- Cloud Protection
- Compliance
- Data Leak Prevention
- Bring your own device
- Copy protection
- Data access control
- Data at rest
- Data in transit
- Data in use
- Data leakage
- Data loss prevention
- Data security
- Data security posture management
- Data security breach
- Data theft
- File security
- Incident response
- Indicators of compromise
- Insider threat
- Ransomware attack
- USB blocker
- BadUSB
- USB drop attack
- Data Risk Assessment
- File Analysis
- File Audit
- Threat Glossary
Cybersecurity risk assessment
What is a cybersecurity risk assessment?
A cyber risk assessment is the process of analyzing your organization's IT and digital infrastructure, such as laptops, mobiles, and software applications for potential threats. Similar to a maze, cybercriminals identify a vulnerable endpoint and make their way up to the sensitive data in servers. With cyber risk assessments, you gain insights into your network's maze-like structure, starting from vulnerable endpoints and extending to critical servers. This information will help you stay on track with your security posture. This is why performing a periodic risk assessment is imperative.
When should a risk assessment be carried out?
Cyber risk assessments must be carried out during product launches, after changes are made to existing business workflows, and on a periodic basis. Certain data compliance regulations also have requirements stating the intervals at which risk assessments must be performed. For example, HIPAA requires organizations storing PHI to perform annual risk assessments.
Cyber risk assessment process
A cyber risk assessment is a five-step process, from meticulously curating IT and digital infrastructure—including networks, endpoints, identities, applications, and data—to assessing and securing them against potential threats. The steps include:
- Curating IT and digital infrastructure: As organizations embrace technology by expanding their IT arsenal, performing organization-wide risk assessments can get complex. To combat this, risk assessments are carried out by curating IT and digital infrastructure specific to a business unit, location, or department.
- Detecting threats and vulnerabilities: This includes identifying suspicious files, unauthorized access, and other unusual incidents that could compromise your network security.
- Analyzing the risks: The next step is to analyze the associated risks after you have identified potential threats and vulnerabilities. This involves assessing the likelihood of the vulnerabilities being exploited and the severity of the potential impact.
- Prioritizing the risks: Prioritizing the risks by accounting for factors like the likelihood of exploitation and potential impact can help you with a high level understanding of your organization's risk landscape. The 5x5 risk matrix or a grading risks on a scale of 0 - 100 could be a great mechanism to prioritize risks.
- Develop a risk catalog: Developing a risk catalog, periodically reviewing the changes in severity of known risks, and identifying new risks as they pop up can keep you on track with your organization's security goals. The database must highlight risk scenarios, identification dates, security controls, and risk levels.
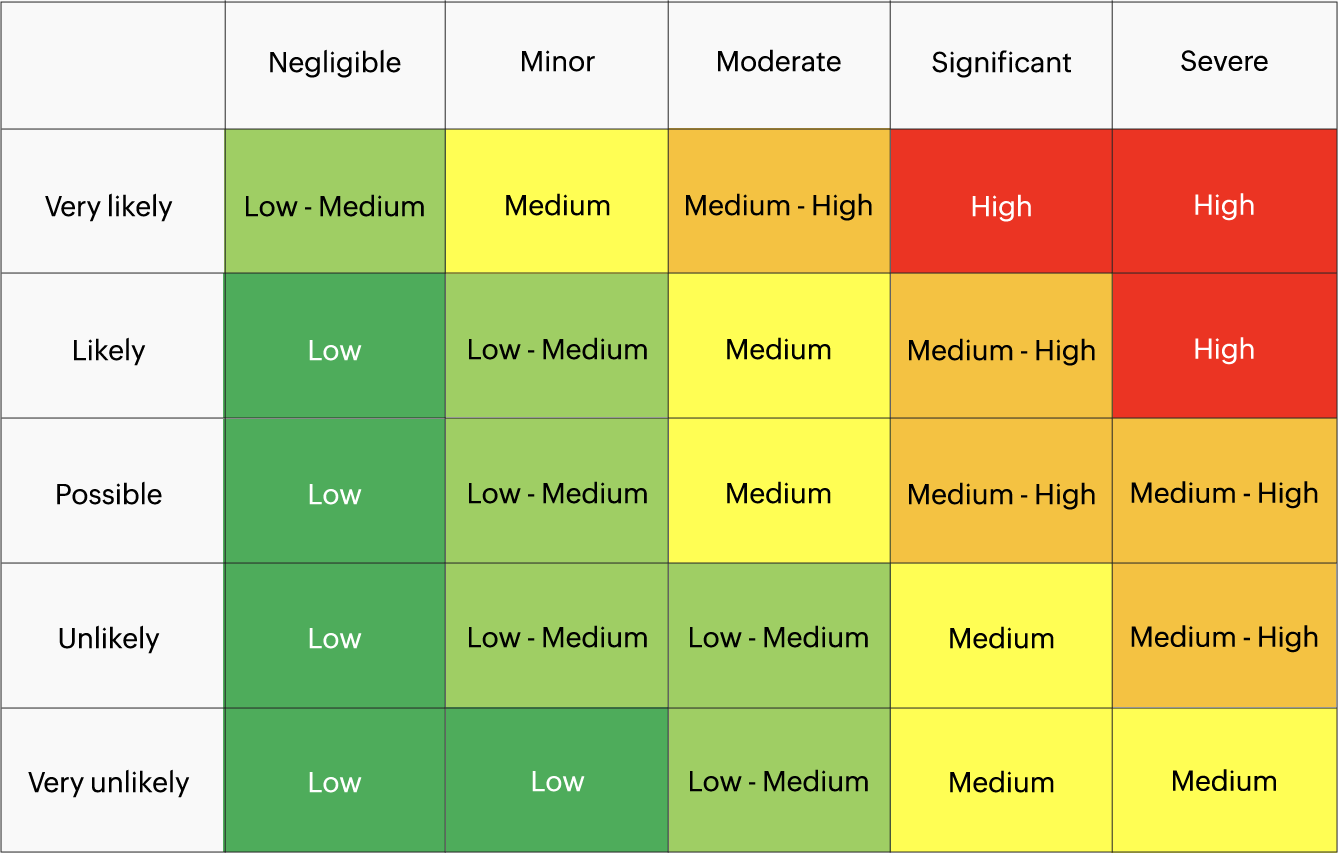
Cyber security risk assessment matrix
The 5x5 risk assessment matrix includes five rows and columns, with the columns representing the severity of the risk and the rows representing the likelihood of its occurrence. Risks can be categorized into 25 different cells, based on the severity of the risk and its likelihood. The spectrum varies from unlikely and not severe to highly likely and severe.
Cyber risk assessment framework
A risk assessment framework outlines an organization's approach to identify, assess, and manage risks to their IT and digital infrastructure. Depending on their network environment, organizations can opt to have their own custom-built framework or adopt industry standard frameworks. A few widely followed frameworks include:
- Factor analysis of information risk (FAIR): FAIR is a quantitative framework that measures, manages, and communicates information risk.
- OCTAVE: The operationally critical threat, asset, and vulnerability evaluation framework defines a risk-based strategic assessment technique for security.
- Threat agent risk assessment (TARA): The TARA framework identifies, assesses, prioritizes, and controls cybersecurity risk based on threats.
How can DataSecurity Plus prioritize and prevent cyber risk?
DataSecurity Plus offers a data risk assessment solution that identifies sensitive data across the network, analyzes the risks associated with the data identified, and prioritizes the risks, by assigning a risk score.
DataSecurity Plus solution is equipped with features, such as:
- Generate reports on sensitive data, their type, location, and the amount of sensitive data across the network with data discovery.
- Analyze and assign risk scores to users and servers with security violations.
- Prioritize and classify risks with data classification.
- Adhere to GDPR and HIPAA risk assessment guidelines.
Try DataSecurity Plus' data risk assessment solution with a free, fully functional, 30-day trial.
Download the free trial