Firewall Analyzer analyzes proxy server logs and provides insightful reports
Firewall Analyzer (Proxy Log Analyzer) collects and archives the proxy server logs, analyzes them, and generates useful corporate internet access information reports. Proxy server reports provide network security administrators and managed security service providers (MSSP) with important insight into the efficiency of their corporate Internet usage. As a proxy log analysis tool, Firewall Analyzer supports BlueCoat, Microsoft ISA, Squid proxy logs and servers. Firewall Analyzer provides the following reports based on proxy log analysis:
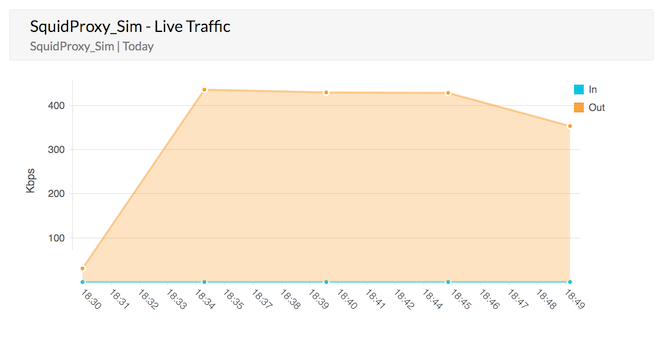
Live Reports
Firewall Analyzer presents a instant view of bandwidth usage through the proxy server. With the Live Reports, bandwidth consumption for various periods like day, week, month, and year is available in graphical format. Using these reports administrators can monitor for sudden spike in traffic and conduct forensic or root-cause analysis and detect network anomalies.
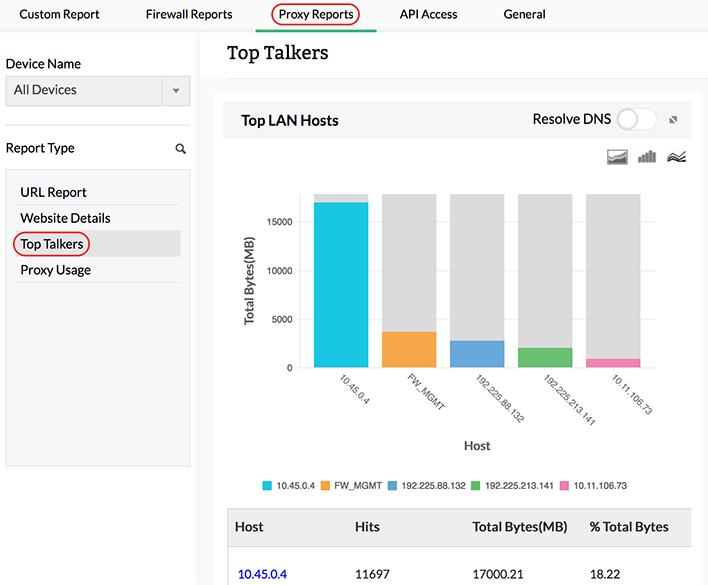
Top Talkers Report
You will be able to find out which of the hosts, users are more active in the intranet, Internet. If there is any abnormality you can investigate and find out the cause using the Top Talkers report. You can also obtain the details of the conversations that have taken place between the source and destination and further drill down to view the top web sites visited, URLs, and more.
Request for a personalized demo
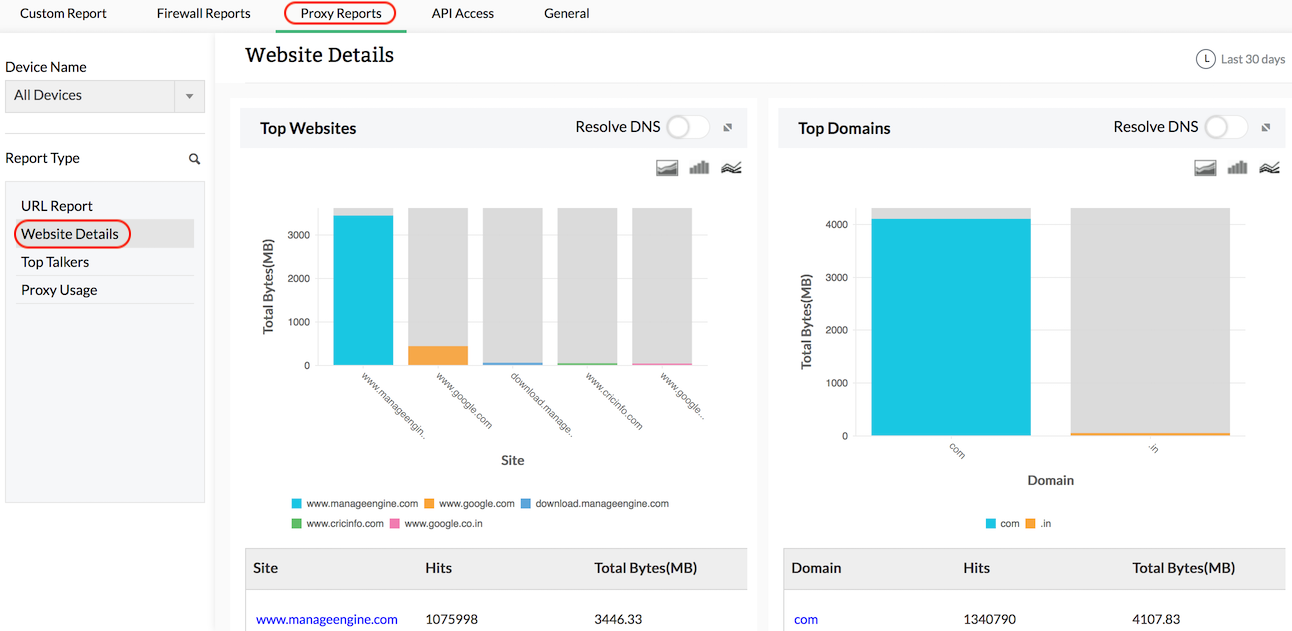
Website Details Report
You will be able to find out which are the websites, domains, and web pages most visited from your company. With this information, you can judge the purpose of Internet access of your company employees. Get the pattern of websites accessed by your employees. Another important aspect is the users denied for Internet access at the proxy server level and the type of requests denied. From this you can have intelligence about the rogue user trying to bypass the proxy server and kind of access requests.
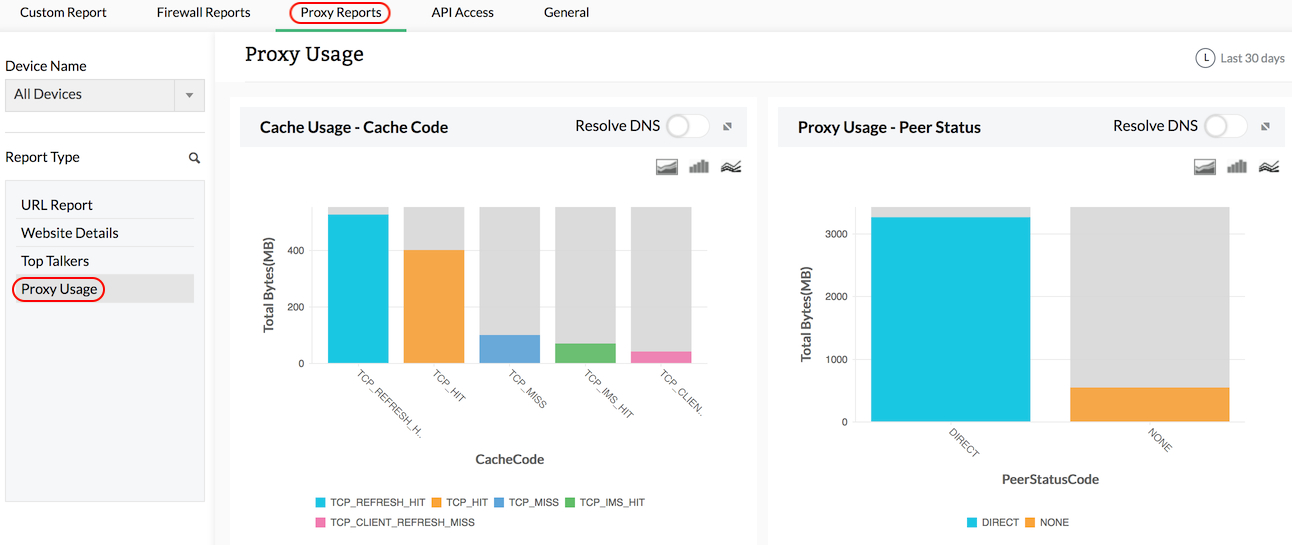
Proxy Usage Report
If you want to get the details of the usage of the proxy server, you will be interested in the following code wise usage reports such as, cache code, peer status code, and HTTP status code. You can also get a report on HTTP operation wise usage. With this information, you can fine tune the proxy server to control and channelize the company's Internet traffic.
URL Categories Reports
You can monitor the category of websites that are allowed and denied. This will be helpful to con troll the web traffic of your company. You can add the relevant category of websites to the allowed list and the irrelevant category of web sites to the denied list.
With proxy server reports, you can have a better control over the company's web traffic.
Featured links
Firewall Rule Management
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
Firewall Compliance Management
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Firewall Log Management
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
Real-time Bandwidth Monitoring
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Firewall Alerts
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
Manage Firewall Service
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.
Thank you for your feedback!