Configuring Microsoft Authenticator for Active Directory-based actions
Microsoft Authenticator is an authentication method, developed by Microsoft, that uses a time-based one-time-password (TOTP) to verify users identities. It is often used in combination with authentication methods for multi-factor authentication (MFA) to secure the login process of critical services.
You need Microsoft Authenticator app to authenticate using this method. While logging in once the user enters the credential, the service asks the user to validate themselves using the the 6-digit TOTP generated on the MS Authenticator app.
Using Microsoft Authenticator for AD-based authentication:
Often administrators provide Active Directory domain users with the ability to self-service password resets. With this,
- Users need not wait for admin or help-desk intervention and can have seamless access to their machines.
- The help-desk or admin will not be tasked with hundreds of password reset requests and can instead attend to other crucial tasks.
However, it can be risky for admins to allow this option as it might increase the security risk. Since users are often not asked the details about the old credentials, their identities must be verified in some other form before they can proceed with self-service password reset. Using an authentication method like Microsoft Authenticator is a secure way to verify a user's identity before permitting them to proceed with a password reset.
ADSelfService Plus, an Active Directory self-service password management and single sign-on solution, offers a self-service password reset option secured by MFA. The solution supports 18 authentication methods including Microsoft Authenticator, security questions and answers, TOTP, and YubiKey Authenticator to verify users' identities during:
- Windows, macOS, and Linux logins.
- Active Directory self-service password reset or account unlock actions via the ADSelfService portal, ADSelfService Plus mobile app, and native Windows/macOS/Linux login screen.
- Enterprise application logins through single sign-on (SSO).
- Self-update of Active Directory profile information, subscription to mail groups, and employee search using ADSelfService Plus.
Enabling Microsoft Authenticator for MFA can be done using minimal steps in ADSelfService Plus:
- Navigate to Configuration → Self-Service → Multi-factor Authentication → Authenticators Setup.
- From the Choose the Policy drop-down, select a policy.
Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy. Only users belonging to OUs and groups included in the policy can perform the self-service feature(s) selected.
- Click Microsoft Authenticator section.
- Click the Enable Microsoft Authenticator button.
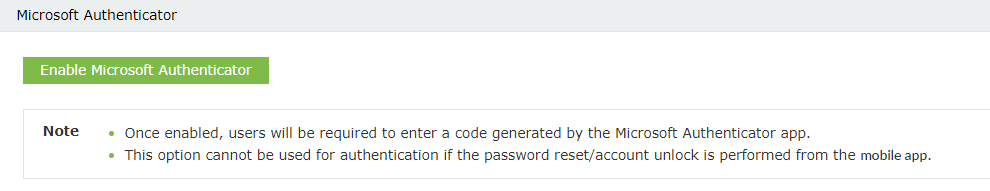
Enable Microsoft Authenticator for Active Directory password resets
- Go to Configuration → Self-Service → Multi-factor Authentication → MFA/TFA Settings. In the MFA for Reset/Unlock section, enter the number of authentication factors to be enforced, and select Microsoft Authenticator along with the other authentication techniques to be used.
- Click Save Settings.
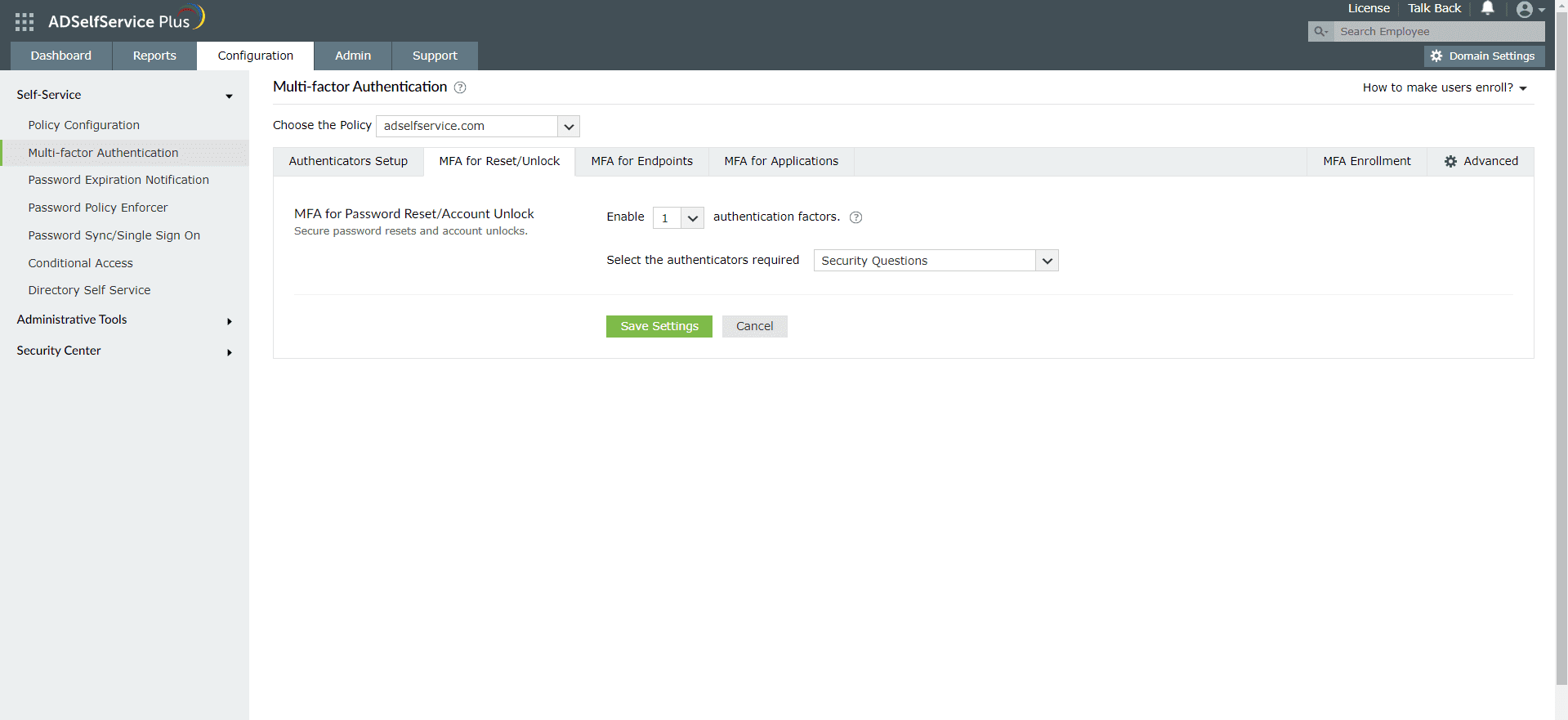
Enable Microsoft Authenticator for Active Directory domain logins
- Go to Configuration → Self-Service → Multi-factor Authentication → MFA for Endpoints.
- Select a policy from the Choose the Policy drop-down. This will determine which authentication methods are enabled for which sets of users.
Note: ADSelfService Plus allows you to create OU and group-based policies. To create a policy, go to Configuration → Self-Service → Policy Configuration → Add New Policy. Click Select OUs/Groups, and make the selection based on your requirements. You need to select at least one self-service feature. Finally, click Save Policy.
- In the MFA for Machine Login section, check the Enable _ authentication factors box and select the Microsoft Authenticator from the drop-down.
- Click Save Settings.
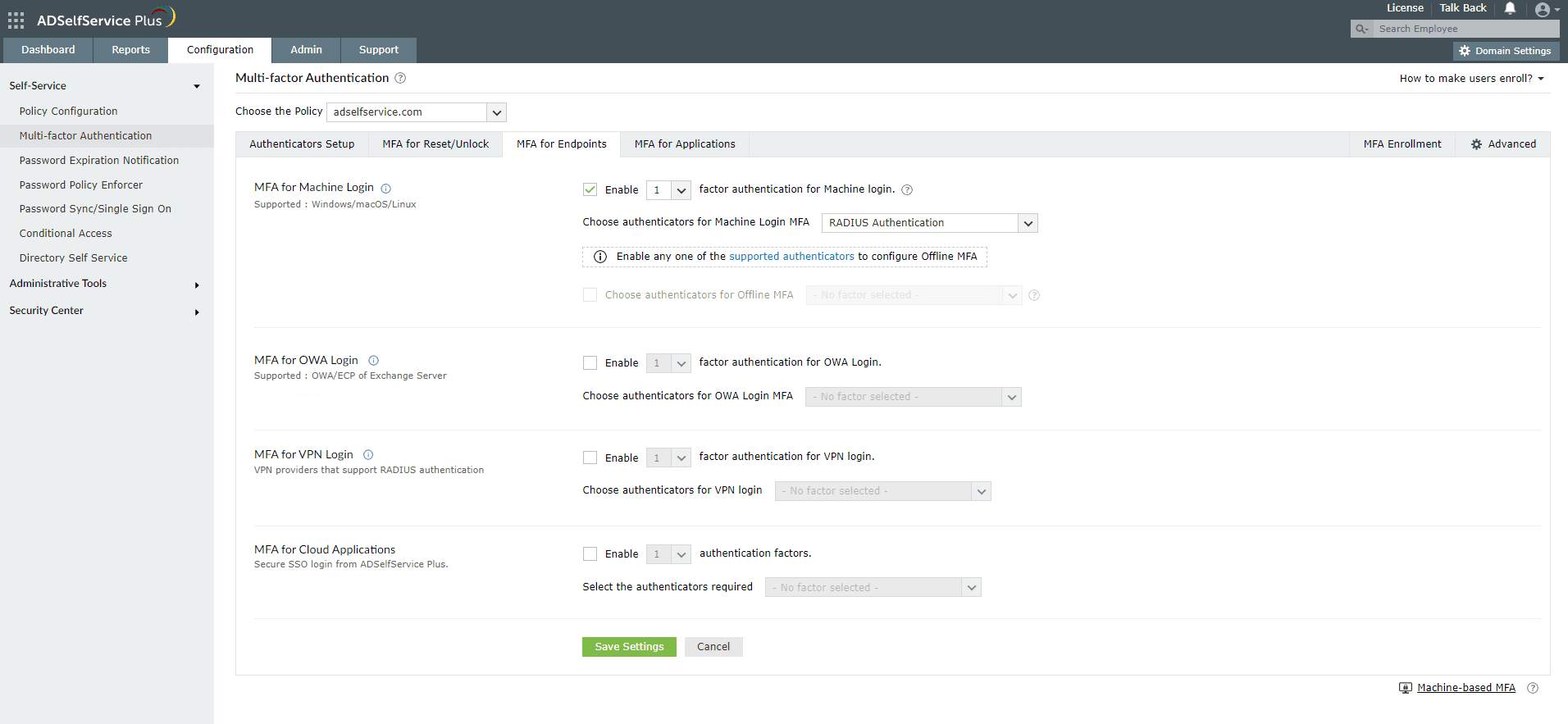
Note:
To enable MFA for Active Directory domain logins:
- The ADSelfService Plus login agent must be installed on client machines. Click here for steps on login agent installation.
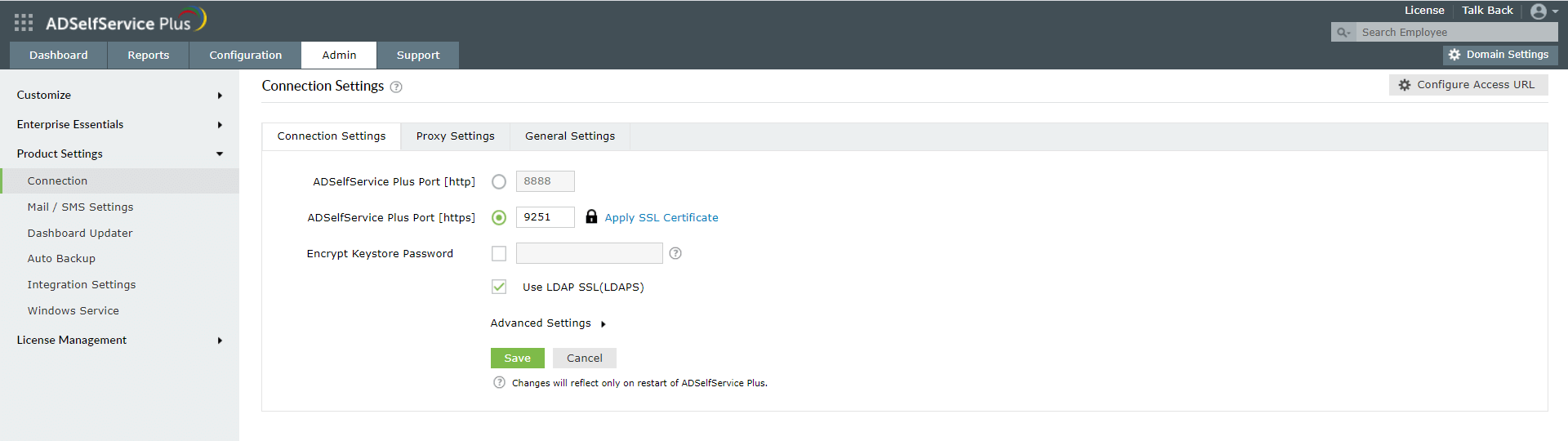
- SSL must be enabled: Log in to the ADSelfService Plus web console with admin credentials. Navigate to the Admin tab → Product Settings → Connection. Select the ADSelfService Plus Port [https] option.
Learn more about ADSelfService Plus and its Multi-factor Authentication feature.
Simplify password management with ADSelfService Plus.
Self-service password management and single sign-on solution
ManageEngine ADSelfService Plus is an integrated self-service password management and single sign-on solution for Active Directory and cloud apps. Ensure endpoint security with stringent authentication controls including biometrics and advanced password policy controls.
- Related Products
