Firewall Analyzer dons the role of Network Traffic Analyzer. Firewall Analyzer provides you (network administrators) an unique way to analyze the traffic of the network. This firewall traffic monitor measures network traffic based on the analysis of logs received from different network firewalls. Firewall logs are collected, archived, and analyzed to get granular details about traffic across each firewall. You need not deploy any hardware probes or collection agents to monitor network firewall traffic.
Network Traffic Analyzer part of Firewall Analyzer carries out traffic analysis which best suits non-NATed (Network Address Translation) networks. The traffic information captured from the Routers will not be suitable for non-NATed networks and it works good for NATed networks. Firewall Analyzer will be able to perform the traffic analysis easily, because the IP address/host name information of source and destination of traffic inside the network is available at the firewall log level.
From the Firewall log data, Firewall Analyzer extract a lot of information about the traffic. As a network administrator, you can visualize the behavior pattern of the network traffic from the traffic analysis reports. Network Traffic Analysis reports help in monitoring firewall traffic and answering the following firewall network traffic issues.
- Who is sending or receiving the traffic?
- Which host is sending or receiving the traffic?
- What is the traffic share of various protocols?
- When the traffic is getting clogged?
You will get traffic analysis reports for the following:
- Firewall wise traffic sent, received
- Intranet traffic report (internal to the Firewall)
- Internet traffic report or web traffic report (external to the Firewall)
- Protocol specific traffic report
Benefits of Reports
If your business depends on inward web traffic, it is critical to keep watching the traffic for maximum business usage and fair personal usage. In this scenario, traffic congestion will hamper your business and keep your customers away. Hence, both inbound and outbound traffic analysis reports are necessary.
Request for a personalized demo
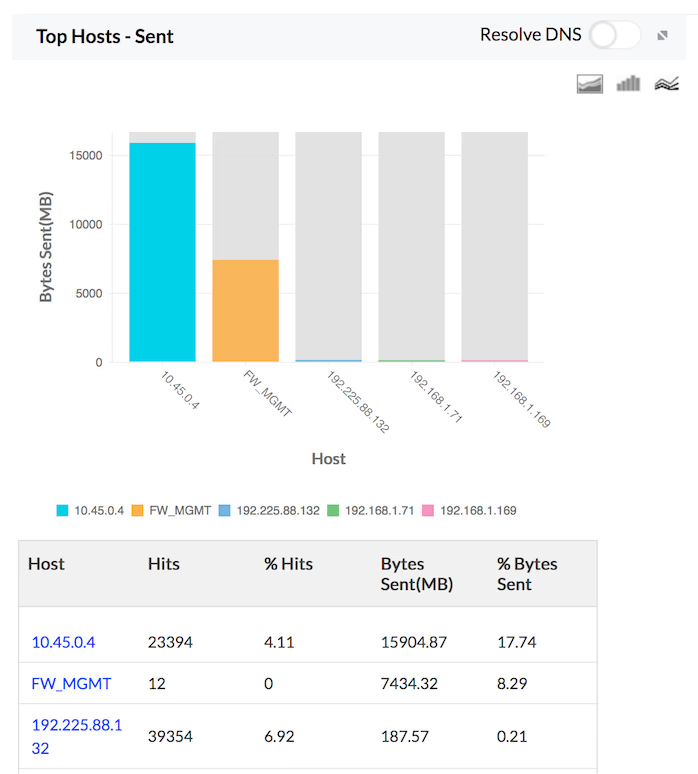
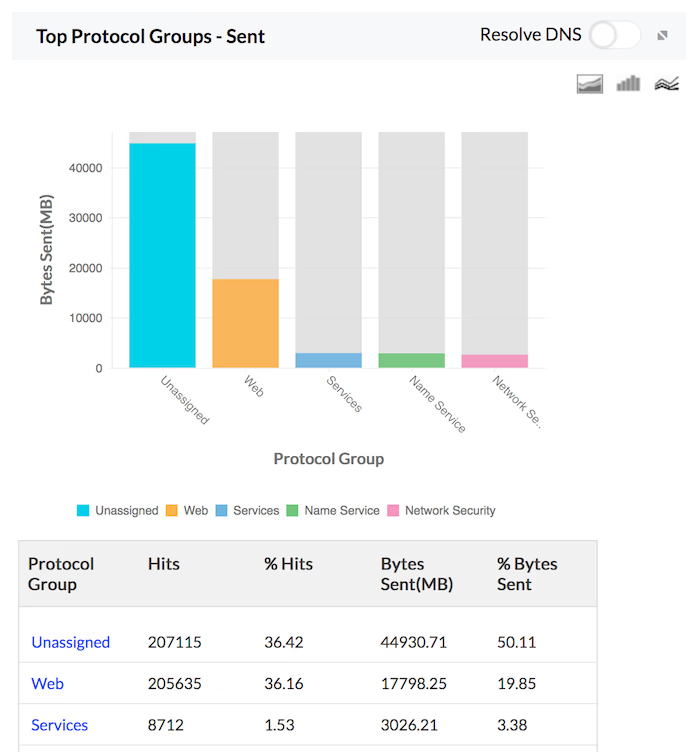
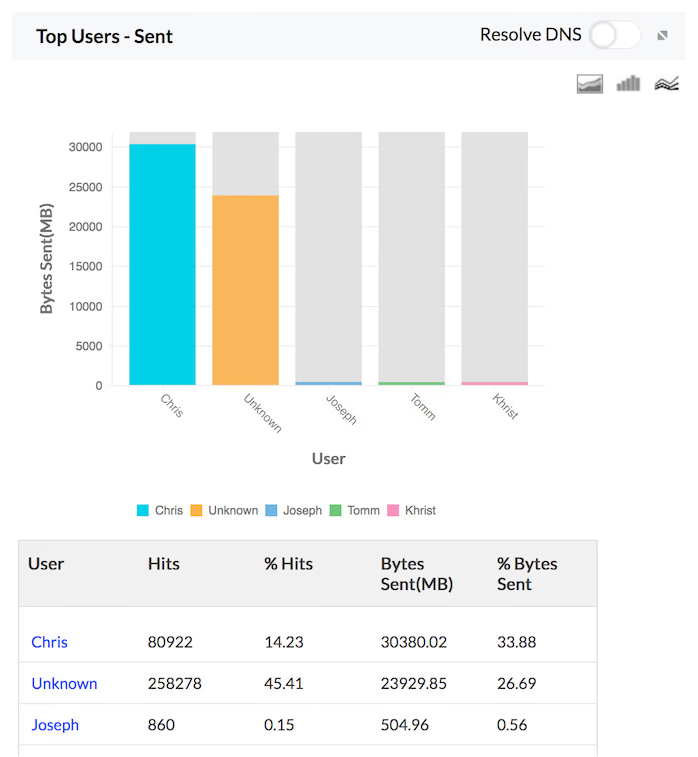
Traffic Sent
The details of the traffic sent by Hosts, Protocols and Users for the specific firewall are provided in the form of graph and table in the Traffic Reports. The granular details of the sent traffic for your network through each of your configured firewall can be drilled down.
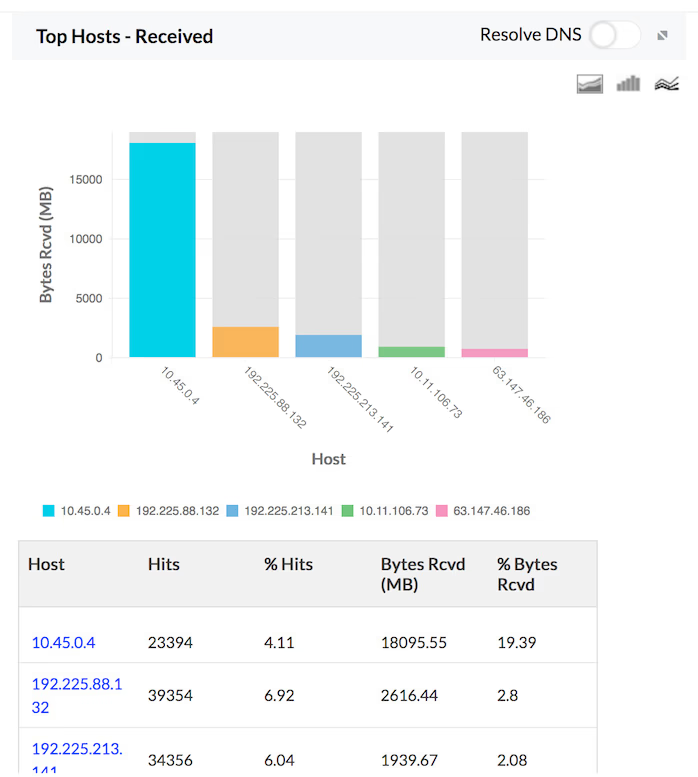
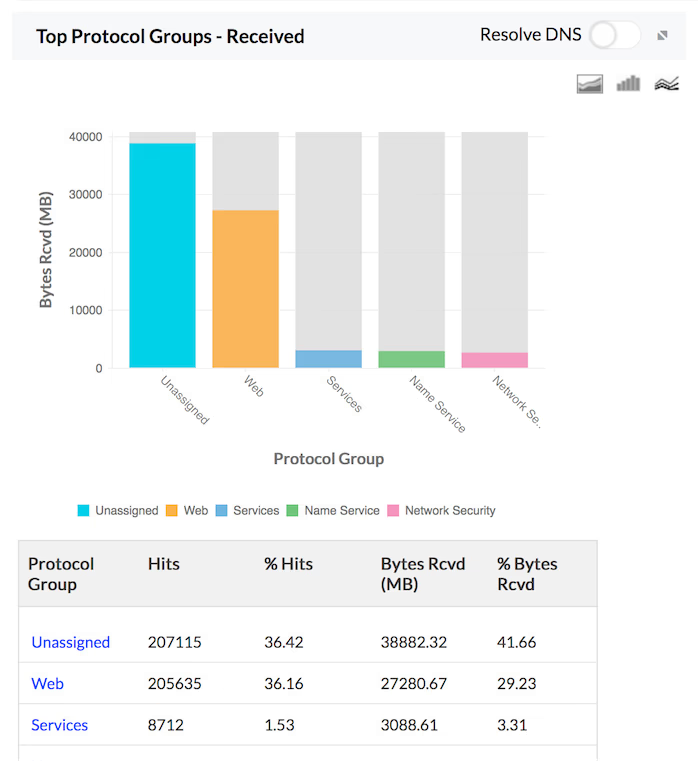
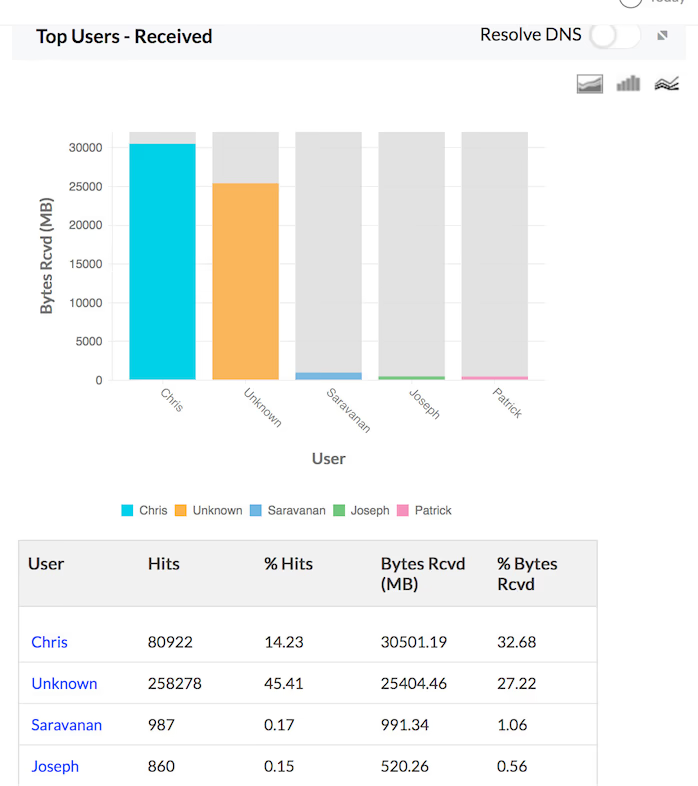
Traffic Received
The details of the traffic received by Hosts, Protocols and Users for the specific firewall are provided in the form of graph and table in the Traffic Reports. The granular details of the received traffic for your network through each of your configured firewall can be drilled down.
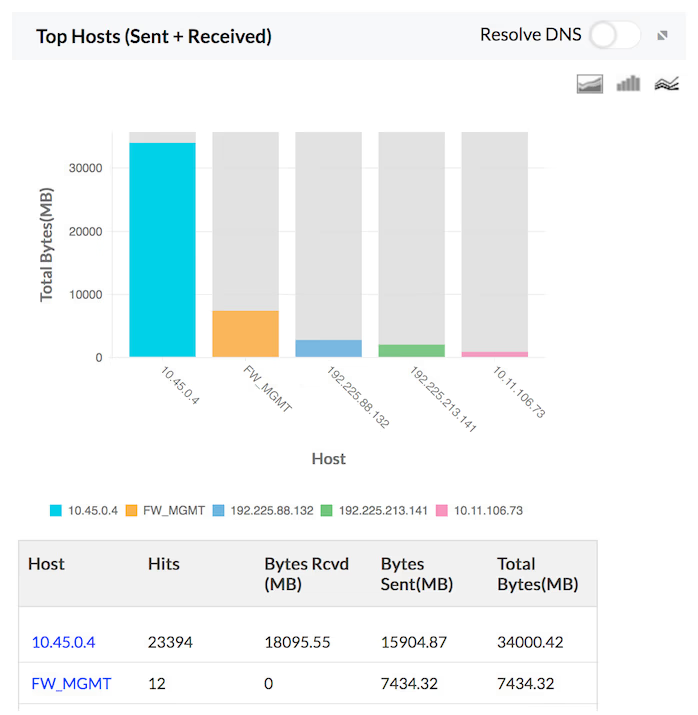
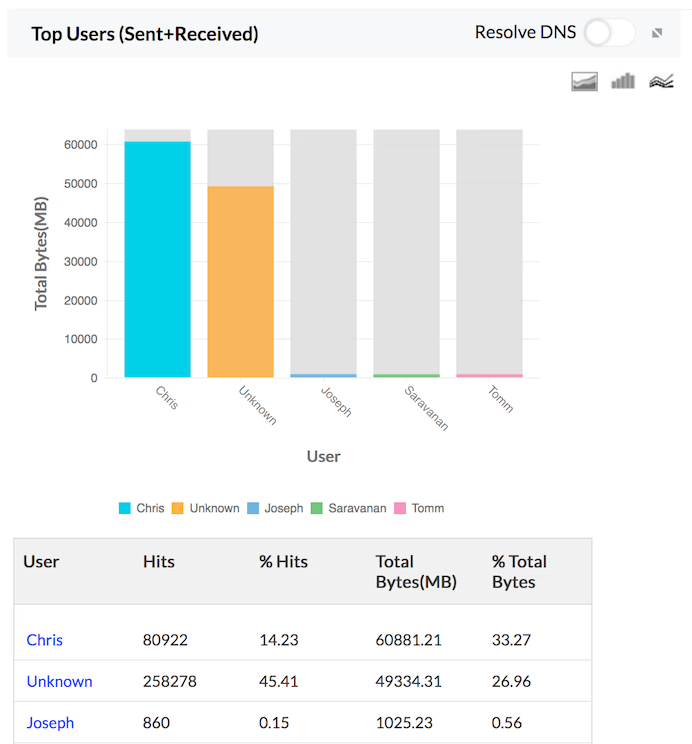
Total Traffic (Sent Plus Received)
The details of the total traffic (sent plus received) by Hosts, Protocols and Users for the specific firewall are provided in the form of graph and table in the Traffic Reports. The granular details of the total traffic for your network through each of your configured firewall can be drilled down.
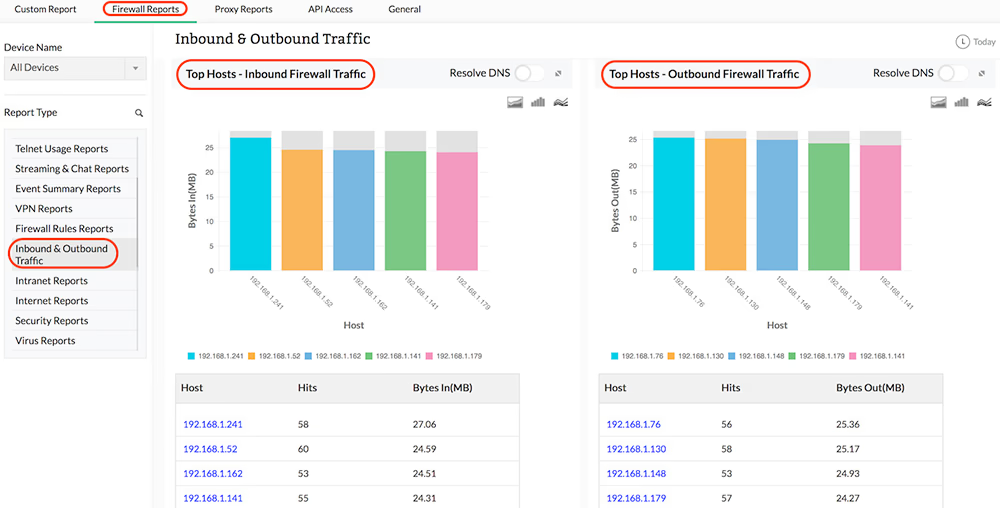
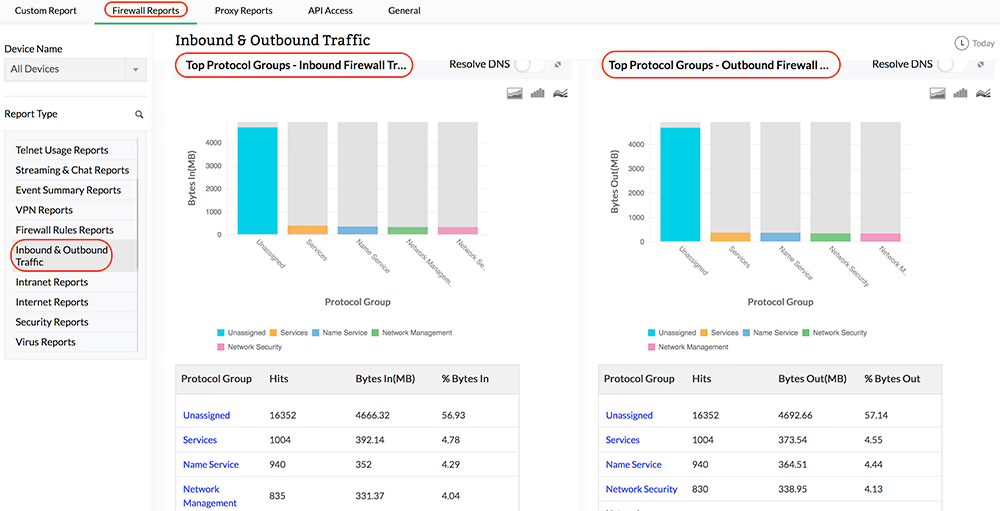
Inbound & Outbound Traffic
The details of the Hosts and Protocol Groups based inbound and outbound traffic of the network for the specific firewall are provided in the form of graph and table in the Inbound and Outbound Traffic Reports. The granular details of the inbound and outbound traffic for your network through each of your configured firewall can be drilled down.
Internet Traffic
The details of the total external traffic (sent plus received) of the network (Internet) by Top Conversations (External), External Hosts, External Protocol Groups, and External Servers for the specific firewall are provided in the form of graph and table in the Internet Traffic Reports. The granular details of the internet traffic for your network through each of your configured firewall can be drilled down.
Enhance bandwidth planning and security with detailed traffic analysis
- Visualize traffic patterns with intuitive dashboards.
- Detect bandwidth hogs and optimize resource allocation.
- Analyse traffic data for better threat detection.
Intranet Traffic
The details of the total internal traffic (sent plus received) of the network (Intranet) by Top Conversations (Internal), Internal Hosts, Internal Protocol Groups, and Internal Servers for the specific firewall are provided in the form of graph and table in the Intranet Traffic Reports. The granular details of the intranet traffic for your network through each of your configured firewall can be drilled down.
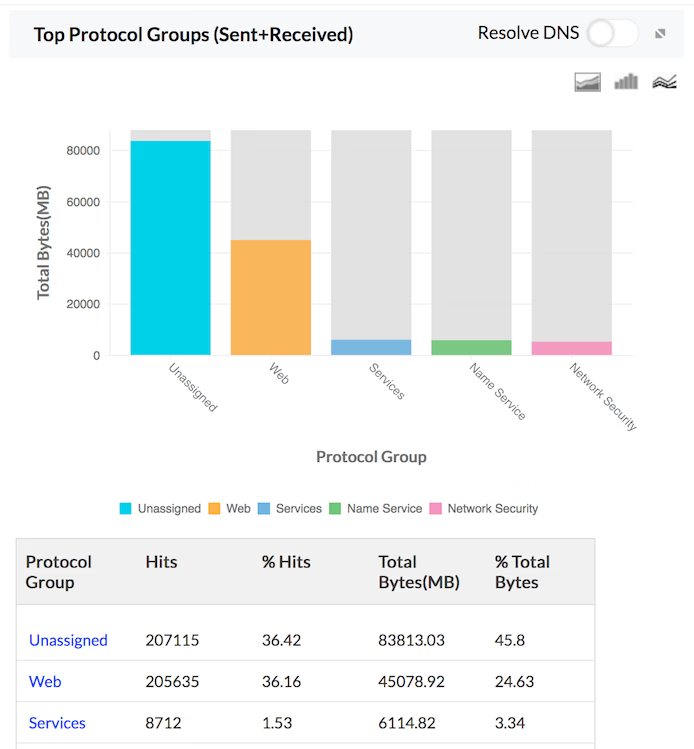
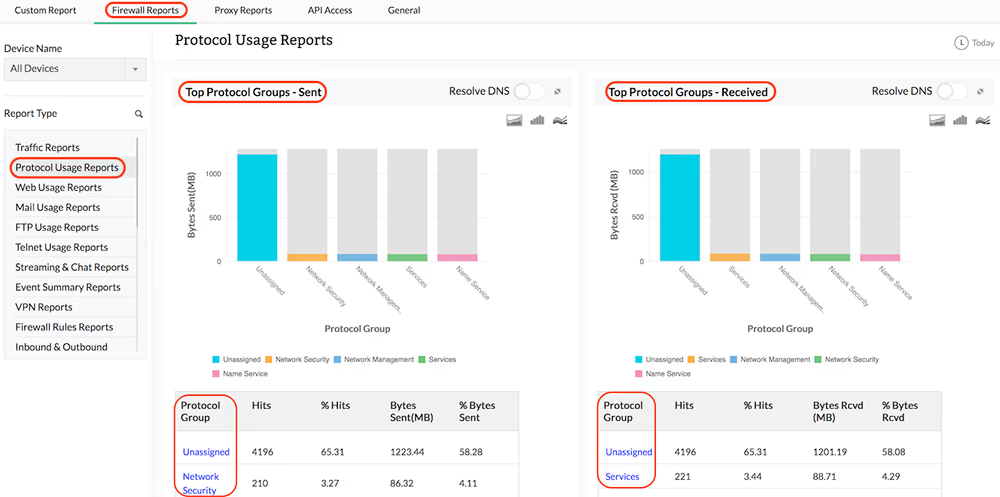
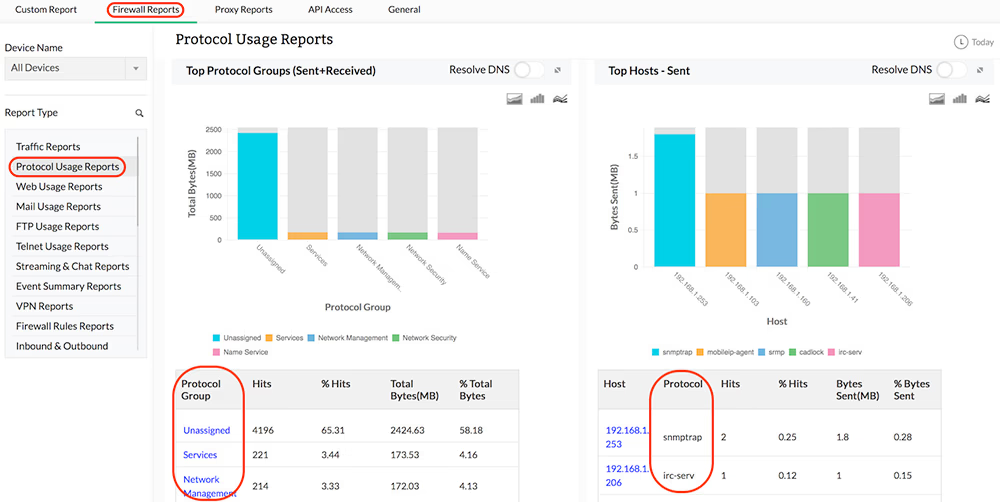
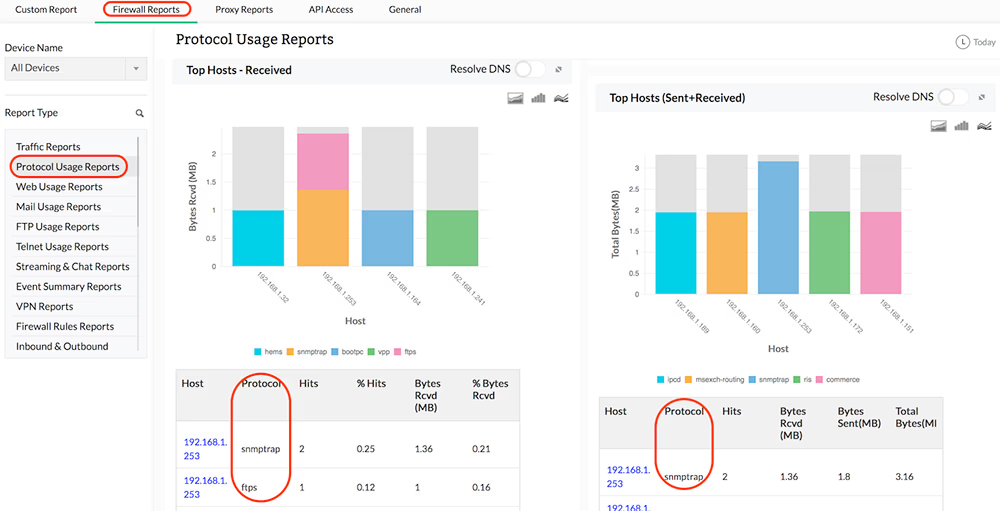
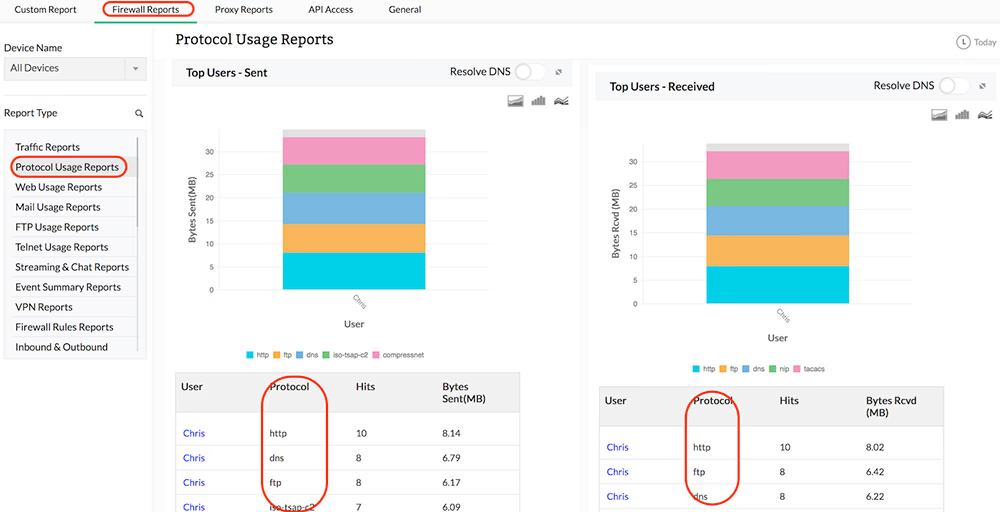
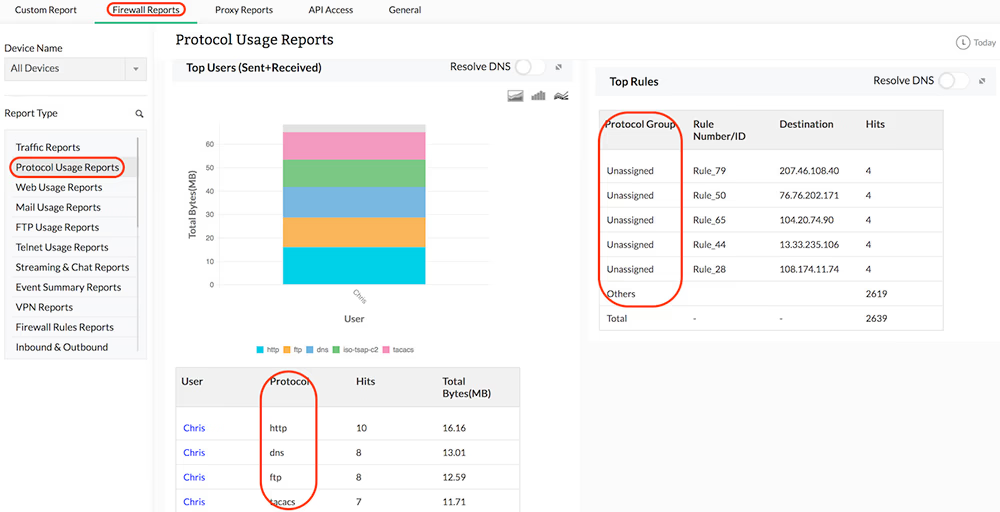
Protocol Specific Traffic
You can get protocol-wise bandwidth distribution across each of your network firewalls, thus giving you an idea of the type of traffic protocols being used or misused in your network environment. Firewall Analyzer also provides a protocol-wise break-up of inbound traffic and outbound traffic flowing across your network firewalls, along with consolidated measurement of total bandwidth (Total Traffic) consumed by each protocol, and by each firewall.
Thank you for your feedback!