Ransomware attacks are terrifying, there's no doubting that. Especially with the ransomware-as-a-service model running rampant, and hackers resorting to triple extortion techniques, the potential negative impact of such an attack on your business is staggering. Understanding how nightmarish it can be to end up as a victim, most organizations have tightened their defenses by deploying ransomware detection tools such as a SIEM, or a security analytics solution. Increased security efforts might be why there's been a 21% decrease in ransomware attacks year over year, even though there were still 493.3 million attacks in 2022, as reported in the 2023 SonicWall Cyber Threat Report. Mind-boggling, isn't it?
These stats reinforce the fact that not only do organizations need a SIEM solution, they also need to know how to leverage their SIEM solution to prevent, detect, and respond to ransomware. To learn how to prevent or detect an attack, you should first know how the attack works in the first place. So, let's start with that.
A ransomware attack is carried out in stages as shown in Figure 1.
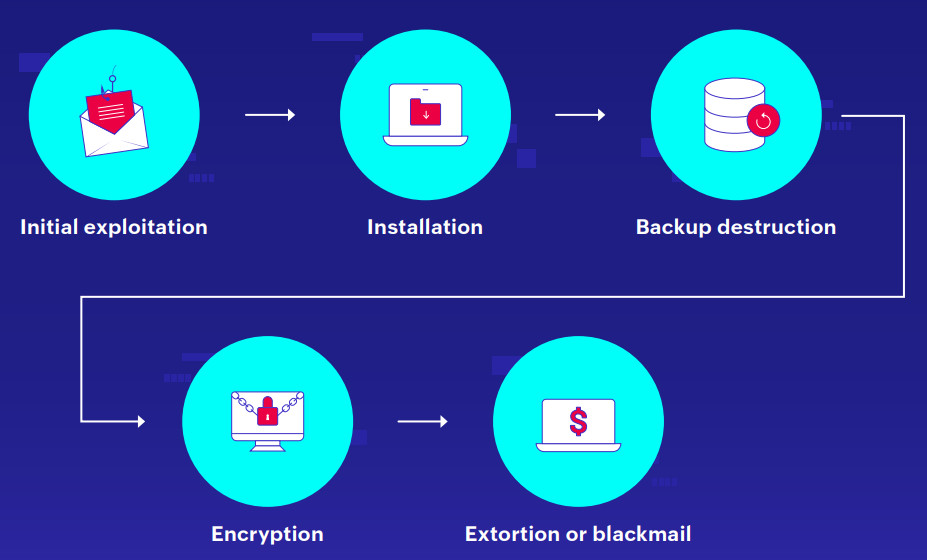 Figure 1: Ransomware stages
Figure 1: Ransomware stages
Initial exploitation: This is how ransomware actors gains entry into the organization's network. To do this, they use phishing (or spear phishing) emails containing malicious links or attachments, brute-force attacks, or malvertising. Through any of these methods, the attackers ensures that the ransomware payload are downloaded into the victim's system without their knowledge or consent.
Installation: In this stage, the ransomware is executed and installed on the victim's system. The initial victim is usually a user who doesn't have many privileges. So, after the initial foothold is established, the ransomware attempts to elevate privileges and propagate the spread of infection by moving laterally. This will continue until the ransomware gains access to an account with the high privileges it requires to carry out its attack successfully.
Backup destruction: It's easy to call the ransomware actors' bluff if the organization has its data backed up. The first thing that attackers would do after acquiring the necessary privileges is to seek and destroy backups. The chances of attackers claiming their reward is higher if the only way for organizations to restore their data is by paying the demanded ransom.
Encryption: In this lethal step, the ransomware encrypts the organization's sensitive data or critical files. How the files should be encrypted, and which file types should be targeted are details that the attackers conveys through their command and control (C&C) channel. The encrypted files can only be recovered with the decryption key the attackers possess.
Extortion: In this final step, the threat actors triumph their malicious achievement to the organization by demanding a ransom for the organization's data. The ransom is usually requested in the form of Bitcoins or other cryptocurrency. Ransom extortion technique can be single, double, or triple. In a single extortion, the data is encrypted and a demand is made. In a double extortion, the original data's exfiltrated, and its copy is encrypted, and if the victim organization fails to pay up, the attackers threaten to sell the exfiltrated data to rival organizations. In a triple extortion, the attackers not only threaten the organization, but also its customers or partners to pay, or their sensitive data will be exposed online.
Figure 2 below shows the ransom note of the ESXiArgs ransomware that plagued the world in February 2023.
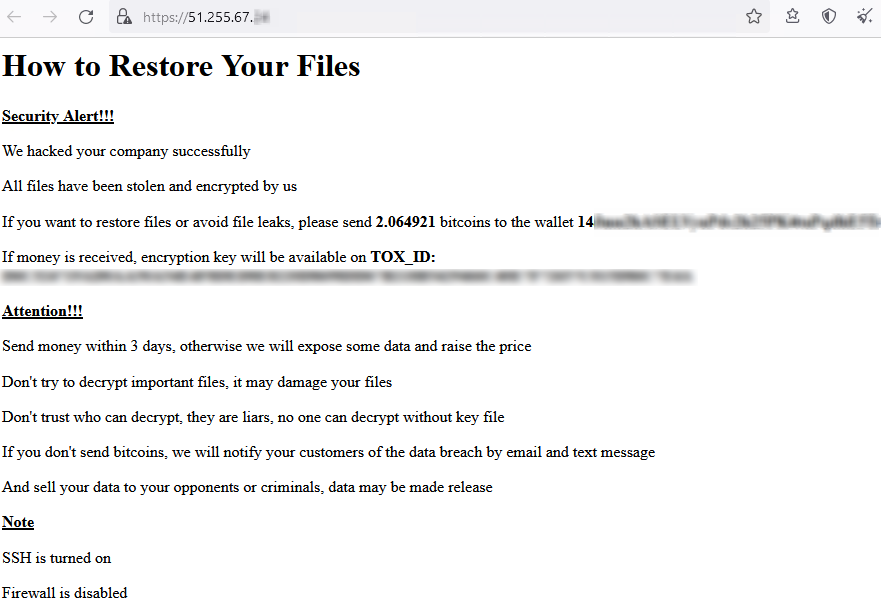 Figure 2: ESXiArgs ransom note
Figure 2: ESXiArgs ransom note
The worst part about ransomware is that there's no guarantee cybercriminals will return your original data—even if you pay the ransom! A good defense is backing up your data frequently and investing in an effective SIEM solution like ManageEngine Log360.
For a SIEM solution to be effective, it first needs to ingest, in real time, the necessary logs such as perimeter device logs, Windows event logs, endpoint logs, database logs, application logs, proxy logs, and IoT logs. To ensure complete visibility, sophisticated SIEM solutions come with the ability to discover devices automatically. Once the logs are successfully ingested, the SIEM then begins analyzing the logs for malicious activities using techniques like threat intelligence, event correlation, and UEBA.
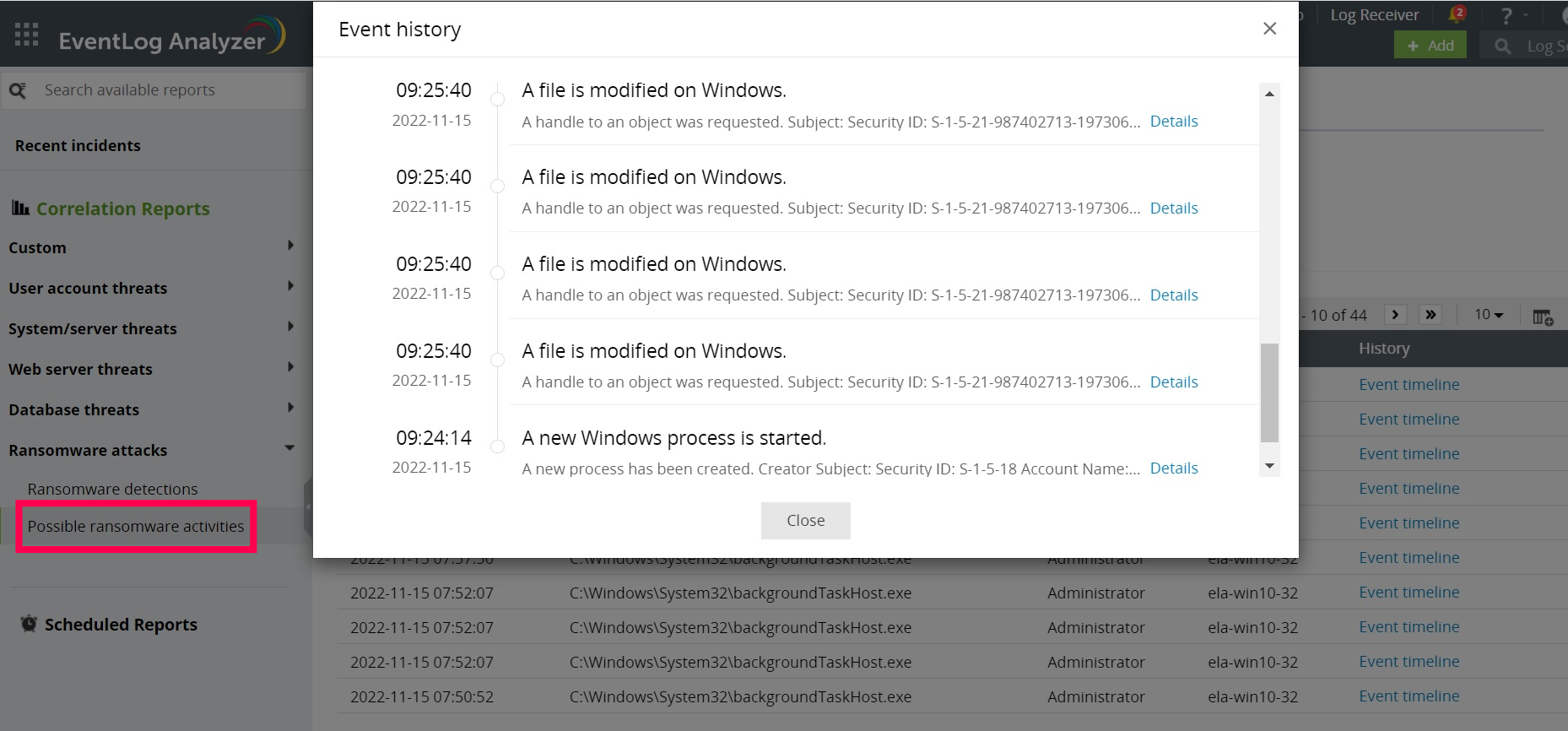 Figure 3: Event timeline of a possible ransomware activity as observed in Log360
Figure 3: Event timeline of a possible ransomware activity as observed in Log360
The alerting and report modules of a SIEM solution help you receive real-time alerts and readily available reports on crucial events. These events include PowerShell executions, user activity, user permission changes, firewall policy changes, GPO changes (as shown in Figure 4), and software installations. Monitoring these can help you detect lateral movement and privilege escalation attempts.
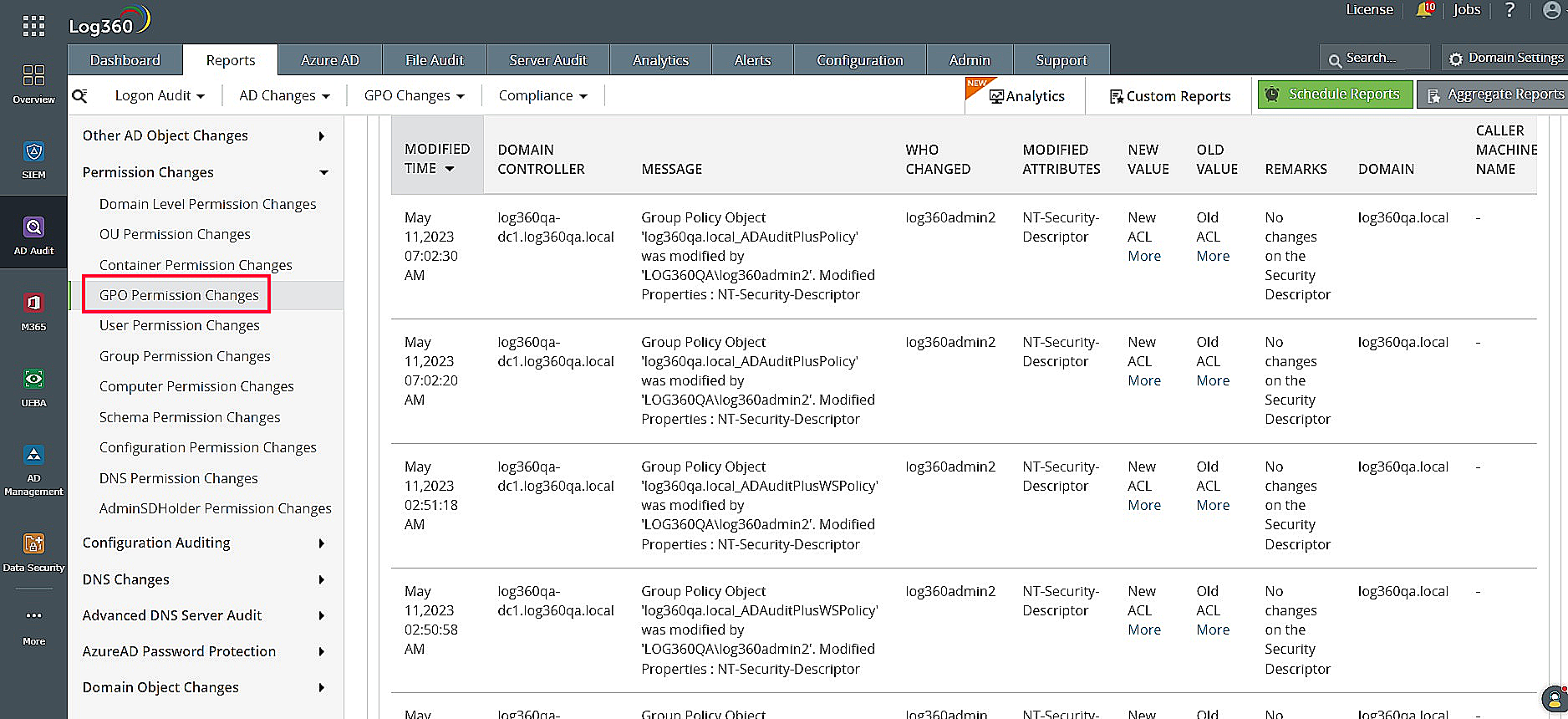 Figure 4: Log360 dashboard showing GPO permission changes
Figure 4: Log360 dashboard showing GPO permission changes
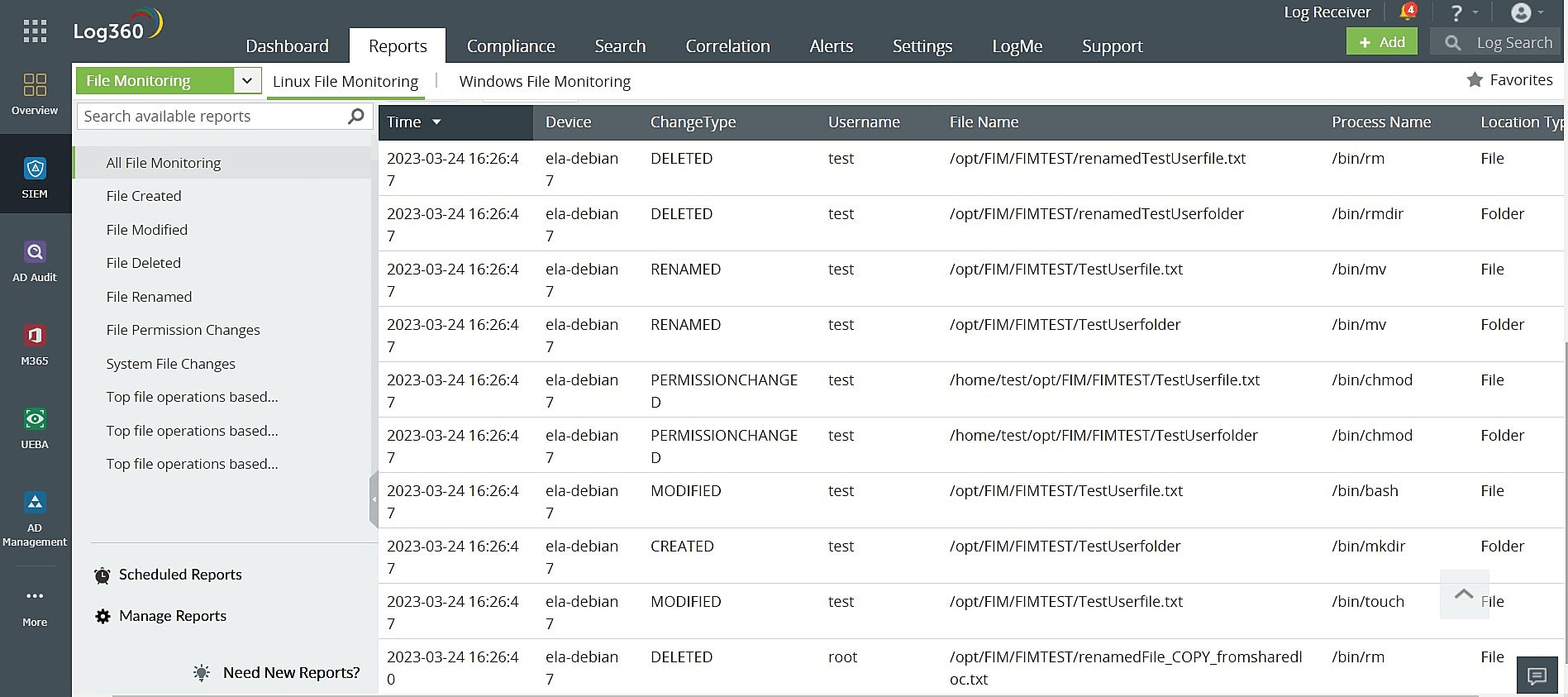 Figure 5: File monitoring events as recorded in Log360
Figure 5: File monitoring events as recorded in Log360
SIEM solutions help stop a ransomware attack in the initial stages. If an attack has already progressed to the encryption stage, a SIEM solution can still help with log forensics. To learn about ransomware in healthcare, read this e-book. To learn how a unified SIEM solution with integrated UEBA, SOAR, DLP, and CASB capabilities like ManageEngine Log360 can help your organization defend against various threats, including ransomware, sign up for a free personalized demo.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.