Will your users' infosec habits make your organization vulnerable to fraud?
In these times, when virtually all business data is stored digitally, good information security (infosec) habits are essential to protect businesses. While digital data has its benefits, it also has a major downside—identity theft. This is when an attacker impersonates a user and steals sensitive information pertaining to your organization. This could lead to a data breach, which in turn results in clients second-guessing your credibility.
How do attackers steal someone’s identity?
The first step towards stealing a user's identity is obtaining their password. This could be done by:
- Carrying out password attacks: Hackers use brute force, man-in-the-middle (MITM), and several other types of password attacks to discover a user's password. They use this password to gain fraudulent access to network resources.
- Using stolen credentials: Credentials stolen from multiple data breaches can be tested against targeted user accounts. Since users tend to reuse passwords across several accounts, this could prove helpful to attackers.
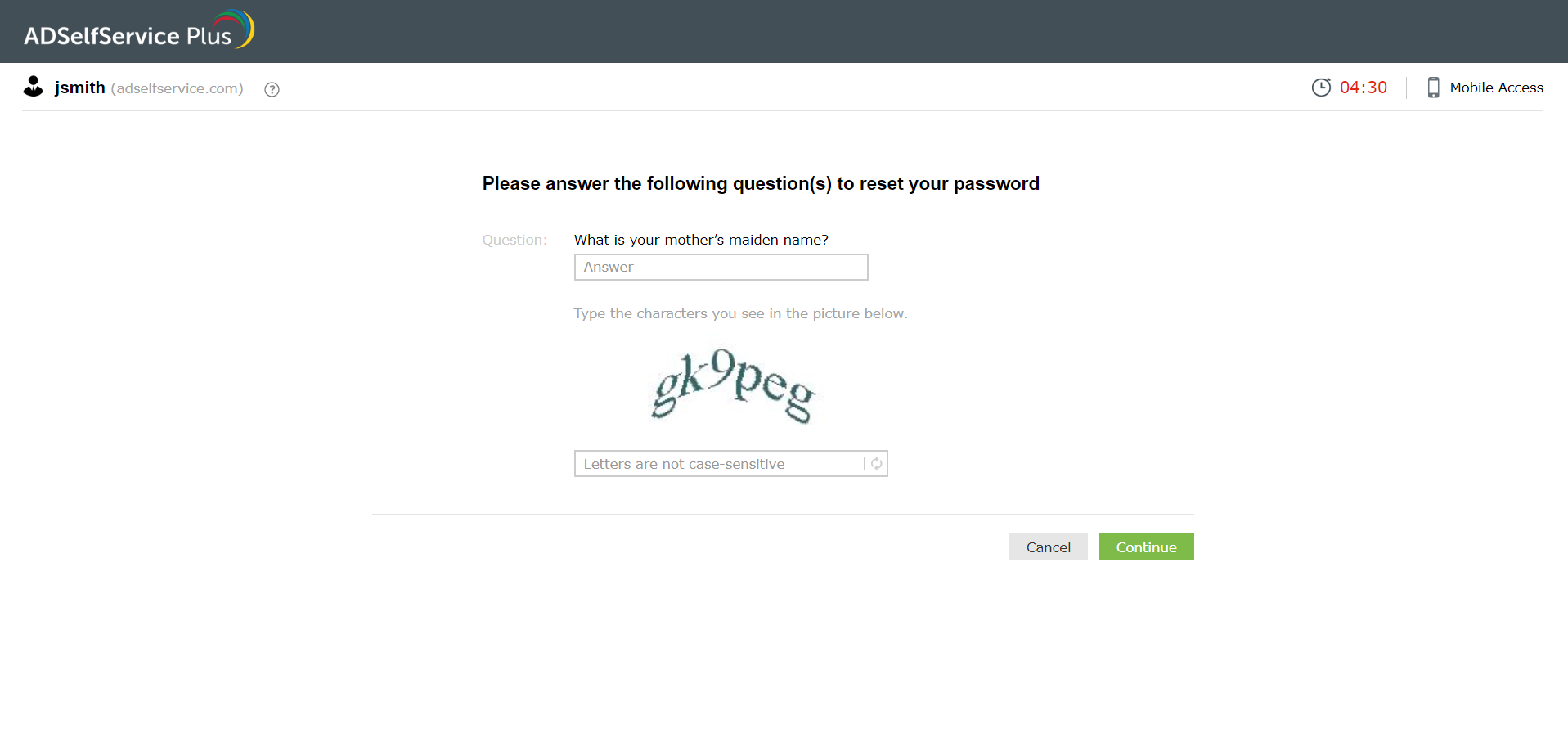
- Hoaxing help desk technicians: Cybercriminals can trick help desk technicians into believing that they are legitimate users and make them reset the password of a targeted account.
What infosec habits prevent identity theft?
- Forcing users to configure complex passwords makes it difficult for attackers to guess passwords.
- Multi-factor authentication (MFA) is an added layer of security that provides a foolproof way to verify the identity of users.
Prevent identity theft using ADSelfService Plus:
ManageEngine ADSelfService Plus is an integrated self-service password management and single sign-on solution that provides advanced password policies and an assortment of MFA methods. Its Password Policy Enforcer and MFA features help you secure your users' Active Directory (AD) credentials from security attacks.
Password Policy Enforcer:
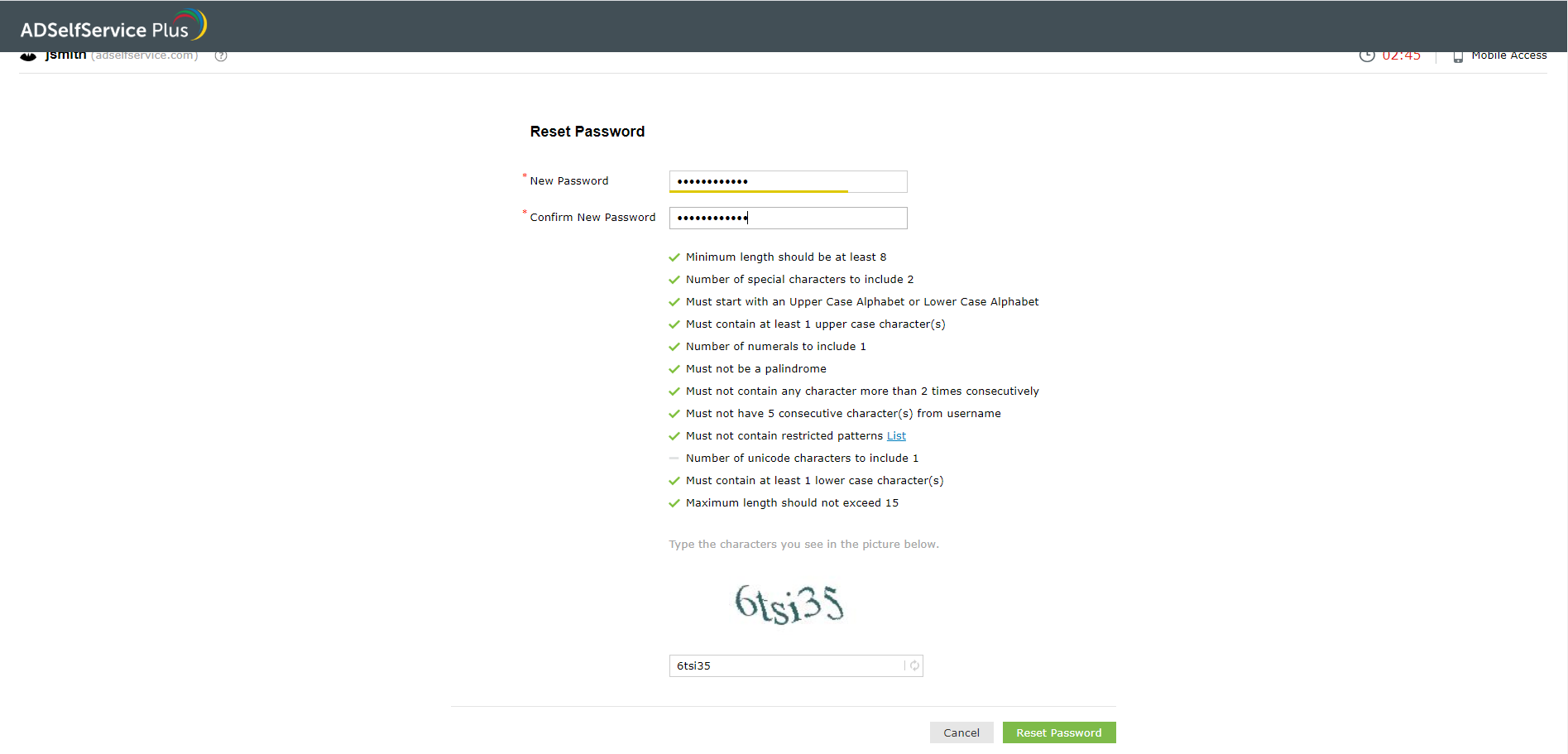
The Password Policy Enforcer feature of ADSelfService Plus allows you to set stringent, OU-based custom password policies. This feature provides complex rules besides the flexibility of assigning different policies for users with different privileges, such as IT admins, finance staff, and managers. On top of supporting AD, this feature can also be used in a wide range of cloud apps, such as Microsoft 365 (formerly Office 365), G Suite, and Salesforce. View a step-by-step guide on configuring the Password Policy Enforcer.
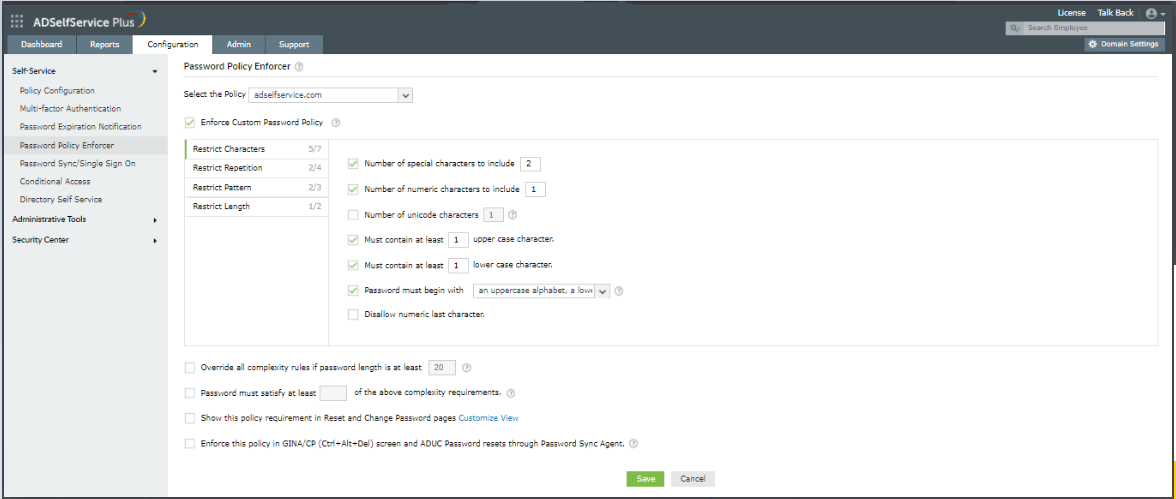
Benefits of using ADSelfService Plus’ Password Policy Enforcer:
- A wide range of complexity rules ensures that passwords are difficult to crack both manually and through bots.
- You can restrict the usage of commonly used dictionary words and keyboard patterns.
- The integration with Have I Been Pwned? prevents the use of breached passwords when users change or reset their passwords.
- Its interactive UI displays password rules to users when they reset their passwords. This will help users understand the policies better and create a password that complies with your organization’s requirements.
- It enables granular password policy creation.
- These policies can not only be enforced while resetting AD passwords through ADSelfService Plus but also via Active Directory Users and Computers (ADUC) and the Windows Desktop Logon Agent (CTRL + ALT + DELETE).
- It strengthens the default set of password policies provided by AD.
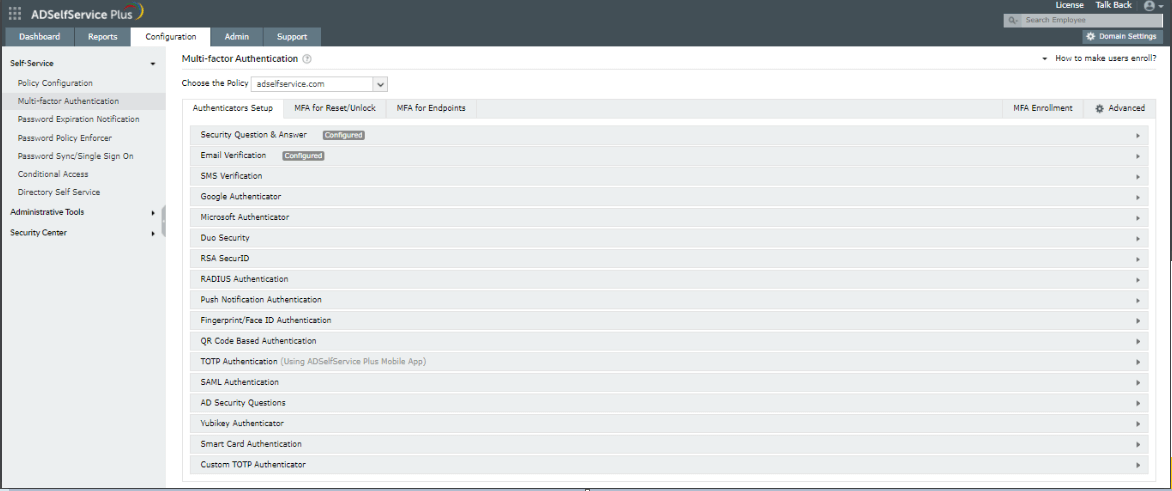
MFA in ADSelfService Plus:
By configuring MFA in ADSelfService Plus, you not only ensure that your users' identities are verified during endpoint logins to your AD domain but also when they log in to cloud applications, such as Office 365, G Suite, and Salesforce.
And what's more?
This feature can also be enabled for local and remote desktop logons to Windows, macOS, and Linux.
ADSelfService Plus provides an array of 17 MFA techniques, including email verification, biometrics, SMS verification, Google Authenticator, and fingerprint authentication. See a full description of all the MFA methods available and a step-by-step guide on configuring them.
How does implementing MFA prevent attackers from accessing user accounts?
With cyberattacks like phishing, keylogging, brute force attacks, and MITM attacks, an attacker might be able to garner a user's credentials. However, as MFA provides another layer of security, attackers won't be able to access a targeted AD account without breaching this layer. If a user has set up fingerprint authentication as their MFA factor, it is almost impossible for an attacker to replicate the user’s fingerprint and break into the respective account. Thus, MFA provides additional security and thwarts cybercriminals from gaining unauthorized access.
Simplify password management with ADSelfService Plus.
Thanks!
Your download is in progress and it will be completed in just a few seconds!
If you face any issues, download manually here
Self-service password management and single sign-on solution
ManageEngine ADSelfService Plus is an integrated self-service password management and single sign-on solution for Active Directory and cloud apps. Ensure endpoint security with stringent authentication controls including biometrics and advanced password policy controls.
- Related Products
