- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
System Monitor (Sysmon) is a Windows logging add-on that offers granular logging capabilities and captures security events that are not usually recorded by default. It provides information on process creations, network connections, changes to file systems, and more. Analyzing Sysmon logs is essential to spot malicious activities and security threats.
ManageEngine EventLog Analyzer, a powerful log management solution, can centrally collect and monitor Sysmon logs from all Windows and Linux devices to ensure endpoint security.
How does EventLog Analyzer help in monitoring and analyzing Sysmon logs?
Upon receiving logs from devices that have Sysmon installed in them, EventLog Analyzer automatically generates out-of-the-box reports that provide detailed information on critical events in the form of intuitive graphs and charts.
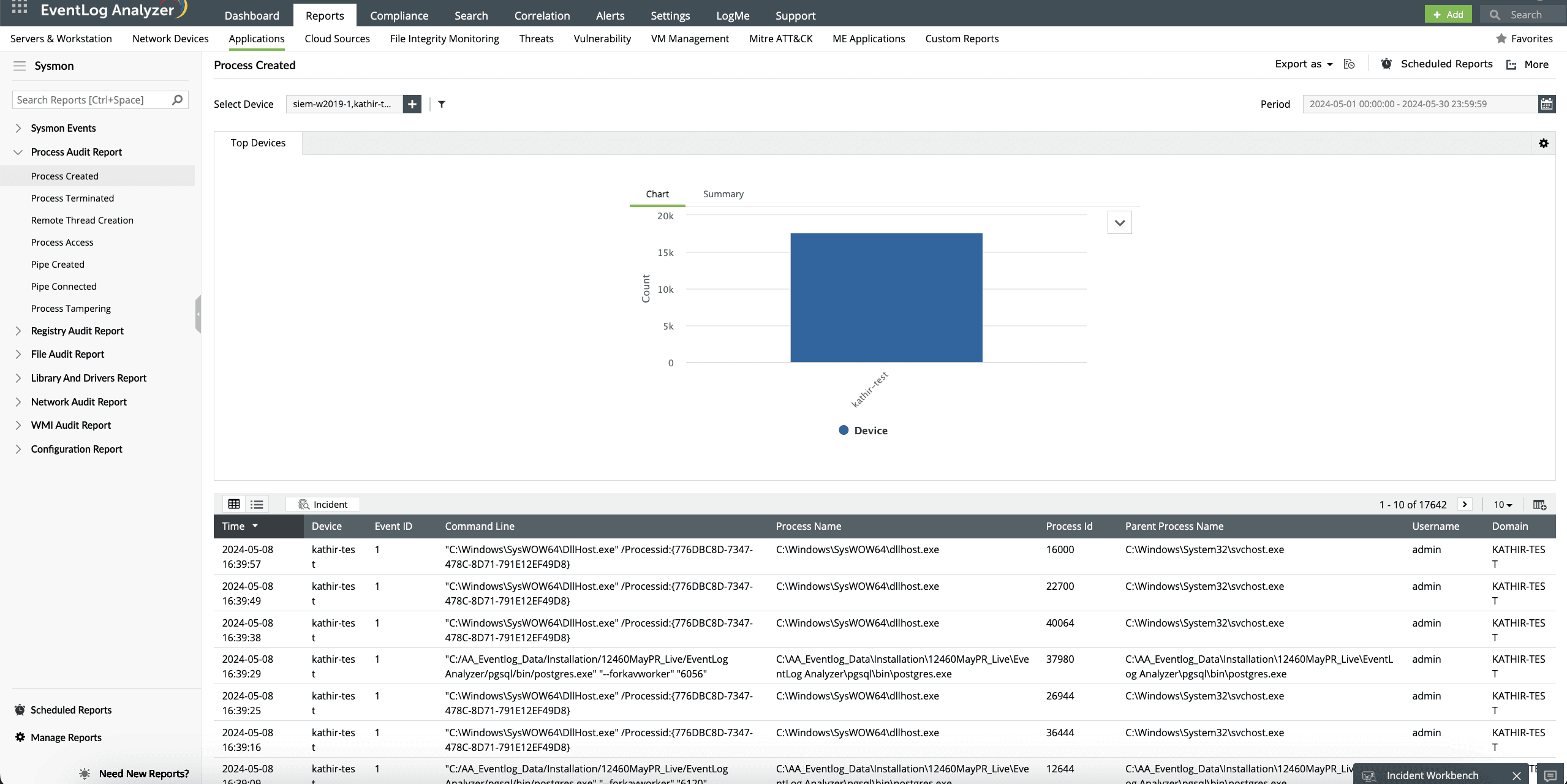
Monitor process creations to spot suspicious installations
EventLog Analyzer helps you keep track of various processes, including processes that are currently running as well as processes that have been terminated. Apart from the process name, you can also view additional information about the process such as the process ID, the parent process name, and the process command line. By correlating this information with threat feeds, you can spot malicious software installations or malware attacks.
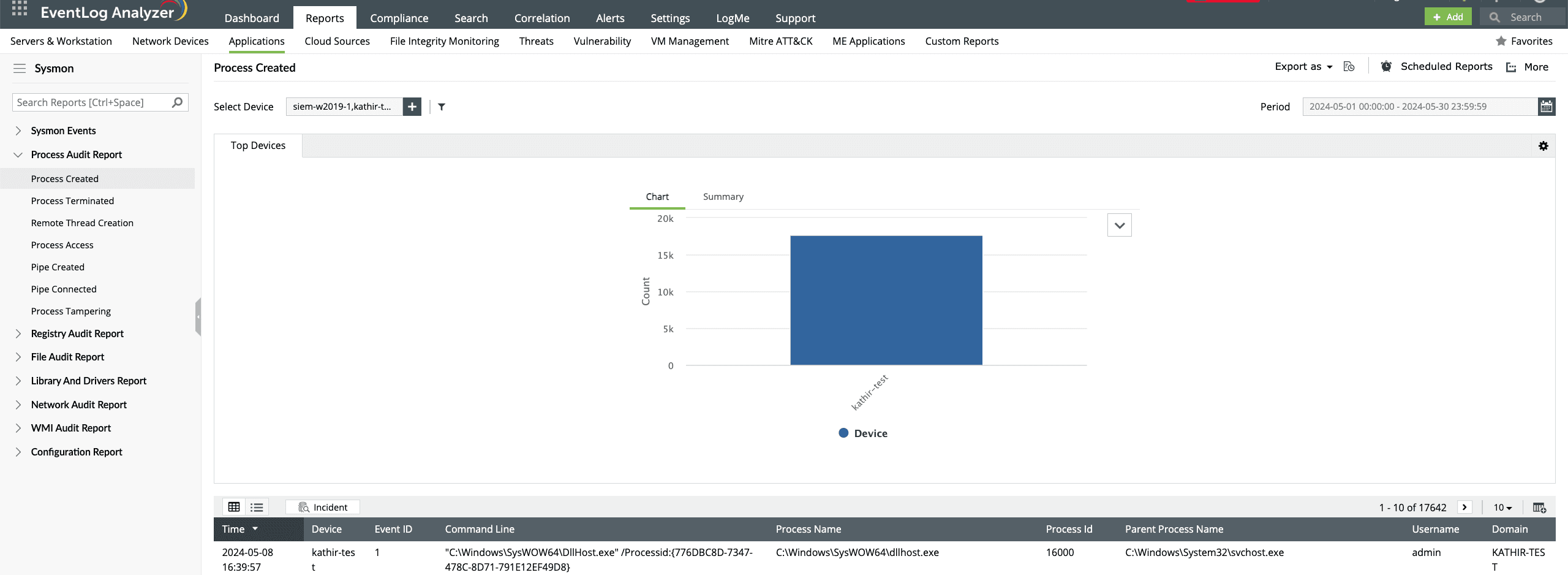
Spot, investigate, and stop malware
EventLog Analyzer can help you detect and investigate various techniques employed by malware. For instance, malware usually modifies file creation timestamps to cover its tracks. With EventLog Analyzer's file audit reports, you can analyze file modifications in real time. Another common technique used by malware includes using named pipes for inter-process communication. EventLog Analyzer's process audit reports can help you monitor Sysmon event logs generated when a pipe is created or connected.
Detect privilege escalations to stop unauthorized data access
By integrating EventLog Analyzer with the MITRE ATT&CK framework, you can analyze Sysmon logs to discover malicious activities like privilege escalation attacks. For instance, by monitoring process creations, you can detect attackers who try to bypass User Access Control mechanisms to elevate process privileges in a system.
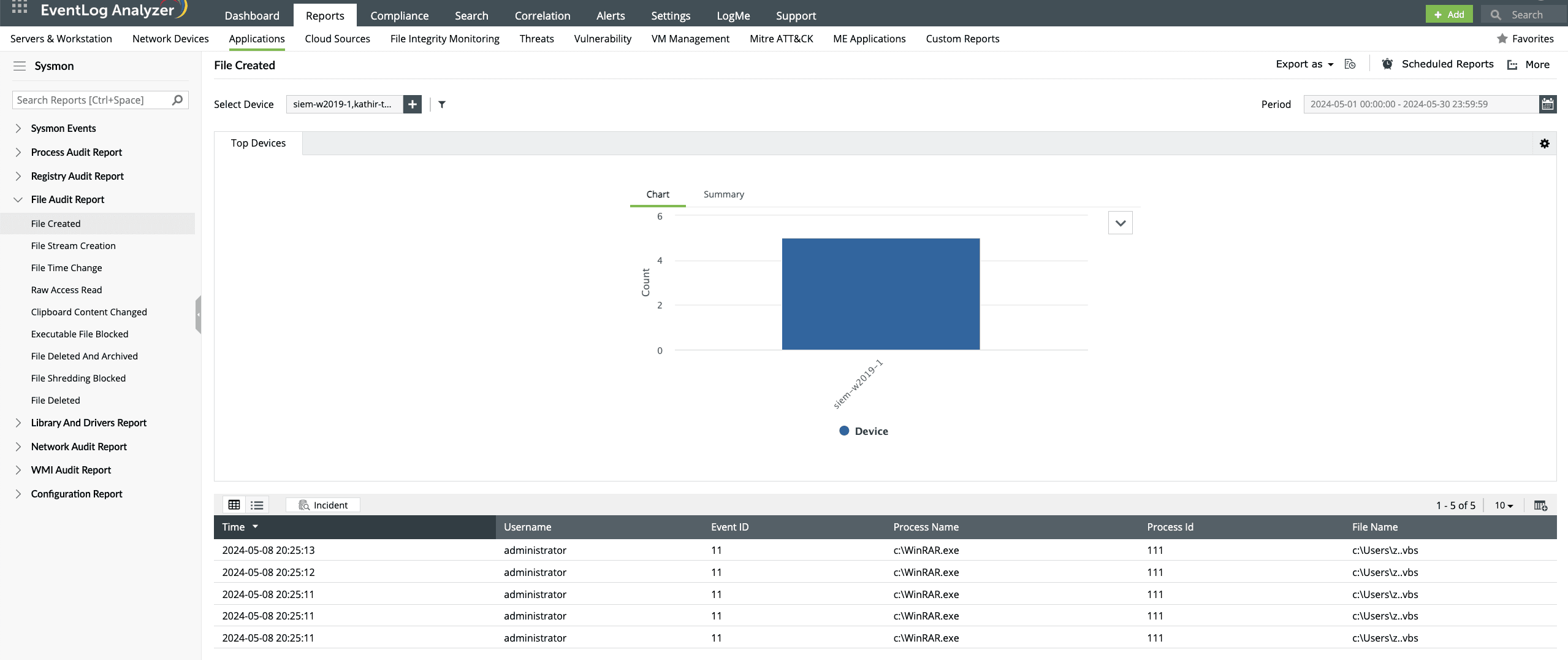
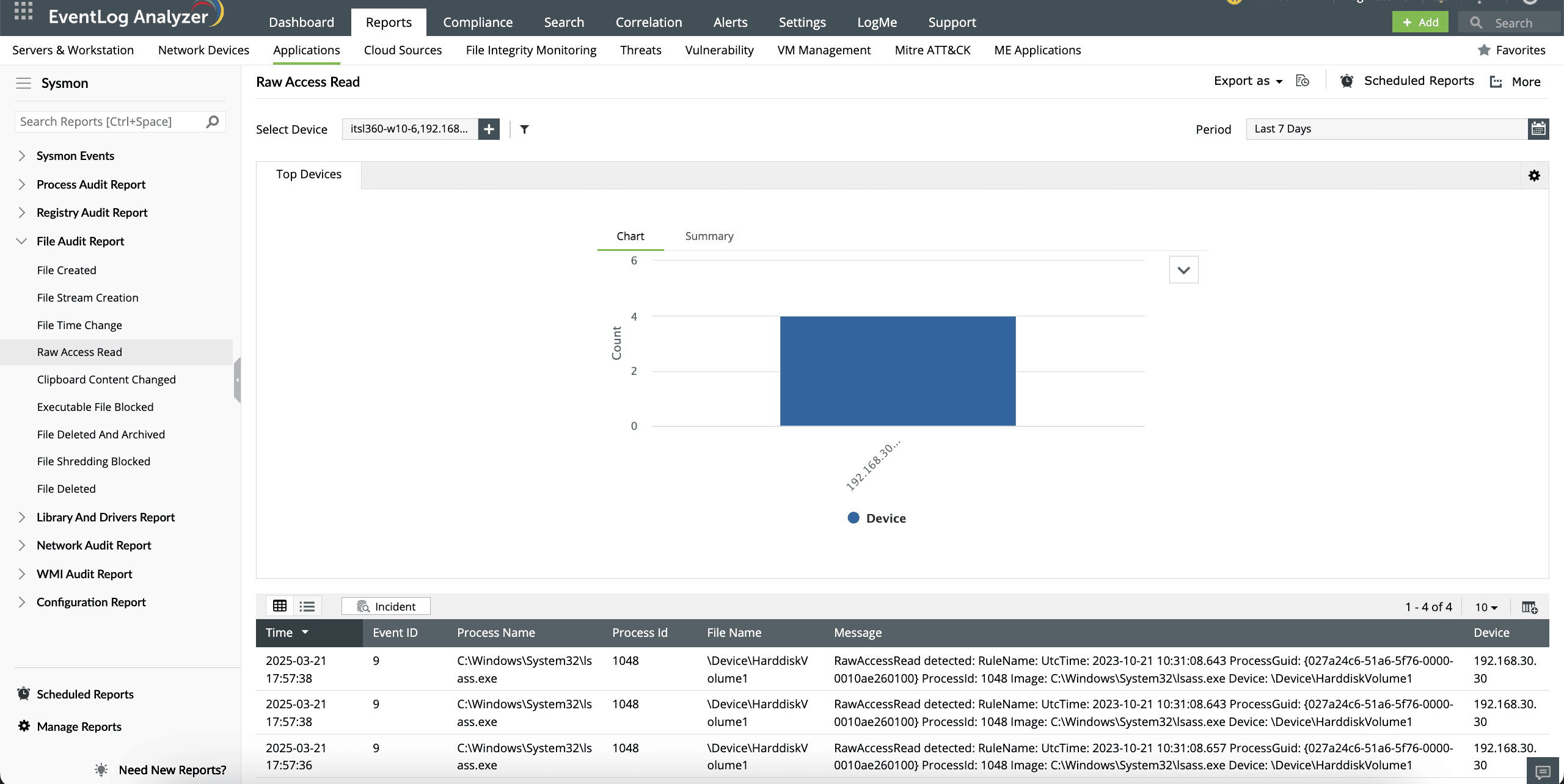
Monitor files to ensure their integrity
With EventLog Analyzer, you can monitor file and stream creation operations. File creation operations will be logged when a file has been created or overwritten. You can also monitor read operations performed on a drive using the Raw Access Read report. This can help you prevent data exfiltration attacks on these files. With EventLog Analyzer's File Stream Creation report, you can monitor when a file stream is created and keep track of certain malware that drop their executables or configuration settings through browser downloads.
Audit network devices and resources
With EventLog Analyzer's in-depth Sysmon log analysis capability, monitor network connections and get visibility into each connection’s process ID, source IP address, source and destination ports, and more. You can also analyze logs generated when a process executes a DNS query, regardless of its result (Success, Failure, or Cached).
Audit registry and configuration changes
Sometimes attackers initiate an attack by modifying registries to launch malicious applications. With EventLog Analyzer, you can monitor changes such as modifications to registry keys and registry values.
You can also monitor the state of a Sysmon service using the Service State Change report, which will tell you if the service has started or stopped running along with its version number.
Other solutions offered by EventLog Analyzer
Windows log management
Collect, monitor, and analyze event log data to detect malicious activities using EventLog Analyzer. It provides you with actionable security information that can help you secure your network efficiently.
Syslog management
Simplify syslog management with EventLog Analyzer. It can centrally collect, filter, and audit syslog messages obtained from various sources, and raise real-time alerts when a threat is detected.
IIS and Apache server log analysis
Detect and mitigate web server attacks on your IIS and Apache web servers with the help of EventLog Analyzer. It also provides comprehensive, graphical reports on error events, security attacks, usage analytics, and more.
Database auditing
Monitor and analyze database server activity, and get real-time alerts and detailed reports for common server attacks, such as SQL injection attacks and denial-of-service attacks.
Network device monitoring
Prevent network intrusions by auditing activities on your perimeter devices. Gain in-depth insights into suspicious network events using EventLog Analyzer's predefined graphical reports.
File integrity monitoring
Protect your company's sensitive data from unauthorized access and modifications with EventLog Analyzer. Get notified in real time when any unusual activity is detected.
5 reasons to choose EventLog Analyzer for Sysmon log analysis
1. Attack detection
Using effective Sysmon log analysis, EventLog Analyzer detects known attack patterns such as privilege escalations and lateral movement.
2. Streamline network operations
With Sysmon log analysis, EventLog Analyzer helps streamline network traffic and detect malicious traffic.
3. Correlate events
Correlate process creation or modification events with threat intelligence or other security events to detect attacks at an early stage.
4. Securely store Sysmon logs
Securely archive your Sysmon logs for future forensic investigation purposes and regulatory compliance requirements.
5. Log forensics
Analyze your network logs and find the root cause of a security breach using EventLog Analyzer's powerful log search engine.
Frequently asked questions
Sysmon log files can be located in the following file path:
C:\Windows\System32\winevt\Logs\.
In the Event Viewer, you can view Sysmon logs in Applications and Services Logs > Microsoft > Windows > Sysmon.
Sysmon event IDs to monitor:
- Event ID: 1 Process creation
- Event ID: 2 A process changed a file creation time
- Event ID: 3 Network connection
- Event ID: 4 Sysmon service state changed
- Event ID: 5 Process terminated
- Event ID: 6 Driver loaded
- Event ID: 7 Image loaded
- Event ID: 8 CreateRemoteThread
- Event ID: 9 RawAccessRead
- Event ID: 10 ProcessAccess
- Event ID: 11 FileCreate
- Event ID: 12 RegistryEvent (Object create and delete)
- Event ID: 13 RegistryEvent (Value Set)
To monitor Sysmon logs in EventLog Analyzer, devices that have Sysmon installed in them can be added by navigating to Settings > Configuration > Manage Application Sources. Click here to learn more.
Sysmon is a Windows system device that's designed to provide detailed information about Windows system activities in real time, which includes process creations, network connections, and changes to file creation time. It operates as a Windows service and device driver, which, once installed and configured, starts automatically with Windows. This ensures that monitoring persists through system reboots and is available from system startup to shutdown. This can give the user an understanding of the system and user behavior, which can later be used for attack detection, anomaly detection, and forensic analysis.
Sysmon can be used to monitor and log a wide variety of system activity, including process creation and termination, network connections, file and registry changes, DNS queries, and so on. This can be used to detect and investigate malware infections and track the behavior of attackers. Sysmon logs are of a great help in gaining insights of the how the systems in place are being used.
Sysmon logs enhance visibility into your network by providing detailed insights into a wide range of system activities. This comprehensive logging can help you identify anomalies and suspicious behavior that could indicate a security breach. Moreover, Sysmon logs can be effectively integrated with log management solutions to provide a centralized view of security events across your network, which can help you correlate events from different sources, identify potential threats, and streamline incident response.











