Basic threshold and anomaly based security alerts notifications in firewall
Firewall Analyzer generates firewall alert message automatically and notifies network administrators, when there is a security breach attempt in the network or abnormal traffic. It detects the anomalous traffic behavior. A firewall security alert can be set up to notify administrators/operators by Email or by SMS or can also run a program to initiate other actions (for example: generate an SNMP trap to be directed to Network/Asset management Application). You can also delete the Alert and deleting bulk alert is possible for a particular profile.
Importance of monitoring firewall alerts
Monitoring security and traffic based firewall alert message is critical in identifying and preventing network threats in real time. These threats can be both exterior or internal. Setting bandwidth based triggers and security based triggers can be useful in identifying internal and external threats respectively. A firewall alert triggered, security admins can investigate and identify the source and type of threats to the network. With normal alert, you can get firewall virus warning from the logs. With this you can take remedial measures for the viruses with known foot prints.
Bandwidth threshold-based alerting
Firewall Analyzer can trigger alerts for the bandwidth usage in real-time. Just set a alert threshold bandwidth value and if the usage crosses the threshold, threshold alert will be triggered and you will be notified through the notification mechanisms. This threshold alert helps you to catch the bandwidth hog. With this you can quickly find out the source responsible for the bandwidth usage and take appropriate remediation measures to stop the business hindering bandwidth usage.
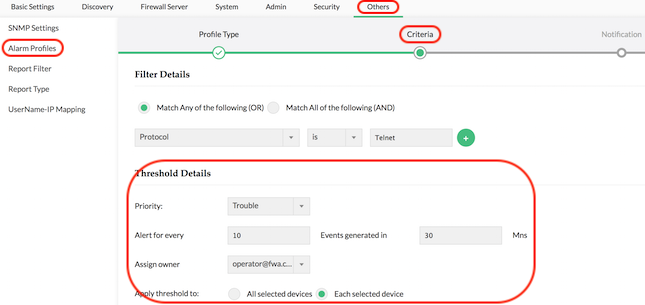
Threshold-based alerting
Alerts can be set up for each device that Firewall Analyzer monitors. You can choose the exact criteria to trigger the alert, set the priority of the alert, and finally set up an email notification or any other notification to immediately notify IT when the alert is triggered.
Request for a free personalized demo
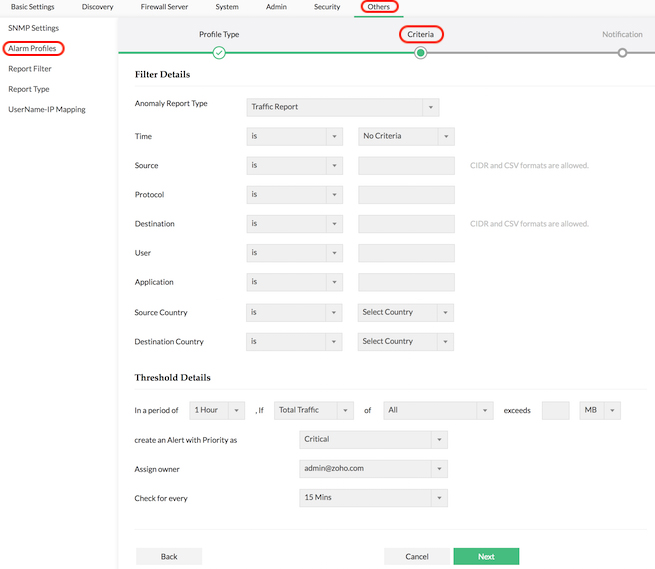
Anomaly-based alerting
Alerts can be set up for detecting anomalous traffic behavior. Anomaly security firewall alert reports can be used for Network Behavioral Analysis (NBA). You can set the filters to detect anomaly security events, choose the threshold criteria to trigger the anomaly alert, set the priority of the alert, and finally set up anomaly notifications or any other notification to immediately notify IT when the alert is triggered.
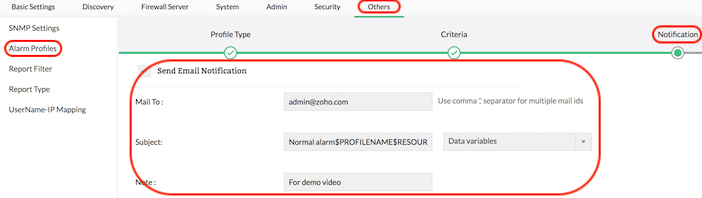
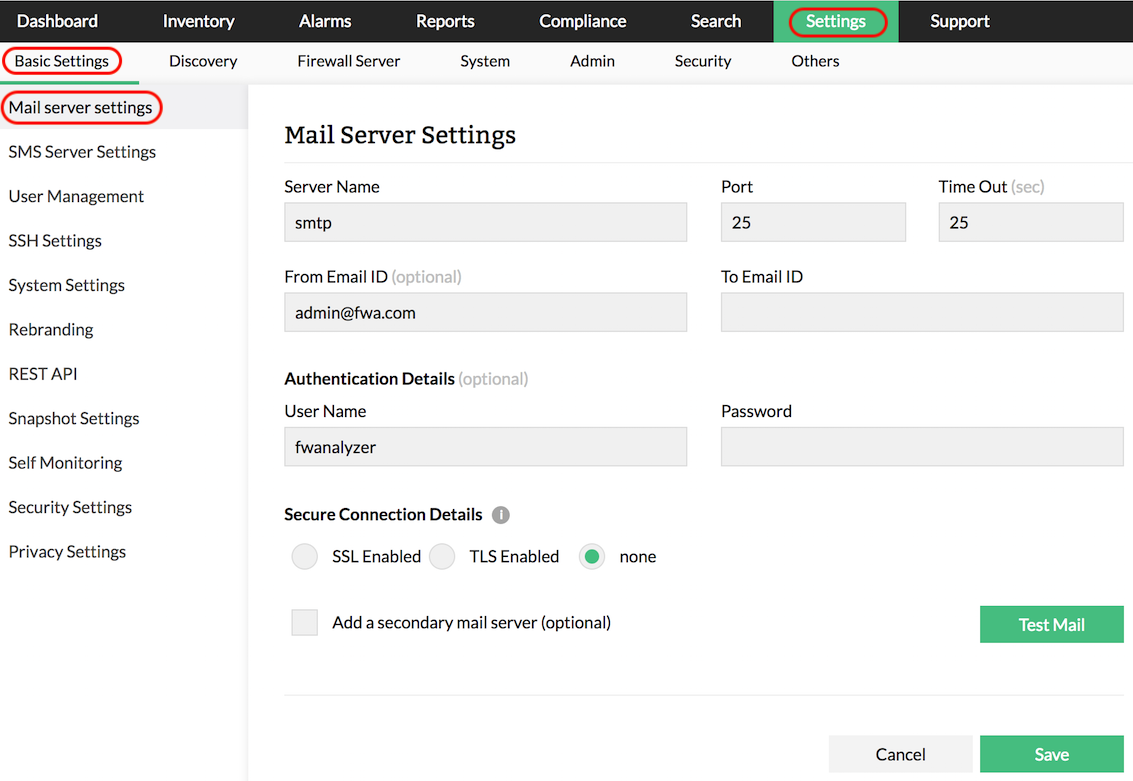
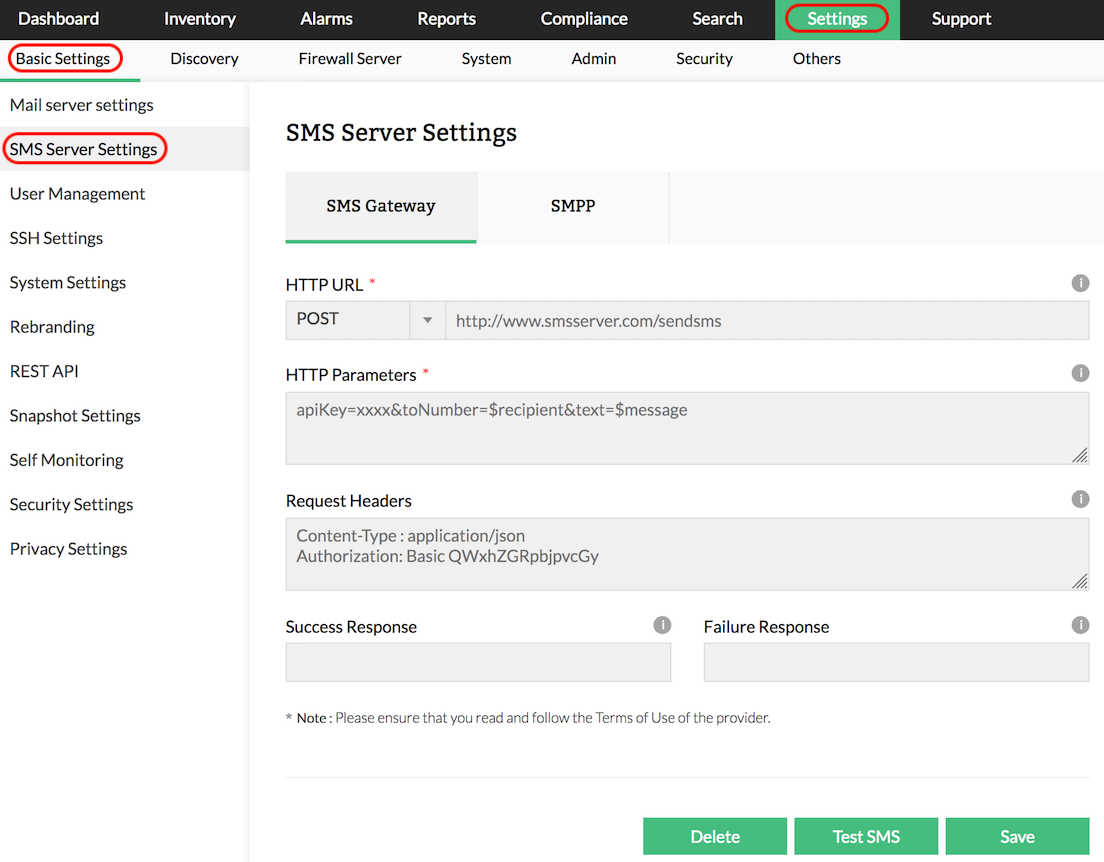
Email notification for alerts
Firewall Analyzer provides a simple alert notification mechanism for the administrators. It provides Email notification of Firewall Analyzer generated alerts in the administrator's email inbox. You can set up an Email notification to immediately notify any user when an alert is triggered.
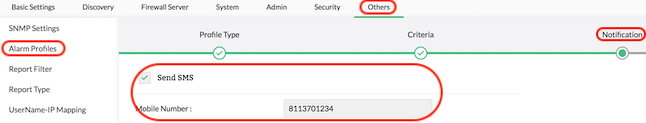
SMS notification for alerts
Firewall Analyzer provides a convenient alert notification mechanism for the administrators on the move. It provides SMS notification of Firewall Analyzer generated alerts in the administrator's mobile phones. You can set up an SMS notification to immediately notify any user when an alert is triggered.
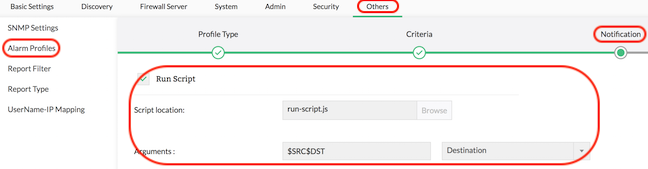
'Run Program' on alert triggering
Alerts Profiles can be configured to perform customized actions on alert trigger. To achieve this, Firewall Analyzer lets you to configure a program to be executed.
Featured links
Firewall Rule Management
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
Firewall Compliance Management
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Firewall Log Management
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
Real-time Bandwidth Monitoring
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Thank you for your feedback!