Automatically analyze VPC flow logs to monitor critical changes to VPCs, network gateways, VPC endpoints, VPC route tables, subnet, and VPC routes. Define a custom alert criteria to get notified on suspicious changes to VPCs, and get insights into who made the change, when, and from where.
Learn More
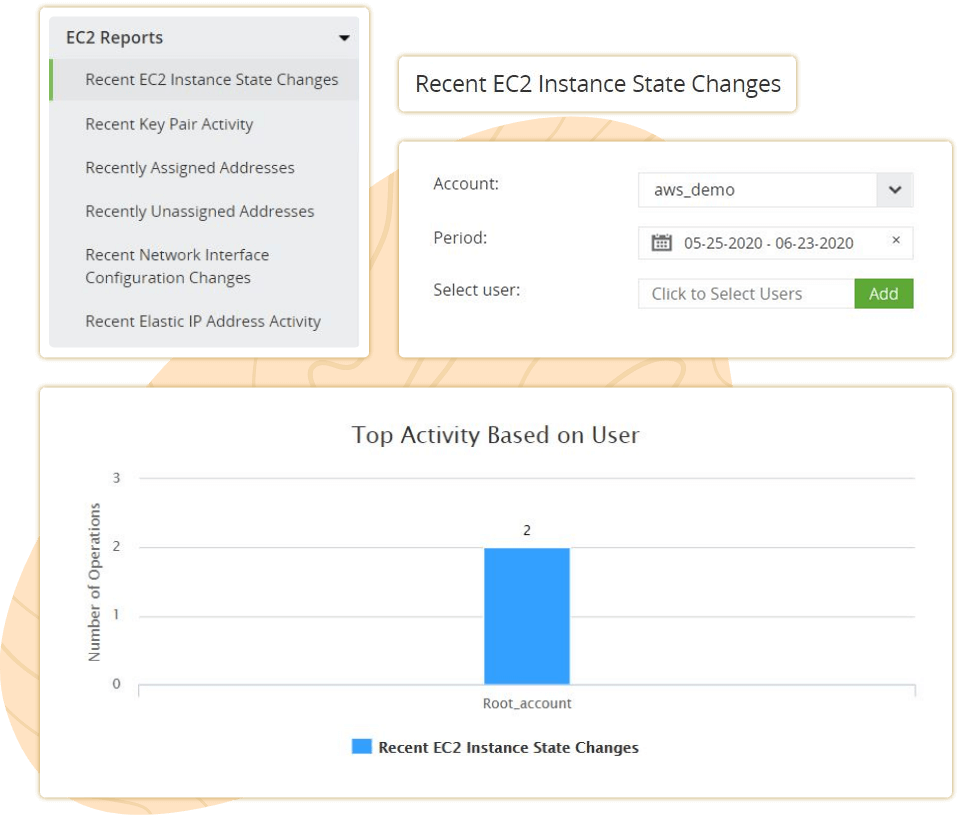
Track EC2 instances and get detailed reports on watchful AWS EC2 instance events such as starting, rebooting, and stopping. Get insights such as name of the event, time of occurrence, source IP address, who made the change, etc. using the interactive analytics dashboard. Customize alert profiles that get triggered when critical events such as EC2 rebooting or unauthorized changes occur. Additionally, get to know who performed the instance events, from where, and when, to double down on the source of every event and prevent malicious inside threats.
Track your AWS RDS error events, recent DB snapshot activities, and DB cluster activities with intuitive analytical reports. Additionally, with Log360, you can monitor the RDS instances' recent activities. Get insights into who performed the events, when they were performed, and from where. Log360 provides insights into the recent database security group configuration changes that help you to spot suspicious and unauthorized changes to RDS access.
Learn More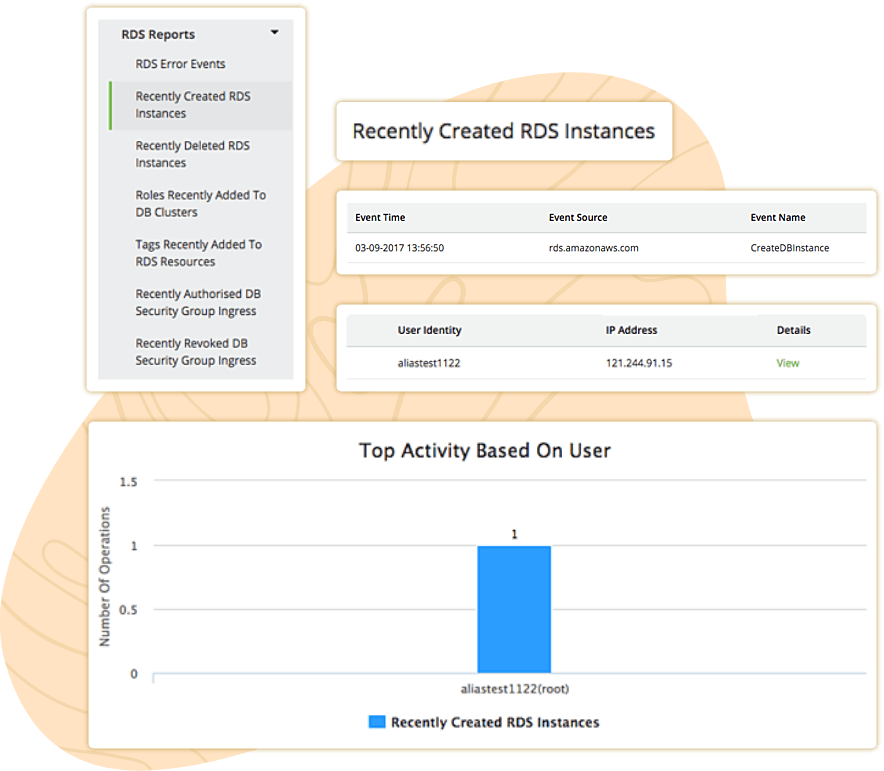
Log360 aggregates ELB access logs from the S3 bucket to monitor and analyze traffic patterns, operational efficiency, data on access requests, and latency trends of your AWS ELB traffic. Set up incident response workflows in place to mitigate and prevent any breach or security attack. Get alerted with real time alerts via SMS and email every time there are attempts at unauthorized access requests or compromised accounts.
Learn MoreGet insights on your cloud environment from reports generated using S3 access logs. Keep track of your bucket activity using reports that highlight events such as creation and deletion of buckets in your S3 architecture. Use S3 traffic analysis reports to monitor all S3 activities both bucket-level and object-level, track deleted or failed requests, isolate the identity of the requesters, discover where a resource is located, understand data access patterns, and identify error conditions.
Learn More
Make use of IAM to create AWS users and groups to effectively manage your access to resources in AWS. Get comprehensive insights on IAM users, groups, roles, MFA devices, password changes, unauthorized activities, and access keys using Log360's IAM reports. In addition, IAM report displays when an event occurred, which user was responsible for an event, the source IP address of the request, the AWS region in which the event took place, and request parameters.
Learn MoreAvoid the hassle of manually figuring out configurations in your AWS environment with a competent cloud log management tool. With Log360's auto-configuration feature, you can make critical changes all by yourself.
Learn MoreThe processes of storing, archiving, and reviewing log data makes maintenance for an indefinite period difficult. To make handling of log data easier, Log360 lets you configure archive interval, log type, location of storage, and retention period based on your needs. Further, these archived logs can be held secure in Stronghold after encryption.
In addition to critical instances, predefined reports cover user login activities and events that occur in AWS web application firewalls (WAF), Lambda, Security Token Service (STS), Elastic Block Store (EBS), Route 53, Elastic IP, elastic network interfaces, and Auto Scaling. An interactive dashboard with visual data provides you with insights on user activity, identity and access management, network security, and cloud functions that ultimately gives an overall perspective of your AWS cloud.
With advanced search options and a smart search engine, it becomes possible to sift through an abundance of cloud logs to retrieve exactly what you are in need of. Additionally, you will be able to receive notifications via email every time an anomaly, an attack, or an unusual activity takes place.
Monitor user activity regularly to gain insights into how your AWS resources can be controlled. Log360's user and entity behavior analytics (UEBA) marks anomalous behavior of the user, such as user logon activities at unusual times, unauthorized movement, changes to security credentials, or suspicious user pattern, thereby alerting security administrators to eliminate threats.
Logs are computer-generated records that describe activities that happen in a sequence within a system. Log analysis is the process of reviewing and deciphering these logs to mitigate security risks, comply with regulations, monitor performance, and understand user behavior.
Amazon Simple Storage Service (Amazon S3) is a web-based cloud storage system that is built to store and retrieve data. Amazon S3 was specifically conceptualized to enable easy web-scaling, availability, among many other functions. Some of the common use cases when it comes to Amazon S3 are data storage, archiving, backup, and disaster recovery.