SOX compliance software helps organizations to automate and manage the requirements of the Sarbanes-Oxley Act (SOX) act to ensure financial transparency and reduce fraud risks.

The Sarbanes-Oxley Act (SOX) mandates that publicly traded U.S. companies prove their financial accountability through robust internal controls. The core challenge for IT is providing a continuous, tamper-proof audit trail for every access attempt and change made to the systems that manage financial data.
Under the Sarbanes-Oxley Act (SOX), executives who certify false financial reports can face fines up to $5 million, imprisonment of up to 20 years, and companies risk delisting from public stock exchanges for material non-compliance.
Log360 delivers auditing and reporting capabilities for SOX compliance, tracking user activity, policy changes, and access controls to ensure financial data integrity and audit readiness.
Log360 transforms complex SOX requirements into actionable security controls, enabling organizations to maintain continuous compliance while protecting financial data integrity.
Here's how Log360 helps with complying to SOX mandates:
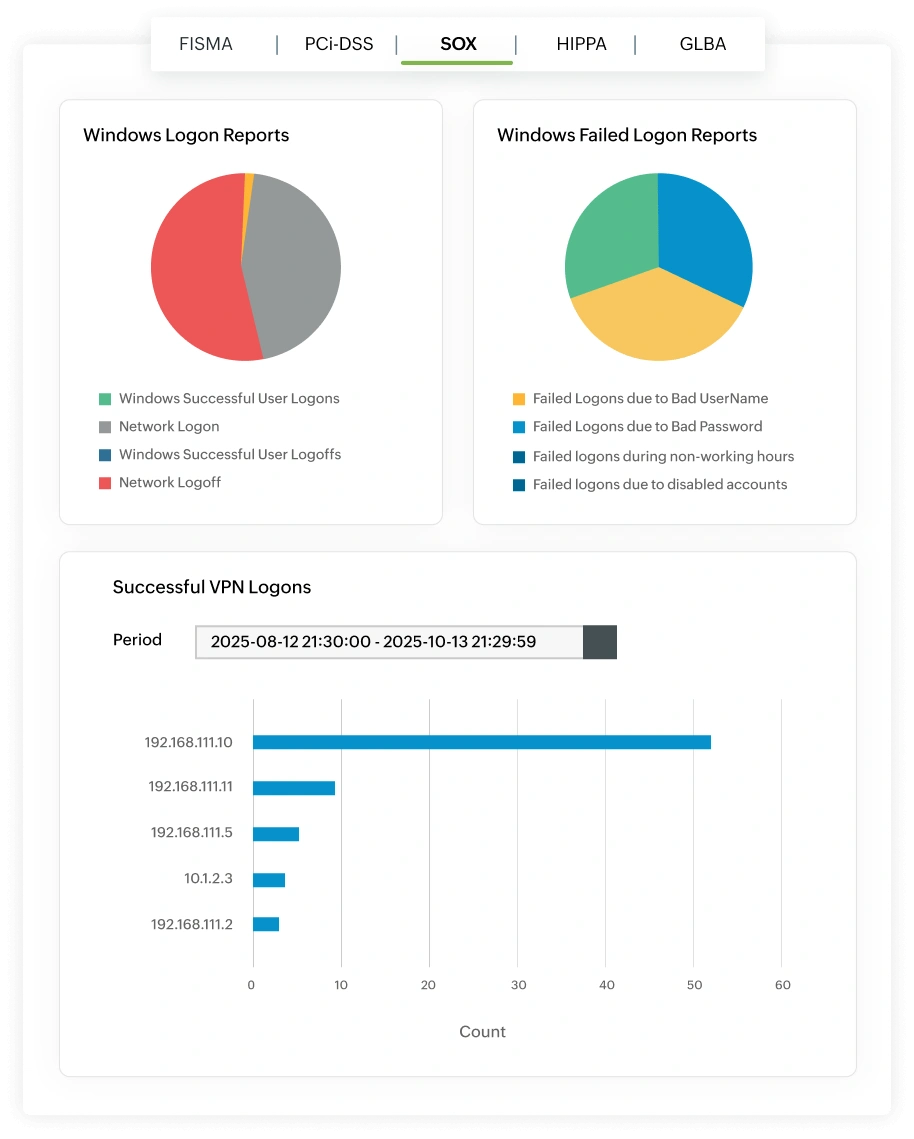
Unauthorized access or manipulation of financial data can compromise reporting integrity and violate SOX controls. Log360 helps mitigate this risk by continuously monitoring every logon, logoff, and privileged access event across your network to identify anomalies that could signal fraud or internal control failures.
You’ll know instantly if an administrator accesses financial systems outside business hours, a terminated user account remains active, or multiple failed logins indicate a brute-force attempt . With complete visibility into remote sessions, VPN activity, and concurrent logins, Log360 enables proactive detection and documentation of suspicious access patterns.
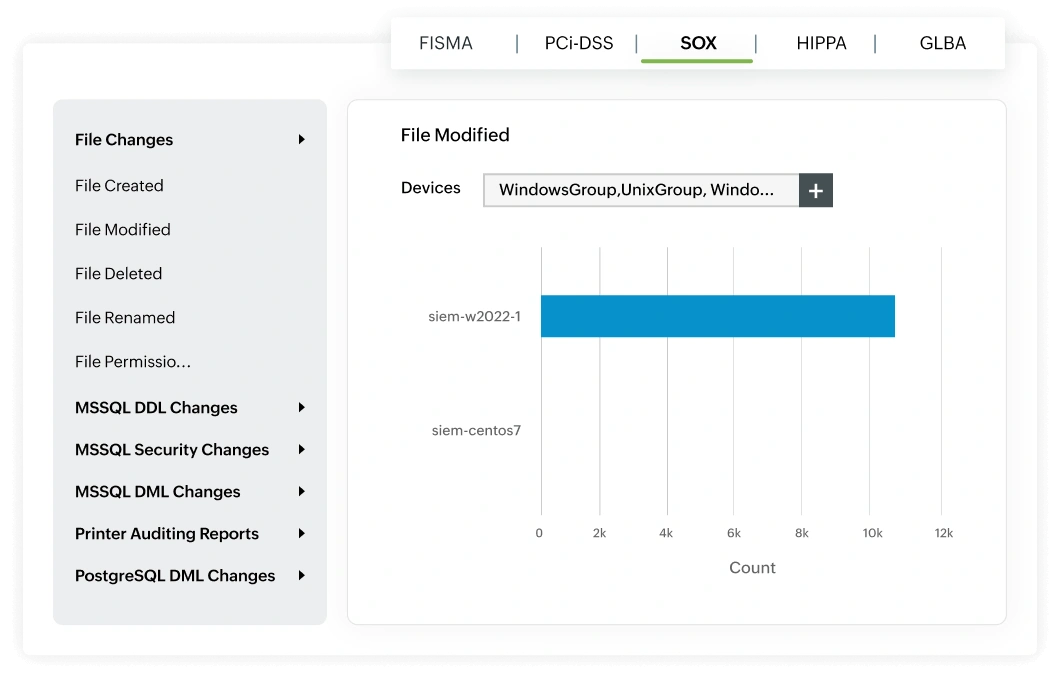
Maintaining the integrity of financial information is a core SOX requirement. Log360's file integrity monitoring (FIM) module strengthens internal controls by capturing every access, modification, or deletion event involving critical financial files and audit records.
The solution builds a complete picture of each activity, who made the change, from which system, what was altered, and whether it aligns with approved business processes. It's real-time alerts notify you the moment financial statements are edited without authorization, transaction logs are erased, or audit trails are tampered with. This continuous visibility not only deters fraudulent behavior but also ensures you have forensic-grade evidence to support audits and investigations.
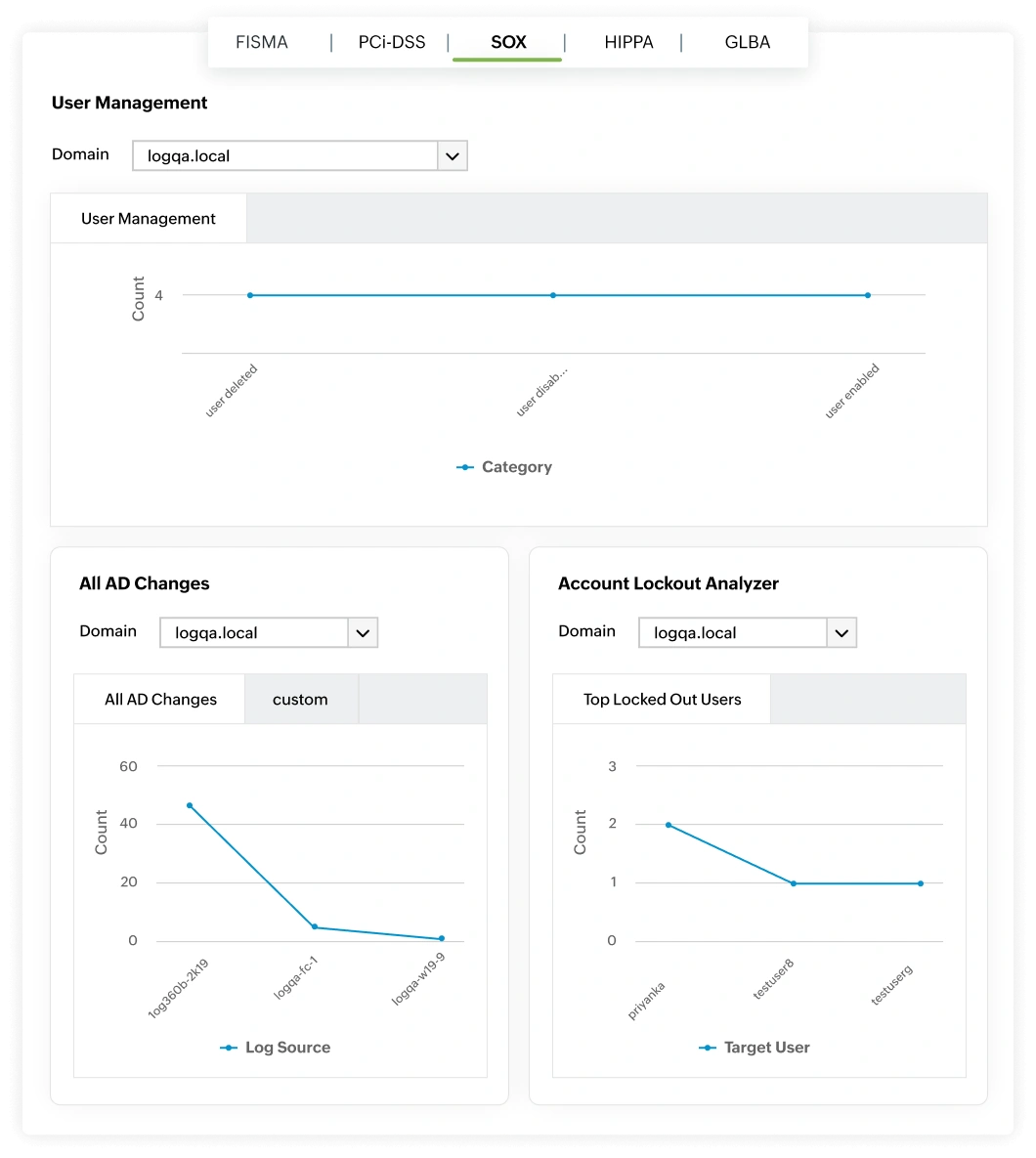
Weak or misconfigured access controls can open the door to fraud and SOX control violations. Log360 helps track policy updates, GPO changes, and group modifications to detect deviations from approved access baselines.
Automatic alerts flag violations that compromise segregation of duties or least privilege. Periodic access review reports provide clear visibility into who has access to what, supporting streamlined audits and ongoing SOX compliance.
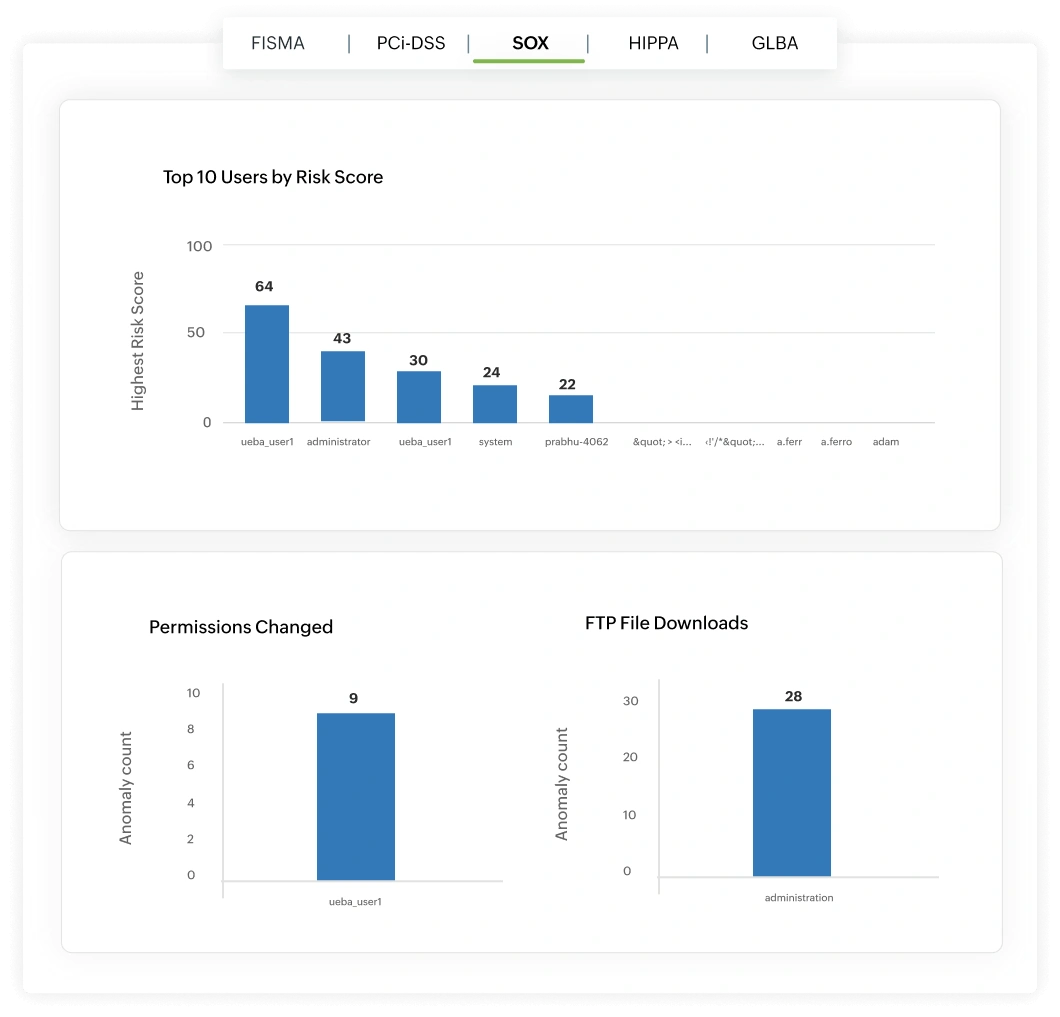
Log360 simplifies Segregation of Duties (SoD) enforcement by monitoring every privilege changes, policy updates, sensitive AD modifications, and user actions that touches financial systems.
The solution's UEBA baselines help identify role-based anomalies, surface events such as unauthorized privilege elevation, cross-functional access, or users executing conflicting tasks. By correlating access entitlements with financial system activity and providing audit-ready reports, Log360 ensures that SoD violations are detected early and backed by complete forensic context.
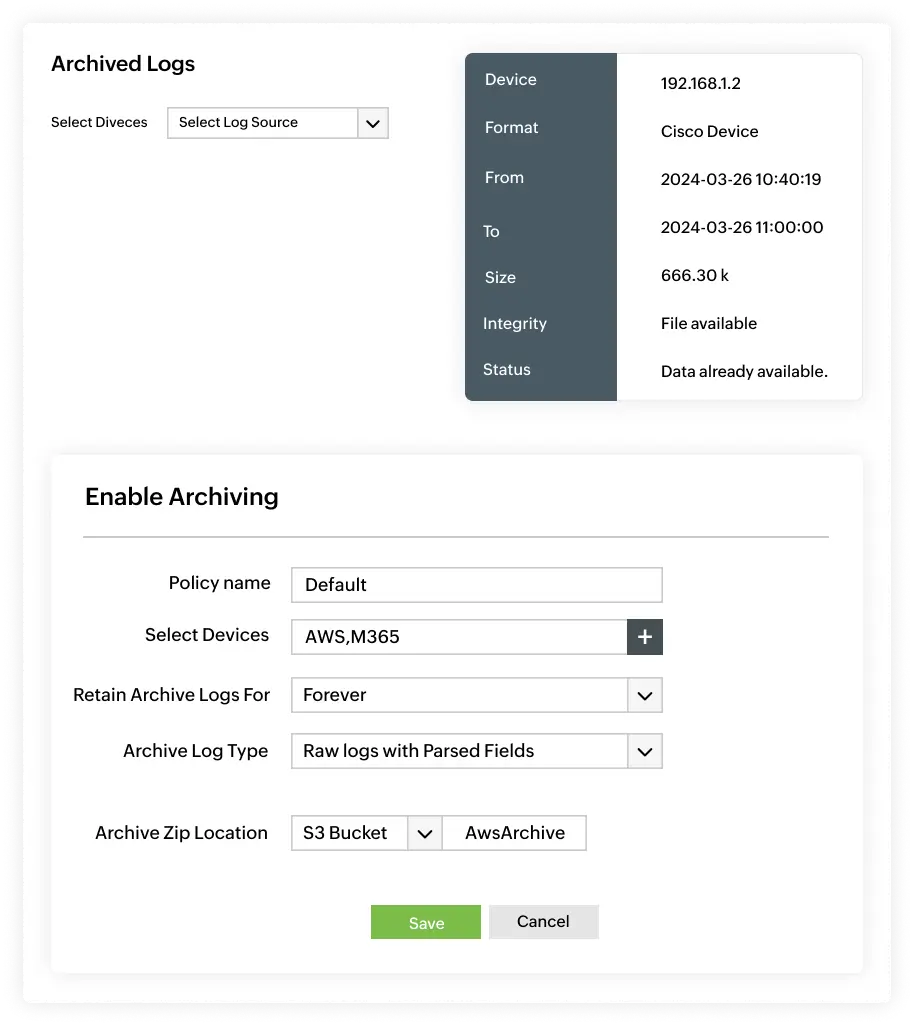
Meeting SOX retention requirements requires more than just storing logs and ensuring integrity, it also demands they are reliably retained and easily accessible when needed. Log360’s archive management ensures every log is protected for seven-year retention requirement with cryptographic verification and role-based access controls.
Easily configure retention periods by log type, and let expired records be purged automatically. When needed, search years of archived data instantly for forensic investigations, trend analysis, or compliance verification, making audits simpler and more reliable.
Log360 simplifies compliance by streamlining log collection, mapping reports to regulations, alerting you to violations before they become risks, and more.
Here's how Log360 simplifies your compliance journey with popular mandates in practice:
Continuously collect and correlate log data from all critical systems to build comprehensive audit trails automatically.
Learn moreGet instantly notified of emerging threats, indicators of compromise, and suspicious activities flagged through global threat feeds and correlation with your network events.
Learn moreGenerate audit-ready SOX compliance reports instantly with detailed evidence and control assessments.
Learn moreDetect and mitigate advanced threats in real-time with 2,000+ cloud-delivered detection rules to identify complex, multi-stage attacks such as privilege escalation, SQL injection, and data exfiltration attempts.
Learn moreGet complete incident timelines with real-time updates, helping administrators understand attack sequences and implement defense mechanisms for future threats.
Learn moreProtect your organization from audit failures by ensuring complete visibility into IT controls that impact financial reporting. With a modern SOX compliance tool like ours, you can continuously validate internal controls, detect gaps, and maintain audit readiness.
SOX compliance software helps organizations to automate and manage the requirements of the Sarbanes-Oxley Act (SOX) act to ensure financial transparency and reduce fraud risks.
SOX applies to all publicly traded companies in the U.S., their subsidiaries, and foreign companies listed on U.S. stock exchanges. It also covers public accounting firms that audit these companies, their officers, directors, auditors, attorneys, and other agents who work with financial reporting.
SOX compliance centers on five critical sections that establish corporate accountability, internal controls, and employee protections:
The many challenges when implementing SOX compliance includes failing risk-based approaches, complex documentation, mis-coordination with auditors, and outdated processes. Log360 addresses these through centralized log management, automated compliance reporting with pre-built templates, real-time alerts for suspicious activities, and comprehensive audit trails that demonstrate regulatory adherence.
SOX compliance for smaller public companies (small reporting companies or SRCs) differs mainly in reduced requirements: they must comply with Section 404(a) (management’s internal control assessment) but are generally exempt from Section 404(b) (auditor attestation), lowering audit costs and regulatory burden. This eases compliance compared to larger firms but still requires strong internal controls to protect investors.
SOX mandates financial reporting accuracy for public companies, ensuring investor trust through strict internal controls and audits. SOC, governed by AICPA, focuses on evaluating service providers' controls over security, availability, and data privacy. Both enhance organizational trust but serve distinct compliance objectives.
Our solutions undergo rigorous third-party audits to ensure compliance with the same global security and privacy standards we help you achieve.

Maintain a single source of truth for everything SOX-related from automated evidence collection and instant compliance reports to security monitoring, incident response, and real-time notifications, all within one console.