Passwords used by employees can either make or break data security in an organization. It's not surprising, however, to know that employees don't often follow good password hygiene. From setting weak and generic passwords to lax password policy rules in native tools like Windows Active Directory Group Policies, several factors pose a serious threat to password security and put organizations' data at risk of exposure.
ManageEngine ADSelfService Plus' Password Policy Enforcer overcomes the drawbacks of Active Directory's built-in password policies and allows you to enforce a custom, advanced password policy that seamlessly integrates with the above-mentioned Active Directory password policies. It fortifies your Active Directory passwords to ensure that your organizational resources are protected from potential cyberattacks.
ADSelfService Plus' password policies can be set to enforce the following requirements:
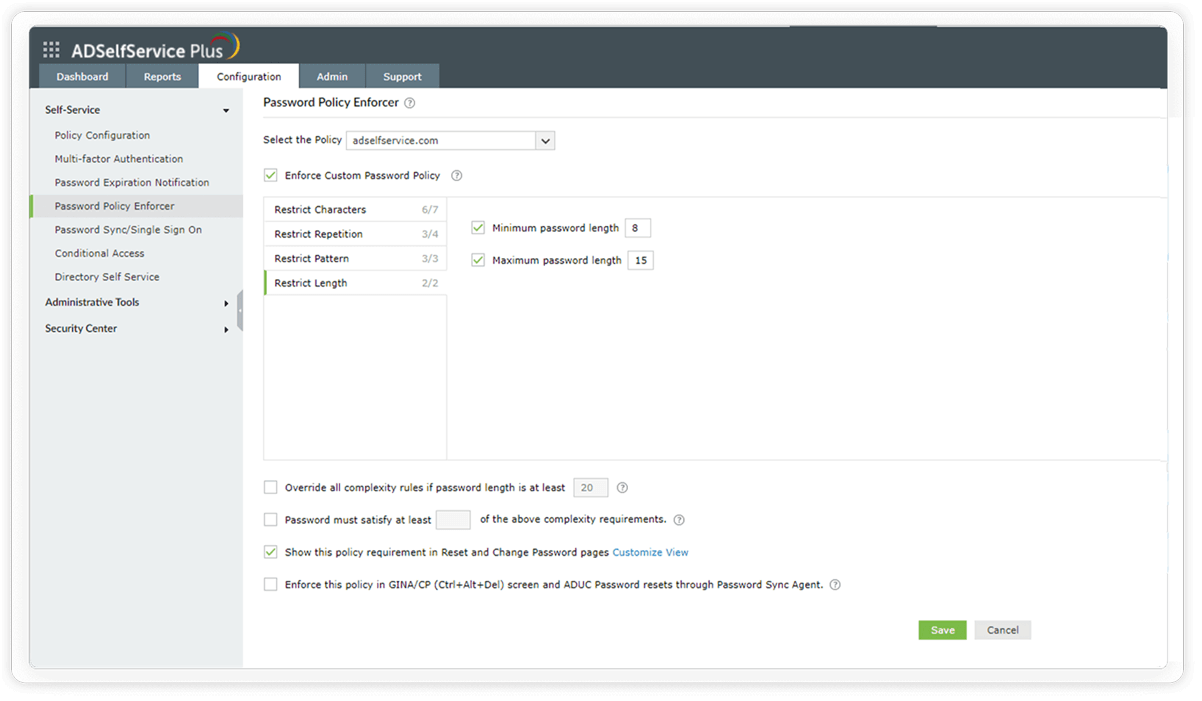
Restrict characters: These password policy settings include mandating the number of special, numeric, and Unicode characters. You can also set the type of character with which the password must begin.
Configure the inclusion of alpha-numeric characters in passwords.
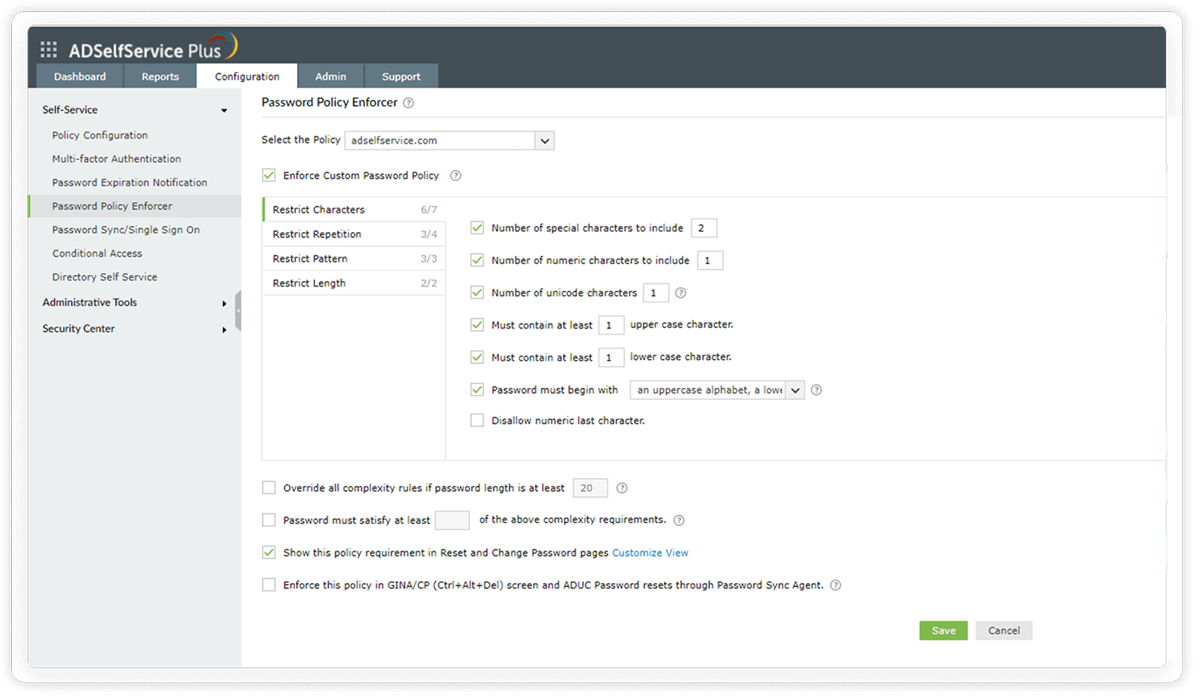
Restrict repetition: These settings restrict the use of consecutive characters from usernames or previous passwords. Consecutive repetition of the same character can also be restricted.
Restrict users from re-using their previous passwords during password creation.
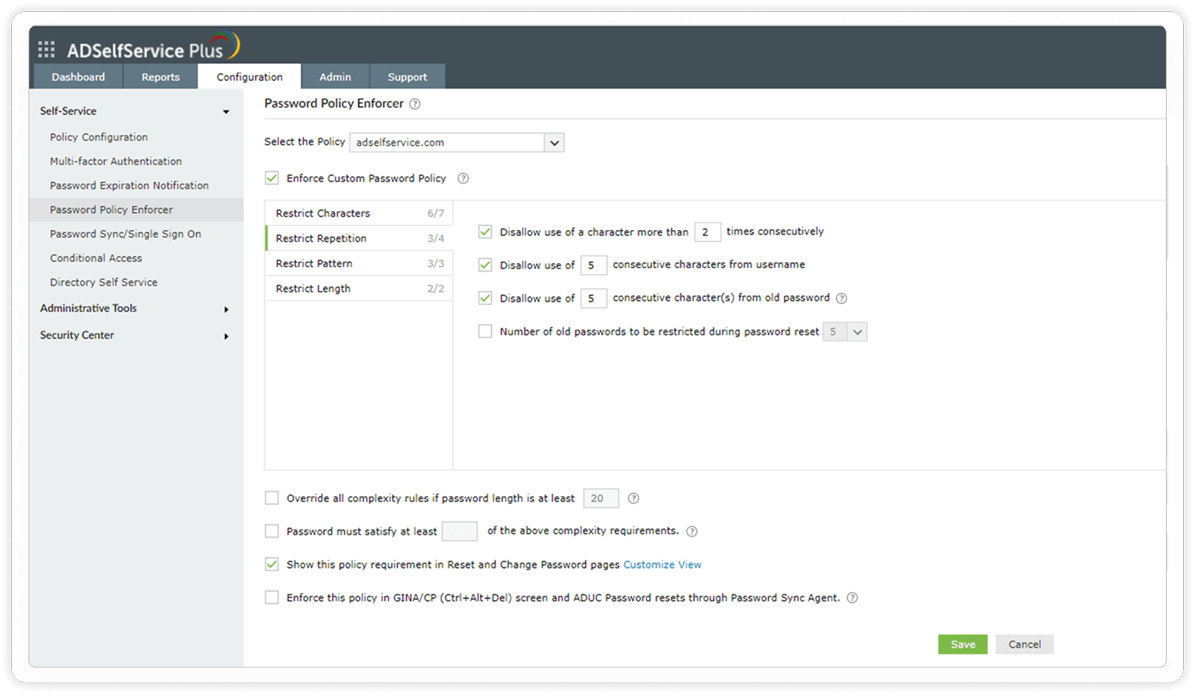
Restrict pattern: The settings under this tab restrict custom dictionary words, patterns, and palindromes that might be commonly used.
Restrict users from using common patterns, dictionary words, and palindromes in their passwords.
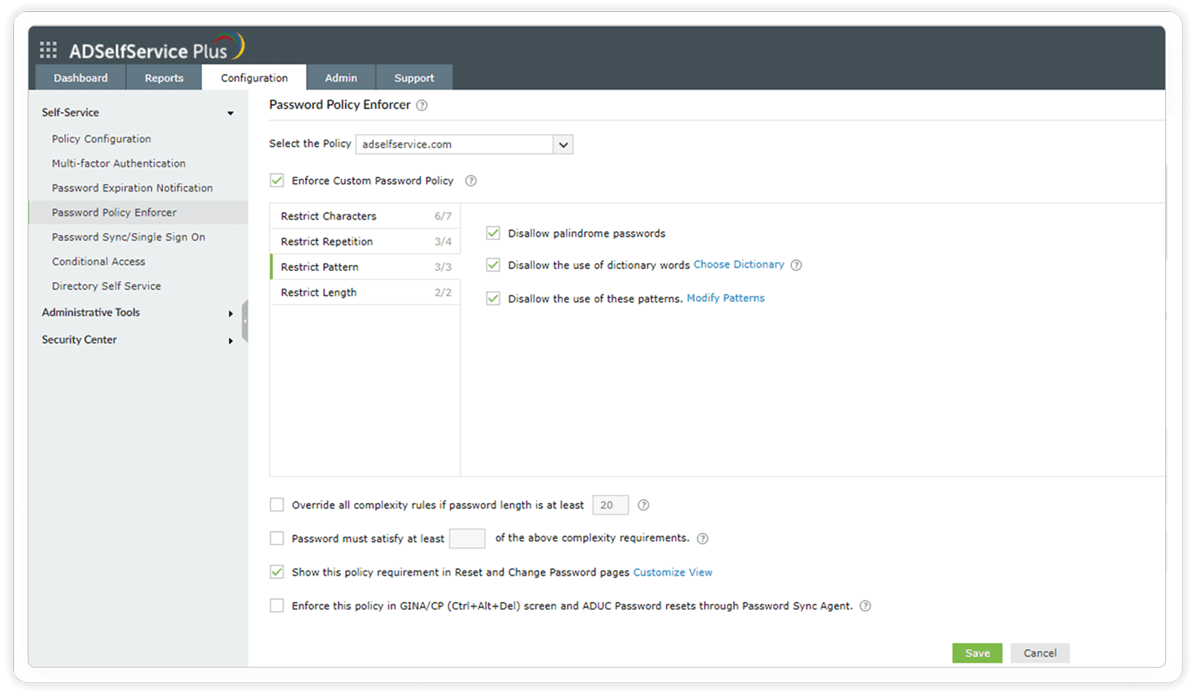
Restrict length: These rules let you set both a minimum and maximum number of characters for the password.
Configure the minimum and maximum password length to satisfy the NIST password guidelines.
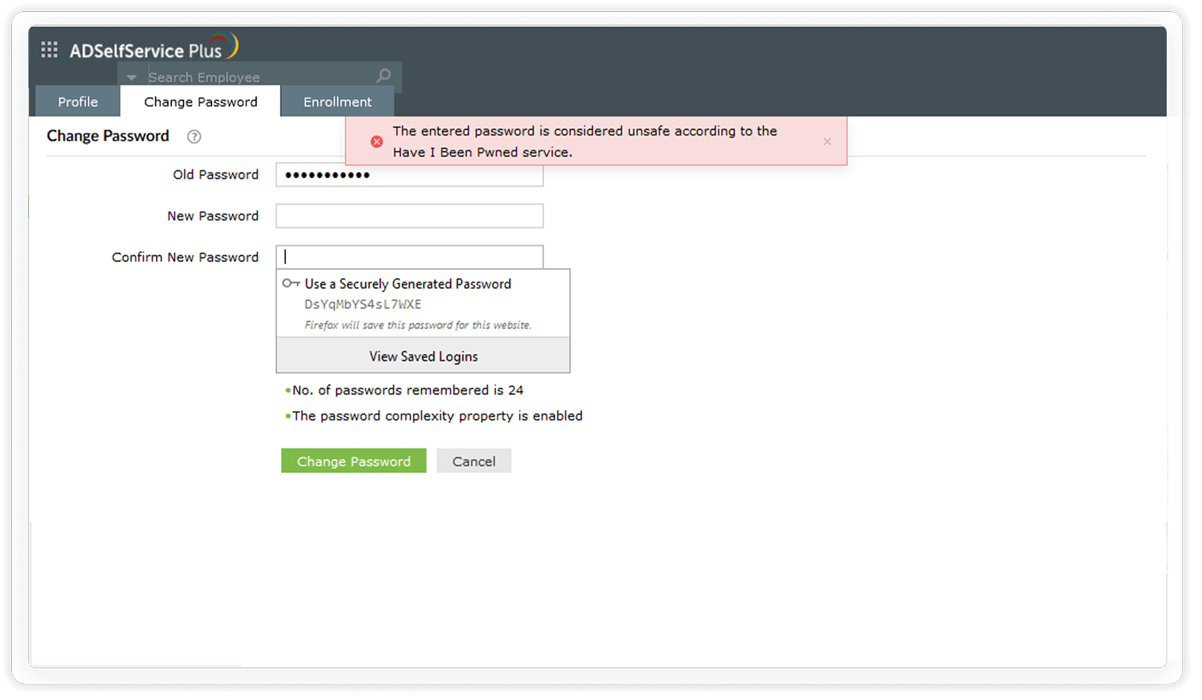
Restrict compromised passwords: ADSelfService Plus lets you integrate with the Have I been Pwned? service, which can ban the use of passwords involved in previous hacks and thus prevents credential stuffing attacks.
A password policy is a set of rules created and enforced to strengthen user passwords. A password that satisfies all the rules of an enforced password policy is considered to secure underlying data better against potential password attacks. A password policy includes rules that specify minimum password length, maximum password age, password history requirements, and password complexity details.
A password attack refers to a threat actor trying to authenticate themselves maliciously into your password-protected account using a compromised password. The different types of password attacks are dictionary attack, brute-force attack, credential stuffing, phishing, man-in-the-middle attack, password spraying, traffic interception, and keylogger attack.
A dictionary attack involves a threat actor trying to hack into a user account by repeatedly trying various combinations of dictionary words. Often, the words used are not necessarily dictionary words, but predictable password choices like names, birth places, or pet's names, which users normally tend to use in their passwords. For this reason, users are advised to avoid such words while setting passwords.
Active Directory password complexity requirements are settings that mandate users to include certain special characters, like uppercase, lowercase, or non-alphanumeric characters, and to avoid using their usernames in their passwords. Users have chosen strong passwords when the complexity requirements of the enforced domain password policy are met.
Securing a user account or data endpoint with only a password makes it most vulnerable to the password attacks of today. Deploying multi-factor authentication mechanisms, however, is good practice to render compromised credentials useless to hackers. It is also interesting to note that advanced authentication mechanisms like biometrics have made even passwordless secure user authentication possible.
The default Active Directory domain password policy defines configurable rules for user account password creation. This password policy is only applicable to the entire domain to which it is linked, and cannot be customized for a specific set of users, groups, or OUs. Active Directory's FGPP, on the other hand, overcomes this drawback and allows password policies to be tailored to different users and groups within the domain.
Allow users to access all enterprise applications with a single, secure authentication flow.
Learn moreEnhance remote work with cached credential updates, secure logins, and mobile password management.
Learn moreCreate a Zero Trust environment with advanced identity verification techniques and render your networks impenetrable to threats.
Learn moreDelegate profile updates and group subscriptions to end users and monitor these self-service actions with approval workflows.
Learn moreEstablish an efficient and secure IT environment through integration with SIEM, ITSM, and IAM tools.
Learn moreSimplify password management with self-service password resets and account unlocks, strong password policies, and password expiry notifications.
Learn more