Firewall Analyzer - Frequently Asked Questions
Why do the intranet reports show zero results?
Verify if intranet's have been configured correctly. If you have specified IP addresses that are not actually behind the firewall, you will get zero values in the reports.
Syslog listener port receiving syslogs from firewall. But receiving firewall non availability alert. Why?
Availability alert triggered based on log processed time. If syslogs are not processed within the schedule time, alert will be triggered. You can see log processing time of specific firewall in Settings > Firewall > Firewall Server > Live Packet Count.
- Check firewall host IP address added under 'Unsupported Logs Received' in device details page. If exist delete from action and check Live Packet Count.
- Restart Firewall Analyzer server once.
- If the issue is still not resolved, send 'Live Packet Count' screenshot, <Firewall Analyzer Home>\logs folder and <Firewall Analyzer Home>\pgsql\data\pg_log logs folder to fwanalyzer-support@zohocorp.com
How to identify the external hosts using intranet settings?
To identify external hosts, you need to configure your intranets in Intranet Settings link of the Settings tab. When configured, all hosts outside your configured intranets will be considered as external hosts. You can see the external hosts in Reports > Firewall Reports > Internet Reports.
How to assign Unassigned Protocols to Protocols and Protocol Groups?
Protocols in Reports
Different firewalls denote the port numbers in the logs in different ways, for example, http:80 can be shown as tcp:80, http:80, etc. Hence, the protocol identifiers are grouped as Protocols and then to Protocol Groups. We found that the reports using Protocols are much usable than the reports based on port numbers. Hence, we show the Protocols in the reports. If all the unassigned protocols assigned to Protocols and Protocol Groups, there would not be any issue of unknown protocols.
Assigning Unassigned Protocols
There will be some unassigned protocols as few protocols are not grouped.
You can view the port details of theunassigned protocols:
Click on the tool icon beside the Firewall name under Devices in the Inventory tab.
In the pop-up window, select Last 6 hours.
It will show all the unassigned protocols along with port numbers.
We have configured the generally used protocols as Groups like Mail, Web, FTP, Telnet, etc. However, you can group the unknown protocols as per your requirement. Configuring Unassigned Protocol will be a one-time activity.
Click on the Unassigned in Protocol Group under Traffic Statistics, which shows all the unknown protocols.
Click on Assign and Select All under Hits and select the Multiple Selection, which lists all the unassigned protocols.
Select the protocols and group it under Protocol Group and assign the appropriate protocol.
If you do not find a Protocol Group, click on the '+' sign to add a new Protocol Group.
Note:Once you assign the protocols, the reports will show the assigned protocols and the newly assigned protocols under their appropriate protocol group only from the assigned time. You will see the unassigned protocols in the reports generated earlier to the assigned time.
If you find that the reports based on ports, please assign specific protocols to the corresponding port numbers and create a custom report to view the details.
Checking the port numbers
Check the port number by clicking on Settings > Protocol Groups > Click on the drop down menu against 'View by Group'and select the appropriate protocol. This will show the protocol identifiers with port numbers.
You can also check the raw log in the folder <Firewall Analyzer Home>serverdefaultarchive<DNS(or)IP addressHot> folder to know the protocol type and port numbers (You can open the file using a notepad).
The Active Directory has been configured, but the user name is not shown in the reports. How to tackle this?
- Connect to the Active Directory server
- Open event viewer
- Check Event ID 672 or 4768.
- If the Event ID is not present, troubleshoot in your active directory server to trigger above event IDs
- If the issue not reolved even after entering the event ID in the Active directory please contact the Firewall Analyzer Support team: fwanalyzer-support@manageengine.com
How to tackle DHCP server dynamic IP changes using periodic updates?
- Click on the Import log button
- Choose remote/local host
- Select schedule option
- Enter the Time Interval (Scheduling time in Minutes) after which Firewall Analyzer should retrieve new log files.
- Click on browse and select the appropriate file
- Select the Change filename dynamically option, if you want to import the log files which change their names dynamically.
- Select the date and/or time file name pattern from the Filename pattern: combo box or add a new pattern
- Finally click on "Import" to import the log file into the database.
PaloAlto, SonicWall firewall is accessible from Firewall Analyzer using SSH credentials, but device rule failed. Why?
Firewall Analyzer uses SCP configuration export command to fetch configuration from firewall. Choose SCP protocol and try again.
If device rule fails, provide inbound access for scp port (tcp/22) in Firewall Analyzer server and try.
If it still fails, take screenshot of firewall CLI and send it to fwanalyzer-support@manageengine.com along with <Firewall Analyzer Home>/logs folder.
How to get notification mail for configuration changes?
Add Device Rule > Select Report > Generate Change Management Report check box to generate configuration change management report.
Under the Notification Options, enter the Email address of the user(s), who need to be informed via Email when any configuration change happens.
How to troubleshoot if device rule failed?
- Connect firewall CLI using putty from Firewall Analyzer server.
- Check whether the IP address shown in putty is the same in Firewall Analyzer IP address field.
- Enter the credentials and login to the device.
- Compare and verify the credential with Firewall Analyzer credential page.
- Check and provide exact 'Prompt' available in CLI.
- Provide 'Banner Prompt', 'Banner Input' and 'Enable Prompt' if exists.
- Save once again.
- If it still fails, take a screenshot of firewall CLI and send it to fwanalyzer-support@manageengine.com along with <Firewall Analyzer Home>\logs folder.
How to claim a failed port?
Check if any other application or service is using that port. If Yes, kill the process and restart the product. Ensure that the killed process does not affect the machine.
How to discover firewall, if syslogs shown in Live Packet Count but device not added?
- Go to Settings > Firewall > Admin > Device Details.
- Check under unsupported device list.
- If the device added as unsupported device, convey us to fwanalyzer-support@manageengine.com.
Firewall forwards syslogs to Firewall Analyzer. But the server didn't receive syslogs. Why?
Windows:
- Install packet capture tool (e.g., WireShark) and check server receiving syslogs in the configured port. If yes send pcap file to us.
- Disable the windows firewall.
- In Windows firewall, add inbound rule for forwarding port even though its disabled.
- Check any NIC card failure issue.
Linux:
- Execute tcpdump command and confirm that syslog is reaching Firewall analyzer.
Command tcpdump -i <interface> host <firewall IP address> port <UDP port>
- Send the tcpdump to Firewall Analyzer support.
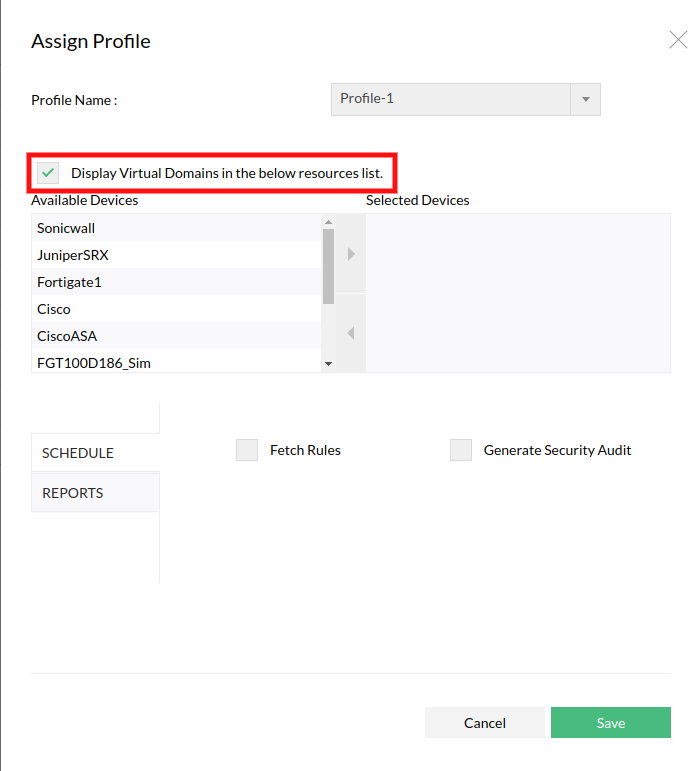
How to add device rule for VDOM devices?
If you want to fetch the rules/configurations from the individual virtual firewalls (virtual domain) separately, select the option 'Display Virtual Domains in the below resources list.' in Assign Profile page. It lists both the virtual firewalls (virtual domain) and the physical devices in the Select Device drop down list.
Thank you for your feedback!