Extract New Fields to Parse and Index Logs
Network Administrators are always in need of more information and insights from their log data. There are times when an IT administrator would identify some log information which is useful and would like to have it indexed automatically as a new field. Having more fields being indexed makes your log data more useful while conducting log forensics analysis and creating network security reports.
EventLog Analyzer allows administrators to (extract or) create custom (new) fields from raw logs by using the interactive Field Extraction UI to create regular expression (RegEx) patterns to help EventLog Analyzer to identify, parse and index these custom fields from new logs it receives from network systems and applications.
Procedure to extract new fields
In the Search screen, select the host(s) or host group(s), if unsure leave it blank. Leaving it blank will search all the hosts of the host groups. Select the log type for which you want to extract new fields. To narrow down the logs, enter specific word(s) in the search query text box, if you are unsure leave it blank. Leaving it blank will list all the log entries in the result. Click Go button. This will list the results for the above mentioned search. Use the Wrench icon of the particular log entry from which you want to extract the new field(s).
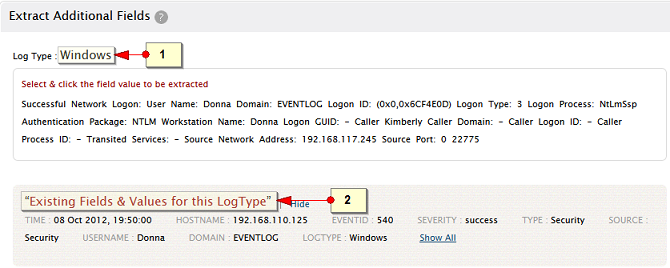
Step 1: Edit the log type and view the existing fields
-
The Log Type is displayed. For non-default log types, the display name will be name of the imported log file or hostname/port
-
View the details of the 'Existing Fields & Values for this Log Type' with the help of Show and Show All links.
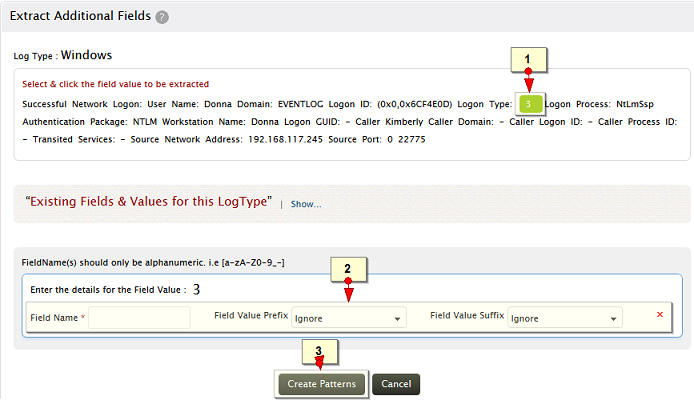
Step 2: Select the required custom field value(s) and specify the details
-
Select and click the field value in the message, to be extracted as field
-
Provide a name for this field. Specify the prefix and suffix to the field value
-
Click on Create Pattern to generate a parser rule or regex (regular expression) pattern
Note: The word(s)/character(s) precefing and succeeding the selected field value are called Prefix and Suffix. These are used as identifiers to extract the fields exactly. The prefix and suffix can have a static value (Exact Match) or dynamic value (Similar Pattern) or they can be ignored.
Example for Static and Dynamic value for Prefix and Suffix
Message : Successful Network Logon: User Name: sylvian Domain: ADVENTNET Logon ID: (0x0,0x6D51131) Logon Type: 3 Logon Process: NtLmSsp Authentication Package: NTLM Workstation Name: SYLVIAN Logon GUID: - Caller User Name: - Caller Domain: - Caller Logon ID: - Caller Process ID: - Transited Services: - Source Network Address: 192.168.113.97 Source Port: 0 22873
The prefix Logon Type can be a static value as most of the logs will have the exact word as 'Logon Type' where as 'Source Network Address' can be dynamic as the logs may have different word(s) like, Source IP Address, Source Address, but with same pattern.
If the prefix and suffix are defined with exact match, the field extraction will be precise.
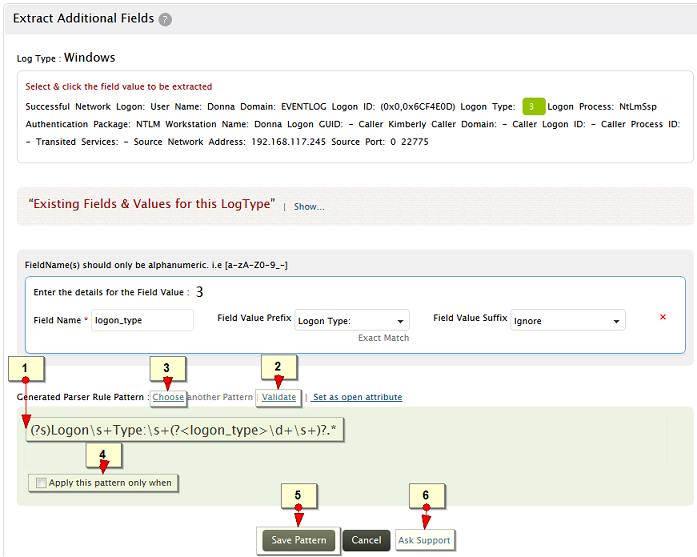
Step 3: Validate the pattern and save it to extract the new field
-
A parser rule pattern is created using the field definition.
-
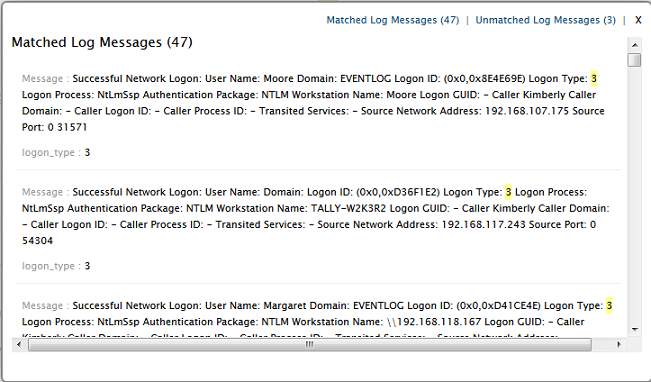
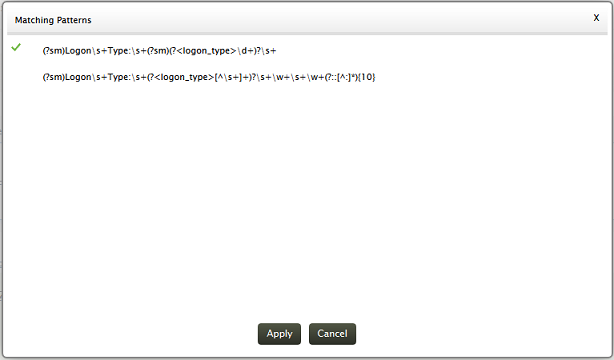
Validate link is used to test the generated pattern against the previous search results. You can manually check the suitability of the pattern by analyzing the 'Matched Log Messages' and 'Unmatched Log Messages' displayed
Screen shot of Validate check
-
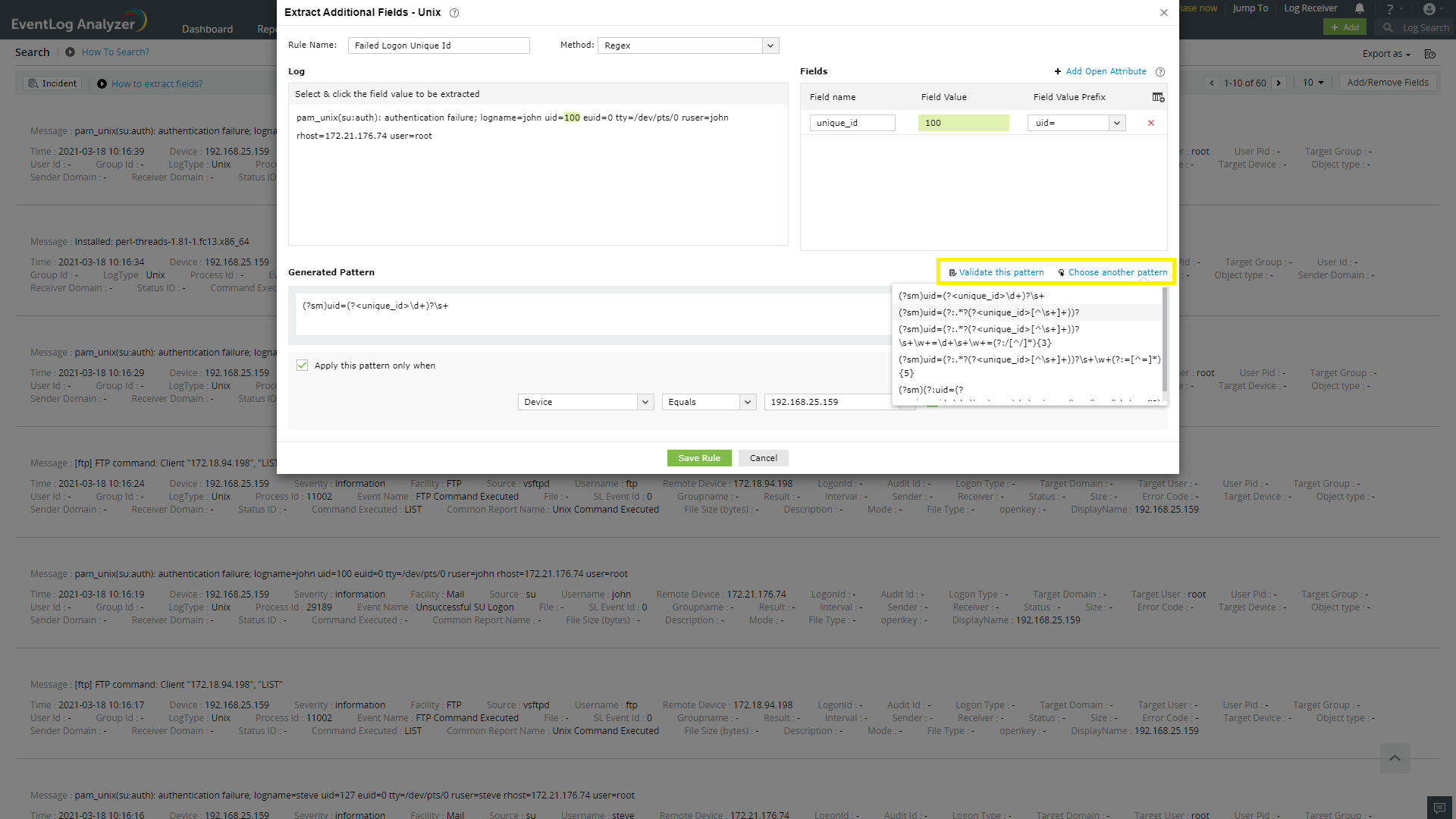
On validation, if the matched log messages of generated pattern does not meet your field definition requirement, the pattern needs to be fine tuned. You can edit the generated pattern manually, if you are familiar with regular expressions (regex). Optionally, click on Choose another Pattern to choose a pattern from a list of patterns generated by the application
Screen shot of patterns generated by the application
You can add a open attribute to this new field. The procedure to add open attribure is shown below in the screen shot.
-
Optionally, you can define any existing field matching criteria to apply the pattern for this specific log type
-
Save the pattern to enable EventLog Analyzer to identify, parse and index these custom fields from the new logs it receives from network systems and applications. While saving the pattern, a pop-up window asks for an option to save this pattern as identity rule for this user defined log type.
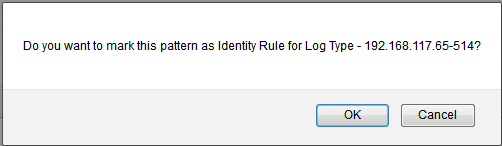
The custom pattern (parser rule) can be marked and unmarked as Identity rule for that user defined log type. Multiple custom patterns can be marked as Identity rules for a particular user defined log type.
The saved pattern will be listed in the Settings tab under Custom Pattern Settings section.
-
Use the Ask Support button, if you face any problem and get assistance from the EventLog Analyzer team


















