| Control families |
Description |
Reports |
| M1. Strategy and Planning |
An information security strategy should be defined and an operating model is to be developed to adhere to the strategy. Information security plans should be developed for every major service to identify and mitigate risks. |
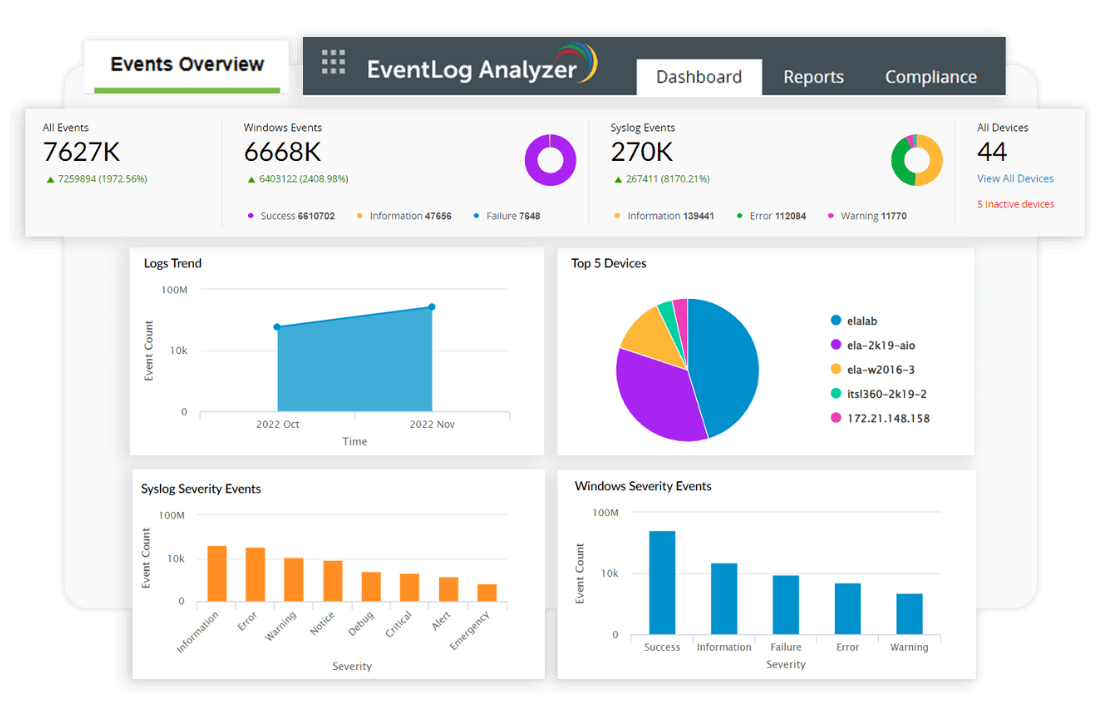
EventLog Analyzer generates detailed reports on security events and incidents, providing valuable insights for developing and refining information security plans. |
| M2. Information Security Risk Management |
An information security risk management process should be implemented. An awareness and training program should also be established. |
EventLog Analyzer provides forensic analysis by retaining logs for retrospective investigation, and its automated incident response workflows ensure swift responses to identified risks, minimizing potential security incident impacts. |
| M5. Compliance |
Organizations should comply with legal requirements, security policies, and technical standards. |
EventLog Analyzer aids in UAE NESA compliance by automatically generating predefined compliance reports for regulations, including legal requirements and security policies. |
| T1. Asset Management |
Assets should be managed and information should be classified and labeled. |
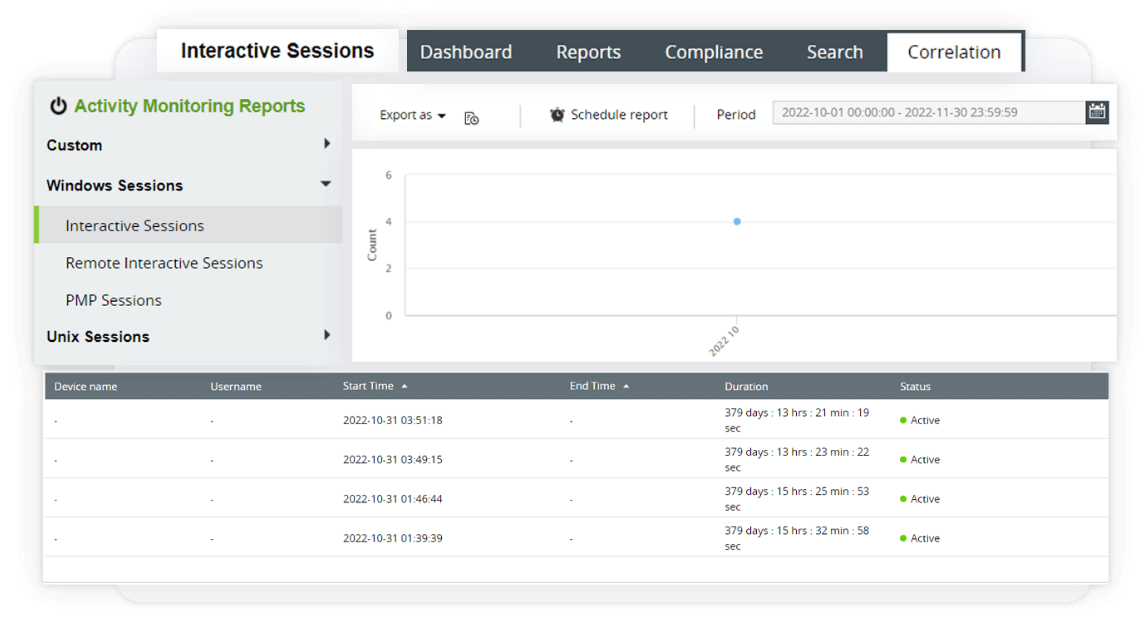
EventLog Analyzer's real-time monitoring capabilities, log analysis, and reporting functionalities support organizations in keeping track of asset activities and ensuring compliance. |
| T3. Operations Management |
To ensure an appropriate level of information security, it is crucial to establish operational procedures and clearly define responsibilities. |
- SQL Server Logons
- Eventlog Reports
- Threat Detection From Antivirus
- Windows Threat Detection
- Malwarebytes Reports
- File Changes
- Symantec reports
|
| T6. Third-Party Security |
Third-party security management should be done to ensure that third parties implement and uphold the necessary level of information security and service delivery. |
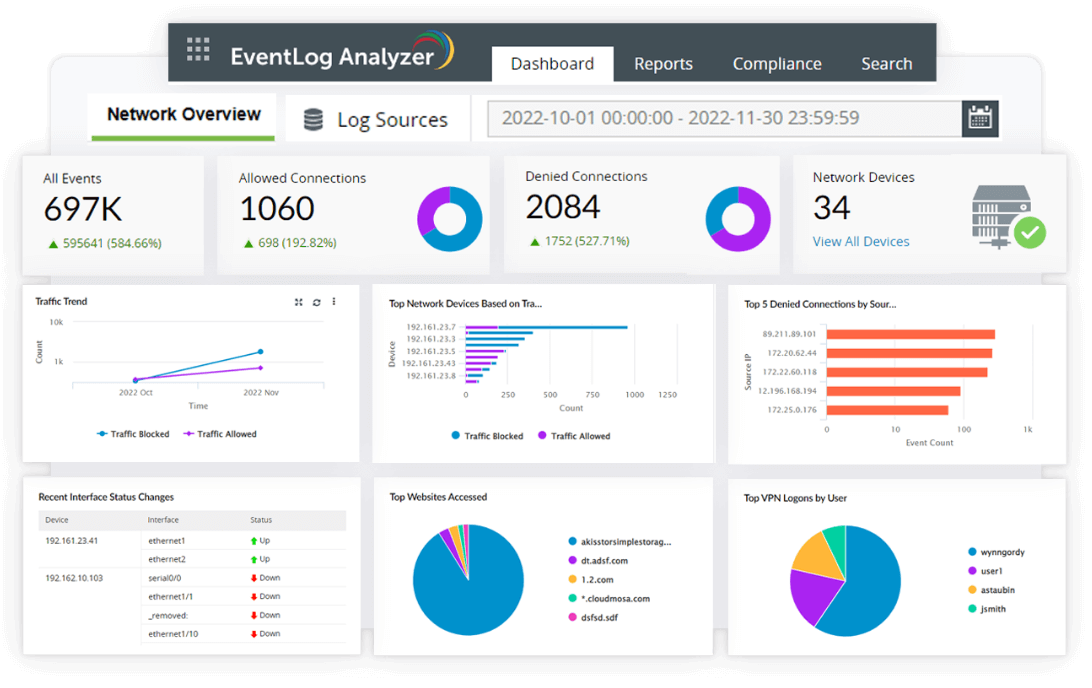
EventLog Analyzer provides organizations with the tools to oversee and monitor the security practices of external parties, contributing to compliance with T6 requirements. |
| T8. Information Security Incident Management |
Maintain an information security incident management policy covering the information security incident procedures covering the detection, reporting, and treatment of incidents. |
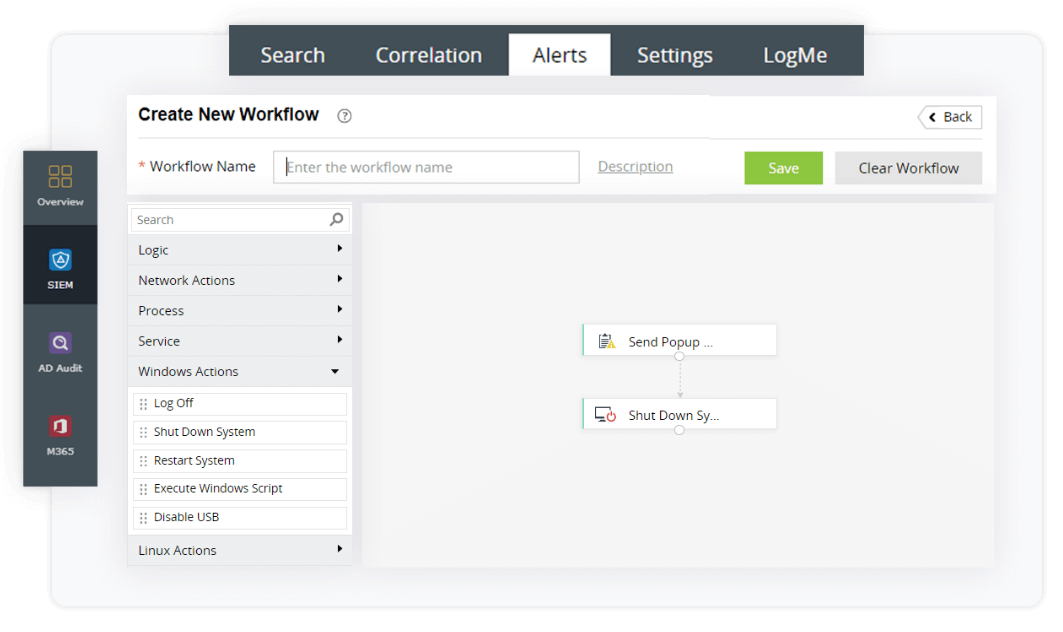
EventLog Analyzer's incident response and management console alerts the users when critical events occur. |