- Cloud Protection
- Compliance
- Data Leak Prevention
- Bring your own device
- Copy protection
- Data access control
- Data at rest
- Data in transit
- Data in use
- Data leakage
- Data loss prevention
- Data security
- Data security posture management
- Data security breach
- Data theft
- File security
- Incident response
- Indicators of compromise
- Insider threat
- Ransomware attack
- USB blocker
- BadUSB
- USB drop attack
- Data Risk Assessment
- File Analysis
- File Audit
- Threat Glossary
Data loss prevention
What is data loss prevention?
Data loss prevention (DLP) involves systematically identifying, locating, and assessing data and user activities with content-and-context awareness to apply policies or proactive responses to prevent data loss. Data at rest, in use, and in motion must be under constant surveillance to spot deviations in the way enterprise data is stored, used, or shared. This includes analyzing data streams across endpoints, data shared with business associates, and data in the cloud.
Why is data loss prevention important?
Data loss prevention has grown beyond legacy systems of only physical and software controls for data protection. DLP is an integrated approach to identifying data that is most vulnerable and responding to threats to its security and integrity. The major reasons for deploying DLP are:
-
Blocking data breaches
3,932 breaches were publicly reported in 2020. Given the staggering rise in data breaches, it's essential to invest in trustworthy tools to help prevent incidents that would disrupt business.
-
Detecting insider activity
Data can be exposed by malicious insiders who stand to gain something from doing so, but unsuspecting users can also accidentally leak data due to negligence. Monitoring for signs of leaks is important to quickly spot and confine the impact of data loss.
-
Securing sensitive data
It's critical to locate and secure all personally Identifiable Information (PII), health records, and card payment information in your data stores. The strategic combination of data discovery, real-time change detection, and rapid incident response provided by DLP tools helps promptly identify an attack and thwart data exfiltration.
-
Complying with data regulations
PCI DSS, the GDPR, and other data privacy regulations require organizations to deploy data loss prevention software to protect sensitive data from accidental loss, destruction, or damage.
How does data loss prevention work?
Data loss prevention involves the following processes to effectively secure and prevent data loss:
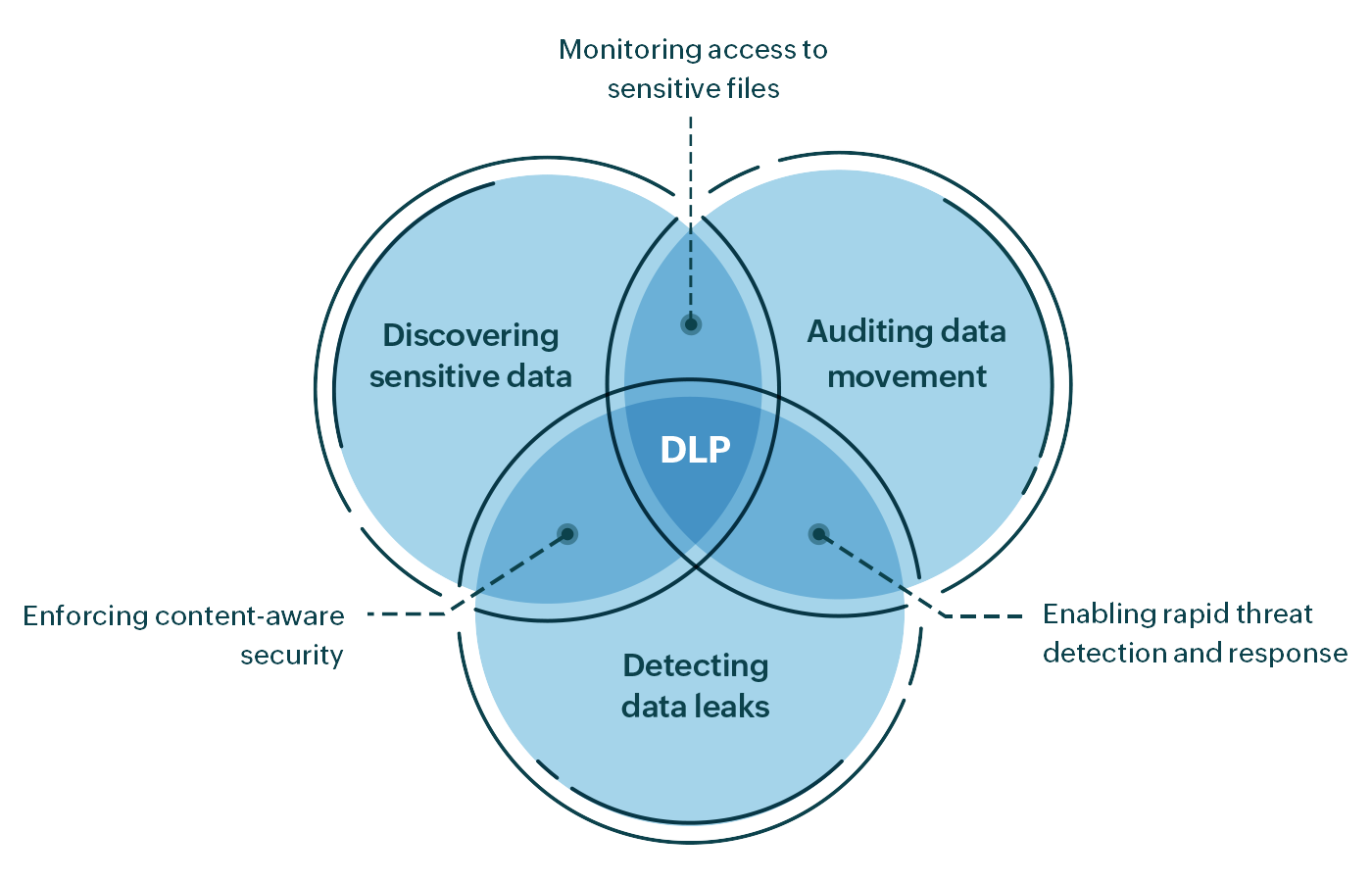
Identifying and classifying data
It's important to identify instances of sensitive data in an organization to ensure it's being handled safely. For example, data in use, in motion, or at rest can contain PII; if this data falls into the wrong hands, the resulting breach or data theft can be fatal to a business. A data classification tool can help not only with locating data but also classifying it according to the level of confidentiality and security required.
Data laws like the GDPR, HIPAA, PCI DSS, and others specify how data should be stored, treated, processed, and handled to prevent data thefts or breaches. Adhering to these laws not only helps secure data and prevent hefty violation fines, but also creates trust among customers.
Monitoring data movements
File access events have to be monitored in real time to detect ransomware attacks, insider threats, and other cyberthreats. File system auditing software can track file creation, deletion, modification, or security permission changes. It can also instantly spot unauthorized changes and unusual file activities indicative of cyberattacks, enabling IT teams to roll out remedial measures as soon as an attack is detected.
Unauthorized data transfers can be caused by privilege escalation or undue access to files. A file analysis tool comes in handy to identify permission inconsistencies and files with open or full access to rectify them. Ensure that the principle of least privileges (POLP) is followed to grant users only the rights needed to fulfill their job roles.
Detecting and preventing data leaks
Control what goes out of user devices, removable storage media, and other file sharing channels. Stringent policies regarding data access and transfer are necessary to ensure that data only reaches the right hands. Secure data by enabling multi-factor authentication (MFA), as it lowers the chances of user accounts from being hacked easily.A data loss prevention tool can help monitor files that are actively used and shared in your organization. For monitoring the cloud, cloud protection software can be used to analyze and block unauthorized web access over the internet.
Besides monitoring data movement, strengthen authorized data movements at the periphery using firewalls and antivirus applications. As a last security measure, data encryption can be used to defend against eavesdropping.
How DataSecurity Plus helps prevent data leaks
DataSecurity Plus is ManageEngine's unified DLP platform that offers the essentials needed to monitor and secure your data stores. It combines data visibility and security features to enable content-and-context-aware DLP.
| Process | Functionalities |
|---|---|
| Locating and classifying data |
PII scanning to pinpoint personally identifiable information like email addresses, phone numbers, etc. Data classification to automate file tagging to sort files as Public, Internal, Sensitive, or Restricted. Permission analysis to find permission inconsistencies that insiders or hackers can misuse for unauthorized data transfers. Data risk assessment to identify data privacy violations, locate the source, and rectify it. |
| Monitoring data movements |
File change monitoring for real-time reports on changes to file repositories. File integrity monitoring to ensure that data is safe from unauthorized changes, and to spot ransomware attacks indicated by excessive file renames or deletions. |
| Detecting data leaks |
Insider threat monitoring to prevent unauthorized transfers of business data out of the organization. File copy monitoring for tracking files copied by users to other network locations or removable storage devices. USB activity monitoring to control or block removable storage devices and peripheral devices. Cloud application discovery for monitoring web traffic from endpoints and managing file uploads. |
Schedule a personalized demo or try all of these features in a fully functional, 30-day trial.
