- Cloud Protection
- Compliance
- Data Leak Prevention
- Bring your own device
- Copy protection
- Data access control
- Data at rest
- Data in transit
- Data in use
- Data leakage
- Data loss prevention
- Data security
- Data security posture management
- Data security breach
- Data theft
- File security
- Incident response
- Indicators of compromise
- Insider threat
- Ransomware attack
- USB blocker
- BadUSB
- USB drop attack
- Data Risk Assessment
- File Analysis
- File Audit
- Threat Glossary
Incident response
What is incident response?
Incident response refers to the strategy and measures organizations take after a cyberattack to minimize damage to their operations, data, and infrastructure. Incident response examples include recovering data after a ransomware attack, stopping insiders or hackers from leaking sensitive data, rebuilding cybersecurity measures, and notifying authorities and customers about data breaches. To address the various cybersecurity risks, a good deal of planning is required to create incident response measures for different scenarios.
Importance of incident response
- To prevent cyberattacks, you have to be prepared in the event of one. You need to review existing implementation and historical records, data backups, and compliance requirements. These and other important aspects need to be planned and collated in a dynamic incident response plan.
- If data has been stolen or leaked, the organization must do what it can to prevent it from being exposed on the dark web and make the details of the breach public. This step and other legal stipulations must be met with to avoid fines, loss of trust, and loss of business. Organizations need to notify stakeholders and customers when their data has been compromised.
- Incident response is necessary to recover after an attack. A good incident response will prevent business operations from being suspended or bottlenecked and help the organization recover from an attack quickly. When the steps to be taken immediately after an incident are clearly defined, it is easier to mitigate the damage.
- Incident response also involves recording the events leading to the attack. Audit trails serve as useful records to prevent the same attack from reoccurring. Effective incident response requires foresight and planning; So a sound incident response plan is essential.
Types of security incidents
Several security incidents are launched by bad actors on a day-to-day basis, targeting businesses of all sizes. Some of these attack types are listed below:
- Phishing: Using this method, cybercriminals aim to deceive people by crafting websites and email addresses that appear legitimate to trick end users into clicking links and providing their sensitive personal information.
- Insider threats: Employees misuse their legitimate privileges to steal sensitive data or can unintentionally be the root cause for compromising data security due to a lack of awareness or carelessness in handling data.
- Ransomware attack: Ransomware is malicious software that encrypts critical files and denies access to them until a ransom is paid by the victims. The primary indication of a ransomware attack is mass data encryption. Usually, the victim pays a hefty ransom in exchange for a decryption key or a tool that decrypts the files. But even when a ransom is paid, data decryption is not guaranteed.
- Distributed denial of service (DDoS) attacks: In this type of attack, systems and servers are overwhelmed with excessive traffic, making them unavailable to legitimate users. This involves a network of compromised devices called a botnet, which the malicious user controls remotely to send illegitimate traffic.
What is an incident response plan?
An incident response plan prescribes the approach to be followed by businesses after a cyberattack. An effective incident response plan provides measures to tackle an ongoing crisis and prevent the same attack from recurring. It has detailed instructions for the IT security team and other concerned teams on how to detect, respond to, and avoid cyberattacks in the future.
How to create an effective incident response plan
The National Institute of Standards and Technology and SysAdmin, Audit, Network, and Security Institute have developed industry-standard incident response frameworks that are widely followed. Both frameworks have similar components, which are summarized below:
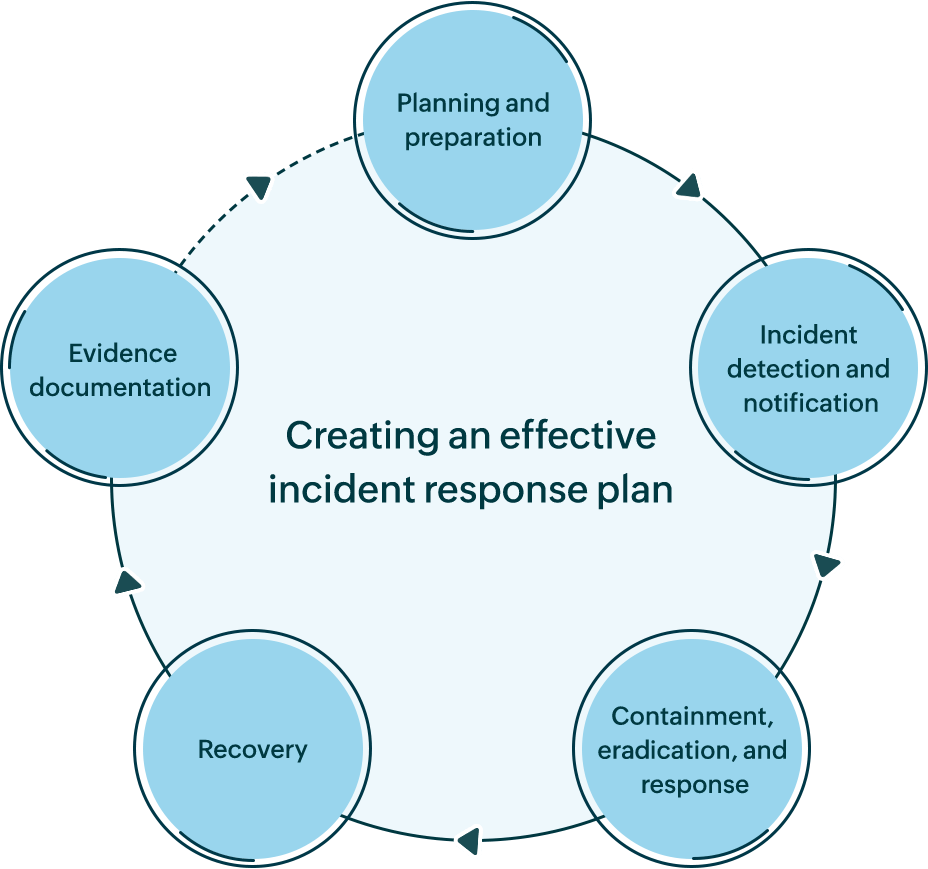
- 1. Planning and preparation
Draft an organizational policy defining the right people with the right duties along with the required time limit to respond. Include all steps from incident detection to post-incident documentation to guide the teams involved. Communicate with the admin, security, and privacy teams regarding the policy and provide adequate security training.
- 2. Incident detection and notification
Implement security incident response software tools to detect system and network intrusion instantly. Watch out for ransomware indicators using ransomware detection software. Prevent data theft and manipulation attempts by insiders using insider threat monitoring software.
- 3. Containment, eradication, and response
Once an attack has been detected, all efforts need to be focused on stopping the further spread of the attack throughout the network and limiting the damage done. Cut off the source of the malware infection by isolating the infected device or disabling the compromised user account.
- 4. Recovery
Start the recovery phase once you've ensured that the cyberattack has ended and affected devices and user accounts are rid of malware, if any. Take stock of stolen or breached data and inform the concerned stakeholders. Restore breached security measures and data backups to resume normal operations.
- 5. Incident trail documentation
Document all the events during and after the incident, including the source of infection or attack, response to contain the attack, and remediation measures implemented. This will help meet the legal requirements of data privacy compliance and help highlight data security loopholes in the network.
Safeguard your data with DataSecurity Plus
ManageEngine DataSecurity Plus provides a unified platform of data visibility and security capabilities. Zero in on your file security and storage protection by proactively monitoring file servers and securing endpoints. With DataSecurity Plus' data protection solution, you can:
- Identify the whereabouts of sensitive data like customers' addresses, email IDs, health records, and more using our data discovery and data classification tool.
- Audit Windows file servers to know about key file events like file modifications, deletions, and permission changes using our file integrity monitoring tool.
- Analyze your file security posture by reviewing effective permissions and inherent permission hygiene issues using our security permission analyzer.
- Detect potential ransomware intrusion in real time via customizable alert-and-response functions using our ransomware detection tool.
- Monitor endpoints for signs of insider activity, including file copy actions, potential web uploads, USB activity, and more using our DLP solution.
- Block access to harmful websites and applications and monitor uploads to cloud storage services like Dropbox, SharePoint, and more using our internet filtering tool.
Schedule a personal demo with one of our experts to try all these features and more. Alternatively, you can download a free, fully functional, 30-day trial.
Download your free trial