Configuring Duo Security for Active Directory password reset
Duo Security is an access security focused application that is primarily used for multi-factor authentication. One of the ways Duo Security can be used to verify users identities is using passcodes. Here, once the user has provided their username and password successfully, they have to authenticate themselves with Duo Security in one of three ways:
- By entering the passcode they receive via a push notification in the Duo Mobile app,
- By entering the passcode they receive through SMS,
- By answering a phone call received from Duo Security and following the instructions provided.
When an organization implements solutions for self-service actions like Active Directory password reset and account unlock, it intends to increase the users' productivity by allowing them to reset their own password without having to depend on the help-desk. It also aims at reducing the help-desk's workload by exempting them from the huge number of password reset and account unlock tickets that would have been raised otherwise.
While improved user productivity and reduced help-desk workload are results organizations should work towards, security should always be of prime importance. Self-service password resets and account unlocks can turn perilous for user accounts if they aren't completely secure. Implementing MFA with Duo Security and other methods ensures a user's identity is verified before they engage in resetting their password or unlocking their account.
ADSelfService Plus, an Active Directory MFA, self-service password management and single sign-on solution, offers self-service password reset along with multi-factor authentication (MFA).
ADSelfService Plus's Endpoint MFA paired with Duo Security can be used to secure:
- Windows, macOS, and Linux logins.
- Enterprise application logins through single sign-on (SSO).
- Self-service password reset and account unlock
- VPN and OWA logins
The solution supports over 17 MFA methods including Duo Security, Google Authenticator, fingerprint authentication, RSA SecurID, and YubiKey Authenticator. Learn more about ADSelfService Plus and its Multi-factor Authentication feature.
Instructions to configure Duo Security for MFA in ADSelfService Plus
Prerequisite Steps:
- Log in to your Duo Security account (e.g., https://admin-3d5d33c0.duosecurity.com), or sign up for a new one and log in.
- Go to Applications. Click Protect an Application.
- Search for Web SDK. Click Protect this Application.
- Copy Integration key, Secret key and API hostname.
Steps for Duo Security verification:
- Navigate to Configuration → Self-Service → Multi-factor Authentication → Authenticators Setup.
- From the Choose the Policy drop-down, select a policy.
Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy. Only users belonging to OUs and groups in the policy can make use of the self-service feature(s) selected.
- Click Duo Security section.
- In the Integration key field, Enter the Integration Key copied in the Prerequisite step 4.
- In the Security key field, Enter the Secret Key copied in the Prerequisite step 4.
- In the API hostname field, Enter the API Hostname copied in the Prerequisite step 4.
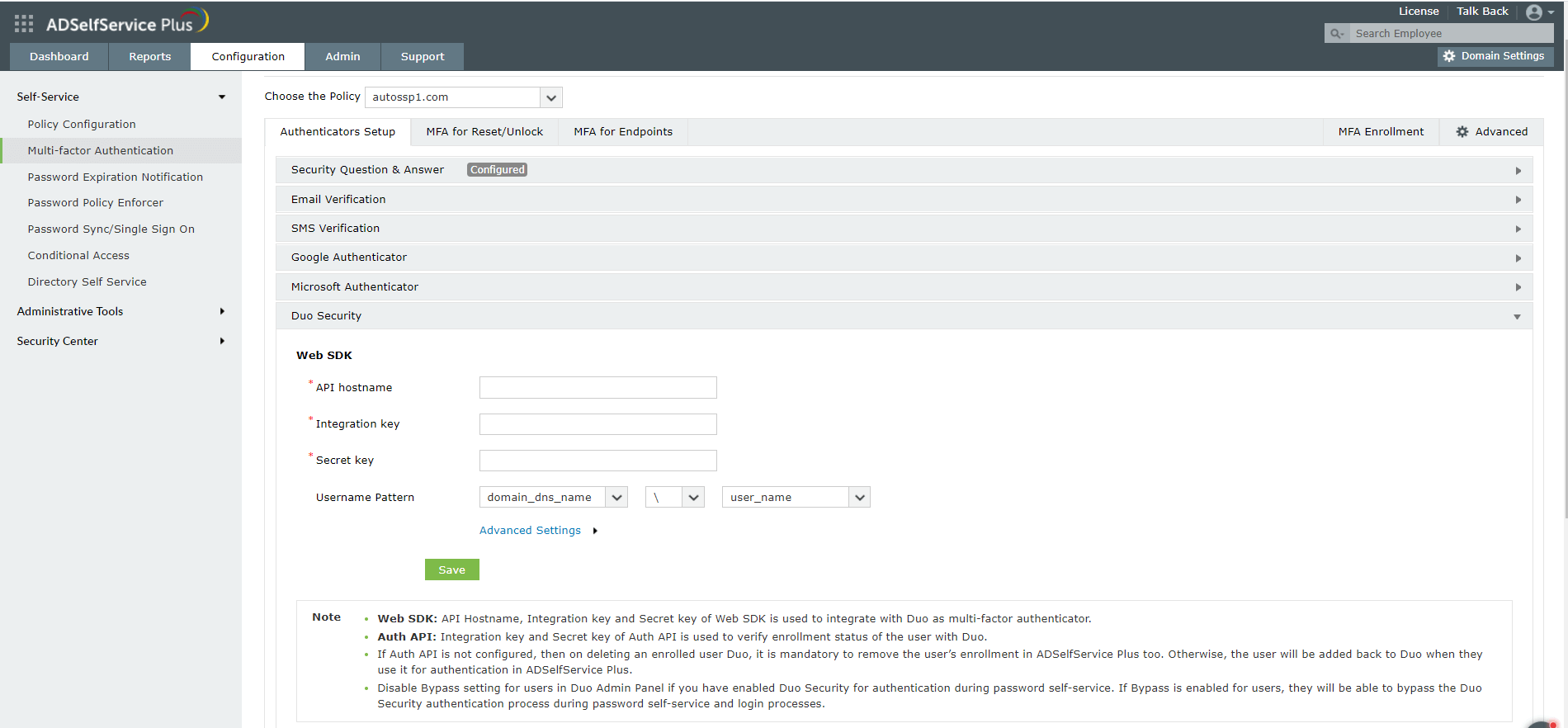
- Click Save.
Enable Duo Security for Active Directory password resets
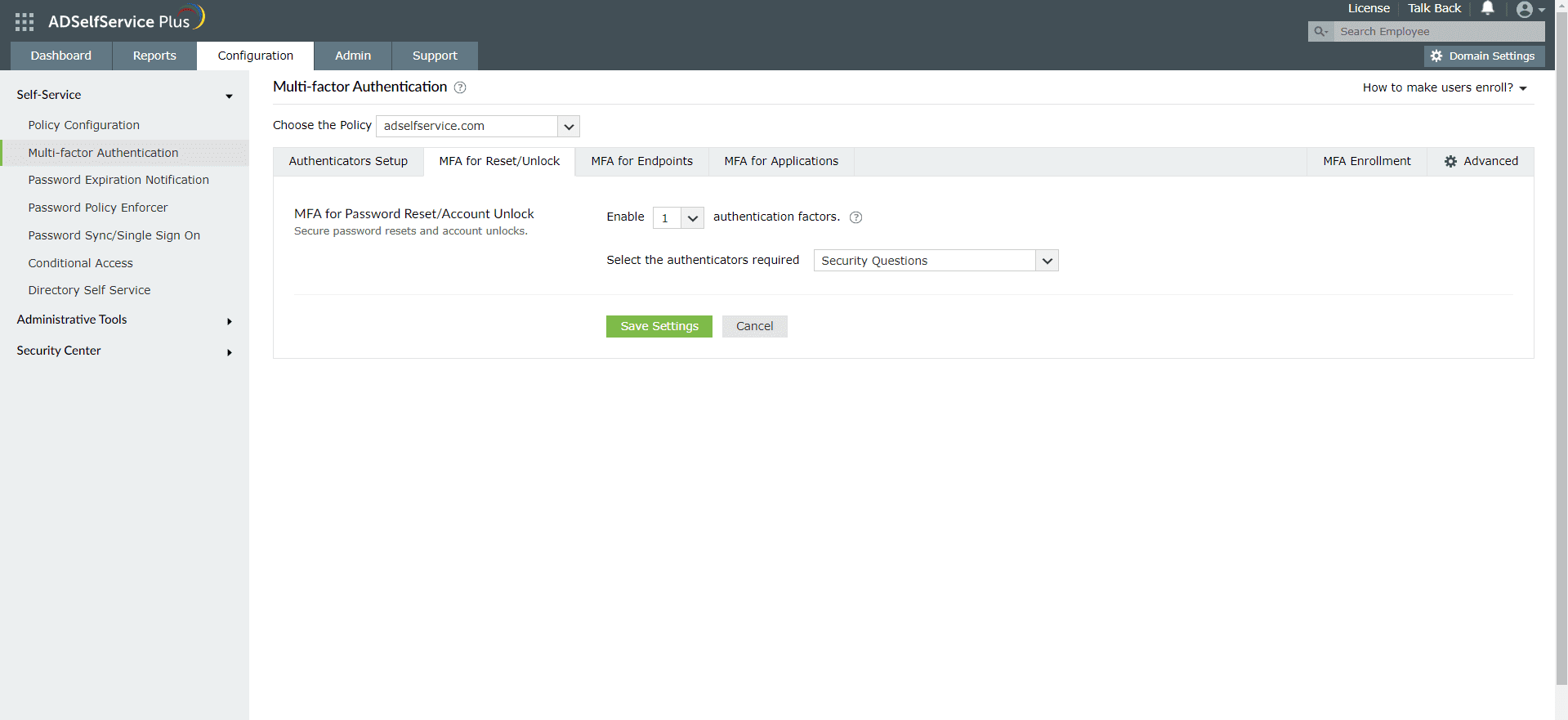
- Go to Configuration → Self-Service → Multi-factor Authentication → MFA/TFA Settings. In the MFA for Reset/Unlock section, enter the number of authentication factors to be enforced, and select Duo Security along with the other authentication techniques to be used.
- Click Save Settings.
Enable Duo Security for Active Directory domain logins
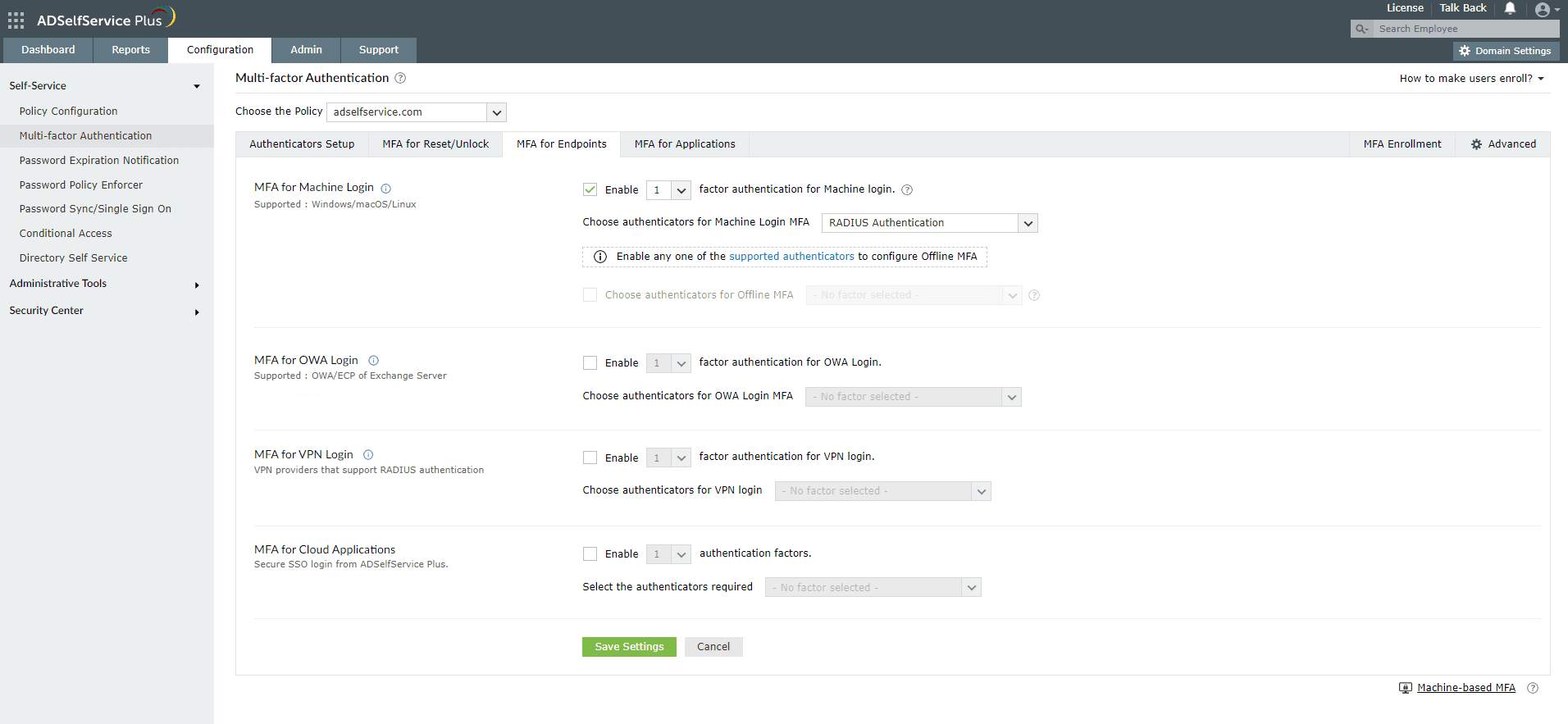
- Go to Configuration → Self-Service → Multi-factor Authentication → MFA for Endpoints.
- Select a policy from the Choose the Policy drop-down. This will determine which authentication methods are enabled for which sets of users.
Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
- In the MFA for Machine Login section, check the Enable _ authentication factors box and select the authentication methods from the drop-down.
- Click Save Settings.
To enable MFA for Active Directory domain logins:
- The ADSelfService Plus login agent must be installed on client machines. Click here for steps on login agent installation.
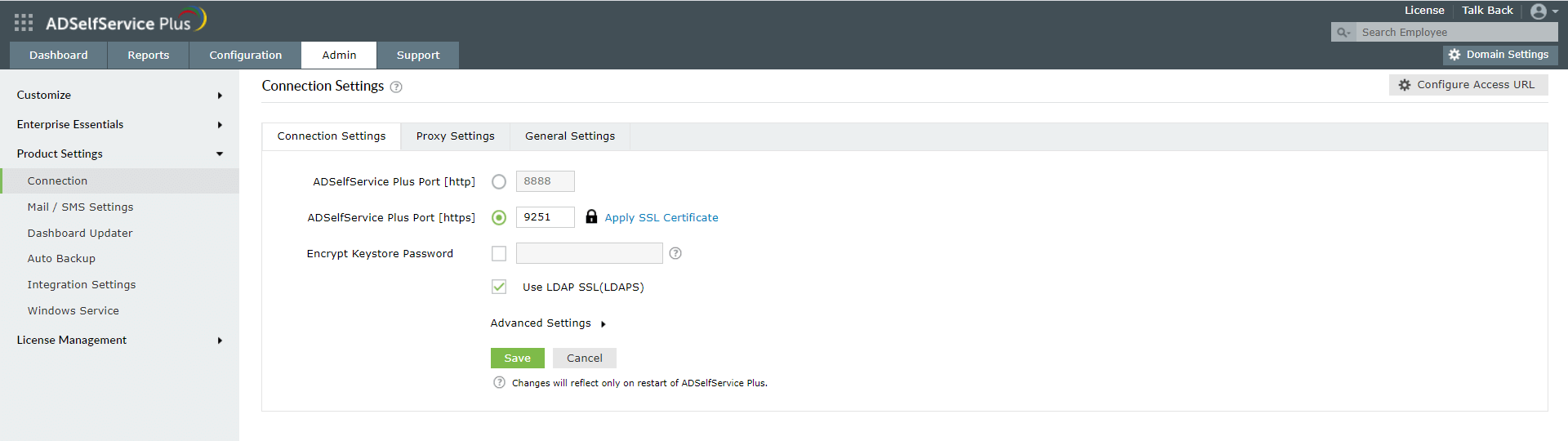
- SSL must be enabled: Log in to the ADSelfService Plus web console with admin credentials. Navigate to the Admin tab → Product Settings → Connection. Select the ADSelfService Plus Port [https] option.
Learn more about ADSelfService Plus and its Multi-factor Authentication feature.
Simplify password management with ADSelfService Plus.
Self-service password management and single sign-on solution
ManageEngine ADSelfService Plus is an integrated self-service password management and single sign-on solution for Active Directory and cloud apps. Ensure endpoint security with stringent authentication controls including biometrics and advanced password policy controls.
- Related Products
