- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
CCPA compliance made easy with EventLog Analyzer
The California Consumer Privacy Act (CCPA) is designed to give California residents more control over their personal information and to hold businesses accountable for protecting that information. CCPA applies to for-profit businesses in California. It also requires that businesses implement security measures to protect against unauthorized access, exfiltration, theft, or disclosure of consumer's personal data. CCPA applies to all for-profit businesses that operates in California.
EventLog Analyzer can help businesses manage their CCPA compliance by providing real-time visibility into personal information usage, automating compliance processes, and generating reports and audit trails to demonstrate compliance to regulatory agencies.
Related Content
- Compliance hub
- What is security compliance?
- What is a compliance audit?
- Risks of regulatory non-compliance
- Compliance management software
- CCPA compliance
Discover how EventLog Analyzer streamlines the process of CCPA compliance
Web server auditing
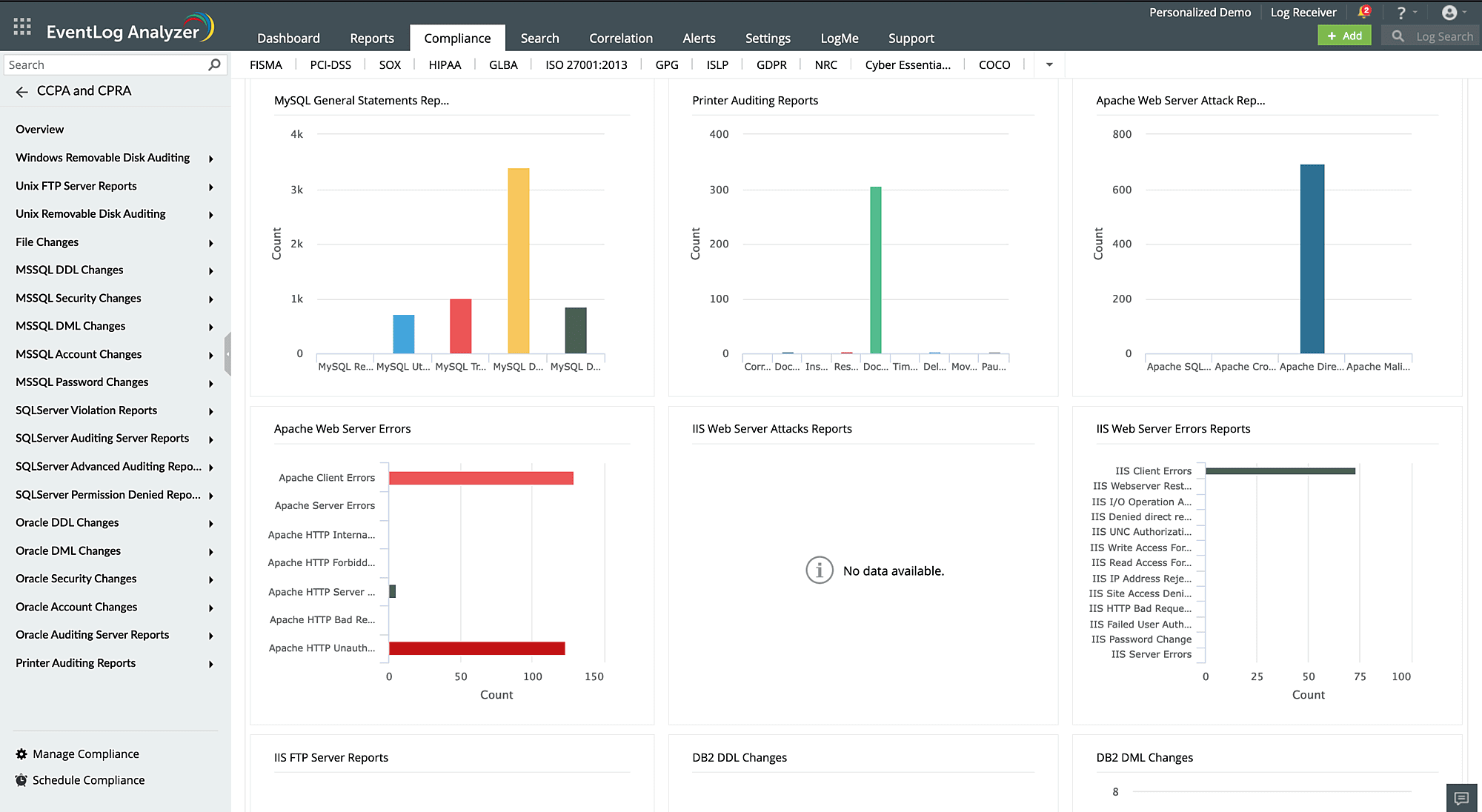
Seamlessly collect and analyze log data from various web servers, like Microsoft IIS and Apache. EventLog Analyzer ensures the confidentiality and integrity of personal information stored on your web servers. The logging tool sends automated alerts when suspicious activity is detected, such as insider threats, account compromise, data exfiltration attempts, or unauthorized access. It also provides actionable insights and intuitive reports on web server errors—such as HTTP 502 bad gateway, HTTP forbidden, and HTTP unauthorized—to help you quickly troubleshoot server issues.
File integrity monitoring (FIM)
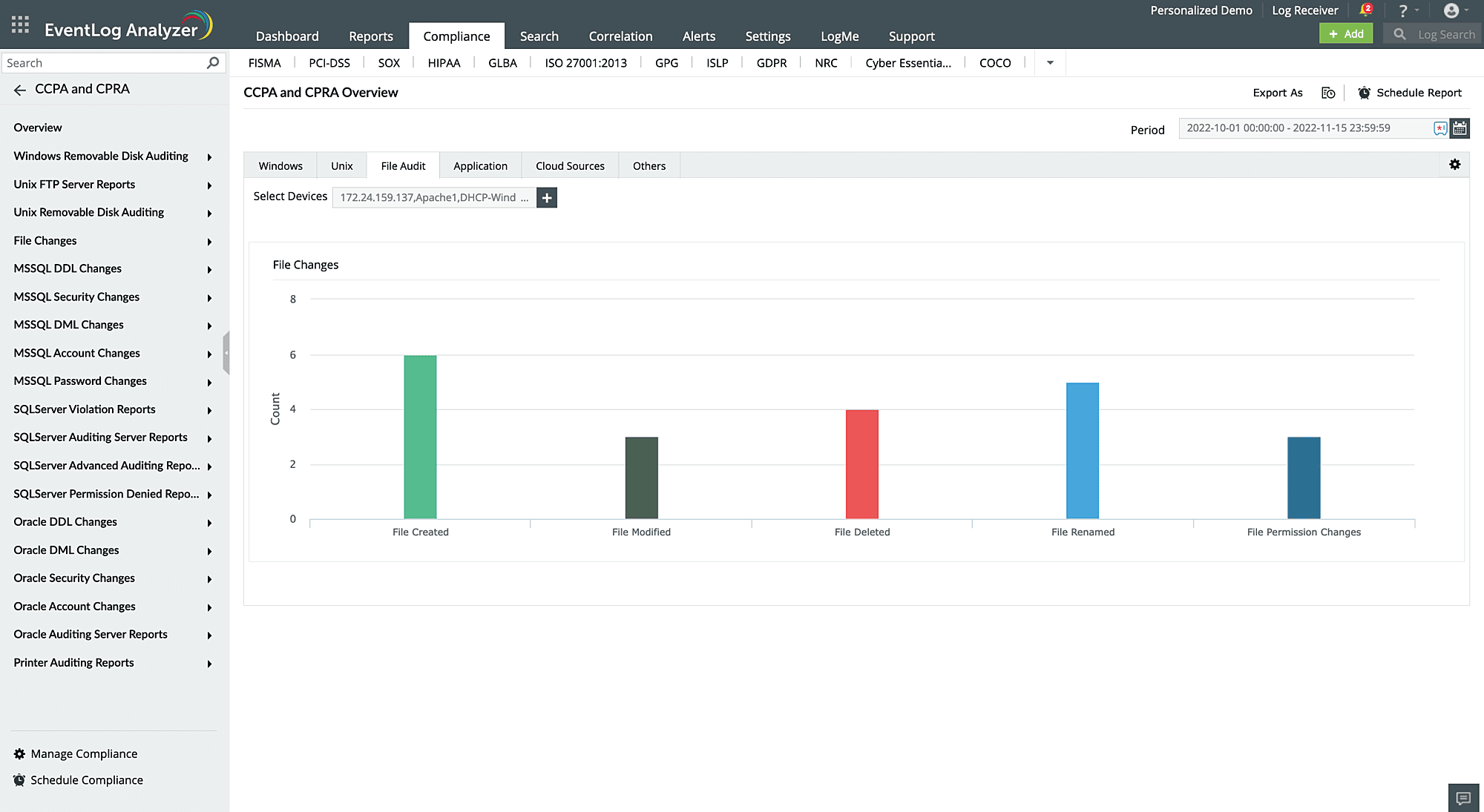
EventLog Analyzer's FIM feature examines logs, creates an audit trail that records all actions made to files containing personal information, and sends out insert alerts (on modifications, renames, creations, and deletions) to help you meet CCPA requirements. You can view detailed information on who made the change, what was changed, when, and from where. You can also audit permission changes and failed attempts associated with any file actions.
Removable disk auditing
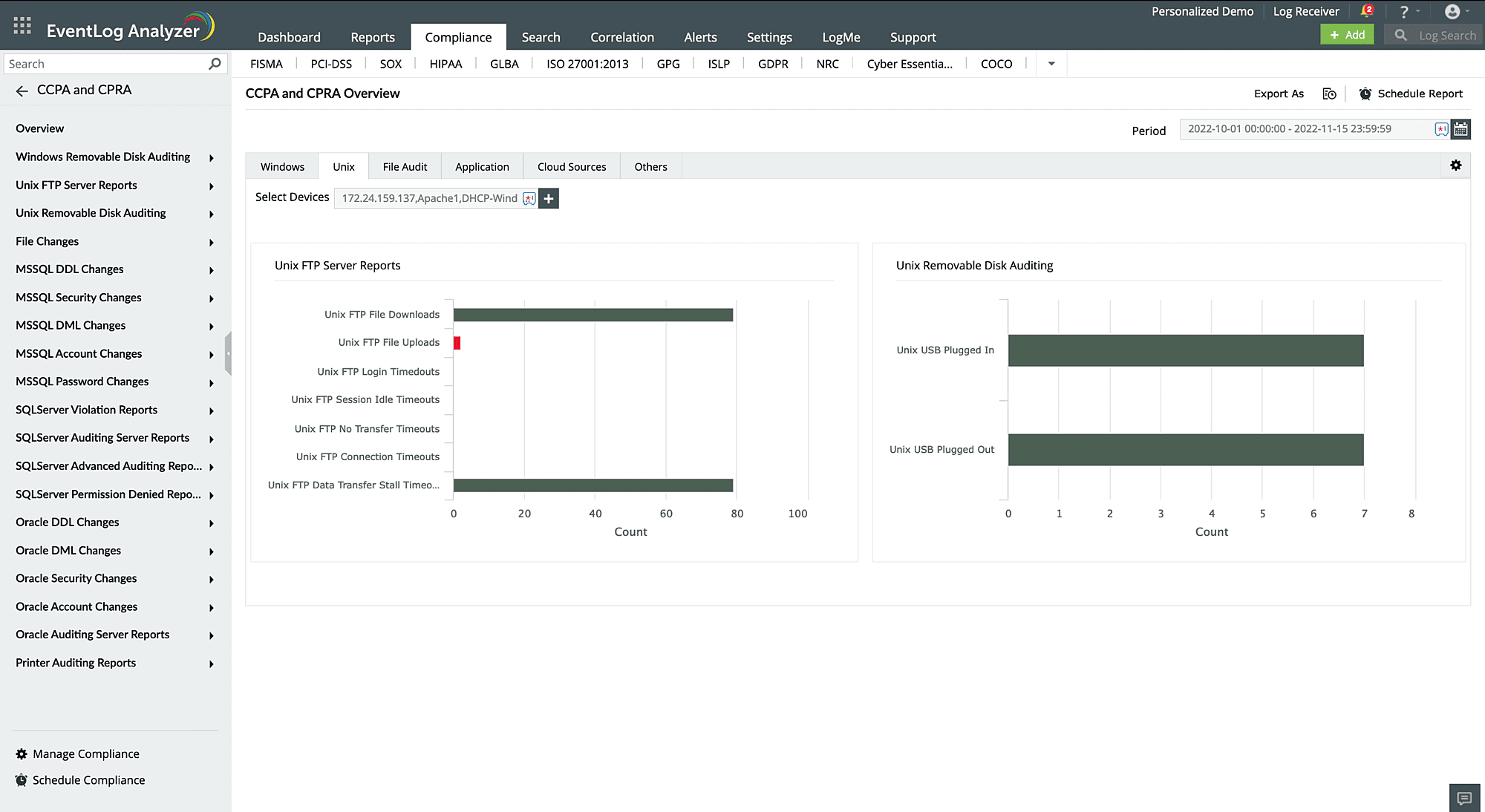
EventLog Analyzer audits USB device activities through Windows event logs and offers a thorough audit trail of all removable disk activity, including when disks are inserted or removed, when files are copied, and when disk properties are modified. This enables you to track and investigate suspicious or unauthorized removable disk activity. When removable devices, such as USB devices, are plugged into or taken out of the network, real-time notifications can be configured to notify the administrator immediately. The solution also has a predefined report that displays all USB and removable disk activities and detects data theft to prevent confidential data leaks.
Database auditing
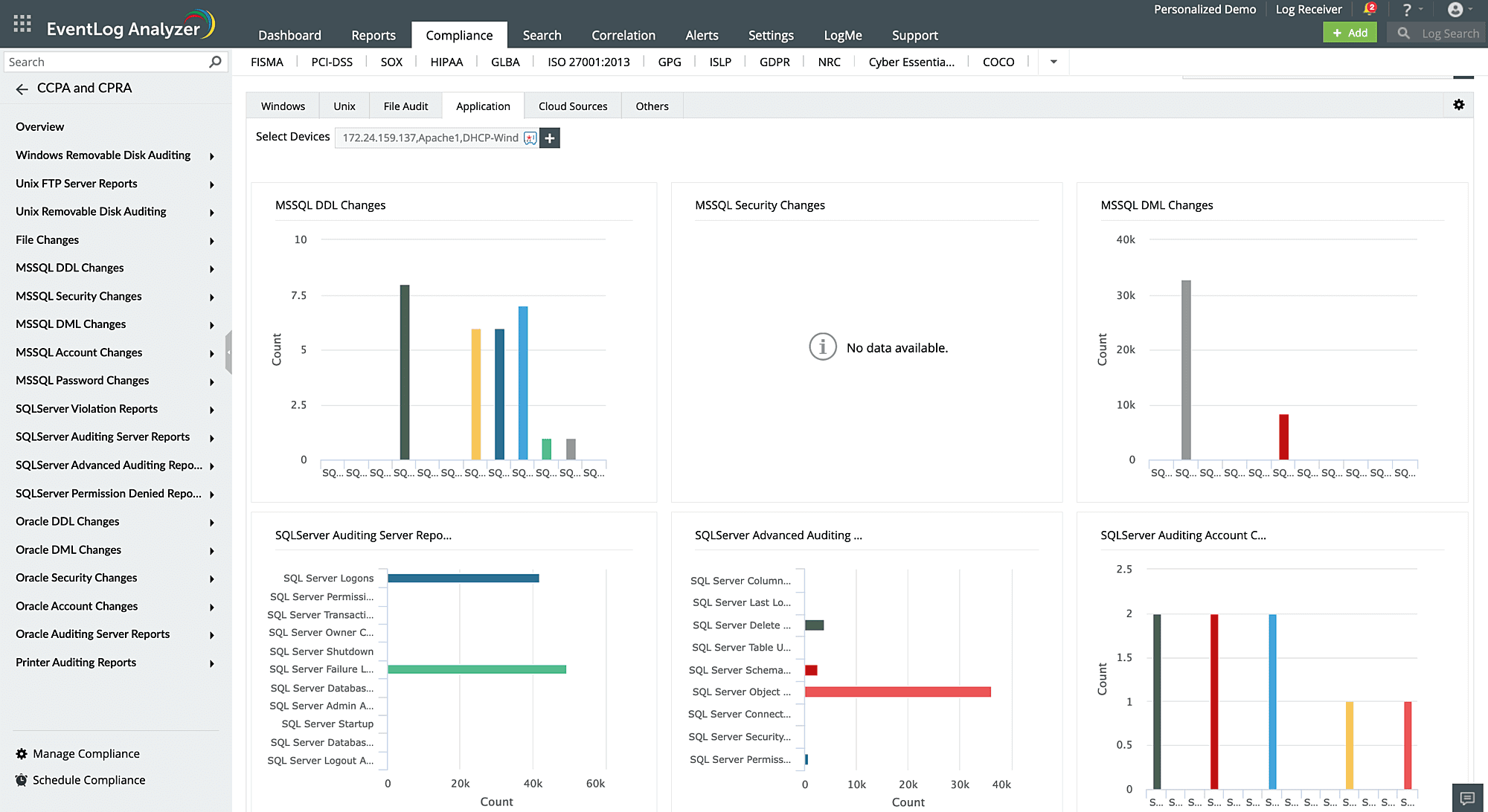
To ensure CCPA compliance, data security administrators must continuously monitor network activity and extract data access information. You can meet this requirement by automatically collecting and analyzing logs from database servers such as Microsoft SQL, Oracle, and MySQL with EventLog Analyzer. If any suspicious activity occurs in your database servers—such as unauthorized logons, DDL or DML queries executed on the database, password changes, permission changes, privilege escalation, or role changes—you will be notified immediately. The solution also helps identify various cyberattacks, like SQL injection attacks, ransomware attacks, denial-of-service attacks, and brute-force attacks.
How does EventLog Analyzer meet CCPA requirements?
| CCPA requirements | Reports by EventLog Analyzer |
|---|---|
|
Section 1798.150.(a) "Any consumer whose nonencrypted and nonredacted personal information, as defined in subparagraph (A) of paragraph (1) of subdivision (d) of Section 1798.81.5, or whose email address in combination with a password or security question and answer that would permit access to the account is subject to an unauthorized access and exfiltration, theft, or disclosure as a result of the business’s violation of the duty to implement and maintain reasonable security procedures and practices appropriate to the nature of the information to protect the personal information may institute a civil action." |
|
What else does EventLog Analyzer offer?
Centralized log management
Collect, store, and analyze logs from perimeter devices, network devices, endpoint security solutions, web servers, database platforms, and applications from a centralized dashboard.
Log visualization
Visualize log data collected from multiple sources and gain valuable insights into important network security events.
Privileged user monitoring
EventLog Analyzer constantly monitors privileged user activities and alerts you when suspicious activity is detected.
Forensic log analysis
Perform in-depth forensic log analysis to trace back attacks and determine the root cause of incidents.
Frequently asked questions
CCPA applies to for-profit businesses in California that meet at least one of these criteria:
- Annual revenue exceeding $25 million.
- Handling personal information of 100,000 or more California residents or households.
- Generating 50% or more of their annual revenue from selling California residents' personal information.
Both the General Data Protection Regulation (GDPR) and the CCPA are data privacy laws that have some similarities and differences. The GDPR applies to businesses that operate within the European Union (EU) or process the personal data of EU residents, while the CCPA applies to businesses that operate in California or process the personal data of California residents. The CCPA defines "consumer" as a California resident, and "personal information" as information that identifies, relates to, or describes a particular consumer or household. Unlike the CCPA, the GDPR imposes hefty fines for non-compliance.
The CCPA provides several important rights to California consumers, including:
- Right to know: California residents have the right to know what personal information is being collected about them, how it's being used, and who it's being shared with.
- Right to deletion: The right to request that their personal information be deleted from a business's records.
- Right to opt-out: The right to opt-out of the sale of their personal information to third parties.
- Right to non-discrimination: The right to not be discriminated against for exercising their CCPA rights.
- Right to access: The right to access the personal information that a business has collected about them in the past 12 months.
- Right to data portability: The right to receive personal information in a readily usable format that allows them to transfer it to another entity.
- Right to opt-in: Businesses must obtain affirmative consent from minors under the age of 16 to sell their personal information.
The California Privacy Rights Act (CPRA) is a privacy law that builds upon the existing CCPA in California. Having taken full effect on January 1, 2023, it expands and strengthens the privacy rights of California residents by adding new provisions, such as the right to limit the use of sensitive personal information and the right to correct inaccurate personal information, additionaly it increases penalties for violations. The CRPA also created a new regulatory agency, the California Privacy Protection Agency, to enforce the law.











