

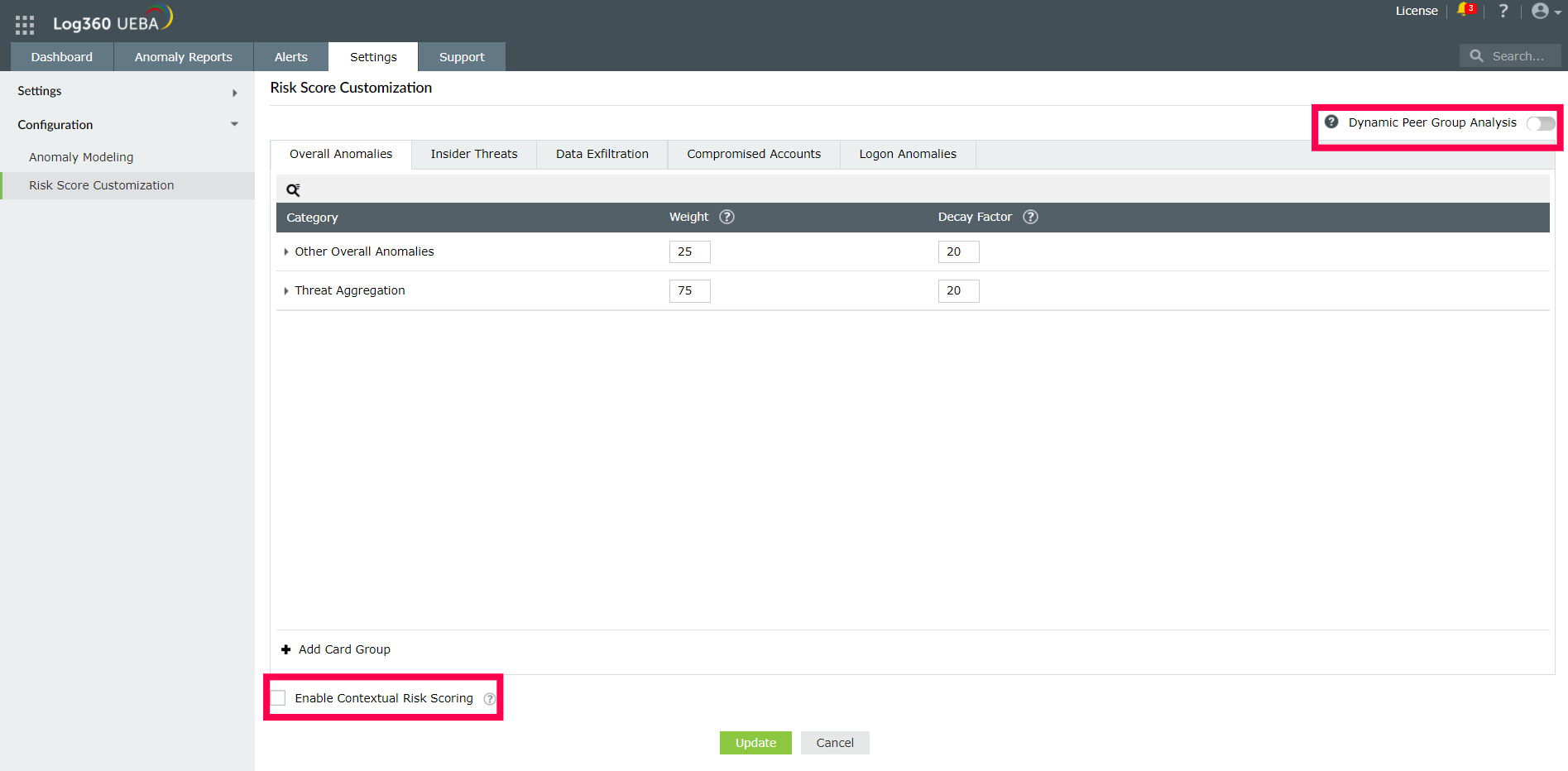
There are five categories of threats for which risk scoring is done in Log360 UEBA. These are:
 Risk scoring in Log360 UEBA
Risk scoring in Log360 UEBA
Any time a user's or entity's observed activity deviates from its baseline of expected activities, the risk score of the user or entity associated with one or more of the above threat categories will be increased.
You will have the flexibility to assign weights and the time decay factor for each activity that affects the risk score of the threat categories. In addition to this, you can:
Users and entities are automatically placed into peer groups based on behavioral traits. The security administrator has the option to enable Dynamic Peer Grouping Analysis when calculating the risk score. A user's or entity's peer group then be considered when calculating the risk score. This will provide better security context and decrease false positives.
You can enable contextual risk scoring to get a better sense of the risk posed by a user at the current time. By enabling this, you get to view the user's contextual risk score besides their peak and average risk scores on the dashboard. The contextual risk score will consider all the subsequent anomalies after the time range chosen by you to provide a more dynamic measure of the risk. This will give you a better sense of the risk posed by the user currently.