The North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) plan strives to improve the security framework of a vast power-grid system in the United States, several provinces in Canada, and one state in Mexico. With ManageEngine EventLog Analyzer, you can seamlessly monitor your Bulk Electric System (BES) cyber assets and fulfill NERC compliance. The solution securely collects and automatically analyzes logs from all the entities of your network and provides predefined reports for various compliance laws, including the NERC CIP.
See how EventLog Analyzer simplifies NERC compliance management
Track firewall activities
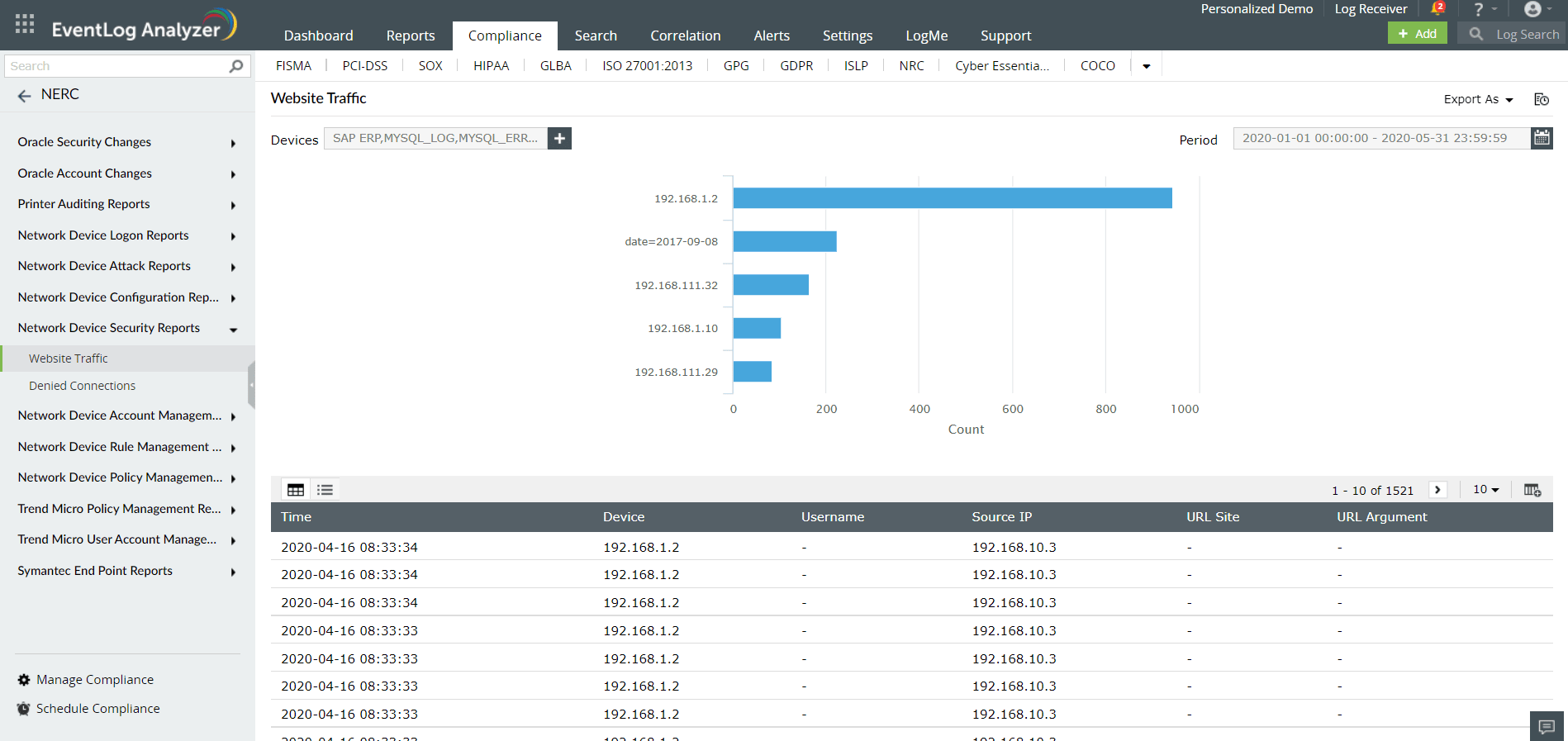
Section CIP 005-6 R1.5 of NERC CIP mandates organizations to monitor inbound and outbound traffic. EventLog Analyzer serves as a firewall log analyzer that offers visibility into the source and type of traffic communicating with your organization's network.
The log management solution generates reports based on the traffic information from allowed and denied connections with sources, destinations, protocols, and ports along with timestamps. You can also gain a better understanding of your network activities with logons, configuration changes, user account changes, and traffic details. This also enables you to comply with section CIP 007-6 R1.1 by monitoring enabled ports.
Monitor user access to critical sources
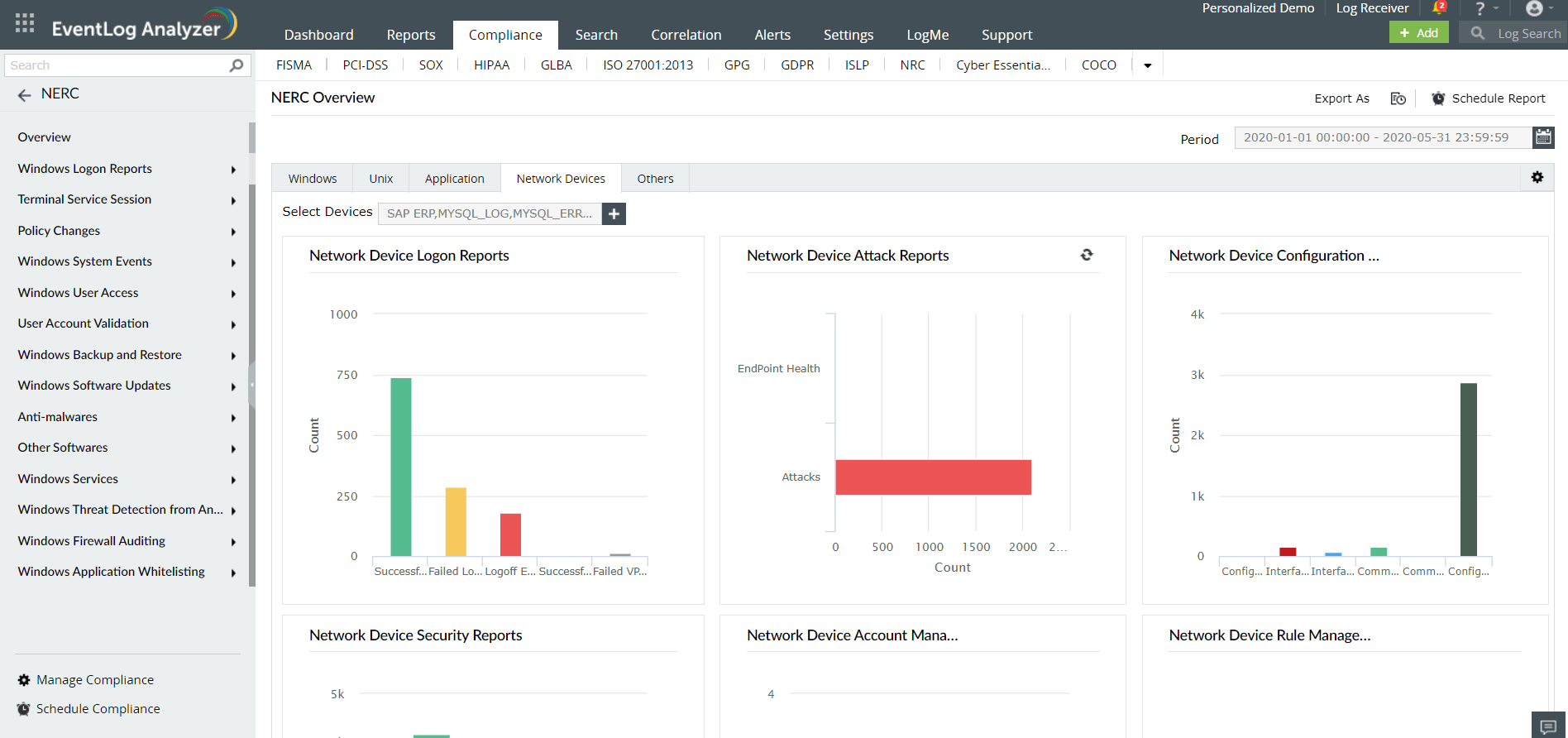
You can satisfy sections CIP 007-6 R5.3 and CIP 007-6 R4.1 of NERC compliance with EventLog Analyzer's user session monitoring. The compliance management solution monitors network logs to detect system and data misuse by auditing the user activity on the network.
The user activity monitoring will provide precise information on critical events, such as user logons, user logoffs, failed logons, successful audit logs cleared, audit policy changes, objects accessed, and user account changes.
Audit privileged user activities
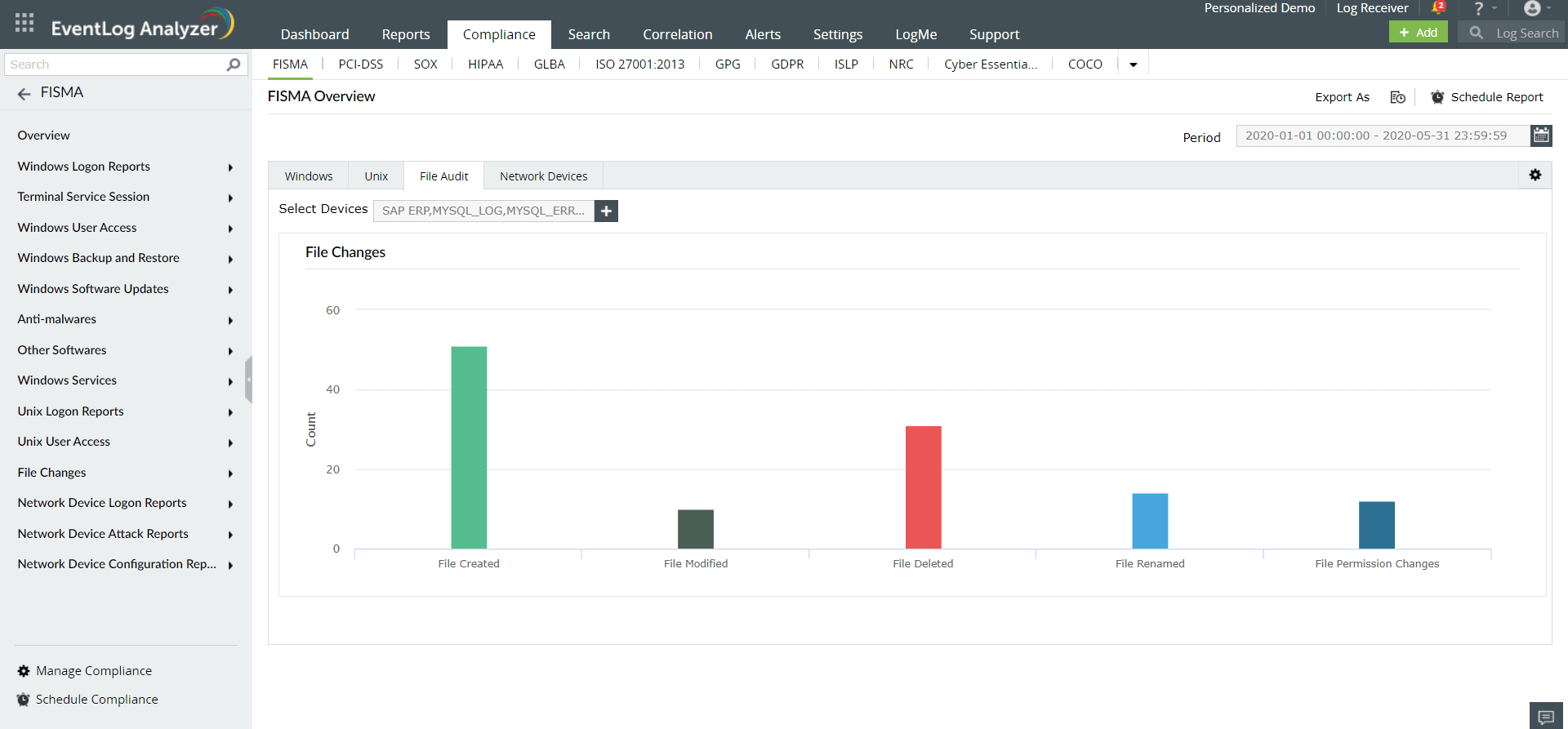
Monitor privileged users who have unrestricted access to critical applications, servers, and databases. EventLog Analyzer's privileged user auditing reports enable you to highlight any form of privilege abuse in your network. It also indicates creation or removal of user profiles and the escalation of user privileges. You will comply with NERC's section CIP 007-6 R5.3 by monitoring these activities.
Actively respond to breaches
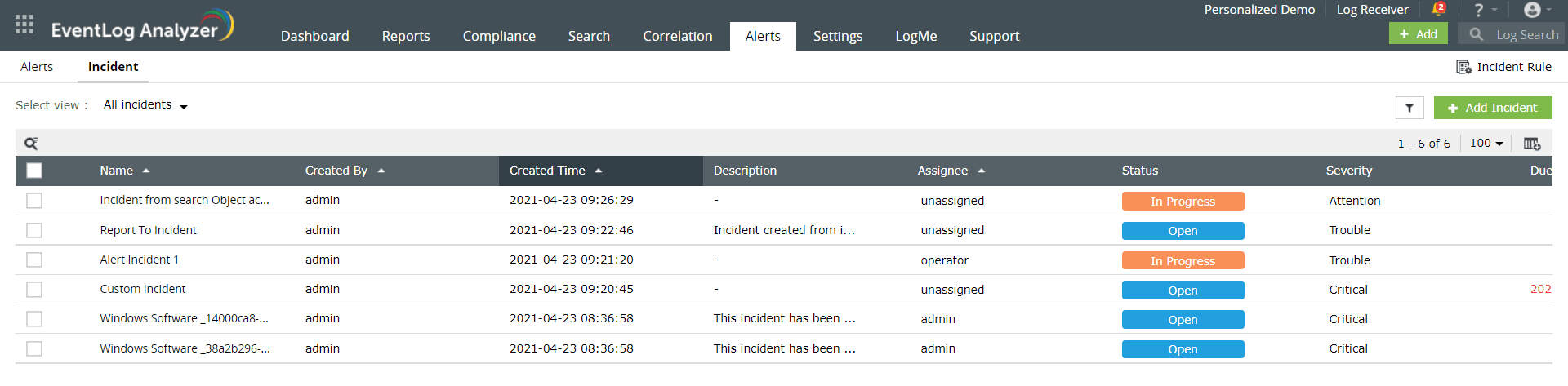
Adhere to NERC CIP's section CIP 007-6 R3.1 by detecting security breaches as and when they occur with alerts that are sent instantly. The integrated incident management system in EventLog Analyzer identifies and handles security incidents effectively by assigning tickets to security administrators and alerting them via SMS or email to expedite the response time. You can also integrate EventLog Analyzer with your external help desk software, such as BMC Remedy Service Desk, Jira Service Desk, Kayako, ManageEngine ServiceDesk Plus, ServiceNow, and Zendesk. You can assign, manage, and track the progress of incoming incidents.
Extensive compliance support
Similar to NERC CIP, EventLog Analyzer offers out-of-the-box support for prominent regulatory mandates across industries, including PCI-DSS, HIPAA, SOX, FISMA, the GDPR, as well as regulations recently enacted and enforced across the globe. The solution monitors every entity of your network to satisfy all the relevant sections and generate compliance-ready reports. It also notifies you with a real-time alerting system whenever a compliance breach is detected. This helps you improve response time and promptly respond to data breaches.
Other solutions offered by EventLog Analyzer
File Integrity Monitoring
Track activities such as creation, modification, and deletion on your files and folders. Receive instant alerts when any suspicious activity is detected.
Learn more
Privileged user management
Audit privileged user activity and spot suspicious events, such as multiple logon failures, unauthorized logons, and attempts that deviate from normal access patterns.
Learn more
Application log monitoring
Audit web server applications, databases, and DHCP applications, generate reports to identify anomalous user activities, troubleshoot application crashes, and detect security threats.
Learn more
Log analysis
Detect anomalies, monitor critical security events, and track user behaviors with predefined reports, intuitive dashboards, and prompt alerts.
Learn more
5 reasons to choose EventLog Analyzer as your NERC compliance solution
Comprehensive log management
NERC emphasizes the importance of monitoring firewall and activities. EventLog Analyzer provides out- of- the- box support for prominent firewall vendors like Barracuda, Sonicwall, pfSense, Palo Alto Networks, and Fortinet. Additionally, the solution supports over 750 other log sources for complete network log management.
Learn more
In-depth auditing and reporting
Audit all the BES cyber assets in your network and obtain a detailed overview on what's happening in the network in the form of intuitive dashboards. The solution also comes with compliance-ready reports for prominent regulatory mandates, including NERC.
Learn more
A powerful correlation engine
NERC mandates that organizations detect network anomalies and trace security threats. EventLog Analyzer's powerful correlation engine holds over 30 predefined correlation rules, and detects known malicious patterns by analyzing activities across the network.
Learn more
Automated incident management
Implement a reliable system to detect and prevent malicious activity in your network. The solution has an integrated incident response and management console that assigns tickets when critical security events are detected to speed up incident resolution.
Learn more
Augmented threat intelligence
Ensure that no malicious source enters your network with the advanced threat intelligence feed. Detect malicious IP addresses, URLs, and domain interactions with the built-in global IP threat intelligence database and STIX/TAXII feed processor.
Learn more
Frequently asked questions
-
What is NERC CIP compliance?
NERC CIP stands for North American Electric Reliability Corporation Critical Infrastructure Protection. It is a regulatory framework designed to ensure the reliability of the North American bulk power system by protecting critical infrastructure, known as Bulk Electric System (BES) cyber assets, from cyberattacks.
The compliance applies to any organization that owns or operates a part of the bulk power system, including electric power producers, distributors, transmission owners and operators, and other entities within this industry.
-
How does EventLog Analyzer assist with the different standards of NERC?
| NERC sections |
Actions required |
What EventLog Analyzer accomplishes |
| CIP 005-6 R1.3 |
Restrict access to critical network devices like firewall.
Document accesses to these sources.
|
- User account validation
- Logon and logoff monitoring
- Account management
- Policy change tracking
|
| CIP 005-6 R1.5 |
Monitor inbound and outbound traffic with IDS and firewall system. |
- Logon reports
- Endpoint health and attack auditing
- Configuration management
- Rules management
|
| CIP 007-6 R1.1/ CIP 007-6 R4.2 |
Configure firewall to open only the ports needed. Others should be restricted.
Monitor enabled ports.
|
- Firewall auditing
- Allowed and denied connections report
- Rules management
- Policy management
|
| CIP 007-6 R3.1 |
Implement a system to detect and prevent malicious activity in your network. |
- System event monitoring
- Threat detection
- Application whitelisting
- Incident response and management
|
| CIP 007-6 R4.1/ CIP 007-6 R5.7 |
Record and monitor successful and failed logins across the network.
Mechanisms to limit the number of unsuccessful attempts and alert when threshold passes
|
- User account validation
- Terminal server sessions
- Logon and logoff monitoring:
- Network devices
- Windows
- Unix
- SQL server
- Oracle database
|
| CIP 007-6 R5.3 |
Monitor users with access to shared documents. |
- User account validation
- Endpoint reports
- File activity monitoring
- Privileged user monitoring
- Account management
- Policy management
- Rule management
- Network device security reports
|
| CIP 009-6 R1.3 |
Information crucial for the recovery of BES should be backed up and stored with one or more processes |
- System events report
- Backup and restore
- Service status reports
|
-
What is the difference between the NERC and the FERC?
The NERC is a non-profit organization that was formed in 1968 with the mission of ensuring reliable operation of the continent's bulk power system. The US Federal Energy Regulatory Commission (FERC) is an independent agency that regulates the transmission and wholesale sale of electricity, natural gas, and oil.
The NERC is responsible for developing and maintaining standards for reliability and security of the North American bulk power system, while the FERC focuses on regulating interstate commerce.
-
What are the NERC Reliability Standards?
The NERC Reliability Standards are the rules that help utilities make sure the grid is reliable, and these standards are updated every two years to meet the evolving requirements of the industry.
The NERC Reliability Standards cover seven areas:
- Asset management and planning
- Reliability evaluation and assessment
- Reliability monitoring and measurement
- System security and assurance
- Resource adequacy and capacity adequacy
- Distribution planning and operations
- Event response planning
-
How does the NERC standards relate to data security?
The NERC standards are a set of requirements for the protection of critical infrastructure. The NERC standard is voluntary, but it has been adopted as a regulatory requirement for the power-grid infrastructure in the United States, Canada, and a part of Mexico. The compliance standards focus on physical and cybersecurity. It also includes guidelines on how to protect against cyberattacks, data security, and the management of data.
Here's how the sections of the NERC compliance ensures organizations to prioritize data security:
- Regular assessments on their facilities and systems to ensure their ability to resist cyberattacks.
- Development of plans to respond to a cyberattack or other malicious event. These plans must include procedures for responding to different types of attacks, including malware infections, unauthorized access attempts, denial-of-service attacks, and other malicious activities.
- Following specific procedures for dealing with information about critical infrastructure during an emergency response situation or disaster recovery process.
Manage logs effectively and stay compliant.
EventLog Analyzer helps you meet various regulatory mandates by auditing. managing, and analyzing logs.

























