- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Microsoft IIS servers, both web and FTP, have become essential for businesses. However, an IT security administrator's job doesn't stop with deploying IIS servers. Post deployment, administrators have to adopt security measures to protect those servers. One proven way to monitor the security of IIS servers is by installing a log management tool that provides out-of-the-box support for IIS logs.
EventLog Analyzer is a comprehensive tool that can manage and audit your Microsoft IIS server logs and provide you with crucial insights on the activities happening in your IIS servers. This software has out-of-the-box support for both IIS web and IIS FTP server logs, and provides in-depth reports that make your auditing job a lot easier.
Learn how EventLog Analyzer serves as an effective IIS log analyzer tool with its advanced analytical capabilities and end-to-end log management features.
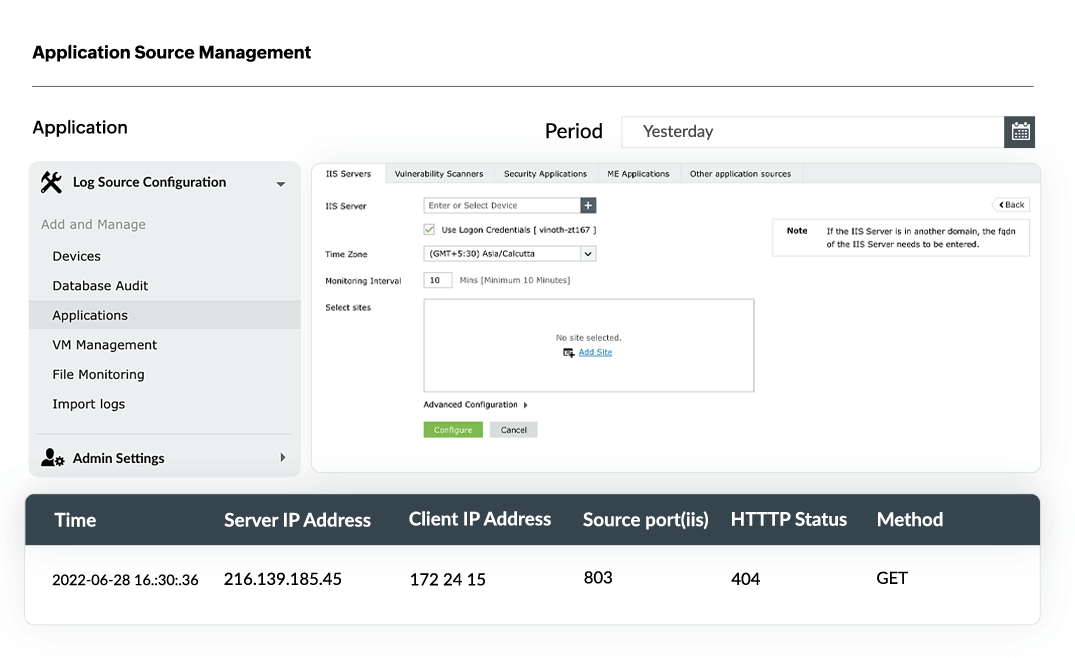
IIS log collection and processing
The log collection process in EventLog Analyzer has been designed to be automated, efficient and seamless with options for both agent-based and agentless-log collection. Also, you can manually configure the log collection settings for IIS servers, select specific sites for monitoring, and add filters to collect necessary data. The collected logs are transferred to the EventLog Analyzer server in real-time and are processed at a rate that can go up to 25,000 logs per second.
IIS log parser
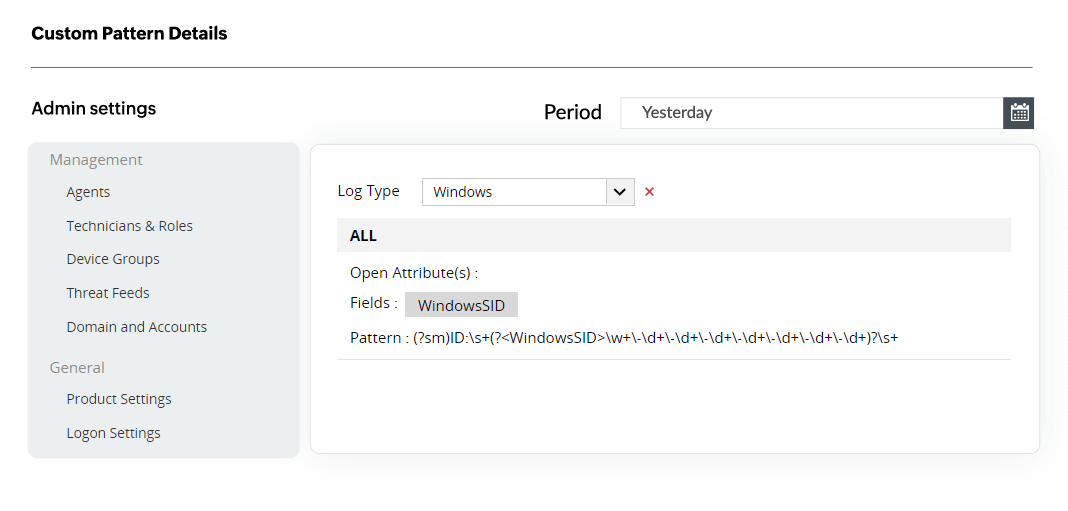
EventLog Analyzer supports parsing logs generated in any format. This includes W3C Extended log file format, NCSA Common log file format, and ODBC logging. This log management tool is also equipped to handle heterogeneous environments hosting multiple of versions of IIS servers (IIS 6.0, IIS 7.0, IIS 8.0, IIS 10, etc.).
By default, the log parsing is done by extracting standard fields like client and server IP address, timestamp of events, server name, and port number. You can also use the custom log parser to index new fields and generate custom patterns to parse logs.
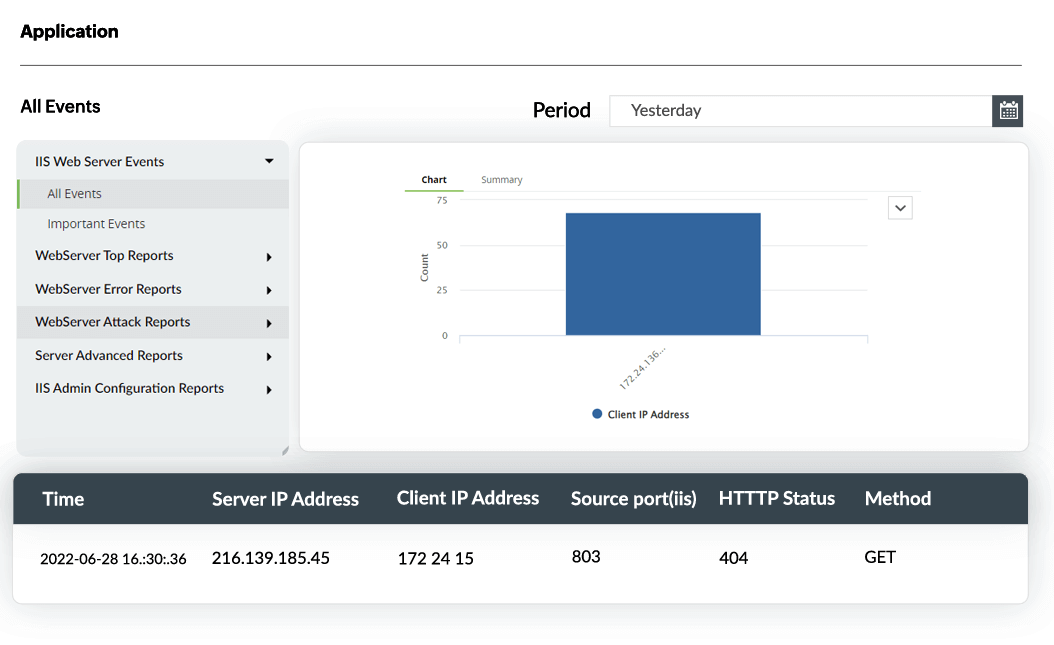
IIS web server log analysis
EventLog Analyzer monitors, analyzes, and audits IIS web server events and provides reports on error events, security attacks, usage analytics, and many more facets of your IIS servers.
- Error reports: These reports list the errors that users experienced while trying to access the websites hosted on your IIS web servers, such as failed user authentication, HTTP bad request, HTTP request entity too large, and gateway timeout. They also help you identify the problems users frequently face, so that you can come up with corrective steps to ensure a hassle-free experience for users.
- Security reports: Server attack reports give information on the attacks detected by EventLog Analyzer in your IIS web servers, such as SQL injection and DDoS. EventLog Analyzer comes with prebuilt alert profiles that can notify you in real time when such attacks are detected. You also get exclusive reports providing information on the users who most frequently access your server, along with server activity trends.
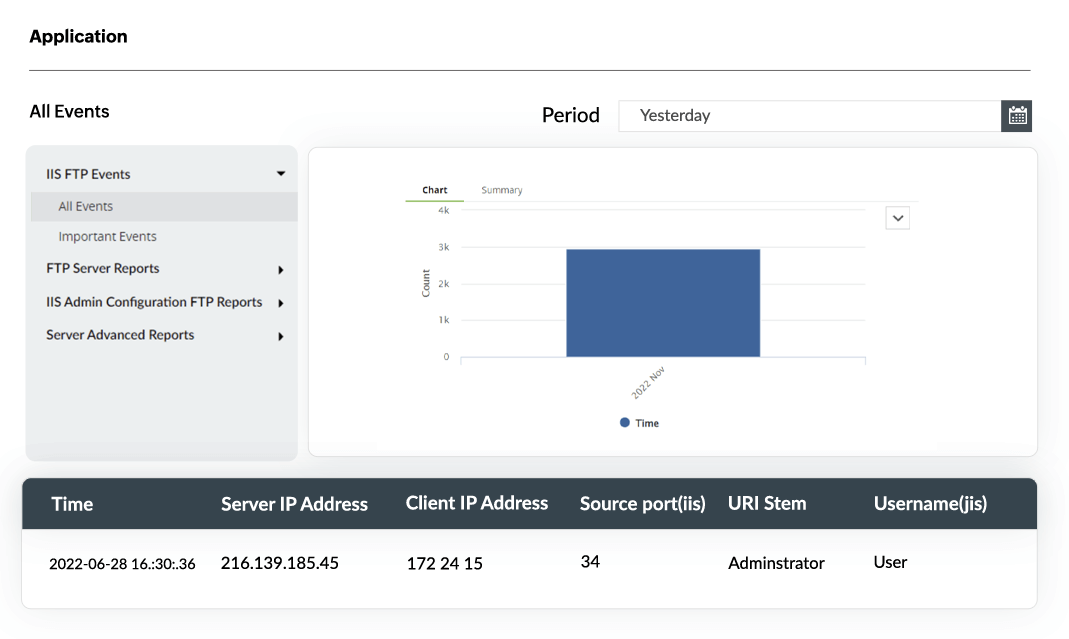
IIS FTP sever log analysis
EventLog Analyzer's reports on IIS FTP servers help in monitoring, tracking, and optimizing user activity by providing you with countless reports on important logons, file downloads, security data exchange, and base sequences of commands. The intuitive dashboard of this IIS log analysis software allows administrators to effortlessly access raw log data and spot the origin point of any activity.
IIS log visualization and reporting
EventLog Analyzer helps you observe log trends by instantly visualizing the log data and presenting the results in graphic reports. Toggle between between multiple graph forms, add the reports as widgets on your dashboard, and compare different trends to get a comprehensive view of your IIS server events. You can also export the reports, schedule them to be mailed to your inbox periodically, and add them as incidents.
Other solutions offered by EventLog Analyzer
Log archival
Utilize the automated log archiving feature in EventLog Analyzer to securely store IIS logs, comply with security mandates such as Cybersecurity Maturity Model Certification(CMMC), Codes of Connection(CoCo), Good Practice Guide(GPG), and FERPA that require IIS log data, and conduct forensic analysis in case of web server attacks and network compromise.
Real-time alerting
Set-up alerts for critical anomalies and error events using EventLog Analyzer's alerts dashboard which contains predefined alert criteria based on IIS report profiles. Enable real-time notifications via email or SMS, add alert severity level, customize the alert message format, set the threshold values for the alert trigger, and configure other advanced settings to create a complete profile.
Windows log analyzer
Audit Windows environments thoroughly with EventLog Analyzer's reports for Windows client machines, servers, firewalls, user activities, active directory, and Windows based threats.
Application log monitoring
Along with monitoring IIS web and FTP servers, EventLog Analyzer also supports Apache servers, database applications such as MySQL, Oracle server, IBM Db2 and PostgreSQL, DHCP servers, print servers, and third party applications.
Event correlation
Correlate IIS logs with events detected across various endpoint devices and applications to identify threat patterns and attack attempts. One example is an application suddenly crashes and new files pop up on your server. This can be correlated with spikes in the interaction with a new external IP by analyzing the firewall logs. This is a possible indicator of a threat actor transferring malware payload to your IIS server. Similarly, EventLog Analyzer offers over 30 predefined correlation rules, options to customize and create new rules, and trigger alerts when patterns are matched.
Frequently asked questions
An IIS log viewer simplifies the process of analyzing and viewing log files by collecting, parsing, and normalizing the log data from various IIS servers. EventLog Analyzer, a comprehensive log management tool, allows you to view IIS logs by presenting the collected data on a centralized dashboard in the form of graphs and reports. Additionally, you can compare log events to identify and analyze suspicious activity in IIS servers, expedite incident response, and conduct root cause analysis.
To manually analyze the IIS logs, you need to enable logging for the hosted sites, select the fields to be logged, and configure log storage and compression. IIS logs are notoriously known for taking up a large amount of storage.
To configure the IIS settings, Launch the IIS Manager > head to the Connections pane > select the intended site > go to the Actions pane > select Settings.
Once log collection is initiated, upload the log files to an open source log parser tool, choose a suitable predefined pattern or add a custom one, export the parsed data to an excel sheet, and generate reports.
The manual method may work for IIS servers hosting limited applications and serving a very small number of end users. However, as the scale grows, it's imperative to use an automated IIS log analyzer tool that can generate reports on the go.
A centralized on-premise log management solution like EventLog Analyzer can comprehensively manage IIS servers and seamlessly perform the following actions:
- Collect, parse, manage, monitor, and analyze IIS web server and IIS FTP server logs.
- Allow users to import log data through an easy-to-use interface and enable periodical log import through log scheduler.
- Audit server activities such as account changes, error codes thrown, files uploaded and downloaded, and more.
- Monitor user activities such as logons and logoffs so that any unusual user behavior is instantly detected.
- Detect anomalies occurring in IIS servers and immediately alert users in real time.
- Provide pre-made audit reports on IIS web and FTP servers for meeting IT regulatory compliance needs.











