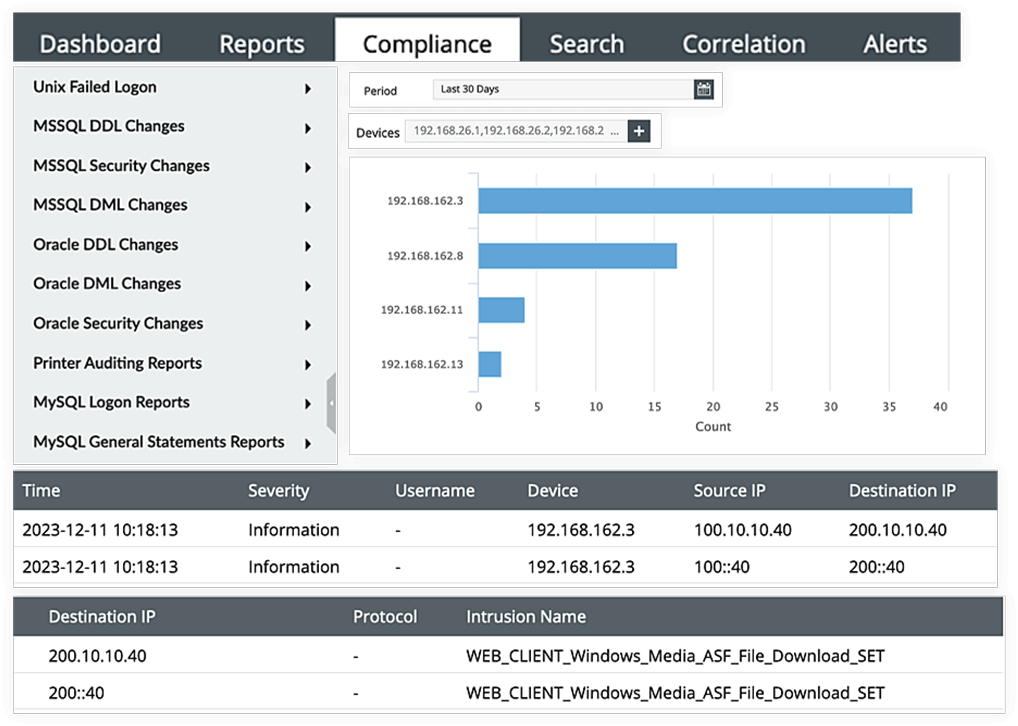
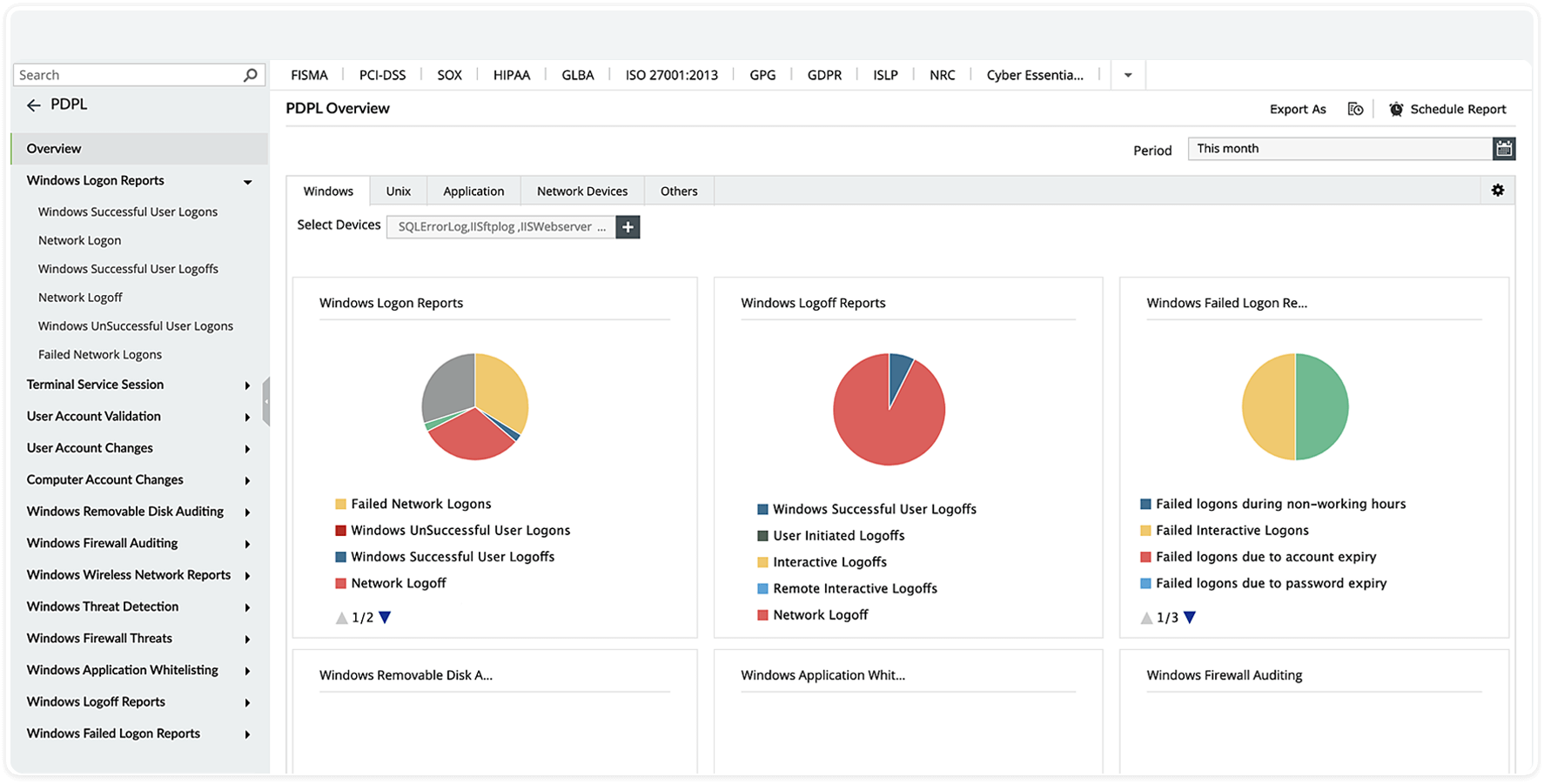
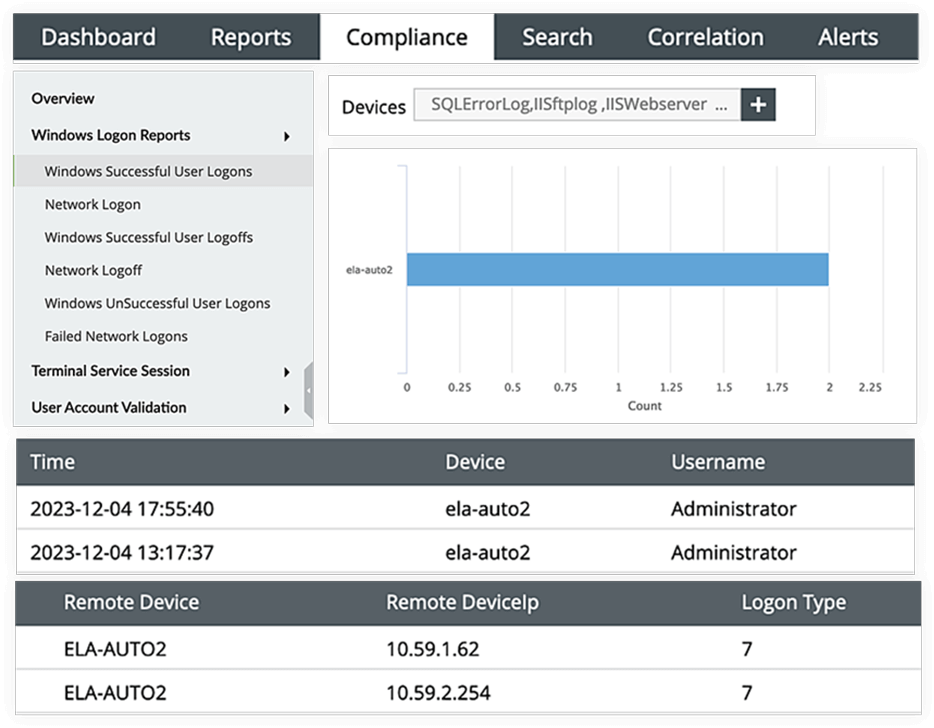
EventLog Analyzer empowers you to meet PDPL requirements and enhance overall information security by monitoring your diverse network entities. It offers a comprehensive suite of reports, particularly to address Article 19 of the PDPL on information security. These reports focus on safeguarding personal data privacy throughout the processing, usage, and transfer stages. The solution actively monitors user logins and logoffs on the network, recording details such as user name, timestamps, and source device. This feature is crucial for quickly detecting and responding to any suspicious behavior, ensuring robust protection for your network.
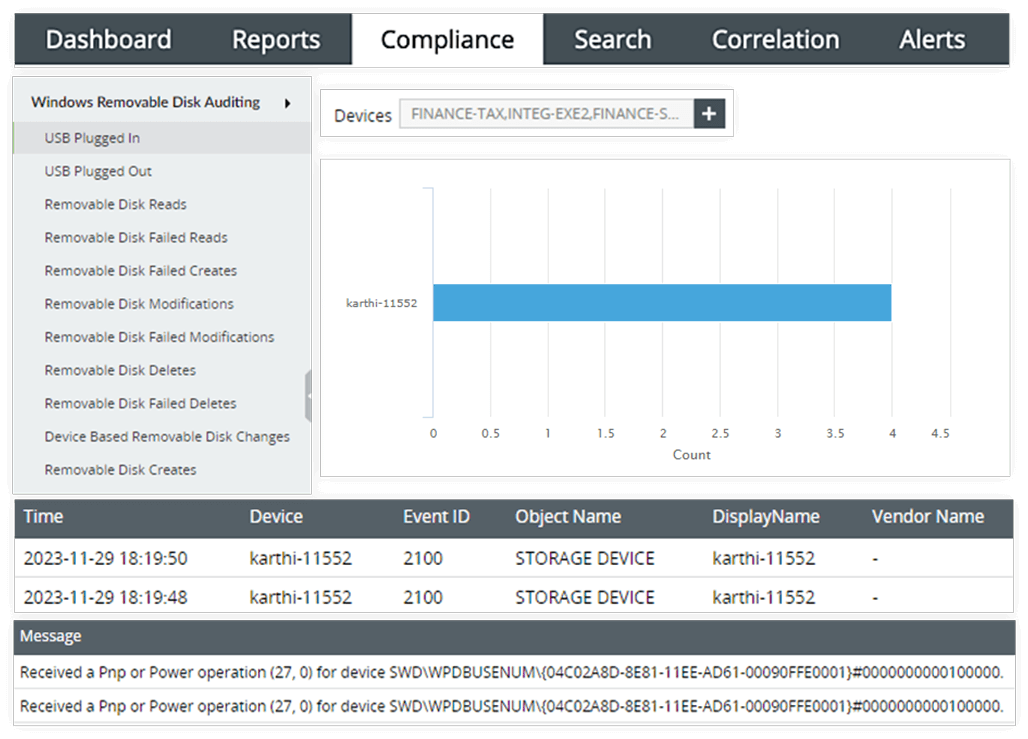
EventLog Analyzer meticulously audits USB device activities using Windows event logs for all actions involving removable disks. This includes tracking disk insertions and removals, monitoring file transfers, and noting modifications to disk properties to facilitate easy tracking and investigation of suspicious or unauthorized removable disk activities. The tool enhances security with real-time alerts for device usage, and its predefined reporting on USB activities helps prevent data theft. EventLog Analyzer's compliance capabilities align with the standards of Articles 19 and 21 of the PDPL, ensuring both data protection and regulatory adherence.
EventLog Analyzer proves PDPL compliance through automated collection and analysis of logs from prominent database servers, such as Microsoft SQL, Oracle, MySQL, Db2, and PostgreSQL. The solution promptly identifies and notifies users of any suspicious activities, such as unauthorized logons, execution of data definition language (DDL) or data manipulation language (DML) queries, password changes, permission modifications, privilege escalation, or role changes. By actively monitoring and reporting database changes, EventLog Analyzer ensures compliance with Article 19 of the PDPL. Aligning with Article 20, it systematically captures and tracks alterations to database security settings, offering a detailed overview of these changes.
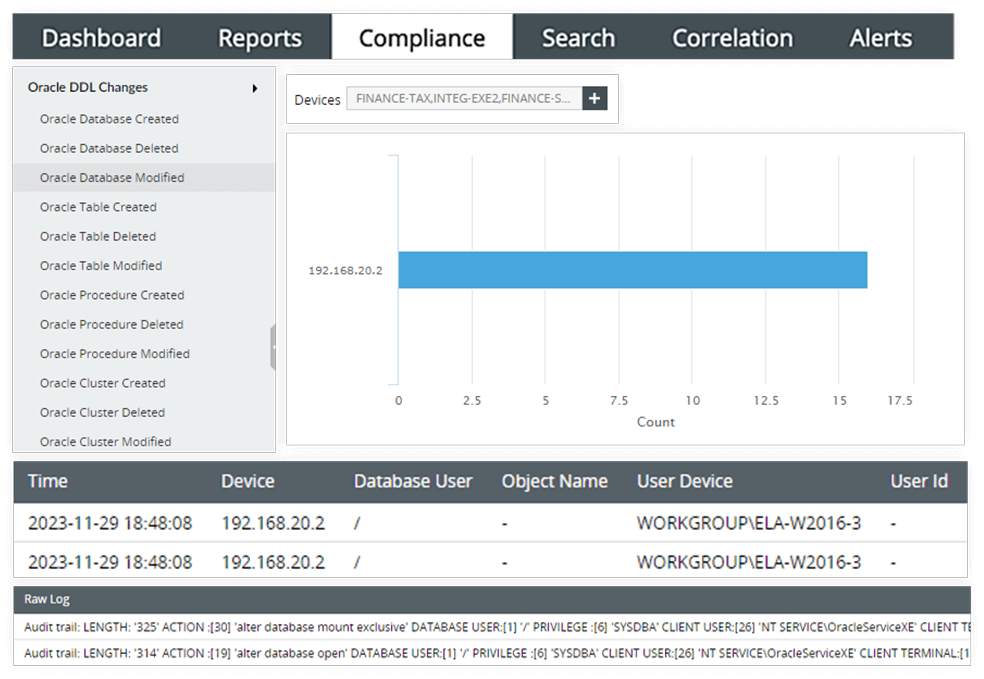
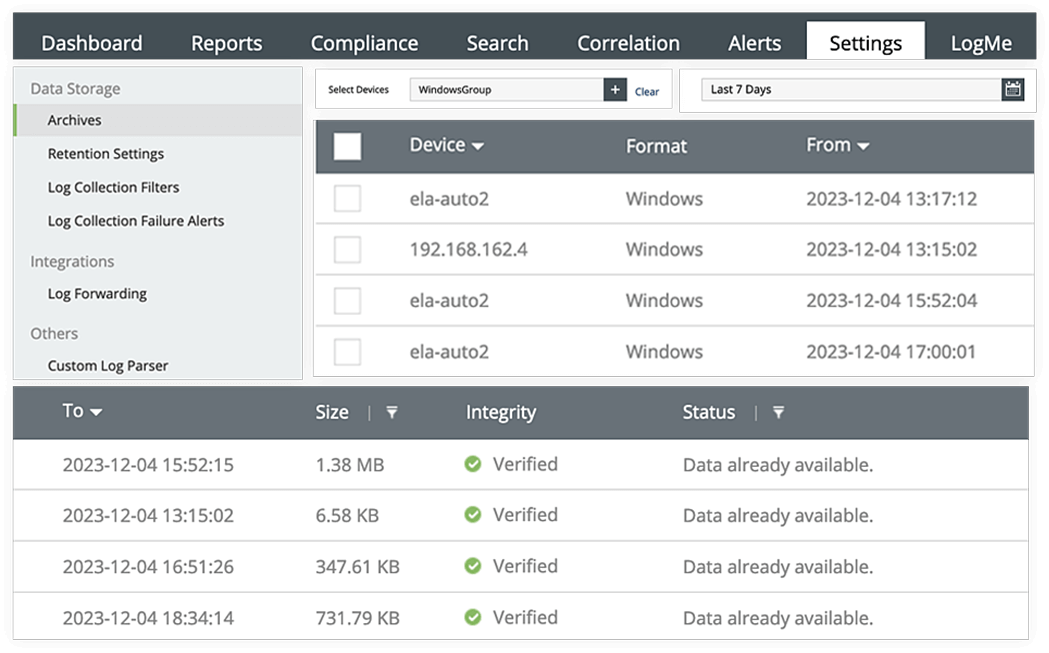
In accordance with Article 20 of the PDPL, the controller is obligated to implement a comprehensive set of measures to protect health data from unauthorized use and breaches. This requirement is met seamlessly with EventLog Analyzer's log archiving feature, which employs structured and comprehensive recording for the collection, processing, storage, and destruction of logs containing personal data. This archived log data serves as a historical record that can be reloaded at any time for log forensic analysis. It enables swift incident response, aids in compliance audits, and facilitates thorough investigations into data theft.
EventLog Analyzer's real-time alerting system promptly notifies the controller upon detecting any breach, damage, or unauthorized access to personal data. This notification facilitates swift responses in accordance with Article 20(1) of the PDPL. The solution offers a comprehensive view of user interactions with sensitive information, vigilantly monitoring files and folders containing confidential data and generating instant alerts when critical changes are detected. Additionally, it helps detect illicit access requests, enabling proactive mitigation of potential risks and ensuring a secure data environment.
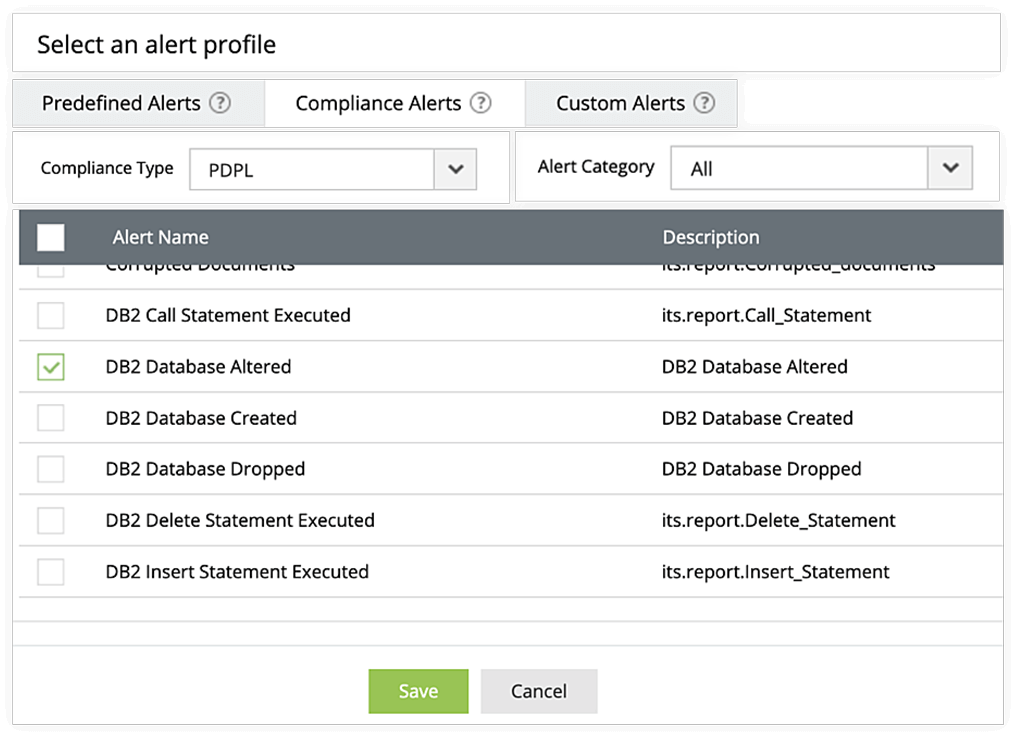
Dive deep into detailed logs and leverage the audit-ready report templates, making compliance checks a breeze. EventLog Analyzer simplifies the process of conducting detailed audit trails, seamlessly aligning with the specifications outlined in Article 19 of the PDPL. The solution's powerful log analysis and reporting features not only create comprehensive audit trails but also enhance overall compliance efforts. Controllers can efficiently generate thorough reports and stay well prepared for regulatory obligations with ease.