Empowering IT, Elevating Businesses
Seamlessly manage and secure your enterprise, employees and endpoints with a single, integrated platform.
years of legacy
customers across the globe
endpoints managed
countries
Trusted by leading IT firms





IT leaders today walk a tightrope. On one side: evolving business goals and the endless demand for employee productivity. On the other: growing endpoint tools sprawl and never-ending security risks. Rigid processes, unrealistic expectations, and fragmented tools aren’t just slowing you down—they’re costing resources and accountability. Most solutions force you to choose between control and convenience, between speed and security. But why should you have to choose at all?
More dashboards, more complexity, and more chaos. It's time to break the cycle by simplifying, unifying, and securing everything in one platform.

Unify business goals, employee productivity, and endpoint security in a single platform.
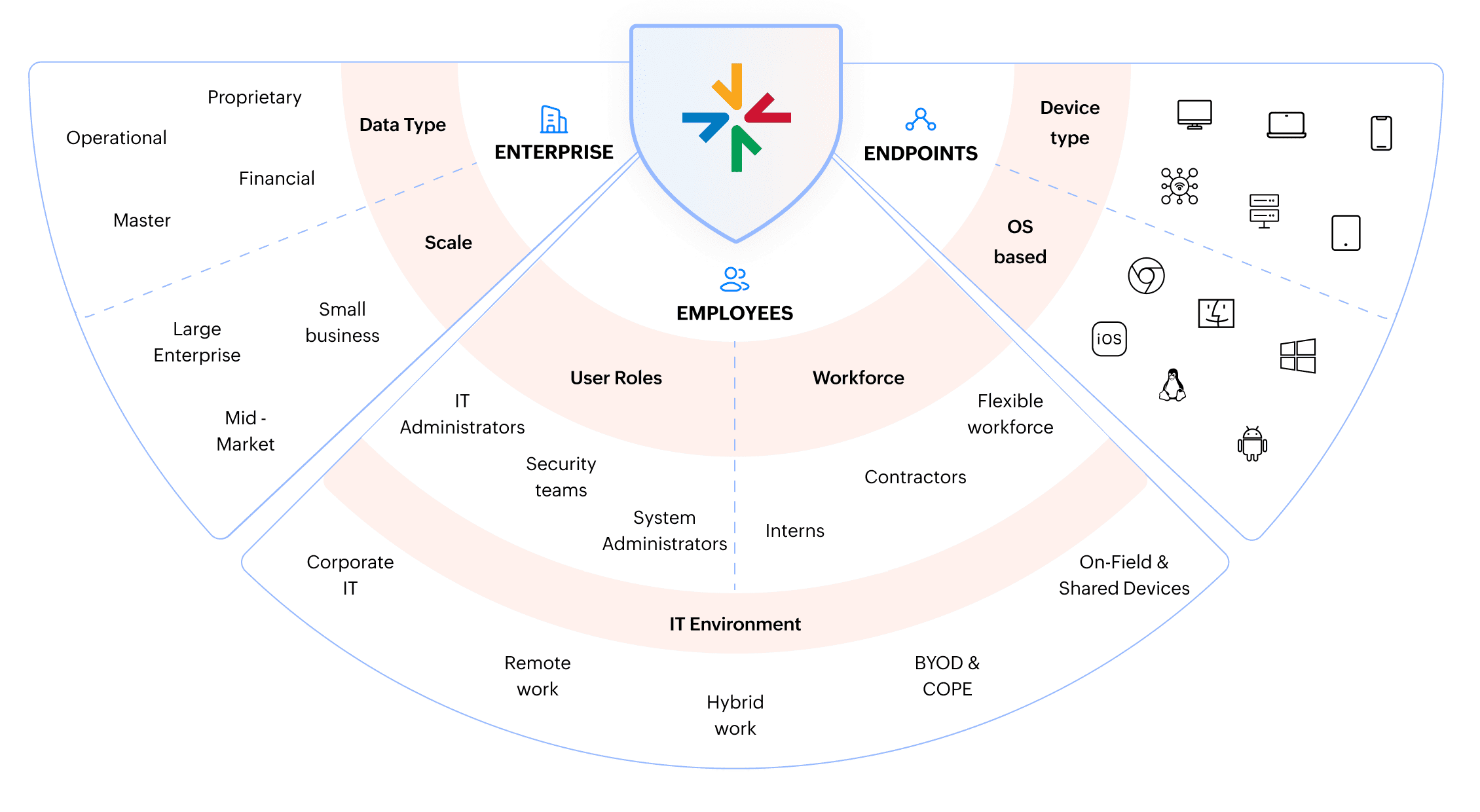
Enterprise
Manage and secure your enterprise with unmatched precision. Endpoint Central eliminates IT blind spots, delivering unparalleled visibility and security.
ManageEngine's global study spanning 7 regions and 19 industries reveals that nearly 50% of IT leadership and staff in the IT Industry lack full visibility into their networks - covering operating systems, configurations, applications, and endpoints. This gap in awareness spans roles from IT support specialists, managers, security architects, sysadmins to CXOs, exposing businesses to significant risks.
Endpoint Central supports 15+ global standards including ISO 27001, HIPAA, NIST, GDPR, and PCI DSS, helping you strengthen security, build trust, and meet regulatory demands with confidence and demonstrate audit readiness across the board.
TAKE THE NEXT STEP
Employee
Endpoint Central aligns productivity, security, and flexibility under a single framework to empower employees.
Insider risk doesn’t always have to stem from bad intent. An employee pastes sensitive data into an AI tool, clicks a phishing link that looks legitimate, or stumbles on malvertising while browsing. Each of these seemingly harmless actions can turn them into unknowing insiders, leaving the organization vulnerable.
Hybrid work is no longer a perk, it’s the new standard. Flexibility to work from anywhere has become a key deciding factor for employees. The challenge for IT leaders is enabling this flexibility without compromising productivity or security. Success lies in delivering seamless digital experiences that ensures every employee—whether remote or on-site—can work without friction.

Start strong with devices pre-loaded with role-specific OS, apps, and configurations-ready for immediate use.
Let employees take control with a self-service portal for instant app installs, updates, hassle-free and IT-approved.


Keep systems secure and up-to-date with automated OS and app patching, seamlessly done after hours.
Protect corporate data with location-based policies, ensuring access only in secure environments like approved Wi-Fi or VPNs.


Separate personal and professional data on BYOD devices with secure, containerized corporate apps.
Lost a device? Quickly locate, lock, or wipe it remotely to keep sensitive data safe.


Remote troubleshooting tools enable IT to fix employee issues without delays, ensuring uninterrupted workflows.
Share data safely with tools that monitor, control, and regulate file transfers, emails, and uploads - always staying one step ahead of leaks.

Endpoints
Protect, manage, and optimize every endpoint - from one powerful console.
Inefficient IT drains budgets and heightens risk. Manual provisioning, tool sprawl, and patch delays slow operations while leaving businesses exposed to costly breaches and fines.
Automate, secure, and streamline every device from day one-cut costs, reduce risks, and boost efficiency.
TAKE CONTROL OF YOUR ITRedundant tools and limited IT visibility drain budgets through unnecessary spend and underutilized assets. Endpoint Central helps you consolidate, maximize asset value, and gain complete control without breaking your budget.
START SAVING TODAY