| POPIA requirements |
EventLog Analyzer reports that can help |
Chapter 2 - Section 4
Personal information should be lawfully processed.
Chapter 3 - Section 19 (1) (a)
Enterprises must secure the integrity and confidentiality of personal information in its possession or under its control by taking appropriate, reasonable technical and organizational measures to prevent loss of, damage to, or unauthorized destruction of personal information; and unlawful access to or processing of personal information.
|
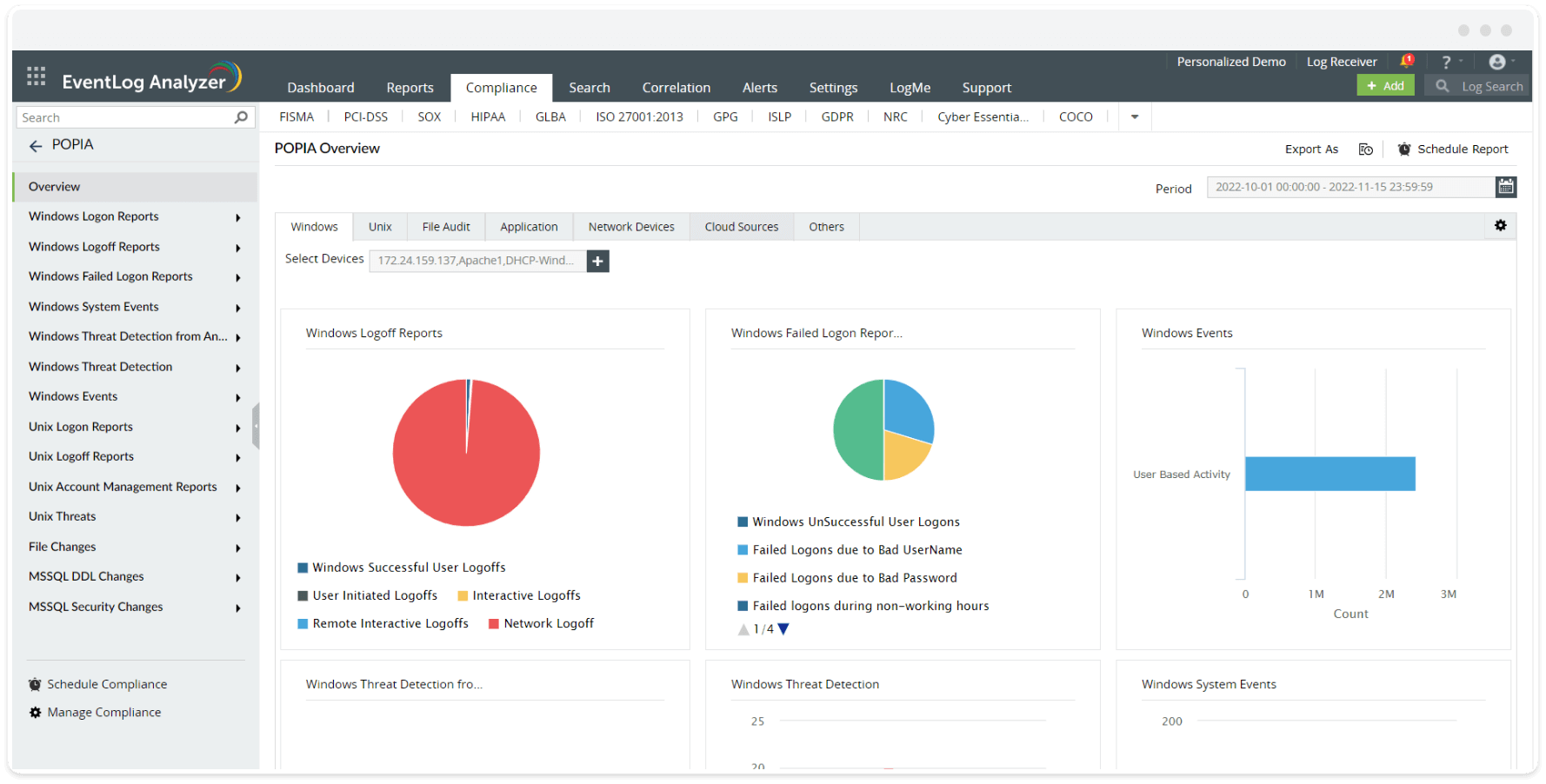
Ensuring integrity of personal information requires constant monitoring of user activities—user logons, logoffs, and any change inside of that user's scope to ensure that it is legitimate change and not an unauthorized event that affects the integrity and confidentiality of the personal information. EventLog Analyzer helps you ensure the integrity and confidentiality of information by monitoring and providing you reports on:
- Windows logon and logoff reports
- Windows failed logon reports
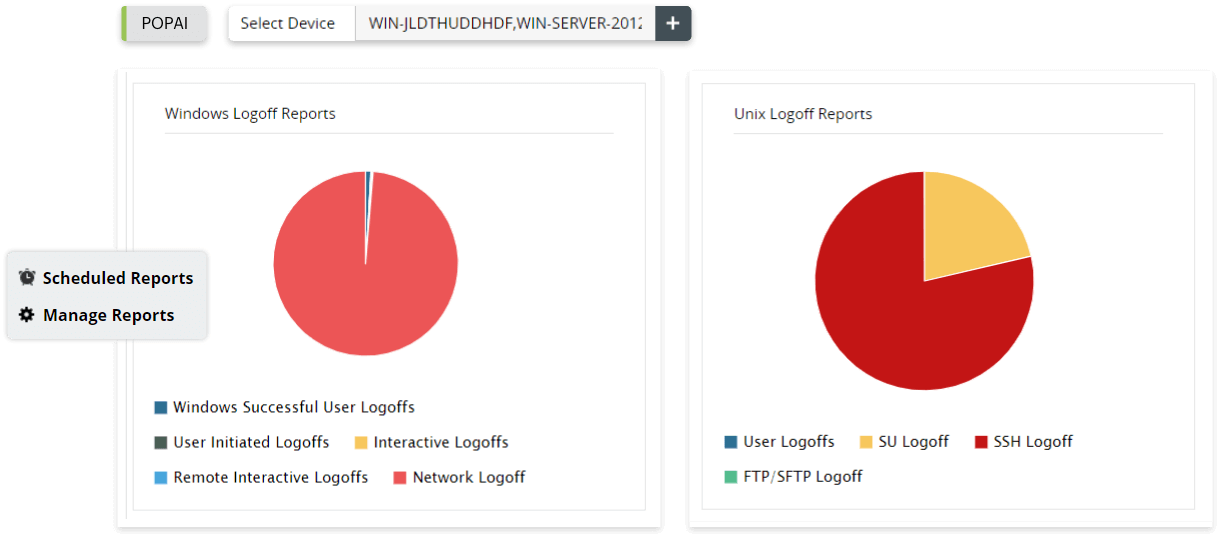
- Unix logon and logoff reports
- Unix and network account management reports
- Network device logon reports
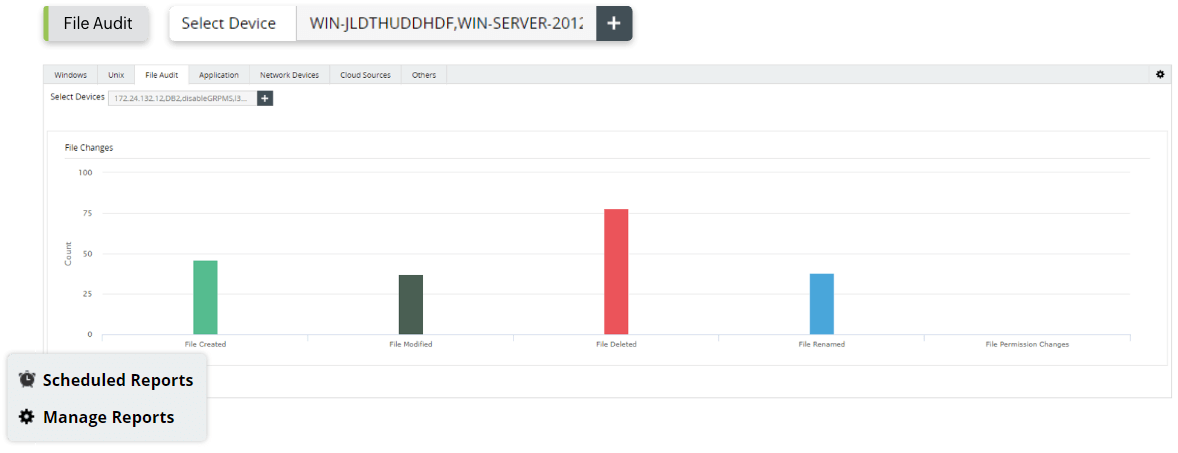
- File change audit reports
- AWS network security groups reports
- Cloud user login activity reports
|
Chapter 3 - Section 19 (2) (a)
Organizations must identify all reasonably foreseeable internal and external risks to all the personal information in its possession or under its control.
|
In order to foresee internal and external risks, it's imperative for organizations to monitor every change and risks from failed login attempts and password changes to account management reports. EventLog Analyzer's reports provide a detailed overview of all the data processing activities within your organization, such as how personal data is collected, processed, stored, and shared. These reports highlight areas where your data could be vulnerable to internal and external threats and provide strategies for mitigating these risks.
- Windows logon and logoff reports
- Windows failed logon reports
- Windows threat detection reports
- Unix logon and logoff reports
- Unix account management reports
- MSSQL DML changes reports
- MSSQL account change reports
- MSSQL password change reports
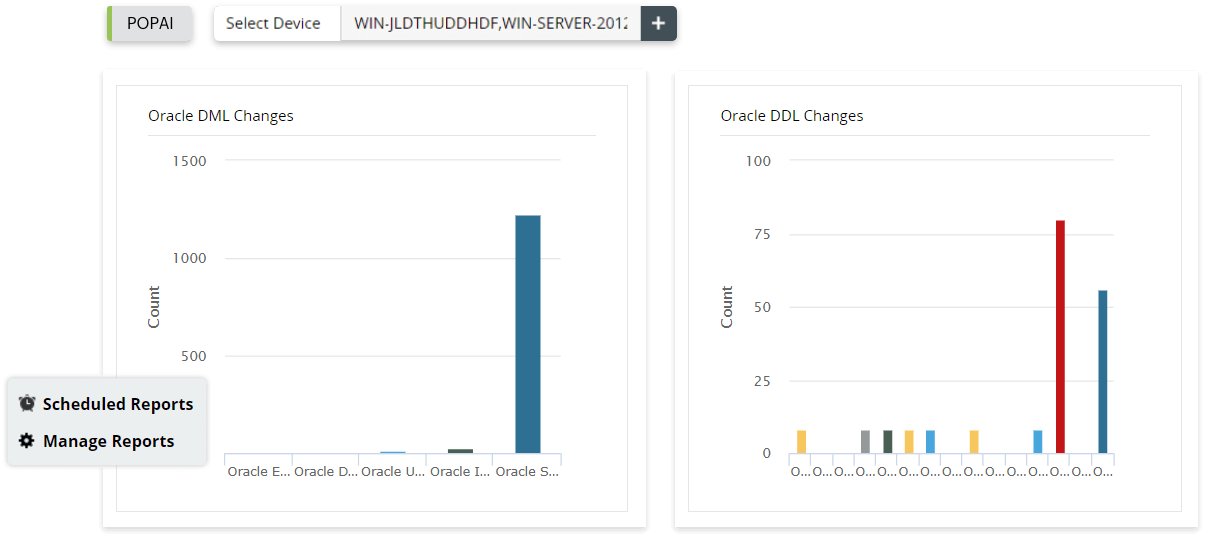
- Oracle auditing server reports
- MySQL logon reports
- File changes audit reports
- AWS network security groups reports
- Cloud user login activity reports
- Symantec DLP reports
- FireEye reports
- Malware bytes reports
- Trend Micro policy management reports
- Trend Micro user account management reports
- Trend Micro security reports
- Symantec endpoint reports
- McAfee reports
|
Chapter 3 - Section 20 (1) (b)
Any operator processing the personal information on behalf of a responsible party or an operator to ensure they are treated as confidential subjects and must not disclose it unless required by law or course or proper performance of their duties.
Chapter 3 - Section 19 (2) (a)
Organizations must Identify all reasonably foreseeable internal and external risks to all the personal information in it's possession or under control.
|
To be compliant with this section of POPIA, organizations need to monitor unauthorized changes to critical files, folders, and configurations or any report that can help identify unauthorized disclosure or modification of personal information. These reports also monitor changes in security configurations of databases to prevent data leaks and priviledge escalations.
- File changes reports
- MSSQL DDL and DML changes reports
- MSSQL security changes reports
- Oracle DDL and DML changes reports
- Oracle security changes reports
- MySQL general statements reports
- DB2 DDL and DML changes reports
|
Chapter 3 - Section 22 (5) (a)
Organizations must provide sufficient information to take proactive measures against the potential consequences of the compromise, including a description of the possible consequences of the security compromise.
|
These reports help in tracking any changes, failures, or suspicious activities within the Windows operating systems and Unix systems. In addition, monitoring network devices for signs of attacks helps identify potential vulnerabilities or unauthorized access attempts on network devices. Since network devices are often the gateway for accessing stored data, including personal information, monitoring these reports helps ensure that the network is secured against breaches.
- Windows system events reports
- Windows threat detection reports
- Unix threats reports
- Network device attack reports
|