Machine-based MFA
Machine-based MFA is a setting intended to protect business-critical machines in an organization by
preventing them from being compromised.
Note: Machine-based MFA requires the Professional Edition of ADSelfService Plus with Endpoint MFA. If you do not have
these, machine-based MFA will not be enforced.
How does Machine-based MFA work?
When machine-based MFA is enforced for a particular machine, any user accessing the machine has to prove
their identity using MFA to log in successfully. The MFA authenticators in the prompt will be based on
the authenticators configured for the user in the MFA for Machine
Login section. These settings differ from policy-based machine MFA settings, as these are meant
to secure sensitive machines under any circumstance, i.e., MFA will be enforced on the selected machines
irrespective of the enrollment status of the user attempting to log in or the availability of the
ADSelfService Plus server.
Note: To set up policy-based settings that apply to users not machines, please
click
here.
When this setting is enabled, users will not be allowed to log in to the machine on which machine-based
MFA is enforced if:
- The ADSelfService Plus server is not reachable.
- The user account is restricted in ADSelfService Plus.
- The user does not belong to any policy that has MFA for Machine Login configured.
- The user has not enrolled for any of the authenticators configured in the MFA for Machine Login
(both online and offline MFA) section, regardless of whether the Force Enrollment
option is enabled for the user policy.
- The user license consumption limit has been exceeded or Endpoint MFA has not been purchased. To
purchase Endpoint MFA, click here.
However, users who have selected the Trust this machine setting on the login screen will be
allowed to log in to the machine without performing MFA for the specified duration after their initial
identity verification.
Note: Make sure to update the login agent to the following latest versions for
proper enforcement of MFA: Windows 5.10, macOS 1.7, or Linux 2.4 and above. If an older version of the
login agent is installed on the machine, and the ADSelfService Plus server is not reachable, the user
will be allowed to access the machine if the Skip MFA when ADSelfService Plus server is down or
unreachable option is enabled.
Steps to enforce Machine-based MFA
- Navigate to Configuration > Administrative Tools > GINA/Mac/Linux (Ctrl+Alt+Del) > GINA/Mac/Linux
Installation > Installed Machines.
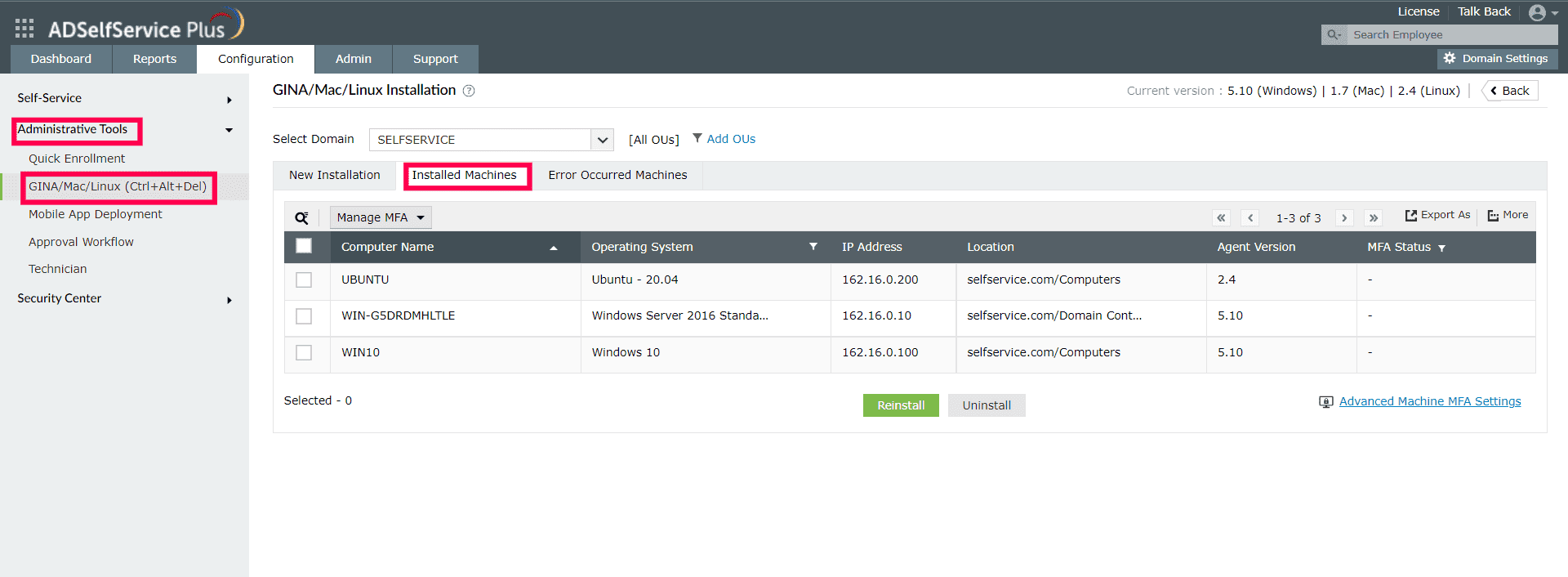
- Select the required domain from the drop-down list.
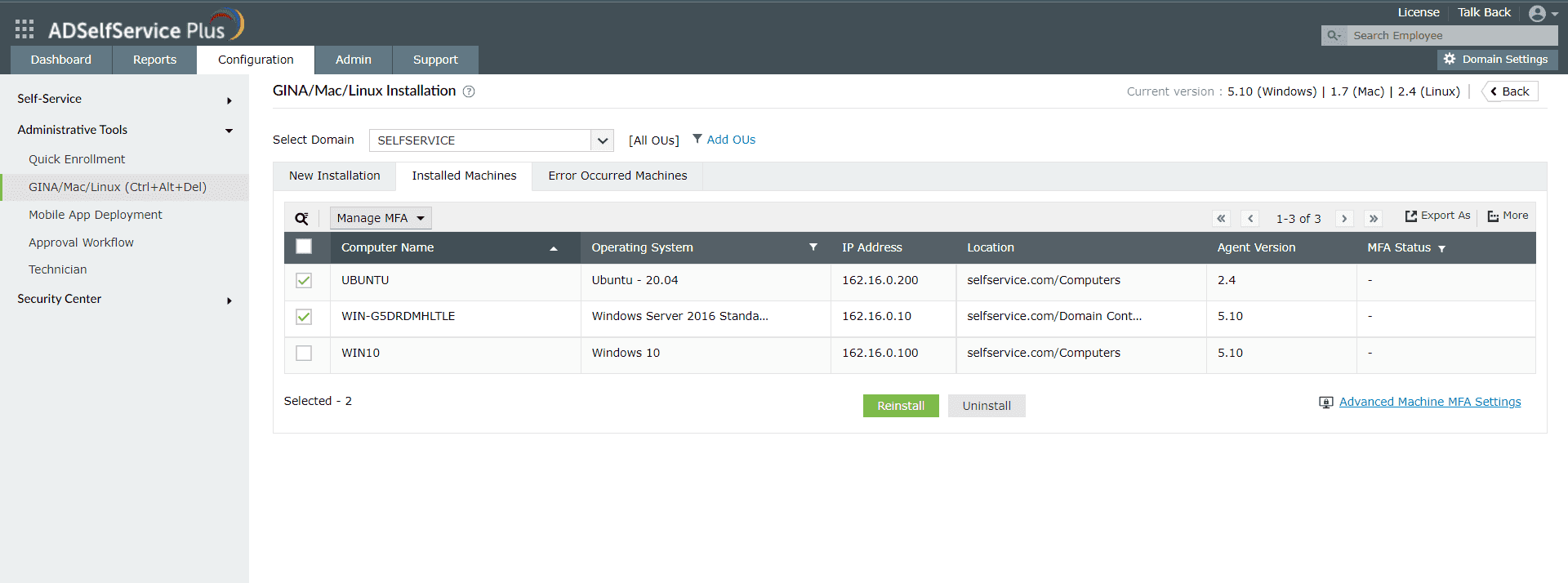
- Select the machines on which you want to enforce machine-based MFA.
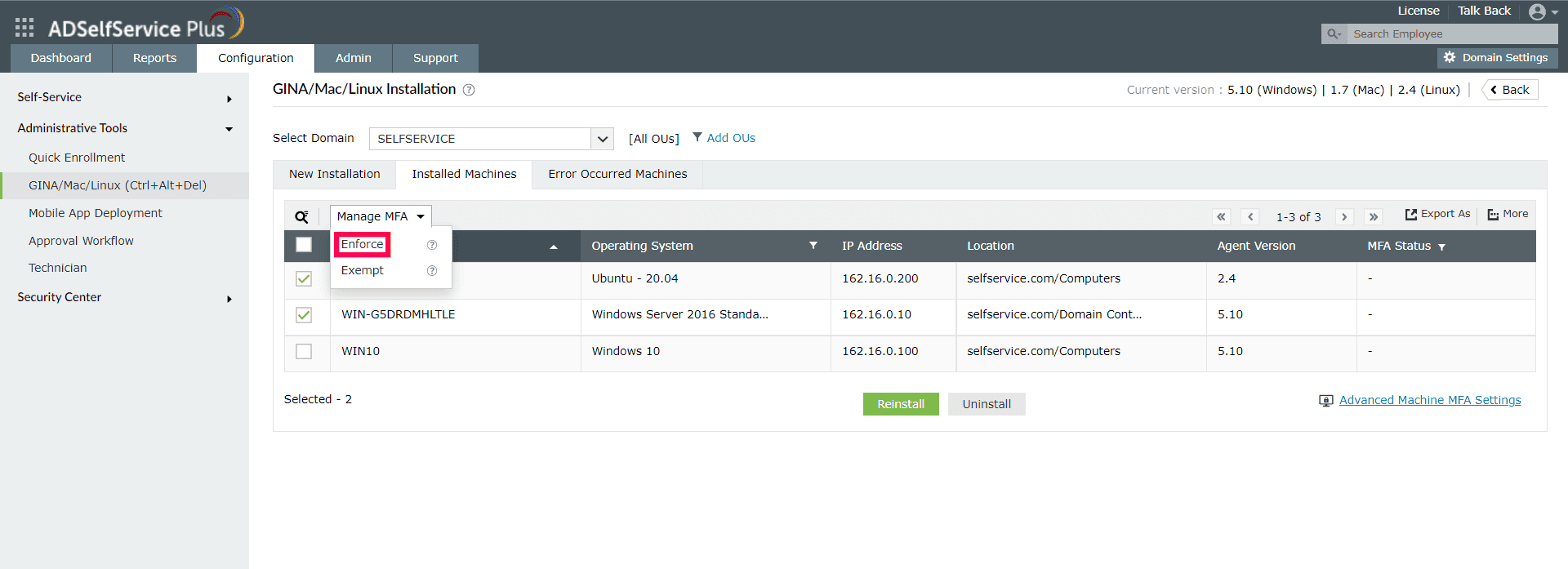
- Click Manage MFA and select Enforce.
Steps to exempt a machine from Machine-based MFA
- Navigate to Configuration > Administrative Tools > GINA/Mac/Linux (Ctrl+Alt+Del) > GINA/Mac/Linux
Installation > Installed Machines.
- Select the required domain from the drop-down list.
- Select the machine that you want to exempt from machine-based MFA.
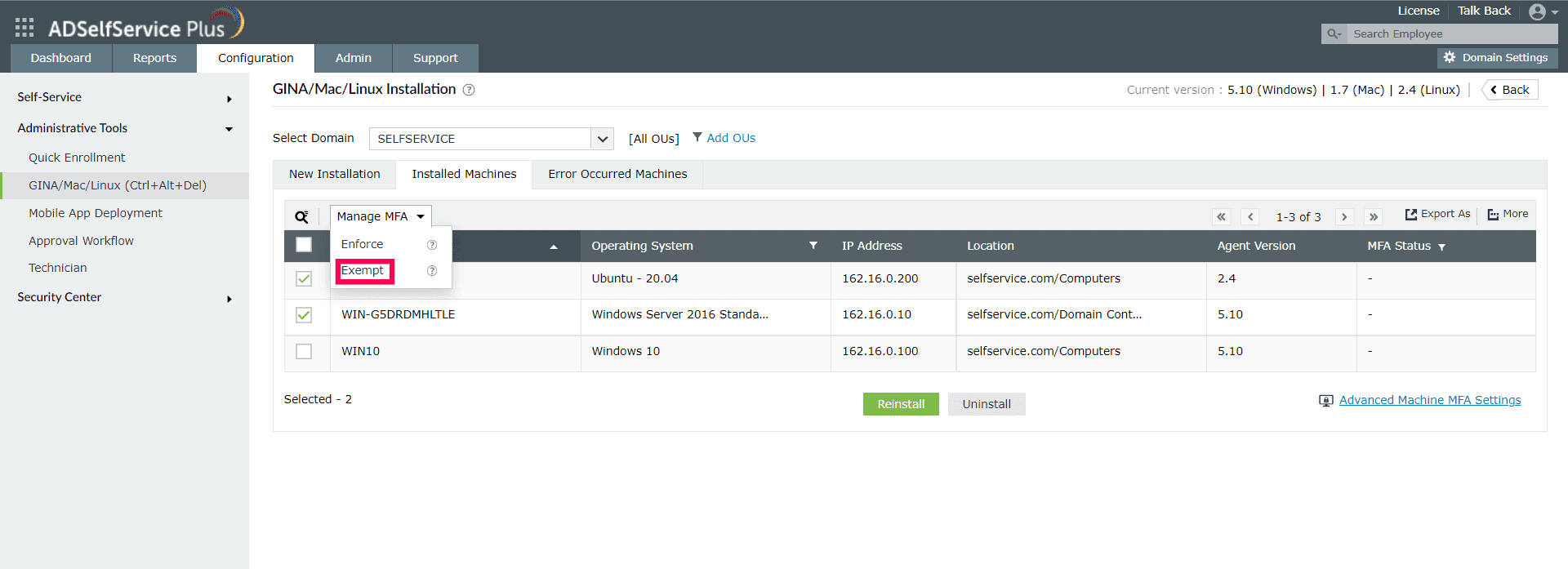
- Click Manage MFA drop-down and select Exempt.
Advanced Machine MFA Settings
ADSelfService Plus allows admins to enable MFA during specific usage scenarios for Windows machines. To request this feature for Mac or Linux, click here.
Note: The Advanced Machine MFA feature requires the Professional edition of ADSelfService Plus with Endpoint MFA. If you do not have these, MFA will be bypassed on Windows machines.
The authenticators in the prompts for the enabled scenarios will be based on the MFA factors configured
in the MFA for Machine Login section. The settings enabled here will be applied to all Windows
machines where the ADSelfService Plus login agent is installed.
Windows MFA settings
- Enable MFA during interactive logons to Windows machines via the GUI:
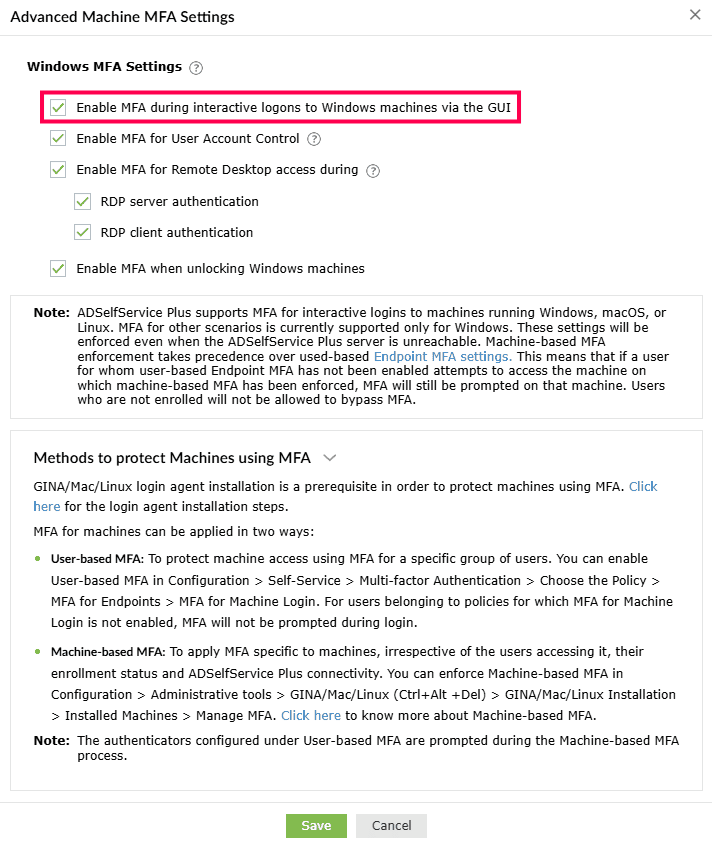
When this setting is enabled, MFA will be required during interactive or GUI-based logins on
Windows machines. Users will be able to perform subsequent actions only upon successful identity
verification.
Note: MFA for interactive logins to Windows servers requires the Professional edition of ADSelfService Plus with Endpoint MFA. If you do
not have these, MFA will be bypassed on Windows servers.
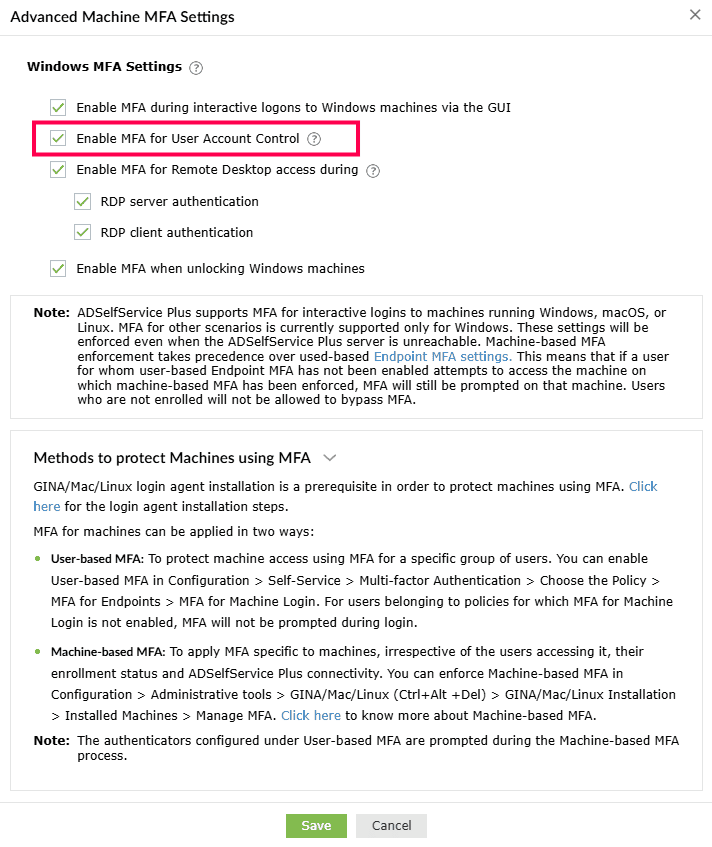
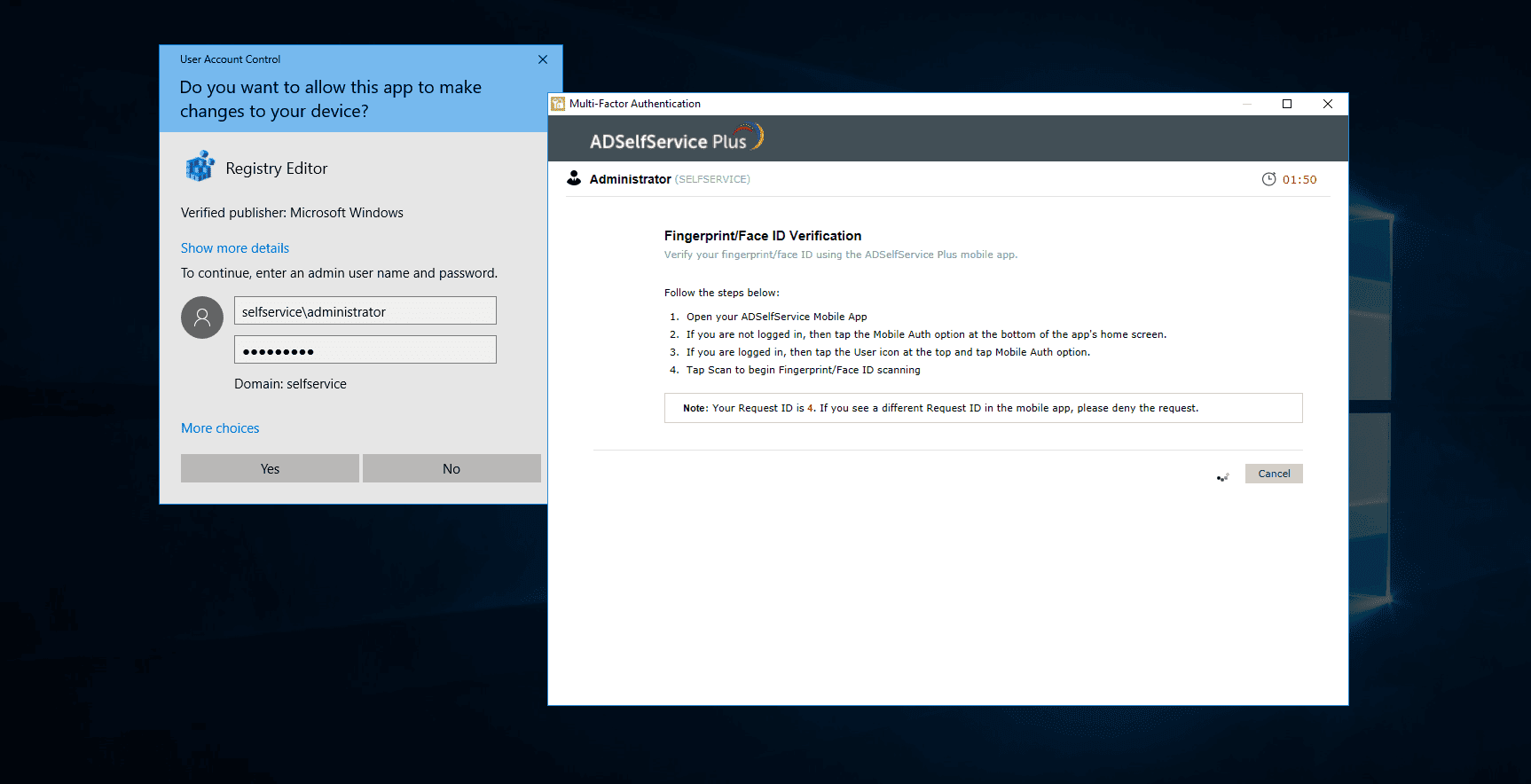
- Enable MFA for User Account Control: This setting enables MFA for all User Account
Control (UAC) credential prompts, and the user will be able to perform the desired action only upon
successful identity verification.
Prerequisite
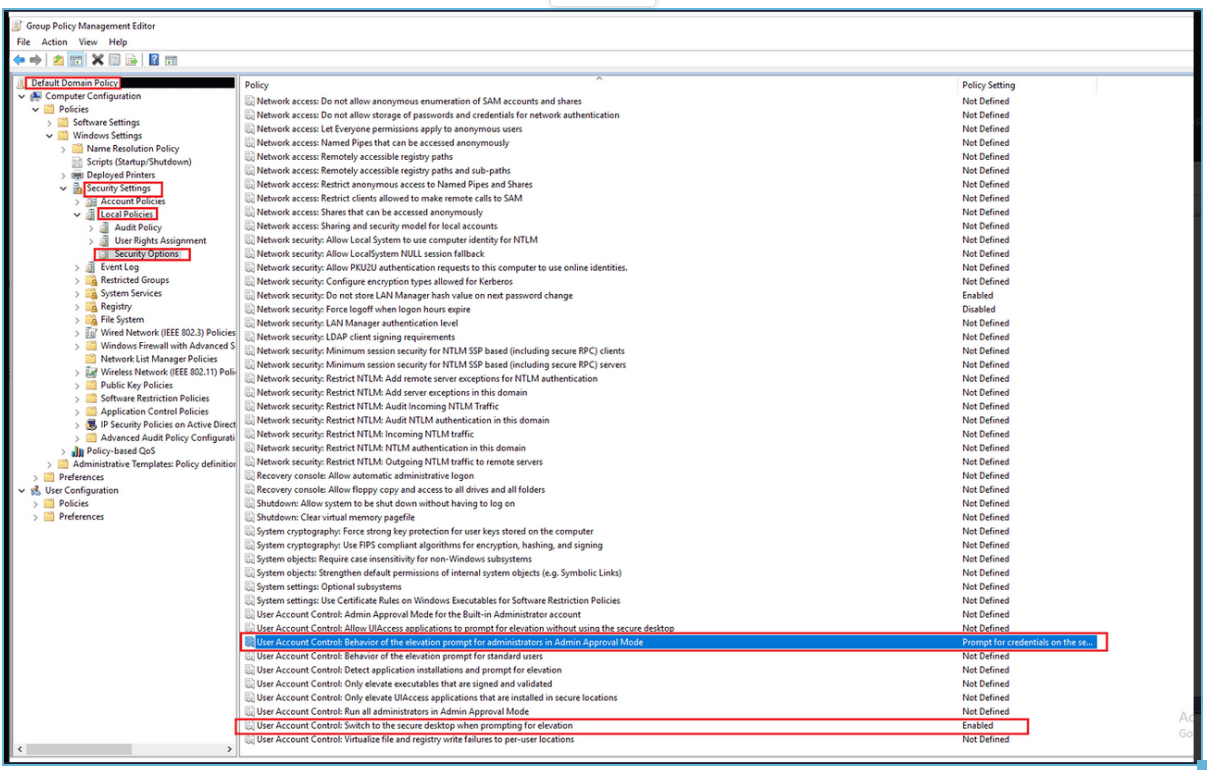
Before configuring MFA for UAC, log into a Domain Controller with Domain Admin privileges, and ensure
the following Group Policy settings are applied to the target computers:
- Open the Group Policy Management Editor (GPMC) and navigate to Computer Configuration >
Windows Settings > Security Settings > Local Policies > Security Options.
- Configure these policy settings:
- User Account Control: Behavior of the elevation prompt for administrators in Admin
Approval Mode → Set to Prompt for credentials on the secure desktop
- User Account Control: Switch to the secure desktop when prompting for elevation →
Set to Enabled
- Once done, enable the Enable MFA for User Account Control option in ADSelfService
Plus.
- This setting is compatible with Windows 7 and later and Windows Server 2008 and later. It is
supported from version 5.10 and above of the ADSelfService Plus Windows login agent.
Note: MFA for UAC on Windows machines requires the Professional edition of ADSelfService Plus with Endpoint MFA. If you do not
have these, MFA will be bypassed on Windows machines.
Note: Actions performed by selecting the Run as a different user
option will not require credentials as prompted for by other UAC actions.
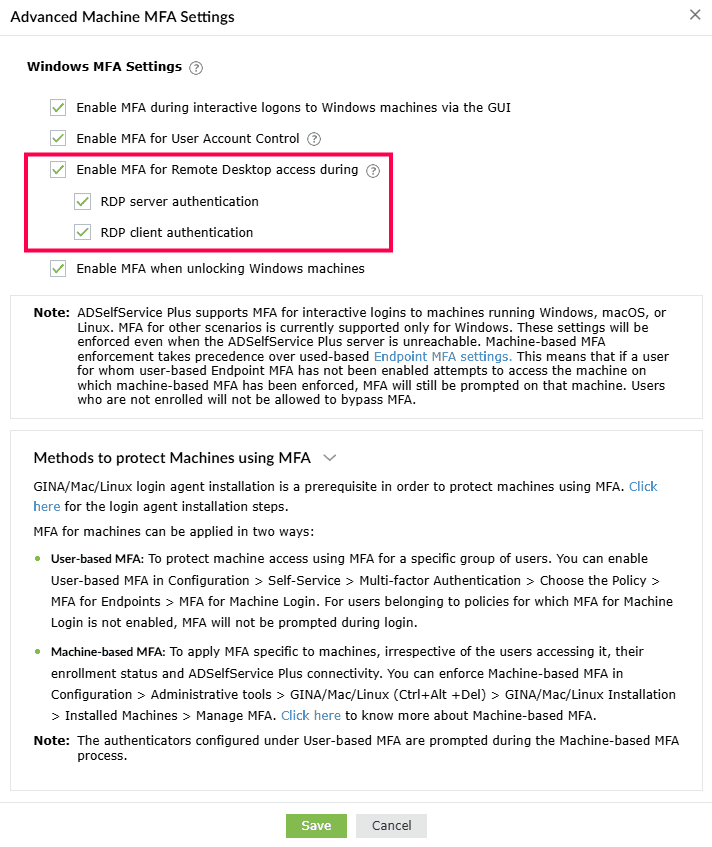
- Enable MFA for Remote Desktop access on Windows machines during: The admin
can configure MFA to be required when establishing connections with machines through the RDP. This
will ensure that RDP connections to machines are secured with an additional layer of authentication.
Note: MFA for RDP access to Windows machines requires the Professional edition of ADSelfService Plus with Endpoint MFA. If you do
not have these, MFA will be bypassed during RDP logins to Windows machines.
There are two ways in which MFA can be configured for Remote Desktop access:
- RDP server authentication: When this setting is enabled, all incoming Remote Desktop
connections to Windows machines where the ADSelfService Plus login agent is installed will
be authenticated and protected using MFA.
- To enable this setting, Select Enable MFA for Remote Desktop access on Windows
machines during and check RDP server authentication.
- RDP client authentication: This setting can be enabled to require MFA for all outgoing Remote Desktop connections from domain-joined machines, via the Windows Remote Desktop application (mstsc.exe) on machines where the ADSelfService Plus login agent is installed.
Note: RDP client authentication is not supported for local users on domain-joined and standalone (workgroup) machines.
Note: Enabling both RDP server and RDP client authentication may
lead to double verification if the ADSelfService Plus login agent is installed on both the
server and client machines. For example, if Google Authenticator is the configured MFA
authenticator, and both RDP server and client authentication are enabled, then the user will
be required to perform identity verification using the code both before and after
establishing a connection with the remote machine.
- To enable MFA for RDP client authentication, log into a Domain Controller with Domain Admin
privileges, and ensure the following Group Policy settings are applied to the target
computers:
- Open the Group Policy Management Editor (GPMC) and navigate to Computer
Configuration > Administrative Templates > Windows Components > Remote Desktop
Services > Remote Desktop Session Host > Security.
- Double-click on Require user authentication for remote connections by using
Network Level Authentication, and check Enabled.
- Click Apply and Save your settings.
To require MFA for Remote Desktop connections in a multi-forest AD environment, there
must be a trust relationship between the two domains. Domain trusts can be added between
forests either through a forest trust (i.e., a trust relationship at the forest level)
or through an external trust (i.e., a trust relationship at the domain level). For steps
to configure a trust relationship, please refer to this document.
Note: With RDP client authentication, you can protect remote
access using MFA only for users accessing the machine from the internet or other public
IP addresses via Remote Desktop Gateway (RD Gateway) by configuring a conditional access
rule with IP restrictions. Learn more about
conditional
access here.
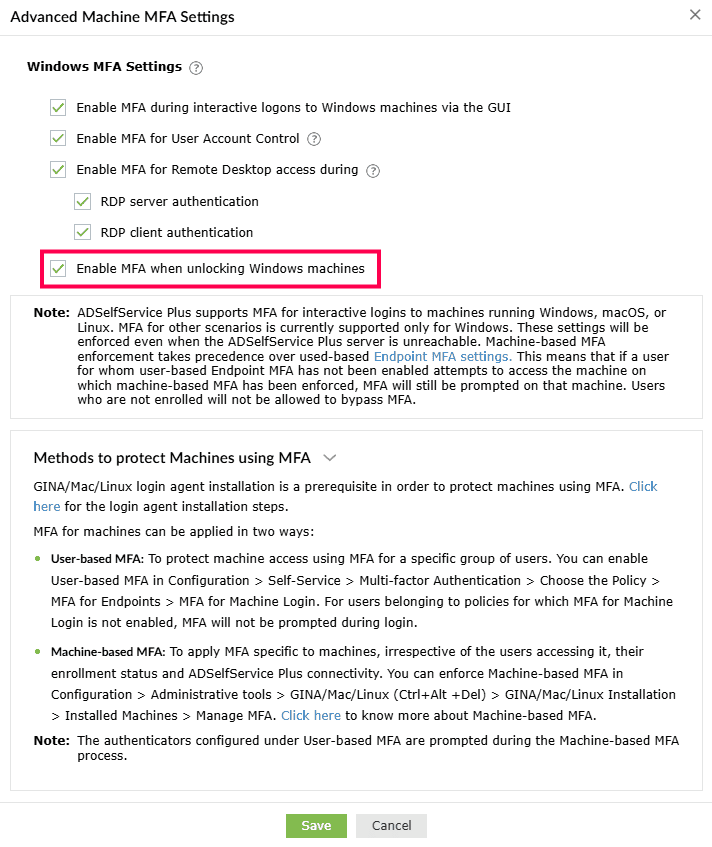
- Enable MFA when unlocking Windows machines: Enabling this setting will
enforce MFA during Windows machine unlocking.
Note: MFA for Windows machine unlocks requires the Professional edition of ADSelfService Plus with Endpoint MFA. If you do
not have these, MFA will be bypassed during Windows machine unlocks.
Don't see what you're looking for?
-
Visit our community
Post your questions in the forum.
-
Request additional resources
Send us your requirements.
-
Need implementation assistance?
Try OnboardPro









