Forensic log analysis
The primary purpose of a network security solution is to protect the network from attacks. It should monitor security events and alert you in real time to help you take remedial actions as soon as possible. In addition, you require in-depth information to analyze the root cause of any vulnerabilities, attack event reconstruction, and user activity; that's where forensic log analysis comes into the picture.
Forensic log analysis is a critical process in cybersecurity, focusing on examining and interpreting logs generated by various network devices, applications, and systems to uncover the details of security incidents. Logs are records of events that occur within an IT environment, including user activities, system events, and communications between devices. Forensic log analysis helps security teams trace the steps of a potential attacker, understand how an attack occurred, and identify vulnerabilities that need to be addressed to prevent future incidents.
Importance of forensic log analysis
Forensic log analysis is a vital process in the aftermath of a security incident. When a network breach occurs, understanding how the attack happened, identifying the entry points, and determining the extent of the damage are essential. Forensic log analysis helps in:
- Incident detection and Response: Forensic log analysis is vital for detecting and responding to security incidents. By analyzing logs, security teams can quickly identify signs of malicious activity, such as unauthorized access attempts, data exfiltration, or unusual network traffic patterns. This enables a rapid response to contain the threat and minimize damage.
- Root cause analysis: When a security breach occurs, it's crucial to understand how it happened. Forensic log analysis provides insights into the sequence of events leading up to the breach, helping identify the root cause. This information is essential for closing security gaps and preventing similar incidents in the future.
- Compliance and legal requirements: Many industries have strict regulations requiring organizations to maintain detailed logs and perform regular forensic analysis. This helps ensure that organizations can provide evidence of compliance and protect themselves from legal liabilities in the event of a security breach.
- User activity monitoring: Forensic log analysis allows organizations to monitor user activities, ensuring that employees and other users adhere to security policies. It can also help detect insider threats by identifying suspicious behavior, such as unauthorized access to sensitive data.
- Post-incident investigation: After a security incident, forensic log analysis is used to reconstruct the attack, understand the attacker’s methods, and determine the extent of the breach. This information is crucial for improving security measures and preventing future attacks.
Challenges in forensic log analysis
While forensic log analysis is invaluable, it comes with its own set of challenges:
- Volume of data: Modern IT environments generate an enormous amount of log data from various sources, including firewalls, intrusion detection systems, servers, and applications. Analyzing this vast amount of data to find relevant information can be overwhelming.
- Log integrity: Ensuring that logs are secure and have not been tampered with is a significant challenge. If an attacker gains access to logs, they may alter or delete entries to cover their tracks, making it difficult to perform an accurate analysis.
- Complexity of log formats: Logs from different systems and devices often use different formats, making it challenging to correlate data across various sources. This complexity can slow down the forensic analysis process and make it more difficult to identify patterns or connections between events.
- Real-time analysis: While forensic log analysis is often performed after an incident, there is an increasing need for real-time analysis to detect and respond to threats as they occur. This requires advanced tools that can quickly process and analyze log data in real time.
- Skill and expertise: Effective forensic log analysis requires a deep understanding of network security, system architecture, and log analysis techniques. Organizations may struggle to find and retain the necessary talent to perform this work effectively.
Firewall Analyzer: Leading forensic log analysis tool
The basic requirements of a forensic log analysis tool include being secure and tamper-proof, and having the ability to archive logs for a specific and flexible period of time. It's not enough to just have historical log data available; you need a powerful search engine to parse these logs and discover the exact information you require for investigation.
ManageEngine Firewall Analyzer is the ideal solution for archiving log data and conducting forensic log analysis. Using this tool, you can choose the storage duration of archived forensic analysis logs, ensure the data is encrypted for security and time-stamped for tamper-proofing, index the archive data flexibly for optimal search, and use the tool's powerful engine to search both the aggregated logs and raw logs. With the added ability to save the search results as reports, you can save time and avoid repeated searches.
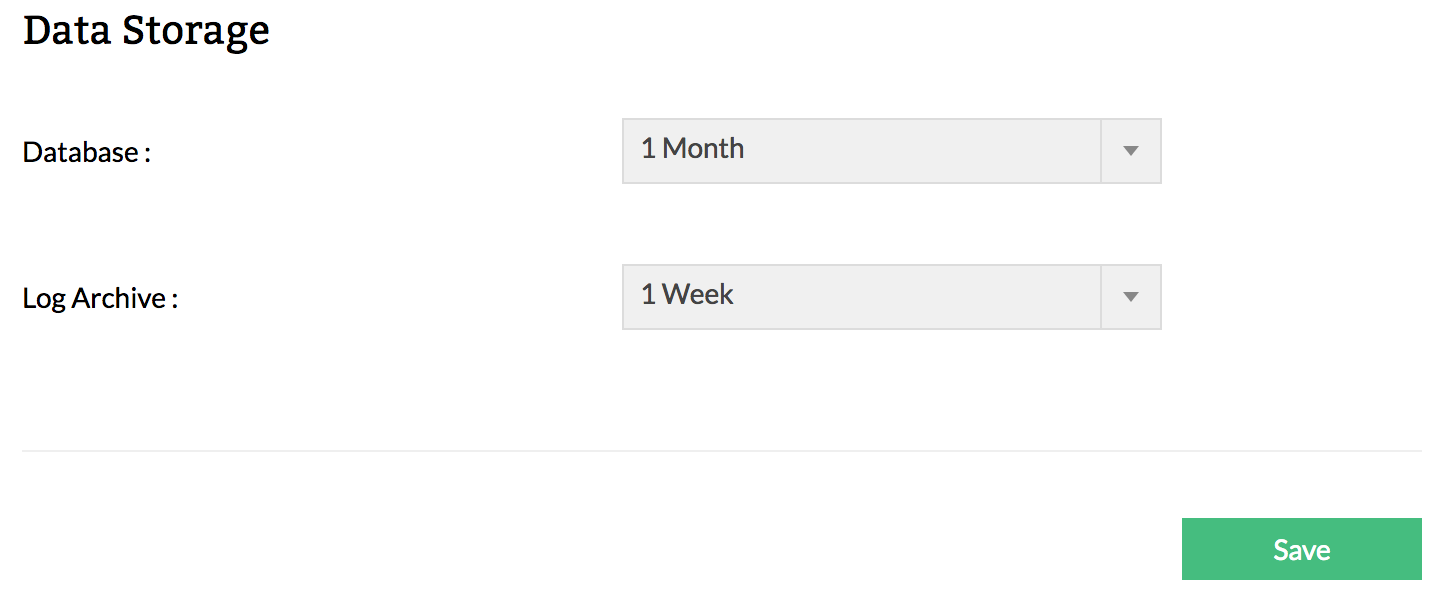
Flexible log archive retention time
This firewall forensics tool archives firewall logs for a flexible time period as per your requirement. Because various regulatory standards mandate different retention periods and your own organization may have one as well, it's important to be able to configure your own archive retention time. Additionally, you can also choose the data retention time of the database.
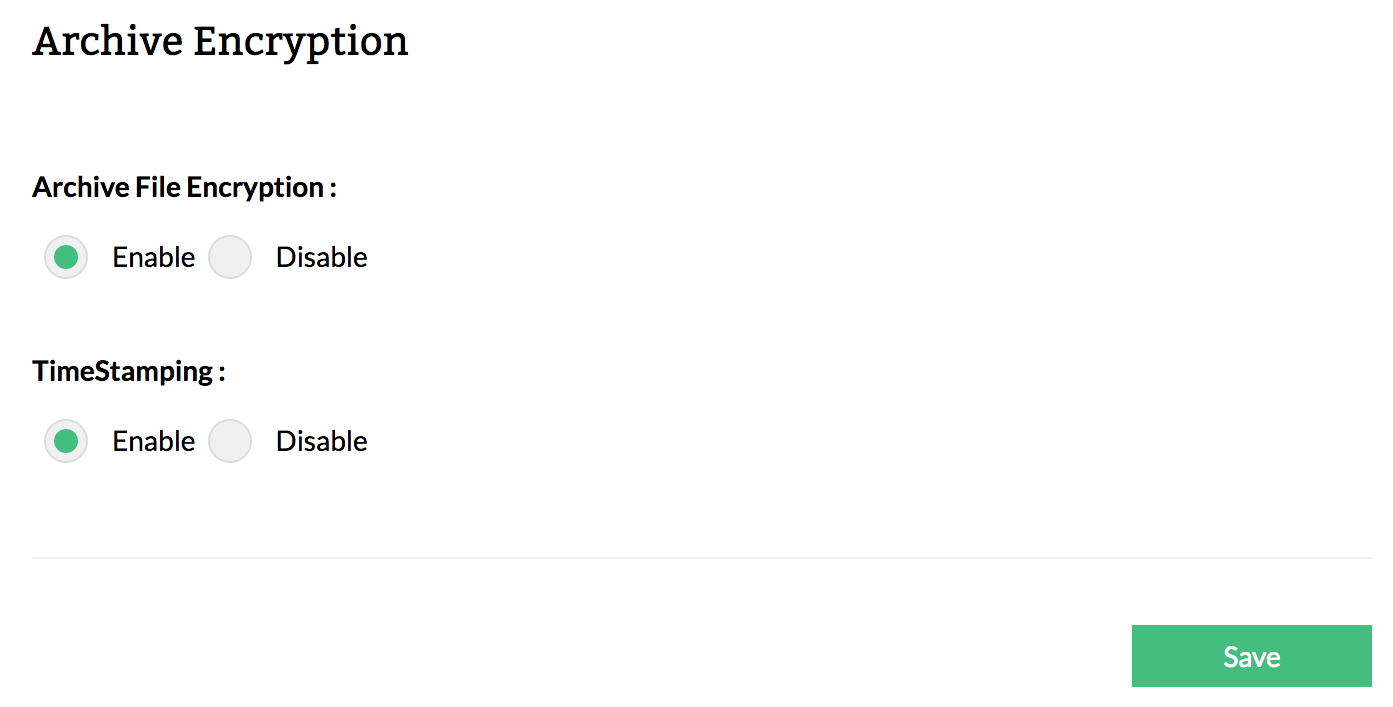
Secure and tamper-proof log archive
This network logs forensics tool secures logs with encryption, ensuring that the logs cannot be read even if they land into the wrong hands unintentionally. Firewall Analyzer also provides time-stamping on log files. Time-stamping prevents the saved logs from being tampered with by any user trying to destroy the evidence of a security attack.
Flexible indexing of log data
Firewall Analyzer has the ability to import and index archived logs. Log indexing is a CPU-heavy and memory-consuming task; to minimize the CPU load and memory consumption, you can choose to index only security logs, or both security and traffic logs. The forensic analysis security logs are critical for finding the cause of an attack or hack.

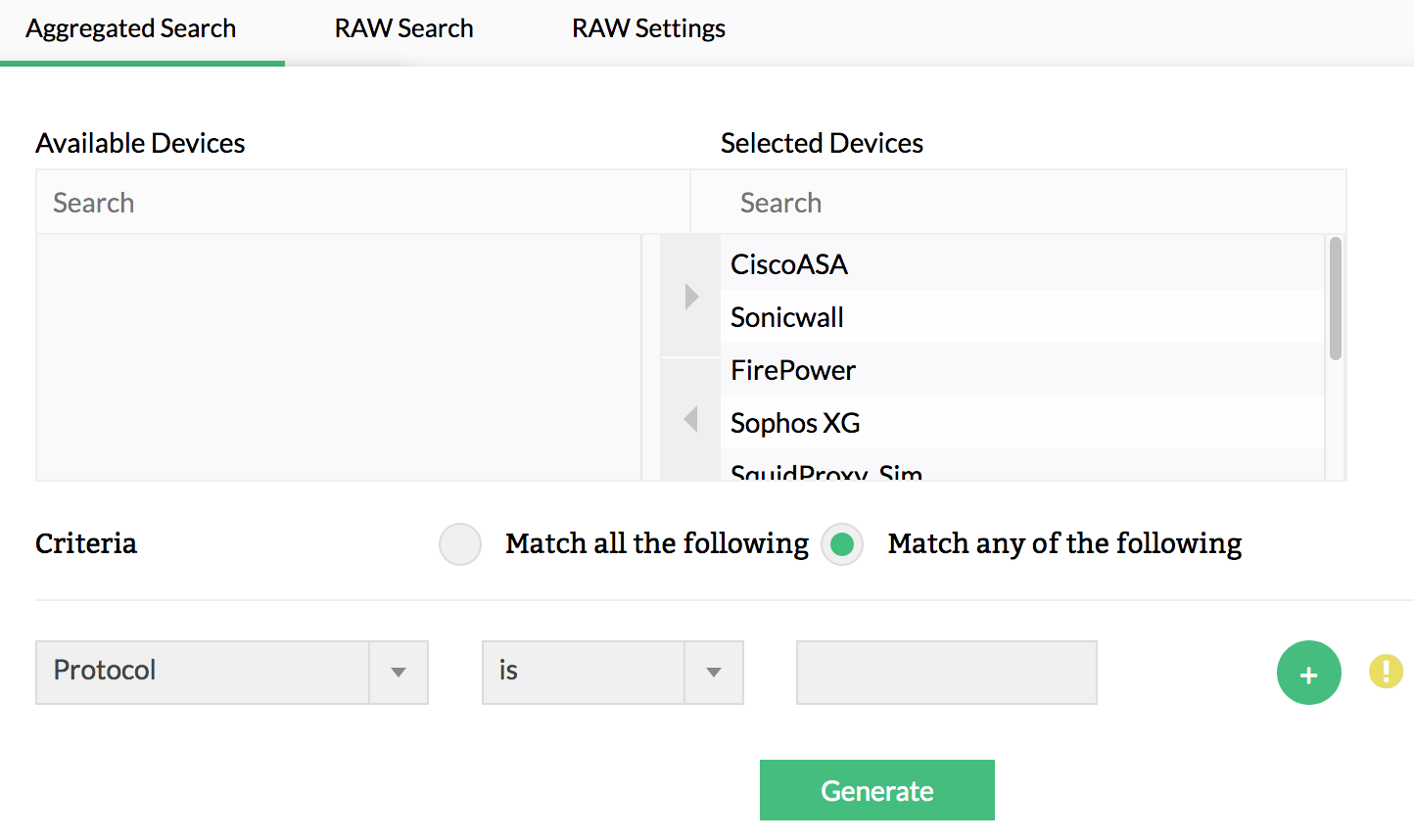
Why you need a powerful search mechanism for forensic log analysis
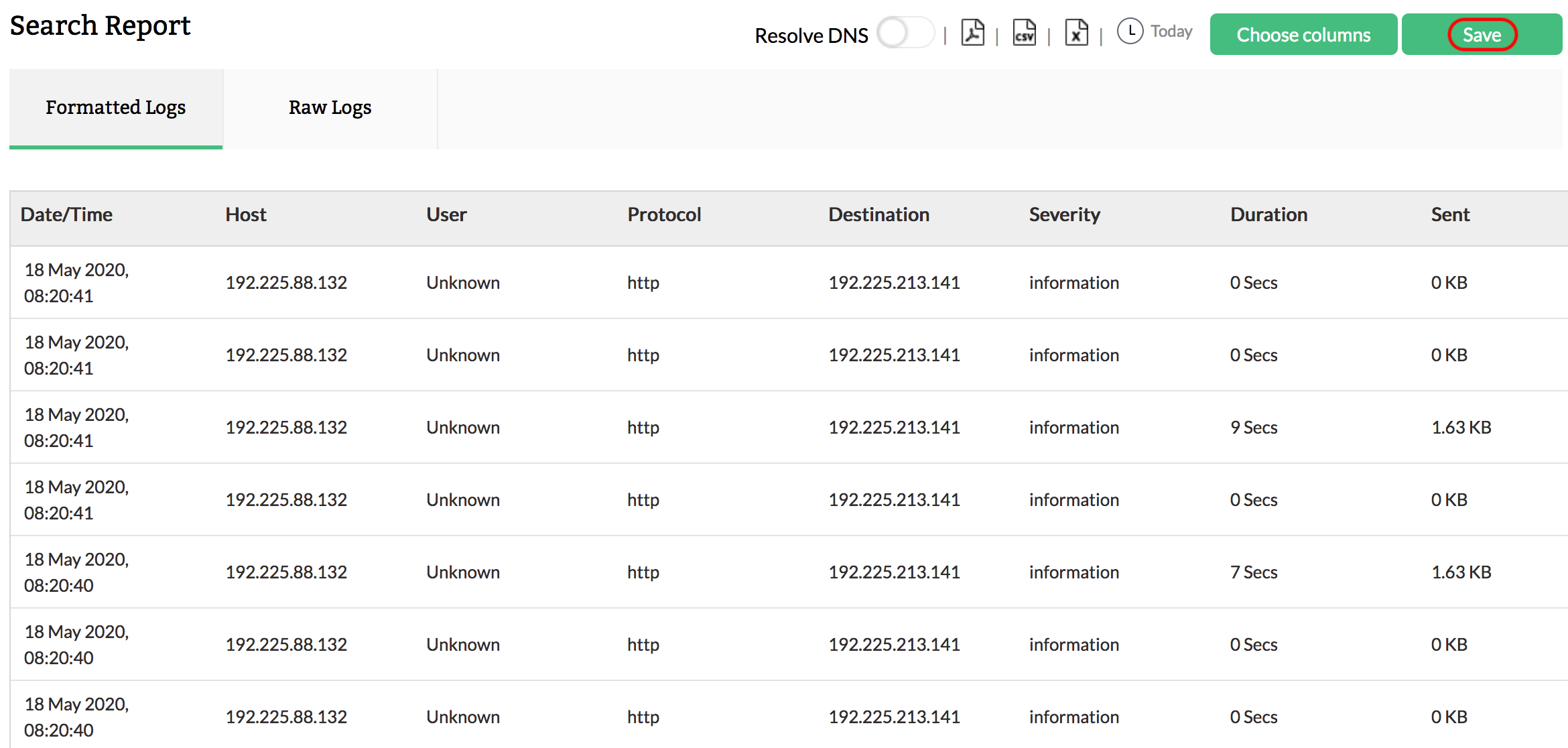
The log archive contains a huge amount of logs. However, the evidence of an attack is only present in a few. It's nearly impossible to manually pinpoint the exact logs that contain this information, and you may have to apply many criteria and filters to drill down to the exact logs of the incident. Even with a fairly good search engine, it can be a tough task. Firewall Analyzer’s log search engine is robust enough to easily and efficiently pull the required logs from the archive by offering both a raw log and formatted log search. If you cannot fetch the desired results with the formatted log search, you can use the indexed raw log search; most of the time, the formatted log search will suffice for forensic log analysis.
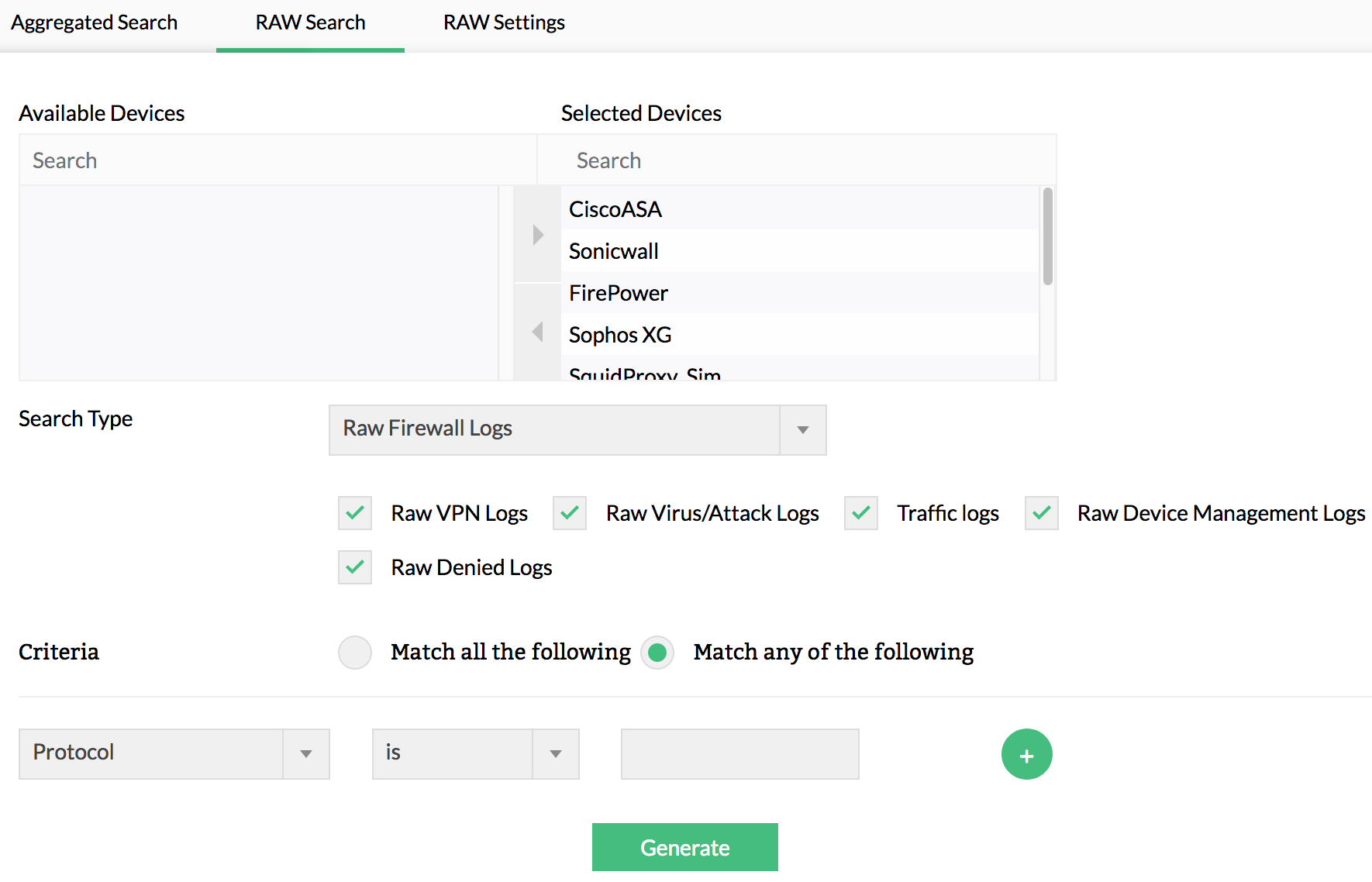
Refer Raw log search report page for more information on raw log search reports.
Saving the search results as reports
Firewall Analyzer has a beneficial feature for forensic investigation in that you can search logs and save the results as reports. This will help you avoid making repeated searches, and circumvents the risk of forgetting specific search criteria and filters.
The significance of forensic log analysis in cybersecurity
Forensic log analysis is an indispensable component of modern cybersecurity strategies. It enables organizations to detect and respond to security incidents, understand the root cause of breaches, and comply with regulatory requirements. However, the process comes with significant challenges, including the volume of data, log integrity, and the need for real-time analysis.
ManageEngine Firewall Analyzer addresses these challenges with a comprehensive set of features designed to make forensic log analysis more efficient and effective. From secure log archiving to powerful search capabilities, Firewall Analyzer provides everything you need to enhance your organization's security posture through detailed and accurate forensic log analysis.
With all these features and more, Firewall Analyzer has everything you need in a forensic log analysis tool. Claim your 30-day free trial.
Featured links
Firewall Rule Management
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
Firewall Compliance Management
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Firewall Log Management
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
Real-time Bandwidth Monitoring
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Firewall Alerts
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
Manage Firewall Service
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.
Thank you for your feedback!