Configuring Salesforce Authenticator for identity verification
ADSelfService Plus supports custom time-based one-time password (TOTP) authenticators for enabling MFA for endpoints such as machines, cloud applications, VPN, and OWA. Below are the steps to set up Salesforce Authenticator as one of the MFA methods for identity verification.
- Navigate to Configuration > Self-Service > Multi-factor Authentication > Authenticators Setup.
- From the Choose the Policy drop-down, select a policy.
Note: ADSelfService Plus allows you to create OU- and group-based policies. To create a policy, go to Configuration > Self-Service > Policy Configuration > Add New Policy. Click Select OUs/Groups, and make a selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
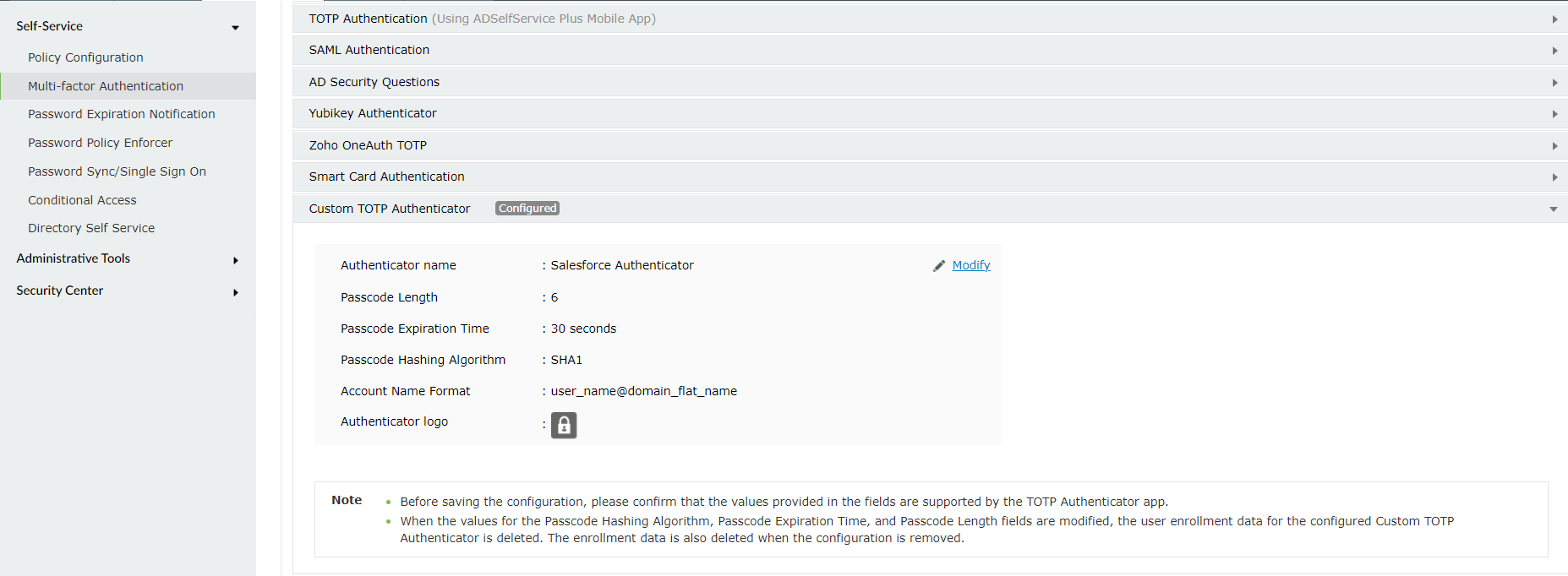
- Click Custom TOTP Authenticator.
- Enter the Authenticator Name, Passcode Length, Passcode Expiration Time, Passcode Hashing Algorithm, and Account Name Format.
Note: All the values provided as options in the fields mentioned above are supported by Salesforce.
- Upload the Salesforce Authenticator logo image file in the Authenticator logo field.
Note: If the Authenticator logo is not uploaded, a default logo will be used.
- Click Save.
To configure Salesforce authenticator as an MFA method for password reset and account unlock:
- Navigate to the MFA for Reset/Unlock tab.
- Choose the number of authenticators you wish to enable in the drop-down field.
- In Select the authenticators required field, check the box next to Salesforce Authenticator.
- Click Save Settings.
To configure Salesforce Authenticator as an MFA method for endpoints:
- Navigate to the MFA for Endpoints tab.
- To enable Salesforce Authenticator as a method of verification during machine login, check the box to enable the required number of factors for machine login and choose Salesforce Authenticator from the list of authenticators.
- To enable Salesforce Authenticator as a method of verification during OWA login, check the box to enable the required number of factors for OWA login and choose Salesforce Authenticator from the list of authenticators.
- To enable Salesforce Authenticator as a method of verification during VPN login, check the box to enable the required number of factors for VPN login and choose Salesforce Authenticator from the list of authenticators.
- Click Save Settings.
To configure Salesforce Authenticator as an MFA method for applications:
- Navigate to the MFA for Applications tab.
- Choose the number of authenticators you wish to enable in the drop-down field.
- In Select the authenticators required field, check the box next to Salesforce Authenticator.
- Click Save Settings.
To modify the configuration:
- Navigate to Configuration > Self-Service > Multi-factor Authentication > Authenticators Setup.
- Click Custom TOTP Authenticator.
- Click Modify and change the information provided wherever necessary.
- If the configuration has to be removed, click Remove Configuration.
- Click Save.
Note:
When the configuration is modified or removed, the user enrollment data for that configuration will be deleted as well.
When a user is shifted from one self-service policy to another and if both these policies do not have the same Custom TOTP Authenticator configuration, the user will be considered as not enrolled.
Enrollment using Salesforce Authenticator
- In the ADSelfService Plus’ user portal, go to the Enrollment tab > Salesforce Authenticator. A QR code will be displayed. If forced enrollment has been configured, the user registration page will be displayed on logging in to the user portal.
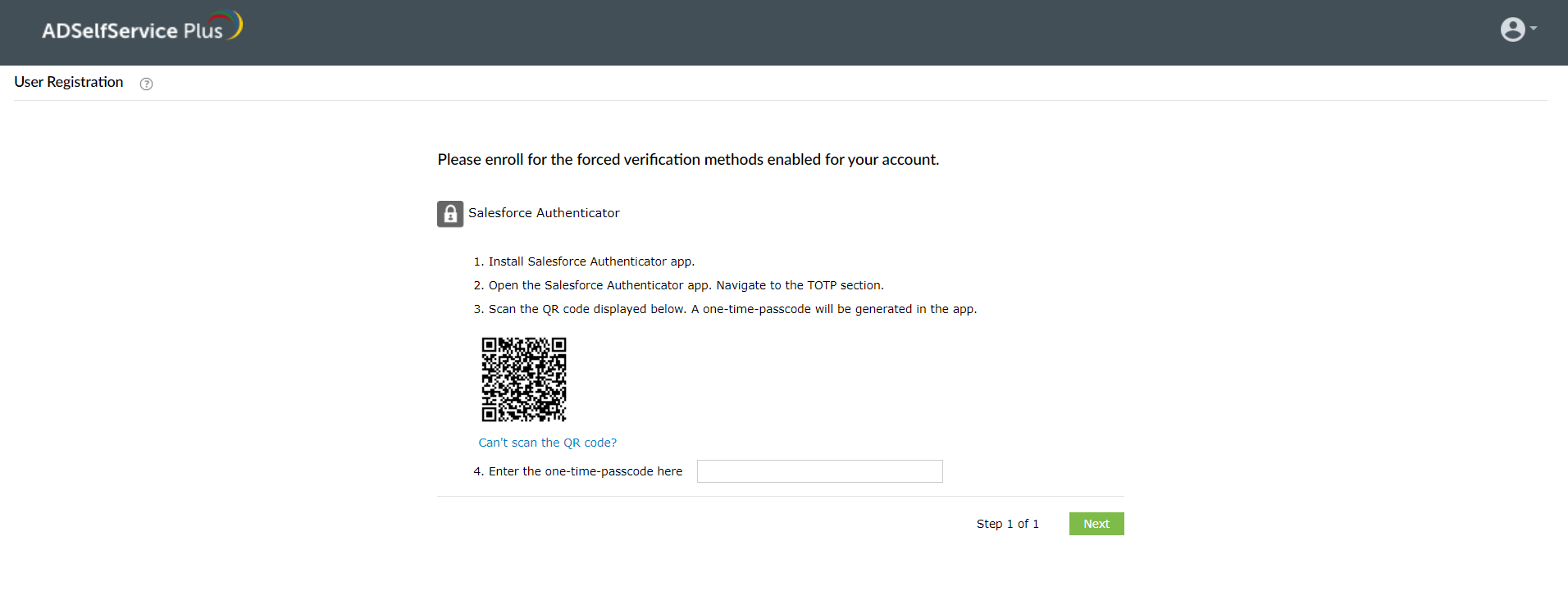
- Open the Salesforce Authenticator application on your device.
- Click Add an Account.
- Select the Scan QR Code option and scan the displayed QR code.
- If the operation is successful, your account will be automatically added to the dashboard.
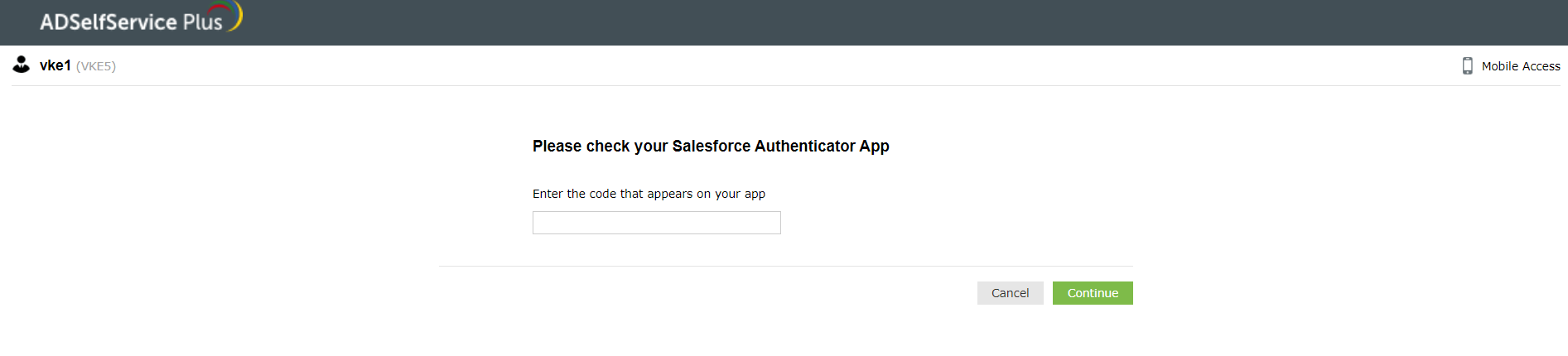
For successful identity verification, enter the passcode displayed in the Salesforce Authenticator application in the passcode field.
Highlights of ADSelfService Plus
Allow Active Directory users to self-service their password resets and account unlock tasks, freeing them from lengthy help desk calls.
Get seamless one-click access to 100+ cloud applications. With enterprise single sign-on, users can access all their cloud applications using their Active Directory credentials.
Intimate Active Directory users of their impending password and account expiry via email and SMS notifications.
Synchronize Windows Active Directory user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
Strong passwords resist various hacking threats. Enforce Active Directory users to adhere to compliant passwords by displaying password complexity requirements.
Enable Active Directory users to update their latest information themselves. Quick search features help admins scout for information using search keys like contact numbers.