- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
The log data generated by your Apache HTTP server is a goldmine of information. Using this , you can ascertain your server's usage, discoverloopholes in configuration, and improve the web server structure, and overall performance. Auditing your Apache logs e helps in:
- Identifying and correcting errors to enhance user experience.
- Monitoring anomalous activity to investigate it further.
- Understanding your users and how they access your site.
- Preventing cyber attacks.
Analyzing Apache logs with EventLog Analyzer
EventLog Analyzer offers a number of comprehensive features for Apache web server log analysis. With EventLog Analyzer, you can:
- Audit Apache server activity by analyzing its log files with comprehensive reports and graphs.
- Detect suspicious user activity on your Apache web server by monitoring Apache access logs.
- Receive real-time alerts through SMS and email if malicious activities are detected.
- Gain deep insights into your Apache server activity with the help of predefined intuitive reports. This helps you uncover suspicious usage patterns.
- Drill down to the raw data and obtain the required information.
- Import logs from different versions of Apache web servers including Apache Tomcat servers.
Note: EventLog Analyzer supports Apache versions 1.3, 2.0, 2.2, 2.3, and 2.4
Apache web server monitoring
EventLog Analyzer automates the Apache web server monitoring process and helps you efficiently extract required information from your logs with interactive dashboards and reports. With instant alerts, you can discover critical events within the massive volume of log data.
Apache web server management
To manage your Apache web servers, EventLog Analyzer offers automated log file imports, predefined Apache web server reports and alerts, flexible search options, and automatic log archival based on a specified schedule.
Apache access log auditing
Auditing Apache access logs is crucial for monitoring your Apache web servers. Apache access logs contain vital information such as the IP address of the client, the HTTP request, and the timestamp. By keeping tabs on the inbound requests to the Apache web server, malicious user activity can be detected in time to prevent an attack.
Apache web server reports
With EventLog Analyzer's web server reports you can:
- Discover the most frequently occurring errors in your Apache web servers.
- Identify the most popular pages in your website to gain insight into user response.
- See who is accessing your site frequently and learn how they discovered it.
- Investigate the occurrences of any particular error, and its cause using the product's log forensics capabilities.
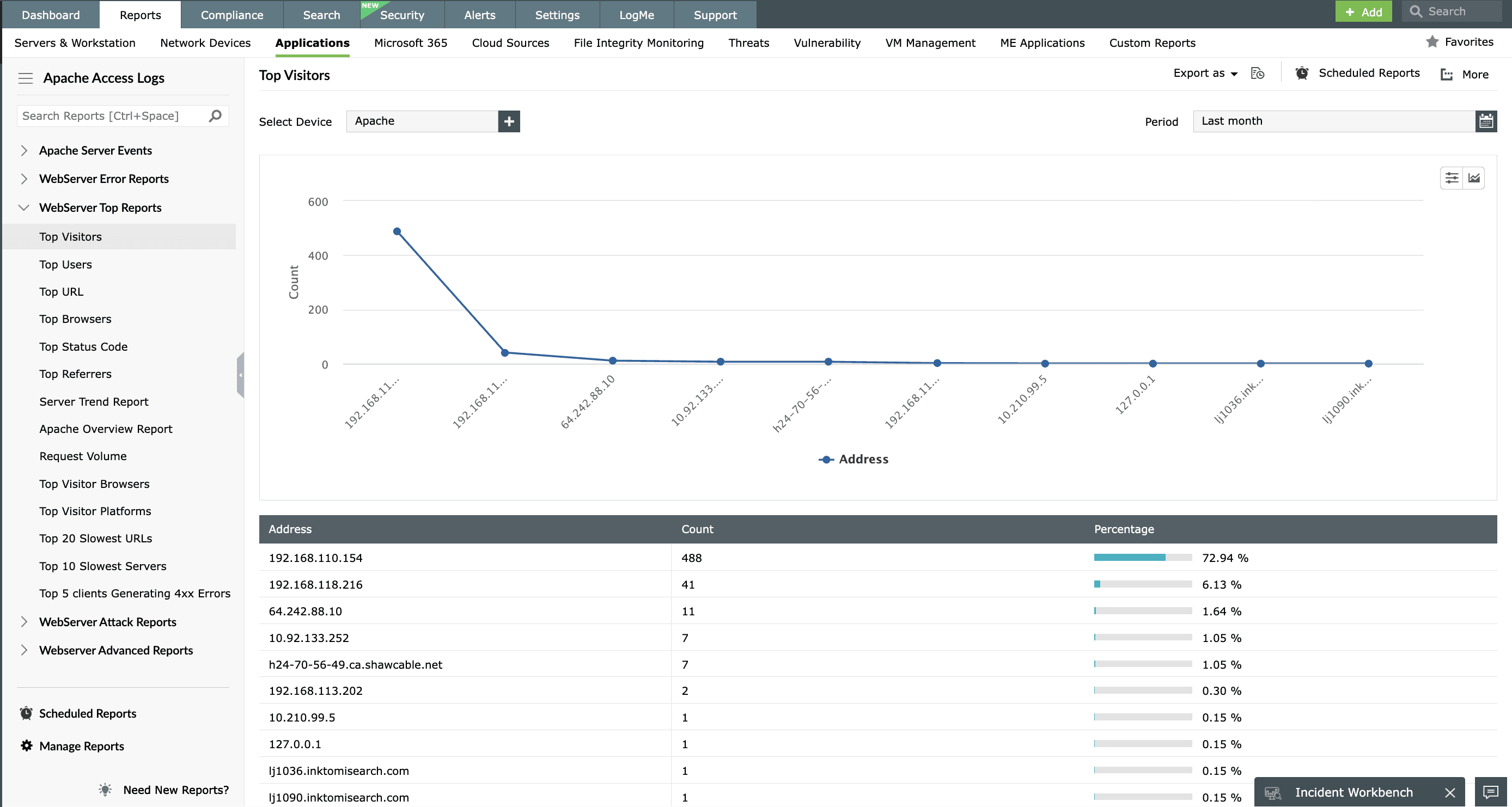
Available Reports
Top Visitors | Top Users | Top URL | Top Browsers | Top Errors | Top Referrers | Apache Server Trend | Apache Reports Overview
Apache web server attack reports
Website administrators should always keep an eye out for common attacks such as SQL injection attacks, malicious URL requests, DDoS attacks and a lot more. EventLog Analyzer can help in mitigating these attacks by monitoring Apache logs in real-time for attacks and instantly notifying IT admins about potential threats.
- Analyzing Apache logs for attacks
- Reporting on occurrences
- Instantly notifying IT admins about potential threats
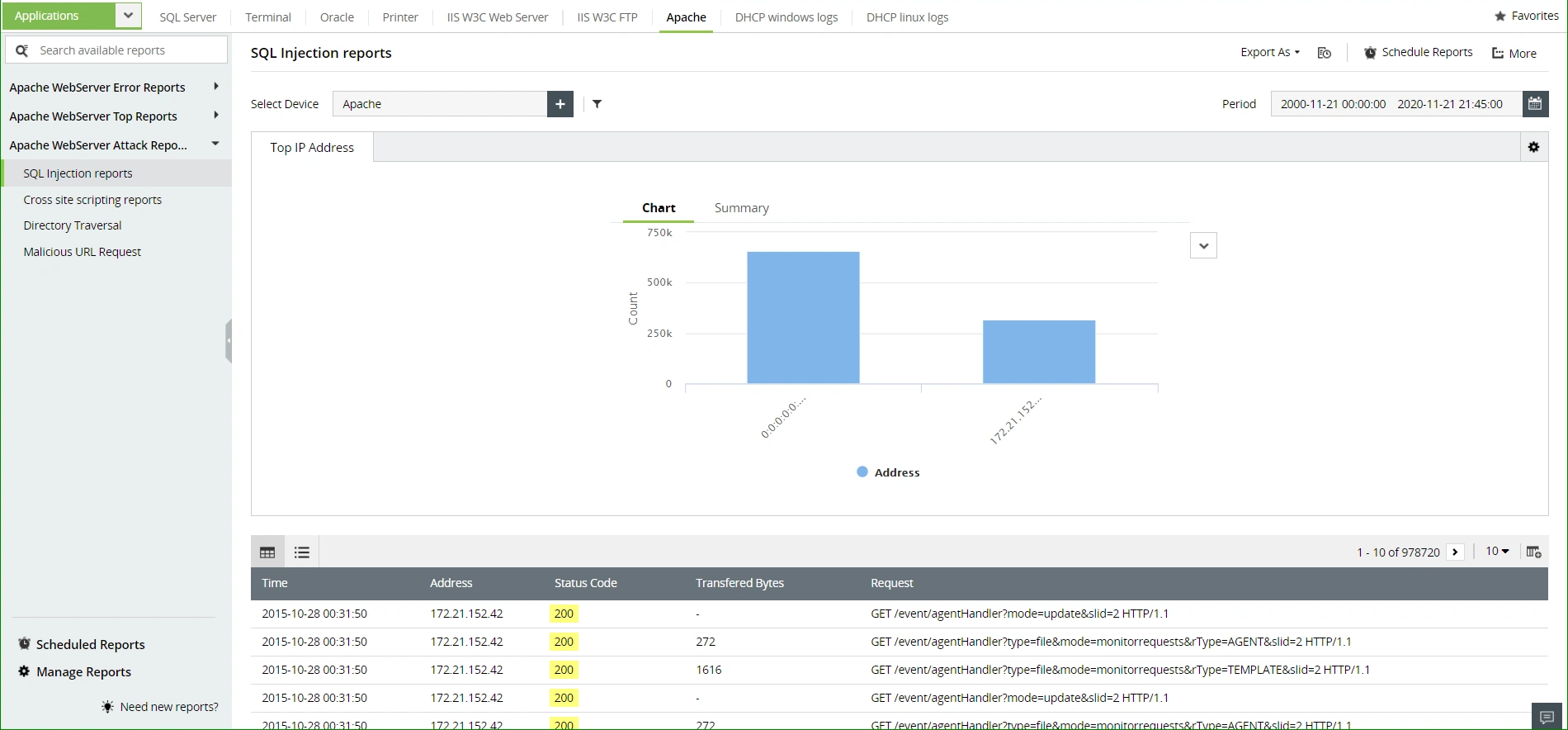
Available Reports
SQL Injection reports | Cross site scripting reports | Directory Traversal | Malicious URL Request
Other features
Syslog management
Collect and analyze Syslog data from routers, switches, firewalls, IDS/IPS, Linux/Unix servers, and more. Get in-depth reports for every security event. Receive real-time alerts for anomalies and breaches.
Windows event log monitoring
Analyze event log data to detect security events such as file/folder changes, registry changes, and more. Study DDoS, Flood, Syn, and Spoof attacks in detail with predefined reports.
IT compliance management
Comply with the stringent requirements of regulatory mandates viz., PCI DSS, FISMA, HIPAA, and more with predefined reports & alerts. Customize existing reports or build new reports to meet internal security needs.
Active Directory Log Monitoring
Monitor all types of log data from Active Directory infrastructure. Track failure incidents in real-time and build custom reports to monitor specific Active Directory events of your interest.
Privileged user monitoring
Monitor and track privileged user activities to meet PUMA requirements. Get out-of-the-box reports on critical activities such as logon failures, reason for logon failure, and more.
Print Server Management
Monitor and audit print server with detailed reports on documents printed, attempts to print documents without proper permission, failed print jobs and their causes, and more.
Need Features? Tell Us
If you want to see additional features implemented in EventLog Analyzer, we would love to hear. Click here to continue












