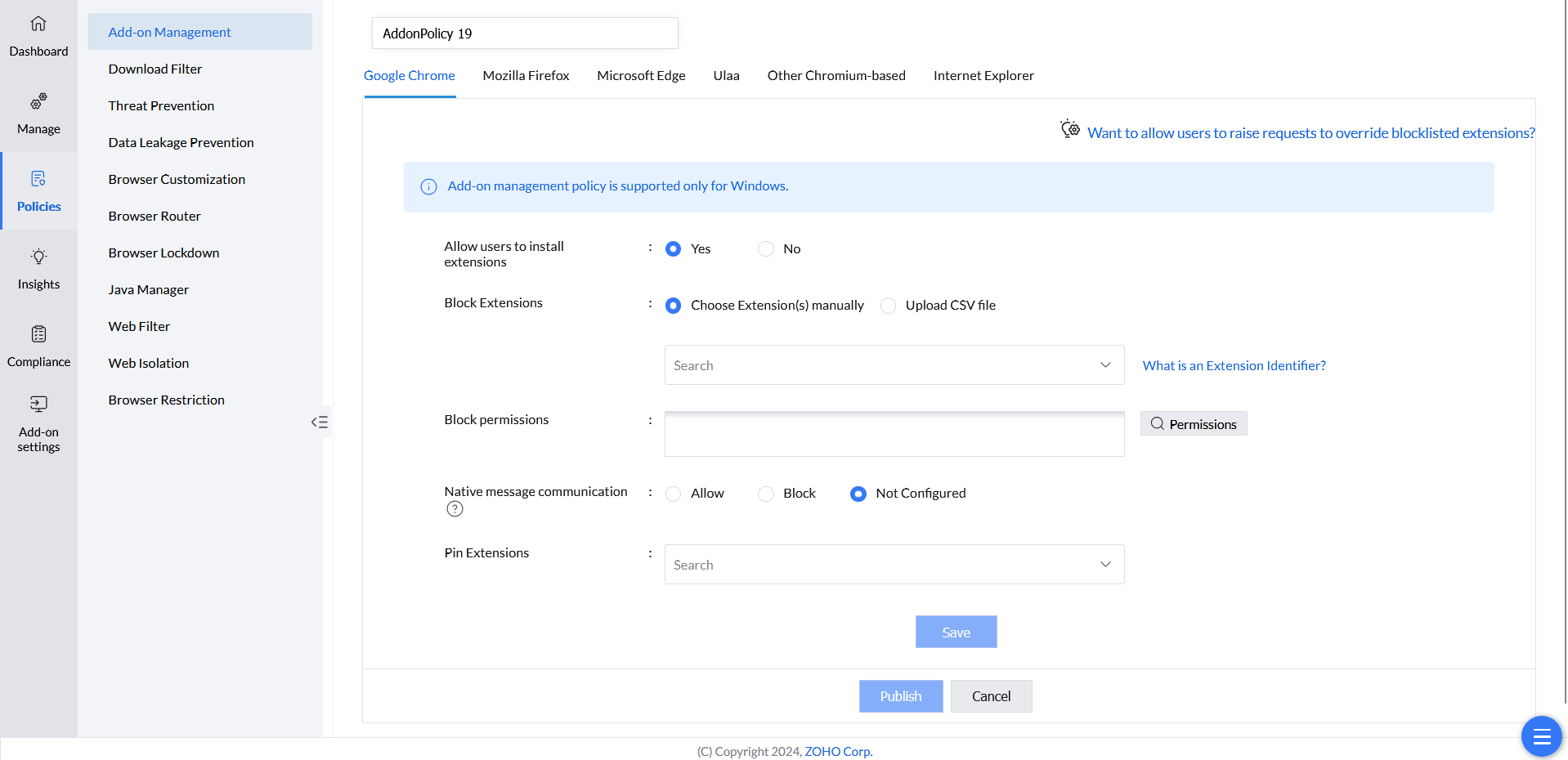
Therefore, it is indispensable for every IT administrator to gain a bird’s-eye view over the browsers used in the network, and the add-ons that are installed, besides fortification.
Note:Ensure you are using build number 10.0.476 and above versions to reap the benefits of add-on management using Endpoint Central. Download the service pack to upgrade to the latest build.