Firewall Analysis: Analyze Security, Traffic Logs and Configurations, Policies, Rules
Firewall Analysis can be split broadly in to two categories. One is, the operation of the Firewall captured in security and event logs. The other is, the administration of Firewall captured in configurations, policies and rules files.
Analyze Security and Traffic Logs
Firewall log analysis provides insight in to the security threats and traffic behavior.
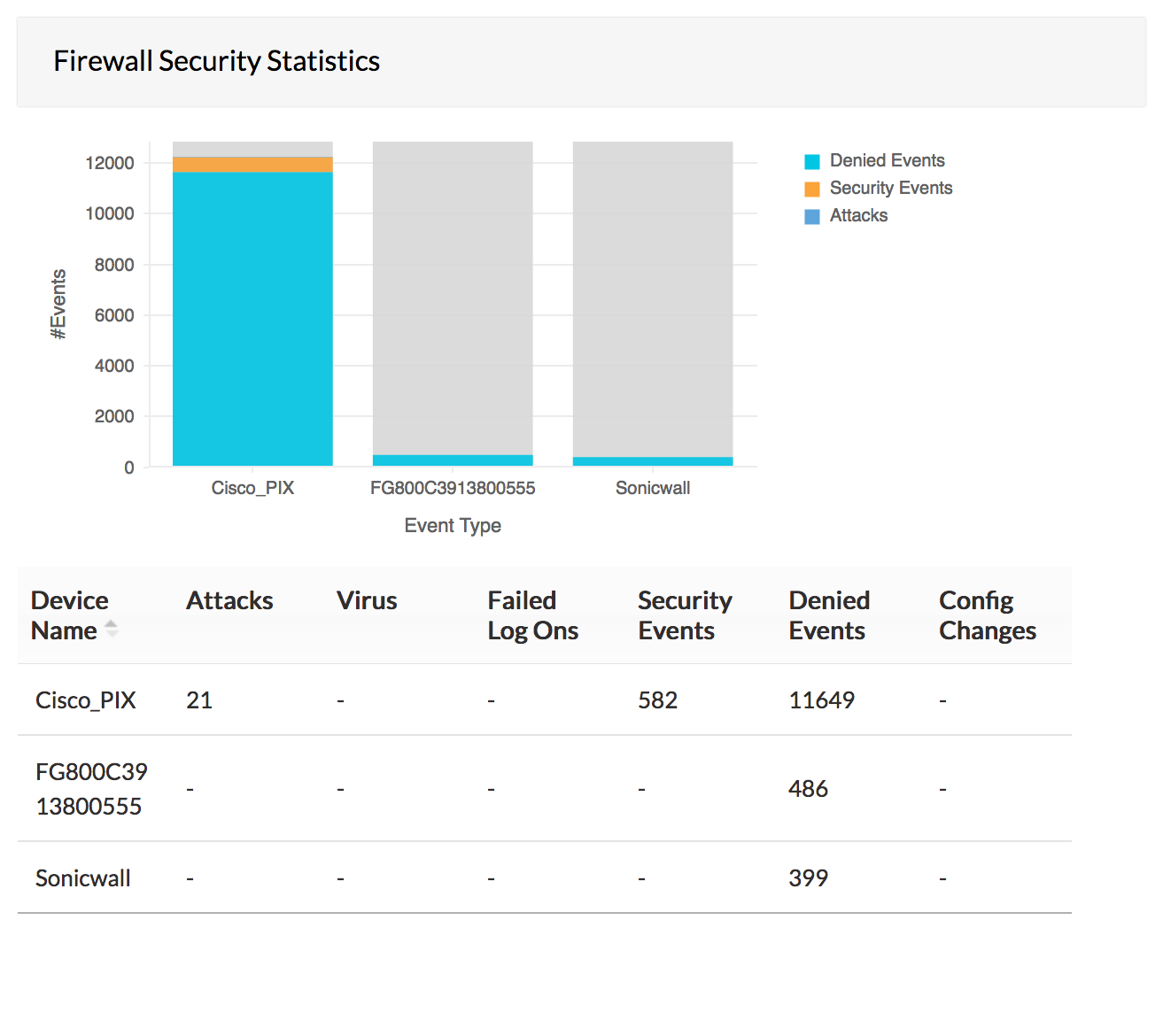
In depth analysis of the firewall security logs provides critical network intelligence about attempts to breach security and attacks like virus, trojan, denial of service, etc. These network security threats pose a grave risk to the critical resources in the network. From the firewall security log reports security administrators can perform security log analysis, visualize network threat scenario and plan their strategy to protect from those threats.
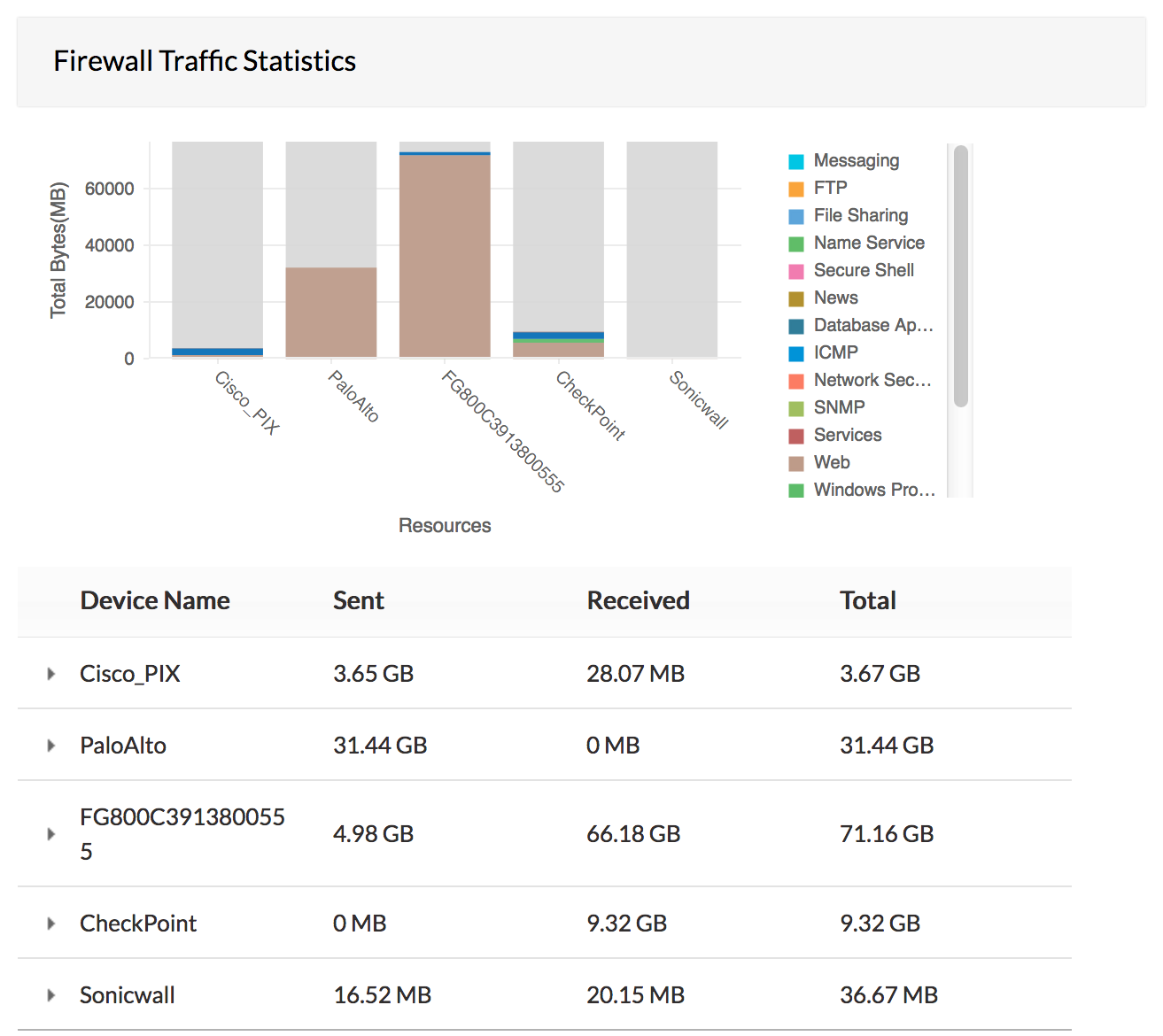
Analysis of traffic logs provides valuable information about bandwidth usage, employee internet usage, bandwidth guzzling web sites, and interface wise traffic. From the traffic log reports of firewall analysis, network/security administrators will be to monitor fair usage of the bandwidth for business purposes and plan for the future requirements of bandwidth capacity.
Firewall Analyzer acts as an extensive firewall log analyzer, collects syslog generated by firewalls and generates reports which enables security admininstrators to perform firewall logs analysis.
Analyze Firewall Configurations, Policies, and Rules
Firewall configuration analysis provides information to optimize the performance of firewalls.
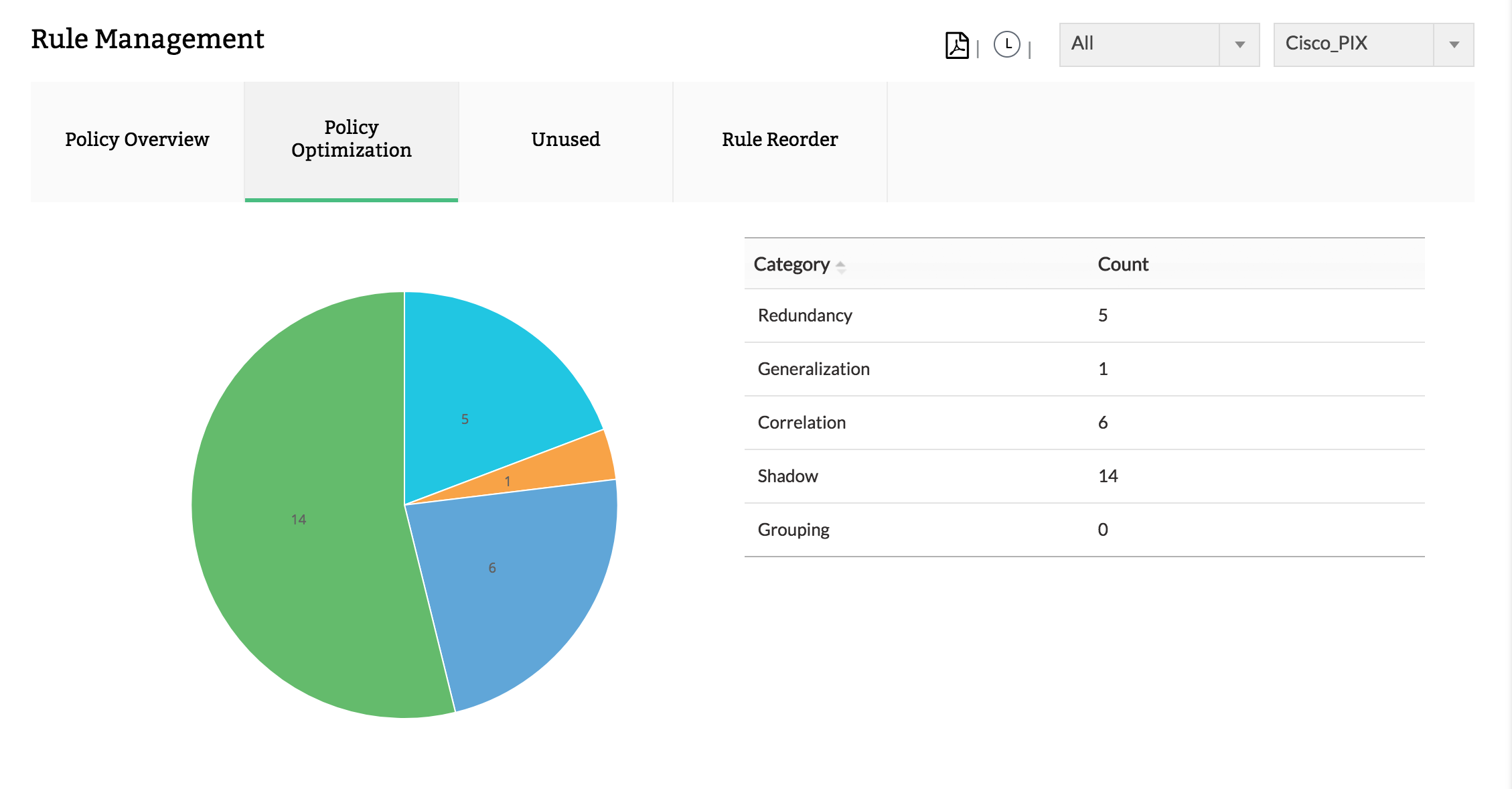
Deeper analysis of the policies/rules provides information about the frequency of usage or non-usage of the rules. This information can be used by the security / network administrators to find out the adequacy of the rules, requirement of a particular rule, rule usage resulting in security policy implementation. From the rules / policy reports of firewall analysis, the administrator can decide whether to delete unused rules, modify the moderately used rules and add new rules to meet the security policy requirements.
Analysis of firewall configuration provides information about wrong configurations, sub-optimal configurations, etc. With this information, the administrator will be able to correct / fine tune the configurations for optimum firewall performance.
Thus, this firewall log analysis tool offers CLI-based configuration monitoring and it supports Telnet, SSH, and SCP protocol for security and traffic log analysis. Firewall Analyzer tool also helps security admins track policy changes, optimize firewall performance and maintain compliance standards.
Featured links
Firewall Reports
Get a slew of security and traffic reports to asses the network security posture. Analyze the reports and take measures to prevent future security incidents. Monitor the Internet usage of enterprise users.
Firewall Compliance Management
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Firewall Rule Management
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
Real-time Bandwidth Monitoring
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Firewall Alerts
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
Manage Firewall Service
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.
Thank you for your feedback!