In the ever-evolving landscape of cybersecurity, detection engines stand as vigilant sentinels, tirelessly scanning for threats to our digital assets. At its core, a detection engine is a software component that analyzes data, identifies anomalies or suspicious patterns, and triggers alerts or actions based on predefined rules or machine learning models. Detection engines operate on the fundamental principle of identifying deviations from normal behavior.
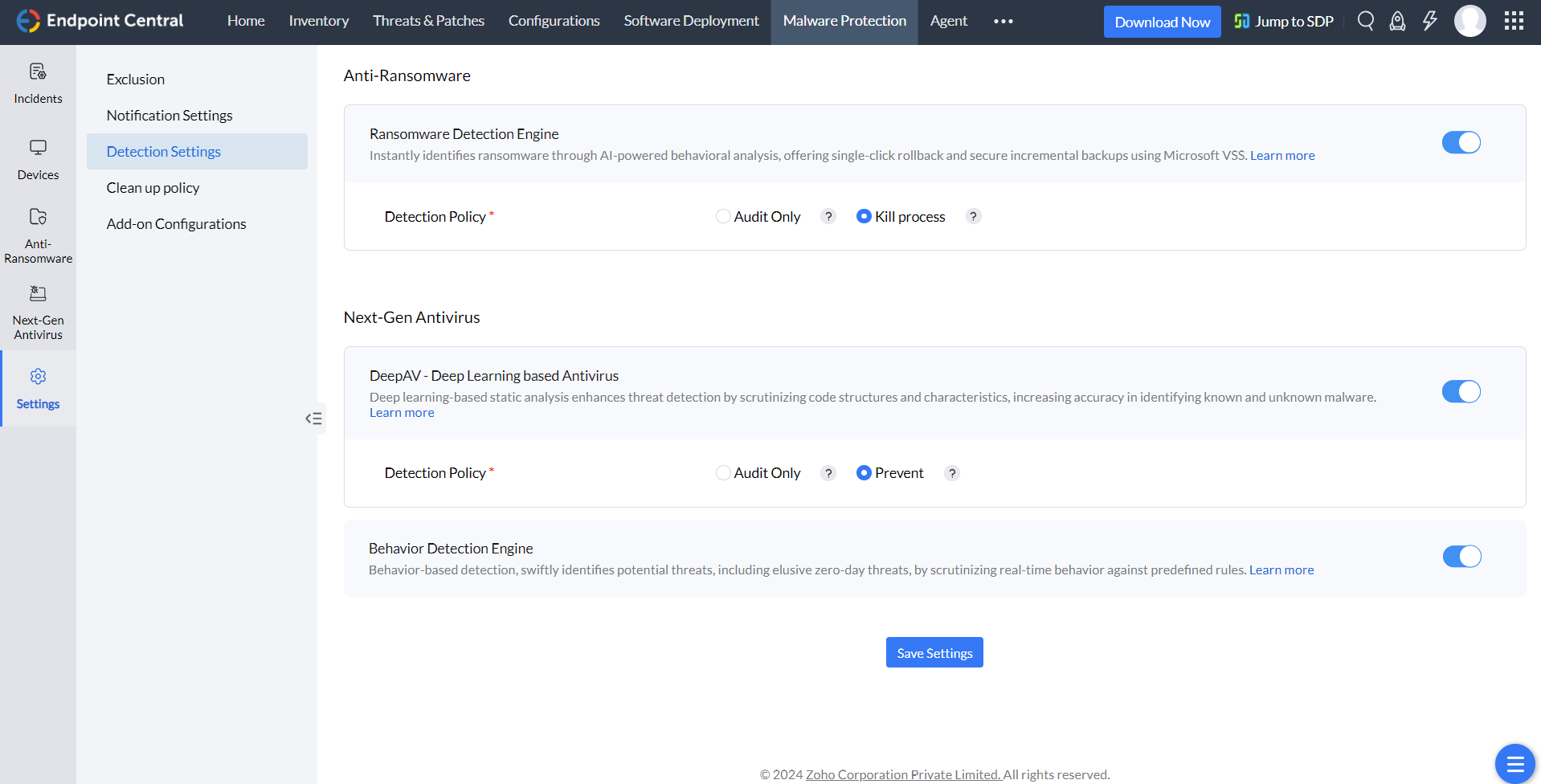
To configure the detection engine settings in detail, navigate to the Settings tab and click 'Detection Settings'.
This document explains the three core detection engines employed by ManageEngine Endpoint Central Malware Protection and their significance during policy configuration. Understanding these engines empowers you to tailor your policies for optimal protection.
In this section:
Ransomware often operates stealthily, lying dormant until it encrypts files or blocks system access. The end users are frequently unaware of the infection until confronted with a ransom demand or the loss of their data. By detecting ransomware early, before it causes significant damage, individuals and organizations can proactively respond and potentially prevent irreversible data loss.
Designed specifically to counter ransomware attacks, the Ransomware Detection engine utilizes a proactive defense strategy as follows:
The Data Exfiltration Engine is designed to identify and prevent unauthorized transfer of sensitive data from endpoints to external or malicious domains. Data exfiltration often occurs silently, with attackers disguising their activity as normal network traffic. By detecting unusual upload behavior early, organizations can intervene before critical information is exposed or compromised.
The Data Exfiltration Engine employs an anomaly-based machine learning approach with the following capabilities and configurations:
Leveraging the power of deep learning, the DeepAV Engine provides advanced malware detection capabilities. The major features and policy configurations are as follows:
The Behavior Detection Engine operates by continuously monitoring application behavior for suspicious activities that suggests a potential malware threat. The following are the main features and policy configurations: