- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
What is the GLBA?
In the United States, the Gramm-Leach-Bliley Act (GLBA) regulates how financial institutions handle and distribute non-public personal information (NPI) pertaining to consumers who use financial services for their personal needs. The GLBA requires financial institutions to uphold the privacy and security of NPI, covering a range of entities such as banks, lenders, and investment advisors, regardless of their size.
How can you comply with the GLBA?
Complying with the GLBA involves dual responsibility to ensure the privacy and security of NPI. The Privacy Rule elaborates on disclosure responsibilities and opt-out requirements, and the Safeguards Rule specifies the establishment of protective measures for NPI.
The GLBA demands stringent protection of NPI. EventLog Analyzer—with its log analysis and management features—assists financial institutions in meeting GLBA requirements. It meticulously tracks, audits, and ensures the security of NPI data. EventLog Analyzer is a comprehensive GLBA audit tool with predefined correlation rules and compliance templates.
Related content
Here's how EventLog Analyzer simplifies GLBA compliance management
User logon and logoff monitoring
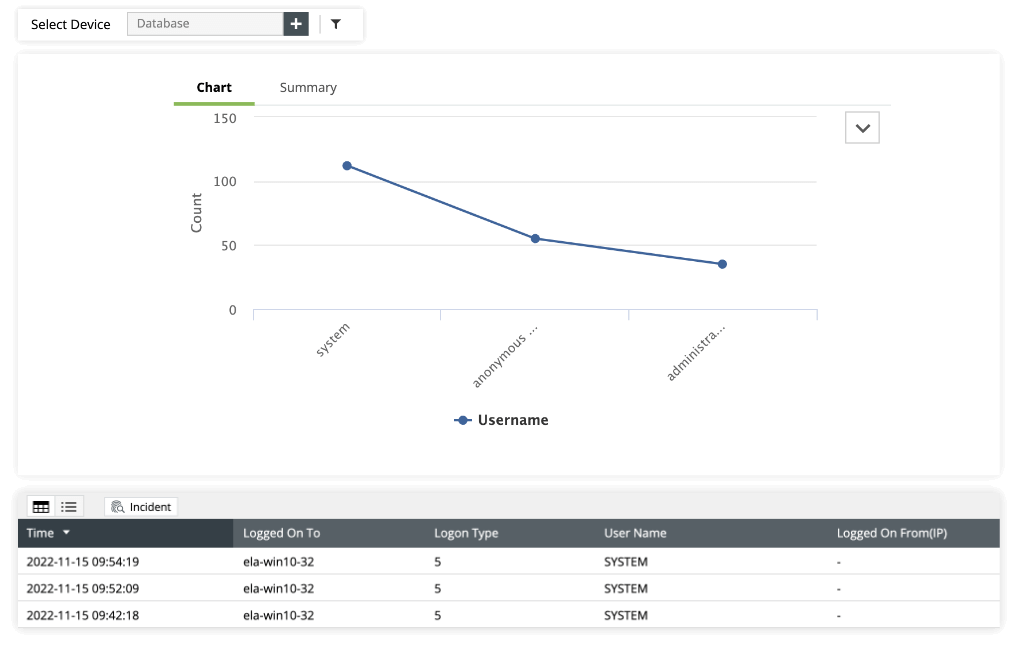
The GLBA emphasizes closely observing user access to systems containing confidential information—not just to catch breaches, but to deter malicious activity. Think of EventLog Analyzer as a surveillance camera watching over your data, offering real-time email and SMS notifications for any unauthorized access. EventLog Analyzer continuously monitors your system and provides detailed reports on user logons and logoffs. This includes successful and failed login attempts, usernames, devices used, times, and reasons for these events.
Privileged user auditing
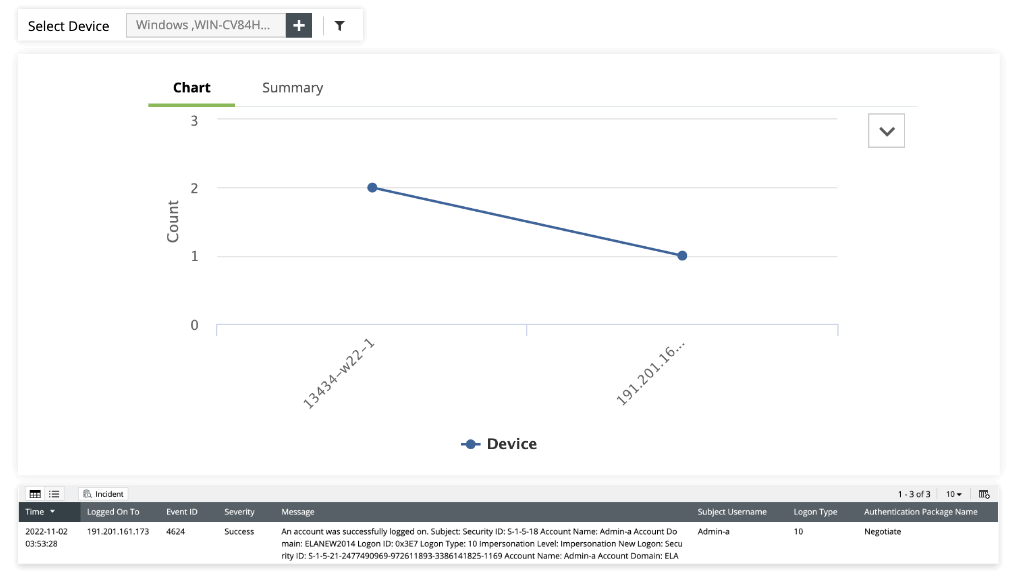
Privileged user accounts have access to critical servers and sensitive data, posing a security challenge that could be catastrophic if compromised. EventLog Analyzer excels in auditing privileged activities, offering insightful and user-friendly reports that pinpoint unusual access patterns. It helps identify privilege abuse and forensic investigations, aligning with the GLBA's stringent data security provisions. By monitoring and auditing privileged users effectively, EventLog Analyzer contributes to robust protection of NPI data, keeping your organization compliant and secure.
Database activity monitoring
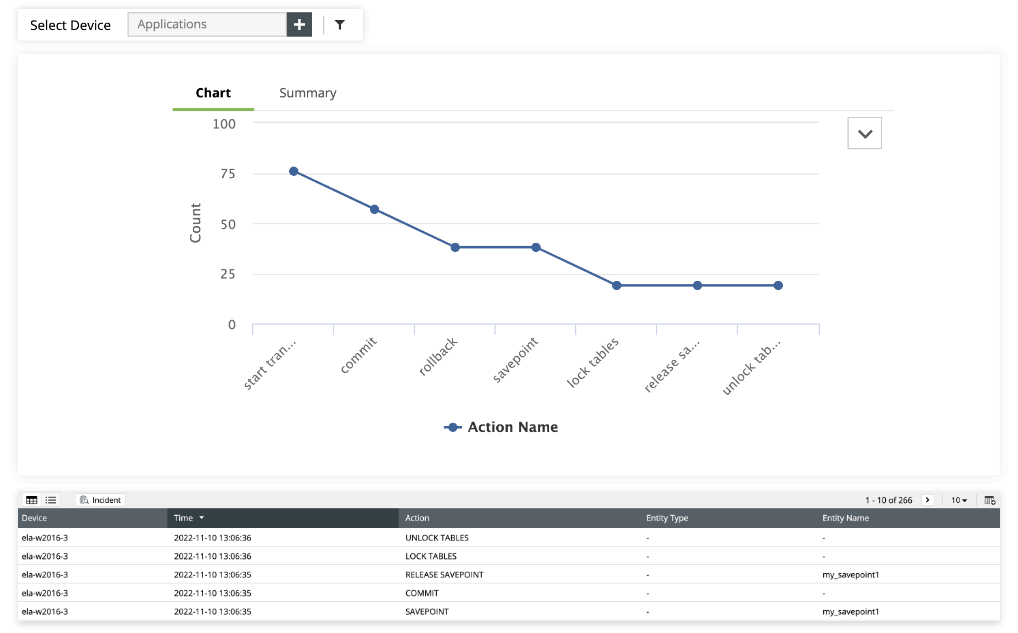
EventLog Analyzer offers database monitoring across platforms like Microsoft SQL Server, MySQL, Oracle, and IBM Db2, aligning with the GLBA’s stringent Safeguards Rule. It offers real-time alerts on data definition language (DDL) and data manipulation language (DML) changes and potential database attacks like SQL injection or DDoS.
Using its powerful correlation engine, EventLog Analyzer detects external threats by correlating network and database activity to reduce potential false alarms. EventLog Analyzer encrypts and compresses log files while archiving to fortify database security and compliance.
Log forensics
EventLog Analyzer simplifies log forensics by gathering, searching, correlating, and analyzing logs from all network log sources like routers, switches, firewalls, and servers. These logs are invaluable in reconstructing the crime scene of a security breach. EventLog Analyzer ensures these logs are tamper-proof and accessible for accurate forensic analysis. With capabilities like instant forensic reports, correlation of suspicious incidents, and swift root-cause analysis, it transforms tedious manual tasks into an efficient, user-friendly process.
How does EventLog Analyzer meet GLBA requirements?
| GLBA requirement | What is it? | Predefined reports in EventLog Analyzer |
|---|---|---|
| Section 314.4(b)(1) | Login Monitoring: Procedures for monitoring login attempts and reporting discrepancies. |
|
| Section 314.4(c) | Response and Reporting: Identify and respond to suspected or known security incidents; mitigate, to the extent practicable, harmful effects of security incidents that are known to the covered entity; and document security incidents and their outcomes. |
|
| Section 501B (1) | Ensuring the confidentiality of customer financial information. |
|
| Section 501B (2) & (3) | Protecting against anticipated threats to customer records. Protecting against unauthorized access to customer information that could result in substantial impact to the customer. |
|
Related solutions offered by EventLog Analyzer:
Monitoring network devices
Monitor the network's perimeter devices and proactively prevent intrusions. EventLog Analyzer supports a wide array of log sources, including firewalls, switches, routers, IDSs, and IPSs.
Learn moreApplication log auditing
Monitor business-critical databases and web servers by leveraging application log functioning to monitor and protect against malicious attacks, data thefts, unintended account changes, and more.
Learn moreCompliance violation alerts
Receive alerts based on predefined compliance criteria for IT regulation violations and ensure compliance with various regulations like the GLBA, the PCI DSS, SOX, HIPAA, the GDPR, and more.
Learn moreThreat intelligence
Ensure network safety with the comprehensive threat intelligence module, drawing insights from major global threat feeds including STIX, TAXII, and AlienVault OTX.
Learn more5 reasons to choose EventLog Analyzer for GLBA compliance management
Comprehensive log management
Ensure watertight security of your financial data with EventLog Analyzer. It ensures GLBA compliance by securely collecting and storing logs via agent-less and agent-based log collection.
Data security and integrity
Guarantee your NPIs remain untouched and data remains secure with encrypted, hashed, and timestamped log archival.
Cloud infrastructure log monitoring
With EventLog Analyzer's cloud log monitoring, ensure all data, even on cloud platforms, is secure and aligns perfectly with GLBA compliance requirements.
Real-time alerts and monitoring
EventLog Analyzer's real-time alert system ensures any suspicious activities are flagged immediately, keeping your operations in harmony with the GLBA's standards.
Forensics and event correlation
With EventLog Analyzer, trace and investigate the root cause of incidents using advanced search, filter, and correlation features, and ensure compliance with the GLBA's Safeguards Rule.











