Firewall Forensics Tools with Raw Log Search & Reports
Firewall Analyzer enables network administrators to search the raw logs of Firewall to pinpoint the exact log entry which caused the security activity. The advanced search results based on raw firewall logs can be converted into report profiles. After search view the raw logs, formatted logs. Firewall Analyzer acts as a forensic log analysis tool, the simple search and advanced search are quite useful to law enforcing authorities for forensic analysis. Archived logs can be imported and security incident mining can be carried out by searching the raw logs.
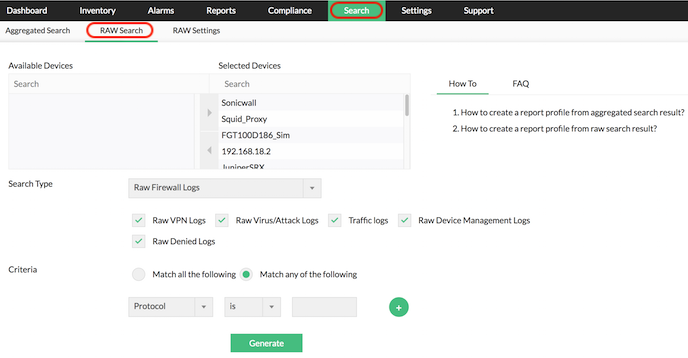
Advanced Search for Raw Logs
Firewall Analyzer lets you to mine the security incidents using the advanced search of raw Firewall logs. This makes security incident mining easy, which is otherwise a task with huge manually effort.
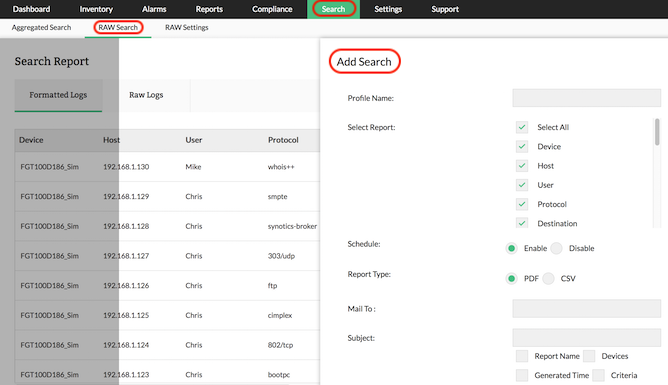
Converting Raw Log Search into Report
Firewall Analyzer lets you to create report profiles based on the advanced search results. The advanced search results will be from raw firewall logs. This firewall forensics tool enables an easy and convenient way of creating a report profile. You can also schedule these reports generation.
Refer Forensic log analysis page for more information on log frensics.
Thank you for your feedback!