- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
What is ISO 27001:2022 compliance?
ISO 27001:2022 compliance is adhering to the standards set forth by the International Organization for Standardization (ISO) for information security management. ISO 27001:2022 is a framework that provides a set of best practices for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS) within an organization. Compliance with ISO 27001:2022 ensures that an organization has appropriate controls and measures in place to manage and protect their information assets, including confidential data, personal information, and intellectual property. It is a globally recognized standard that can help organizations demonstrate their commitment to information security and improve their overall security posture.
Related content
Discover how EventLog Analyzer streamlines the process of demonstrating ISO compliance
User access control
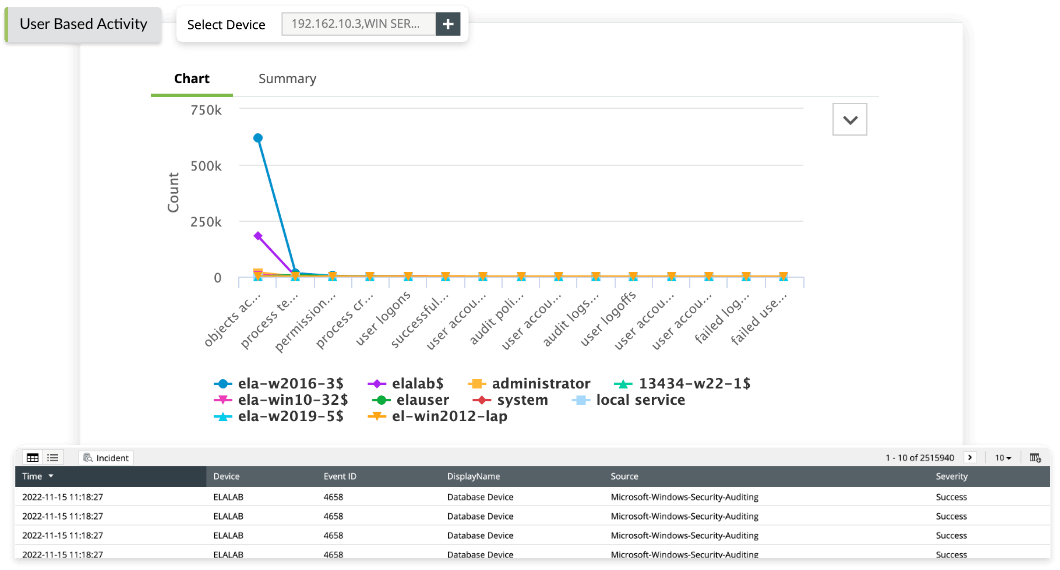
User access control is an important feature in ManageEngine EventLog Analyzer that helps organizations comply with ISO 27001:2022 requirements which relates to access control. This feature enables organizations to control access to log data by defining user roles and permissions, and restricting access to sensitive log data only to authorized personnel.
User access control helps organizations demonstrate compliance during audits and regulatory reviews by providing a record of who accessed log data, when, and for what purpose.
Log archival and retention
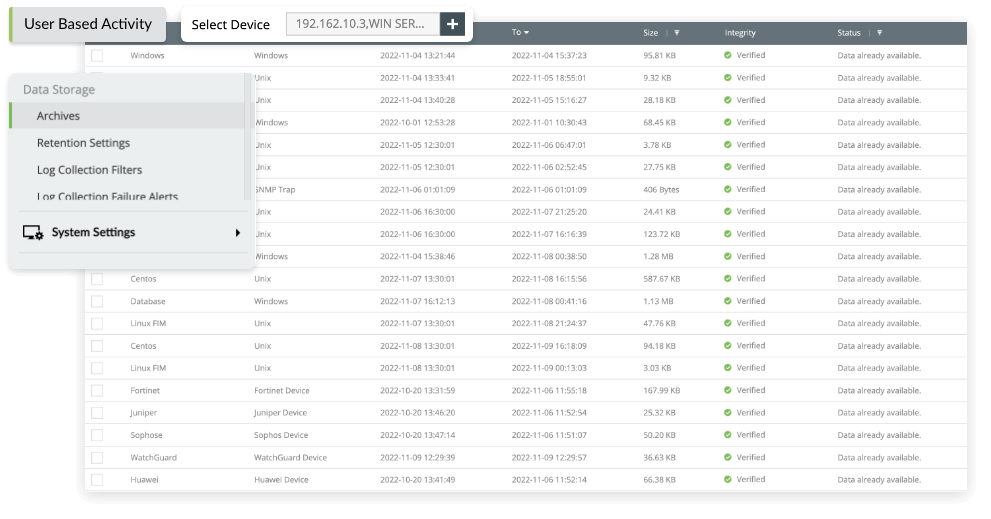
The log archival feature in EventLog Analyzer encrypts, hashes, timestamps, and stores logs along with the the time of archive creation, size of the archive, and the device whose event logs have been archived. ISO 27001:2022 specifies that logs need to be retained for at least one year. Configuring log retention in EventLog Analyzer ensures that organizations retain log data for the required period of time as specified by ISO 27001:2022.
Compliance templates
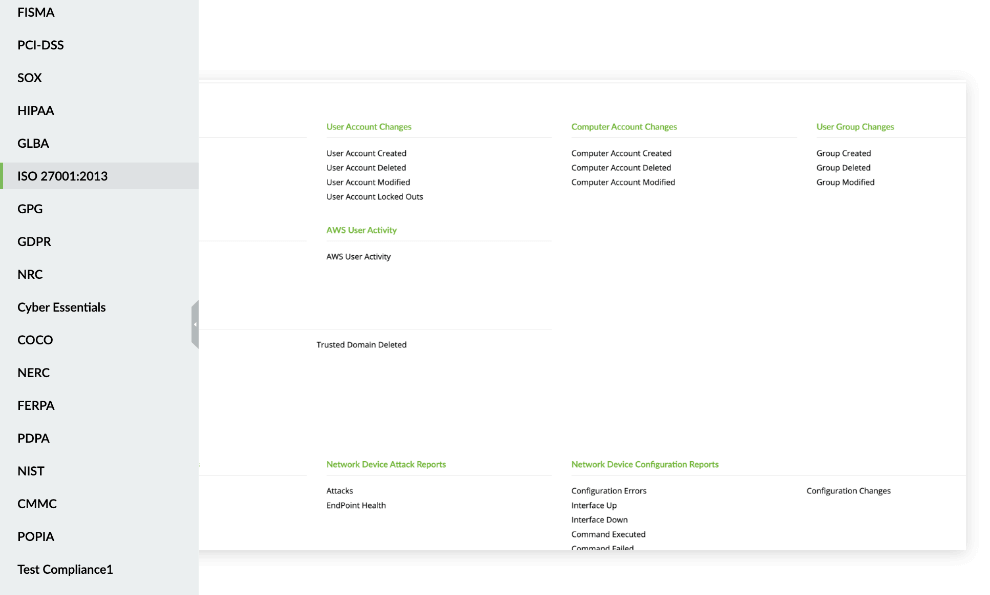
Compliance templates are prebuilt reports provided by EventLog Analyzer that help organizations comply with regulations, such as ISO 27001:2022, PCI DSS, HIPAA, and the GDPR. These templates simplify the configuration process by delivering a baseline configuration that meets the requirements of the standard or regulation, thereby saving time and effort. The prebuilt reports help organizations track their compliance status and provide evidence of compliance to auditors.
Log auditing
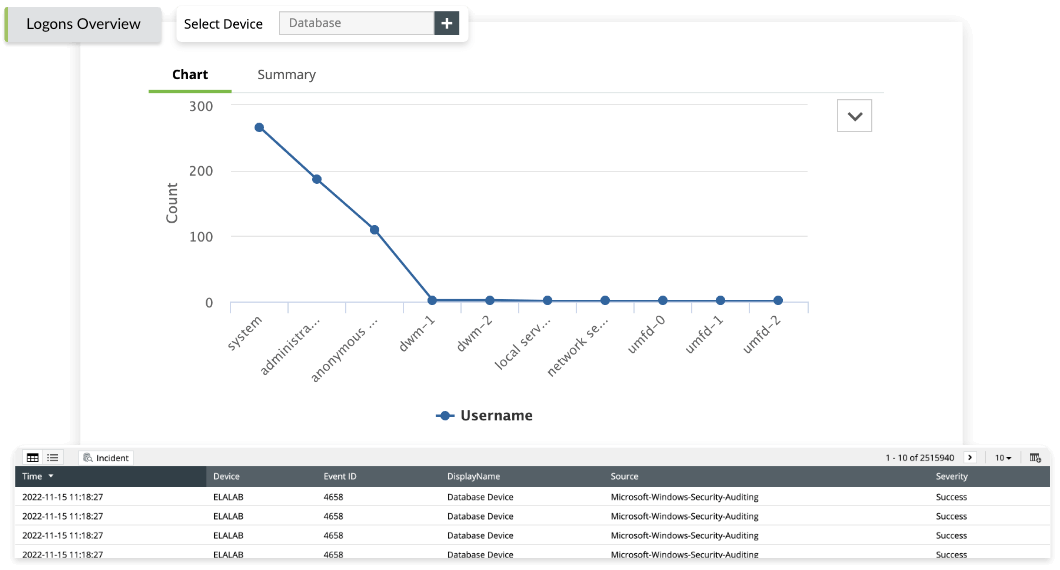
The log audit feature in EventLog Analyzer ensures the log data is properly managed and audited for ISO 27001:2022 compliance. By recording all actions taken on log data, the log audit provides a clear and detailed history of log data access and changes, which can be used to identify and investigate security incidents or compliance violations.
It can also help organizations meet ISO 27001:2022 standards related to log management and auditability, which requires organizations to maintain an audit trail of all user activities related to log management.
User and file activity monitoring
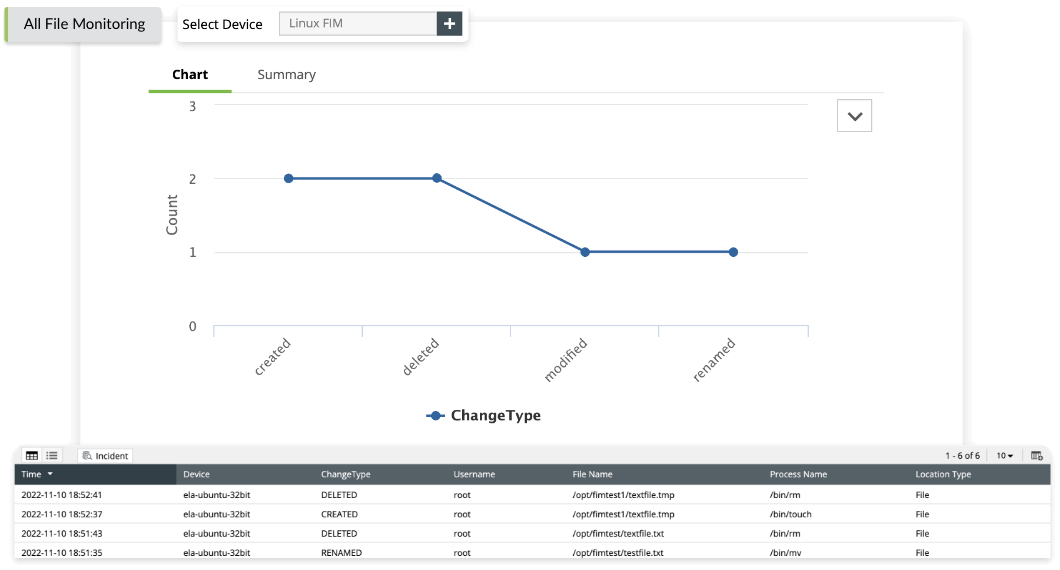
The file integrity monitoring (FIM) feature of EventLog Analyzer helps organizations comply with ISO 27001:2022. The compliance standard requires organizations to implement appropriate controls to detect unauthorized changes to critical files and folders. EventLog Analyzer's FIM feature helps organizations achieve this requirement by tracking and alerting on changes made to files, ensuring the integrity of their systems and data.
Similarly, ISO 27001:2022 requires organizations to implement appropriate controls to monitor and manage user access to critical systems and data. Tracking user logon and logoff activity and alerting on suspicious or unauthorized activity is crucial for this requirement. EventLog Analyzer's logon and logoff monitoring feature helps organizations implement procedures to monitor login attempts, report discrepancies, and detect possible abuse.
Become ISO 27001 compliance ready with EventLog Analyzer
| ISO 27001:2022 requirements | Requirement description | EventLog Analyzer reports |
|---|---|---|
| 9.2.1 User registration and deregistration | A formal user registration and deregistration process should be implemented to enable assignment of access rights. |
|
| A.9.2.5 Review of user access rights | Asset owners shall review user s' access rights at regular intervals. |
|
| A.9.4.2 Secure log-on procedures | Where required by the access control policy, access to systems and applications should be controlled by a secure log-on procedure. |
|
| A.12.4.1 Event logging | Event logs recording user activities; exceptions, faults, and information security events shall be produced, kept, and regularly reviewed. |
|
| A.12.4.2 Protection of log information | Logging facilities and log information shall be protected against tampering and unauthorized access. |
|
| A.12.4.3 Administrator and operator logs | System administrator and system operator activities shall be logged, and the logs protected and regularly reviewed. |
|
Note: EventLog Analyzer provides out-of-the-box reports for ISO 27001:2013 compliance also.
What else does EventLog Analyzer provide?
Event correlation
Correlate events from different sources to deliver a more comprehensive view of security incidents. This feature helps identify complex security attacks that involve multiple systems or applications.
Learn moreThreat intelligence
Proactively detect and respond to potential security threats and integrate with third-party threat intelligence feeds to provide real-time threat intelligence data. These features enable you to stay ahead of emerging threats and take appropriate action.
Learn morePrivileged user monitoring
Monitor and audit the activities of privileged users—such as administrators and executives—to ensure their actions comply with organizational policies and industry regulations.
Learn moreLog forensics
Perform forensic analysis on log data, which helps identify the root cause of security incidents and facilitate investigations.
Learn moreFrequently asked questions
The benefits of ISO 27001:2022 compliance include improved efficiency, increased customer satisfaction, reduced costs, and enhanced reputation. Compliance also helps organizations meet legal and regulatory requirements and reduce the risk of fines or penalties for noncompliance.
The ISO 27001:2022 certification process typically involves several stages, including gap analysis, documentation, implementation, internal audit, and external audit. During the external audit, an independent certification body reviews the organization's processes and determines whether they meet the relevant ISO standards.











