What is deep packet inspection?
With hybrid working a normal part of life, new technologies are used everyday in conjunction with the landslide of data invariably transmitted through networks. It's crucial to provide a seamless user experience with high uptime, quick problem resolution, and insightful intelligence. To accomplish this, it is important to have end-to-end monitoring of the network.
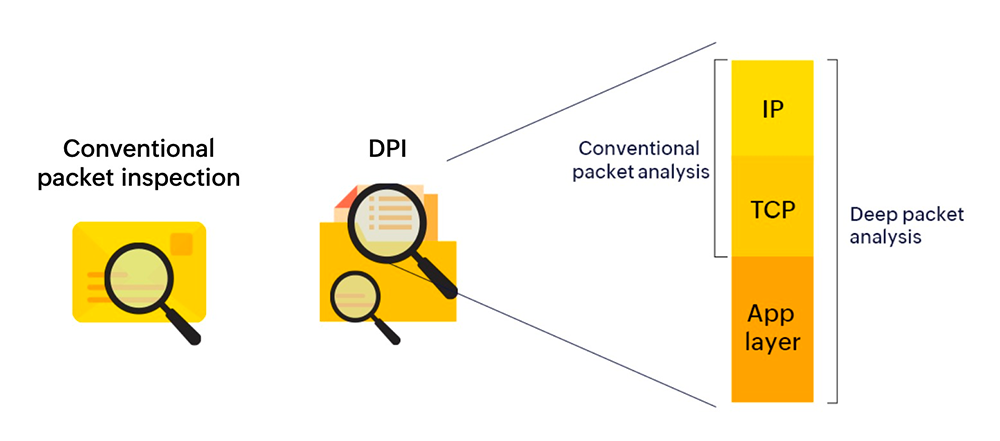
Deep packet inspection is a technique used to inspect and analyze the content of packets in real time as they flow through a network, enabling real-time analysis and decision-making. It is used for a variety of purposes including security, traffic management, data exfiltration, policy violations, malware, and quality of service. DPI allows for the examination of packet data at the application layer of the network, beyond just the header information, which provides more information about the content of the packet. It involves looking at the actual payload or content of a packet, including the data being transmitted and the applications that are generating it.
How deep packet inspection works
Deep packet inspection evaluates packets based on rules assigned by network admins or ISPs. Unlike conventional packet filtering, Deep packet inspection monitors the contents of these packets as well as identifies where it came from and the service or application that sent it. It then decides how to handle this traffic based on the predefined rules, and can work with filters to redirect non-business critical traffic coming from specific online services or IP addresses.
Deep packet inspection software is used with firewalls and intrusion detection systems as an addition to traditional security systems to cope with the increase in volume, and complexity of data and security threats or anomalies.
Deep packet inspection vs. conventional packet filtering
In an organization, information being transmitted as packets of data pass through different control points throughout the network. Until a few years ago, conventional packet filtering was the best available option to manage network traffic without entirely slowing down the organization’s network. However, this had it’s limitations. Conventional packet filtering only reads the header information of each packet, which includes data such as IP address and port number. This made it easier for threats to evade firewalls. With today’s improved processing power and the need for better visibility,Deep packet inspection monitors each packet, including data and metadata from each device on the network without completely slowing down the network.
The system can then automatically decide how to handle each incoming packet based on these rules, enabling an organization to prevent hidden threats and attacks.
According to a study by Verified Market Research the deep packet inspection (DPI) market size was valued at USD 16,484.81 million in 2021, and is estimated to reach USD 114,043.93 million by 2030, registering a CAGR of 24.61% from 2023 to 2030.
Deep packet inspection techniques
DPI is primarily used by firewalls and intrusion detection systems for detecting malware and other security threats, and to be a proactive method to monitor the overall health and performance of your network infrastructure. There are several techniques used to perform DPI and the four major DPI techniques include:
Pattern or signature matching
Pattern or signature matching is a method that monitors every network packet to analyze and compare its contents against an index of common attacks and previously identified threats. Constantly updating this threat intelligence database enables effective security against attacks. However, this is also a major limitation to this method, as pattern or signature matching is restricted to detecting only known attacks and cannot identify new or unfamiliar attacks.
Protocol anomaly
Protocol anomaly ensures the prevention of unknown attacks passing through the organization’s network. It uses the “default deny” method that denies all access to a system or network by default, and then selectively allows access only to those resources that are permitted. It is commonly used in firewalls and other security systems to prevent unauthorized access to a network. When correctly configured, this method ensures that only business critical connections are permitted to pass through the network, only authorized users and devices are able to access these resources, and legitimate traffic is not blocked.
Intrusion prevention system (IPS)
An IPS is a type of intrusion detection system that goes beyond just detecting malicious traffic. It is a technology that monitors network traffic for signs of potential threats or malicious activity and takes action to prevent or block these threats. It typically operates by inspecting network traffic in real time, looking for patterns or signatures of common attacks or anomalies that indicate potential attacks. An IPS may use a range of techniques including signature-based detection, behavior-based detection, and anomaly-based detection.
Heuristic and behavior analysis
Heuristic analysis and behavior analysis are two commonly used techniques that detect and prevent security threats activity.
Heuristic analysis is an approach where an automated security tool or software analyzes network traffic behavior to identify patterns or attributes that may indicate a threat. It uses a set of rules or algorithms to detect known attack patterns or suspicious behavior and then flags any potential matches. Heuristic analysis is often used to identify previously unknown or "zero-day" attacks, where new malware or malicious behavior is being used that may not have a known signature.
Behavior analysis is a technique that monitors the activity of systems or software for anomalous or suspicious behavior. It works by setting baselines for what is considered normal behavior, and alerting on the occurrence of or blocking any activity that breaks pattern and deflects from those baselines. Behavior analysis is used to identify malware or other malicious activity that may not have a known pattern or signature.
They complement traditional signature-based detection methods by enabling security tools to identify and respond to new and previously unknown threats.
Use cases
There are several uses to deep packet inspection, such as blocking malware, lawful interception, intrusion detection, detecting the recipient and sender, and network management.
Blocking malware
DPI, when combined with threat detection, can be used to block malware before it affects your network. This process includes detecting existing threats based on pattern matching and heuristic analysis.
Content policy enforcement
DPI allows organizations to block or limit access to any unauthorized application. It can be used to detect or block traffic patterns that violate policies and unauthorized data access.
Stopping data leaks
DPI helps with the management of the incoming and outgoing traffic, and network activity. It can be customized to filter out sensitive data to prevent potential leaks.
Challenges and limitations of deep packet inspection
All technology, no matter how beneficial, has its challenges and limitations. The three major challenges and limitations of DPI are:
- While an extremely efficient tool to detect and prevent Denial of Service, overflow and buffer attacks, DPI can facilitate the creation of similar attacks making the network vulnerable to the same threats it provides security against.
- Deep packet inspection can be a bandwidth hog that causes a strain on the network and firewall due to the huge volume of data involved.
- A highly effective deep packet inspection tool can be complex and hard to manage. It also required constant updates and revisions for optimal functionality.
Benefits of deep packet inspection
Some of the key benefits of deep packet inspection solutions include:
- Improved network security: DPI can be used to detect and prevent a wide range of security threats, including malware and spam. By analyzing the content of each packet, it can detect attacks that may surpass traditional firewall and intrusion detection systems.
- Quality of service and compliance monitoring: DPI can be used to prioritize network traffic based on its content or source, ensuring that mission critical applications and users receive the necessary bandwidth. This improves the overall network performance and user experience. DPI can also be used to ensure compliance of policies, and detect and flag any traffic that violates regulations.
- Troubleshooting: DPI can be used to identify the root cause of network traffic issues such as excessive packet loss, latency, or jitter by analyzing network traffic at a granular level.
- Bandwidth management: DPI primarily works as a security system to detect applications that are bandwidth hogs. It also effectively monitors and controls network bandwidth usage, reduces congestion, and prevents network slowdowns.
Integrating DPI in your organization
Deep packet inspection(DPI) offers a number of benefits when it comes to an organization’s network security and traffic. ManageEngine NetFlow Analyzer is a Deep Packet Inspection Engine that monitors and measures both application response time and network response time to identify the root of your network traffic issues and anomalies.
Click here to learn more about ManageEngine’s Deep Packet Inspection agent. If you’d like to learn more about integrating DPI at your organization, we’d love to speak with you to optimize your DPI processes with NetFlow Analyzer. Schedule a free personalized demo to discuss how we can help implement DPI at your enterprise, or start a free 30-day trial.
More on Deep Packet Inspection
What does deep packet inspection do?
+
Deep packet inspection is an advanced approach to examine your network traffic. It analyzes the packet headers and payloads unlike the conventional packet filtering technique, where only the header part will be analyzed.
Why use deep packet inspection?
+
Deep packet inspection can be beneficial to enterprises to analyze the network packets, and identify bottlenecks by gathering data such as response times.
How is deep packet inspection done?
+
Deep packet inspection is a process of analyzing the network traffic to provide a complete picture of data packets flowing through the endpoints to verify which is at fault; whether application or network.