Entra ID (formerly known as Azure Active Directory) is a cloud-based identity and access management service developed by Microsoft. It provides centralized management of user identities, authentication, and authorization for cloud-based applications and services. By integrating Entra ID with Endpoint Central, customers can synchronize user, computer, and group data, streamlining IT operations and enhancing management efficiency within Endpoint Central. Kindly note that this feature is available from build 11.4.2522.03.
Before integrating Entra ID with Endpoint Central, ensure the following requirements are met:
Ensure you have an active Entra ID subscription (e.g., Entra ID Free, Premium P1, or Premium P2).
You must have access to the Endpoint Central platform with at least SoM Full Control and All Computers Scope / Administrator permissions to configure the Entra ID integration.
An SSL certificate can be installed on the server hosting Endpoint Central to ensure secure communication during synchronization.
Configure NAT settings to allow communication between Endpoint Central and Entra ID.
Follow the steps below to add an Entra ID domain to Endpoint Central.
Go to the Agent tab. Select Domain and then click on Add Domain.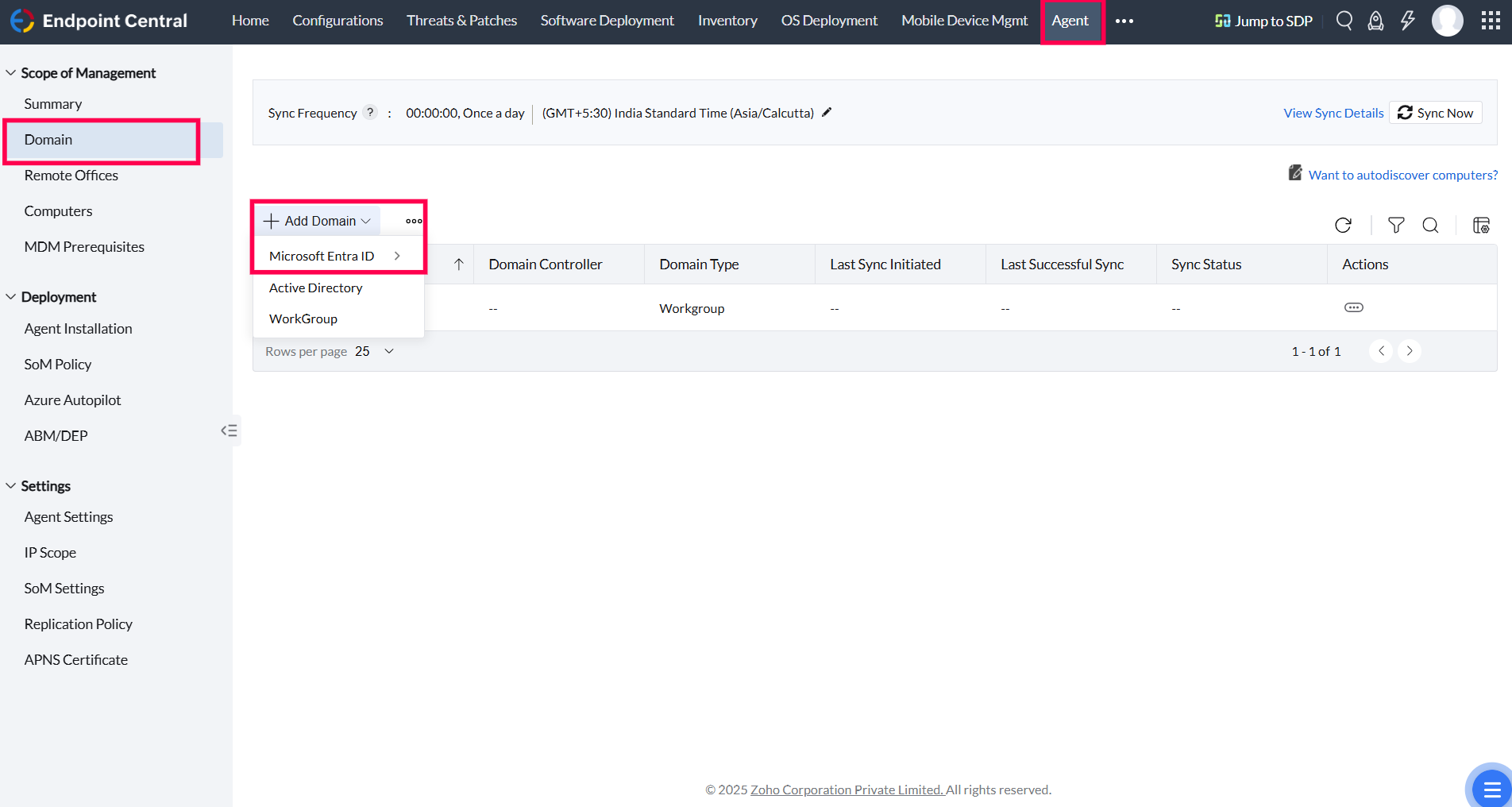
Click on Add Domain and select Entra ID from the available domain types. Select the specific Entra ID services you wish to integrate (e.g., Global, DoD, etc.).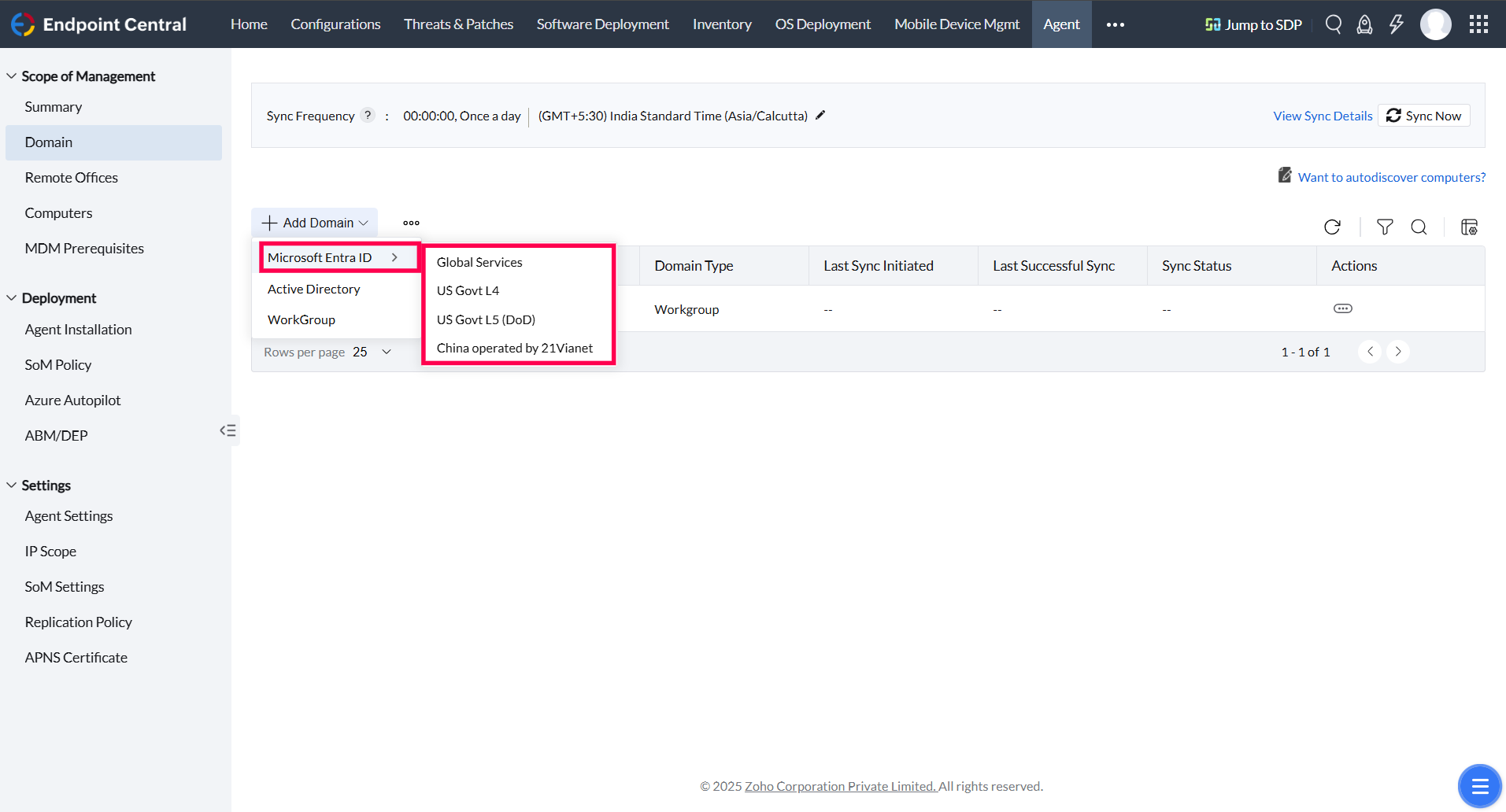
Note: Endpoint Central supports integration with various Entra ID services, including Global, US Govt L4, L5 (DoD) and China operated by 21Via Net.
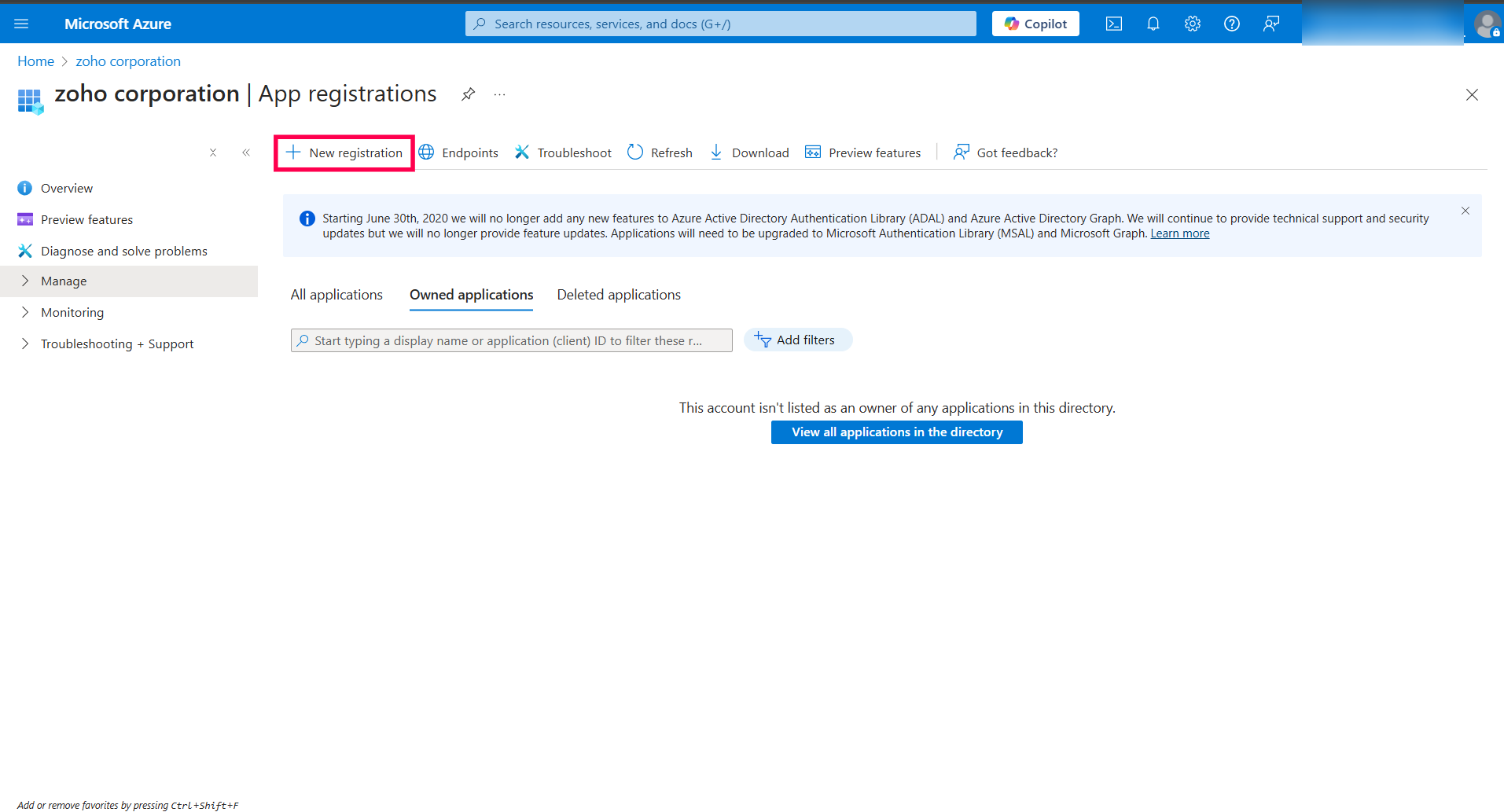
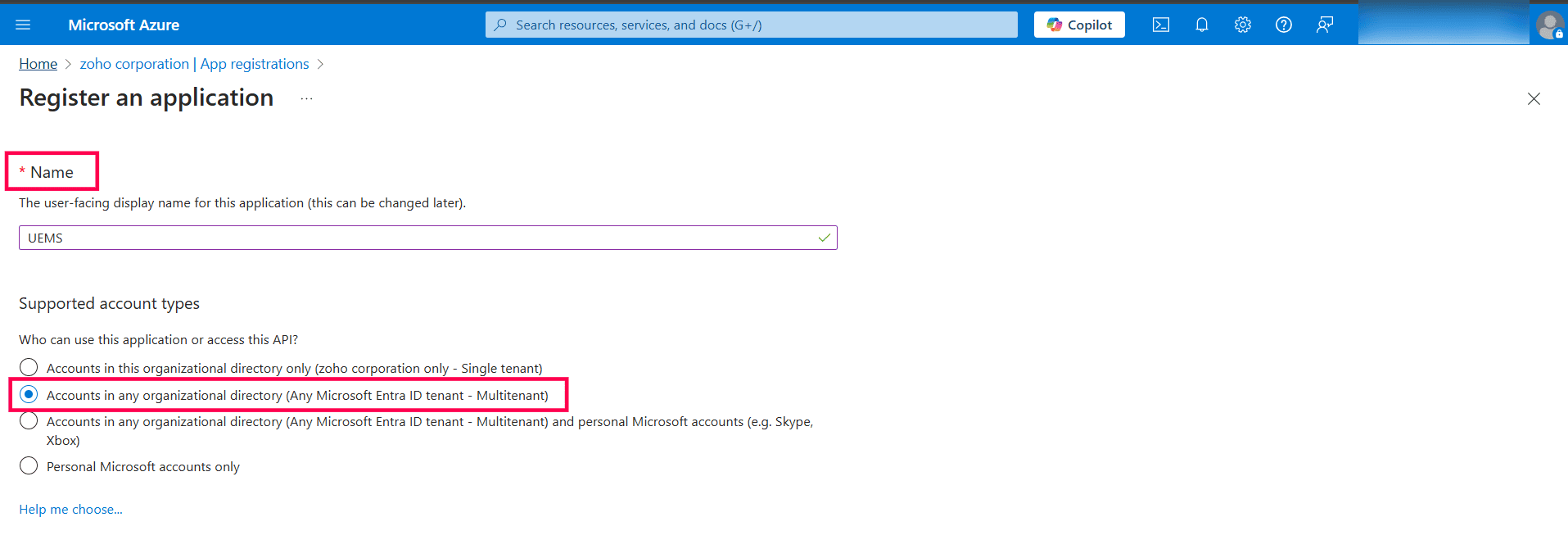
Info: The same app registration can be used for all tenants within your organization.
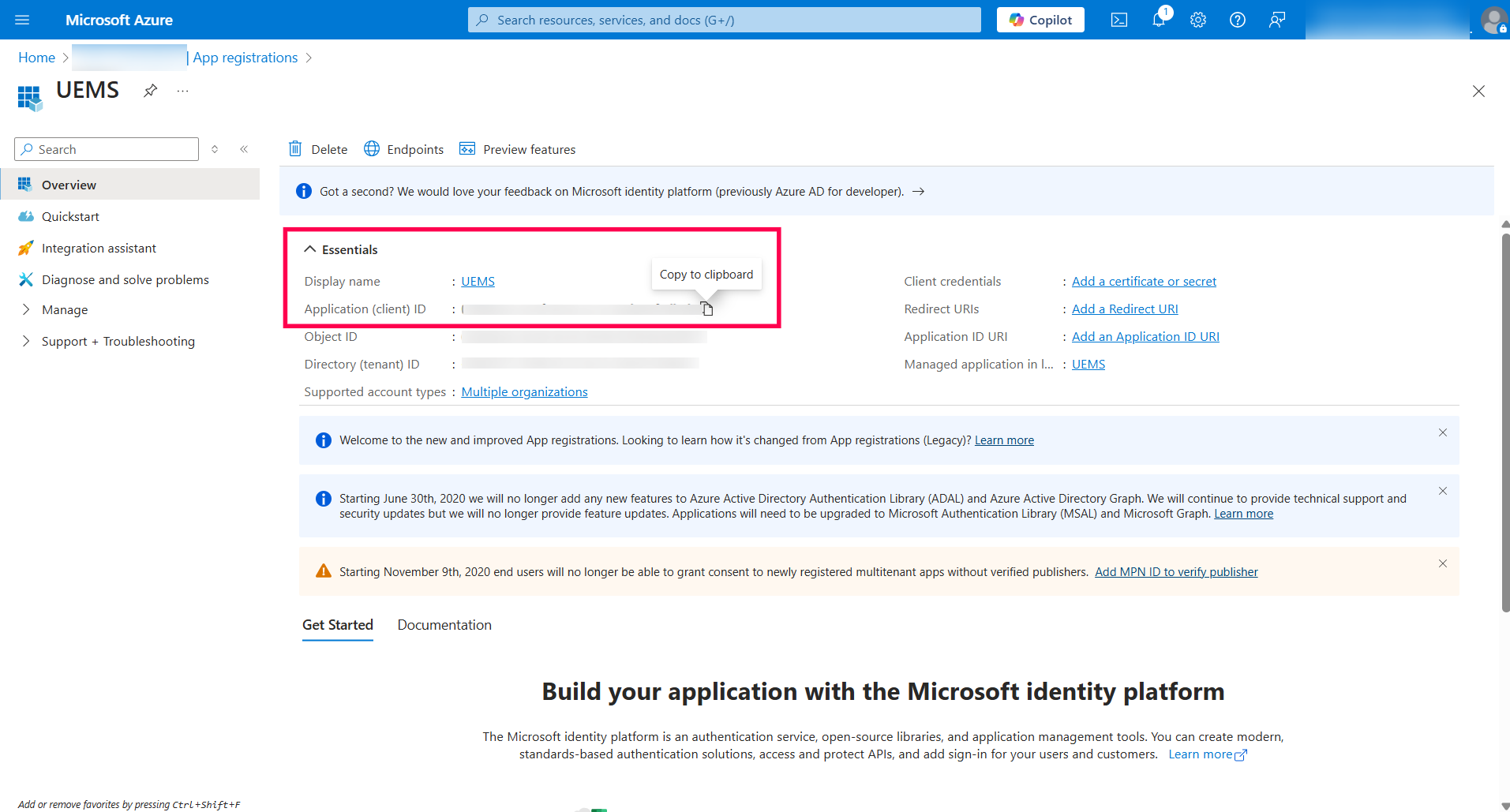
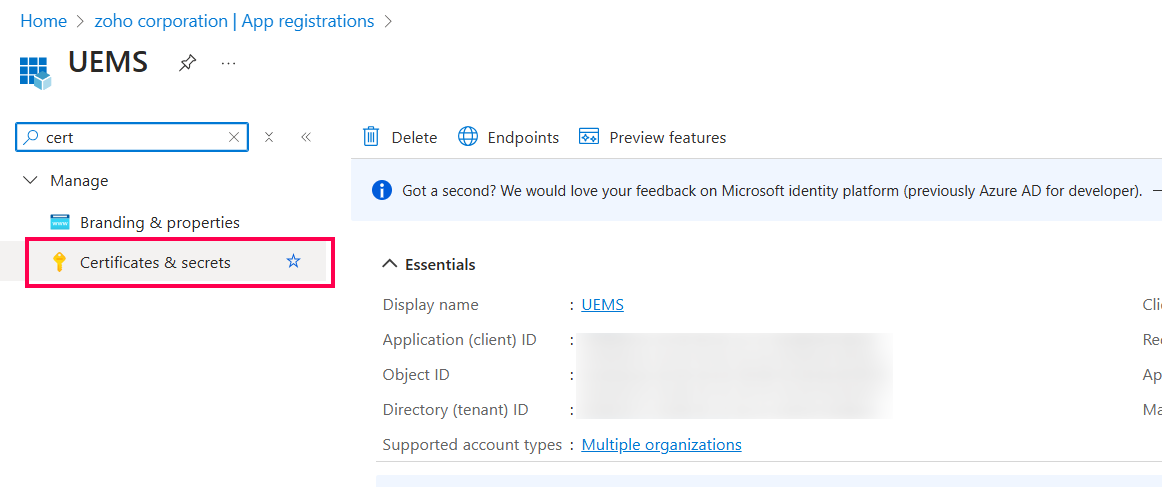
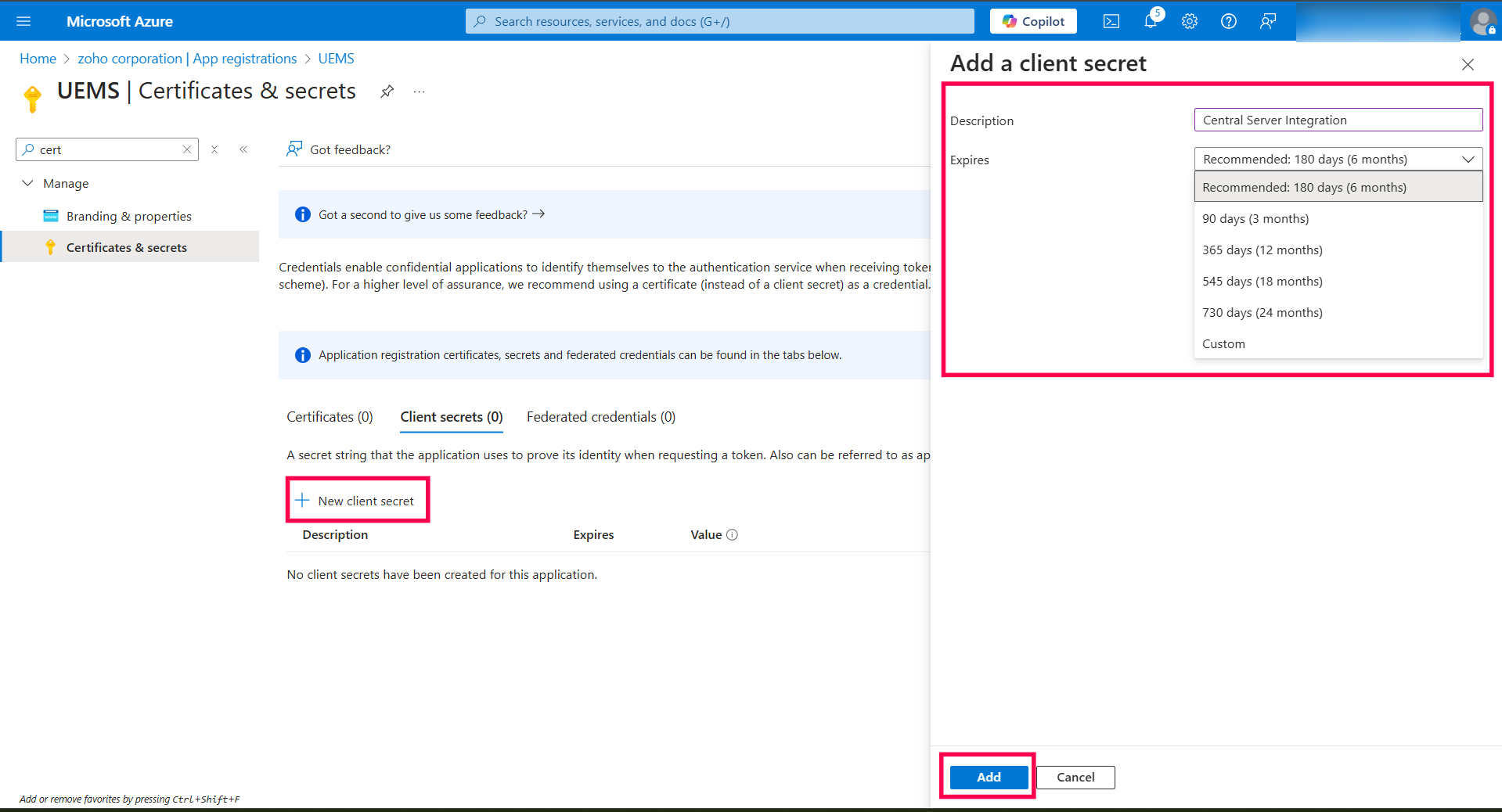

After authentication and accepting the consent from Azure Portal, return to Endpoint Central and configure the sync frequency for the Entra ID domain. Choose from the following frequency options:
Once the Entra ID domain is added, you can manage it through the Actions menu.
To add Entra ID computers, select the domain, navigate to Actions, and click Add Computers.
To initiate a sync immediately, navigate to the Actions menu for the corresponding domain and click Sync Now.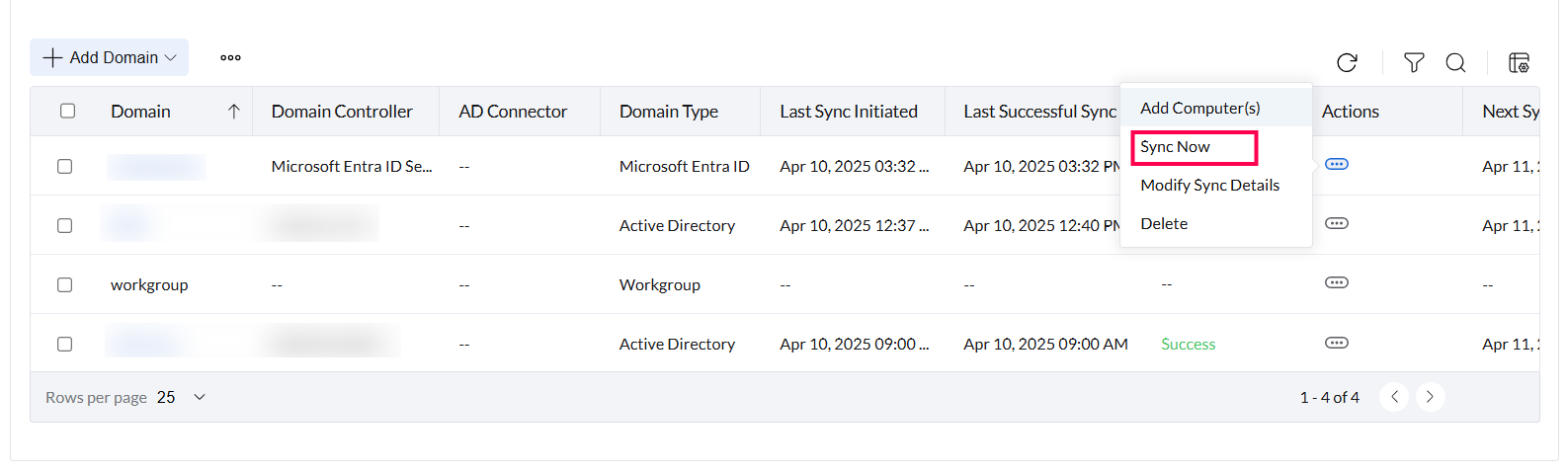
Note: You can only initiate a manual sync 4 times per day.
To edit domain details, navigate to the Actions menu of the corresponding domain and click Modify Domain.
Note: this Option only to applicable to Windows Server Active Directory
To update the sync frequency or start time, navigate to the Actions menu of the corresponding domain and click Modify Sync Details.
To delete a domain, navigate to the Actions menu of the corresponding domain and click Delete.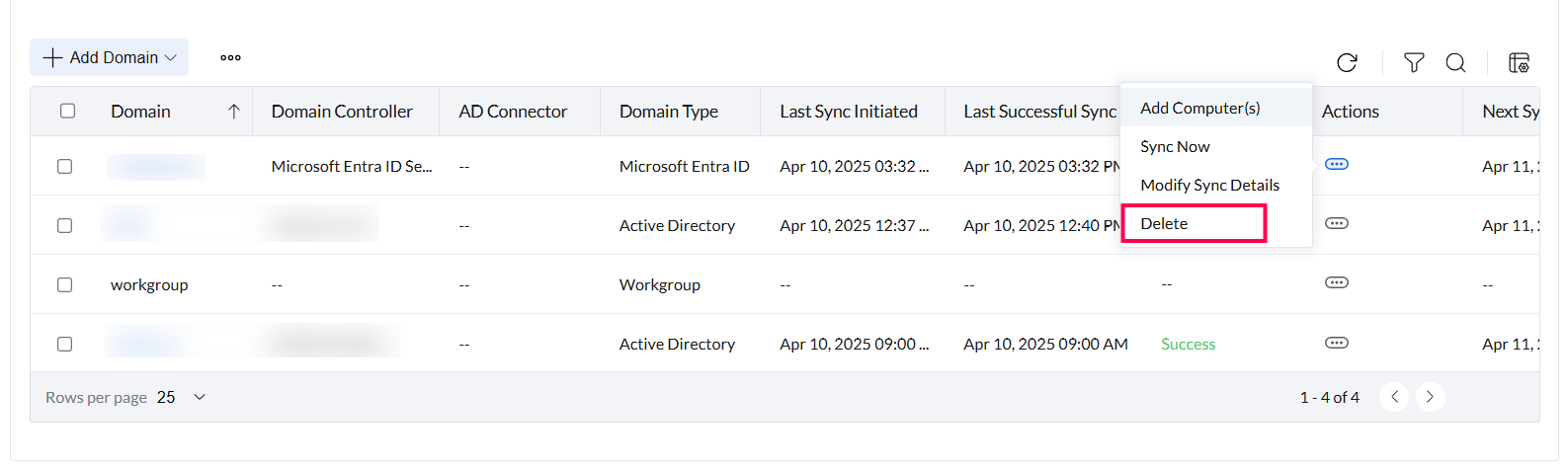
Important: Deleting a domain will erase all associated data for that domain. A domain cannot be deleted unless all the managed computers are removed from the Scope of Management.
To convert a domain-based device to a workgroup, select the domain, click the corresponding action, and choose Change to Workgroup.
Note: this Option only to applicable to Windows Server Active Directory
If you encounter issues during the Entra ID configuration or syncing process, consider the following steps:
Ensure that the server running Endpoint Central has proper network connectivity to Entra ID.
Ensure that the app registered in Entra ID has sufficient API permissions to access directory data.
Verify that your SSL certificate is correctly installed and valid for secure communication between Endpoint Central and Entra ID.
Ensure that the sync frequency is configured correctly based on your organization's requirements.
Ensure that the provided Client ID/ Secret is valid or have not reached the expiry date. If not, get the Client ID and Secret value from the Azure Portal, update in the OAuth details available in OAuth tab, and reauthenticate Domains.