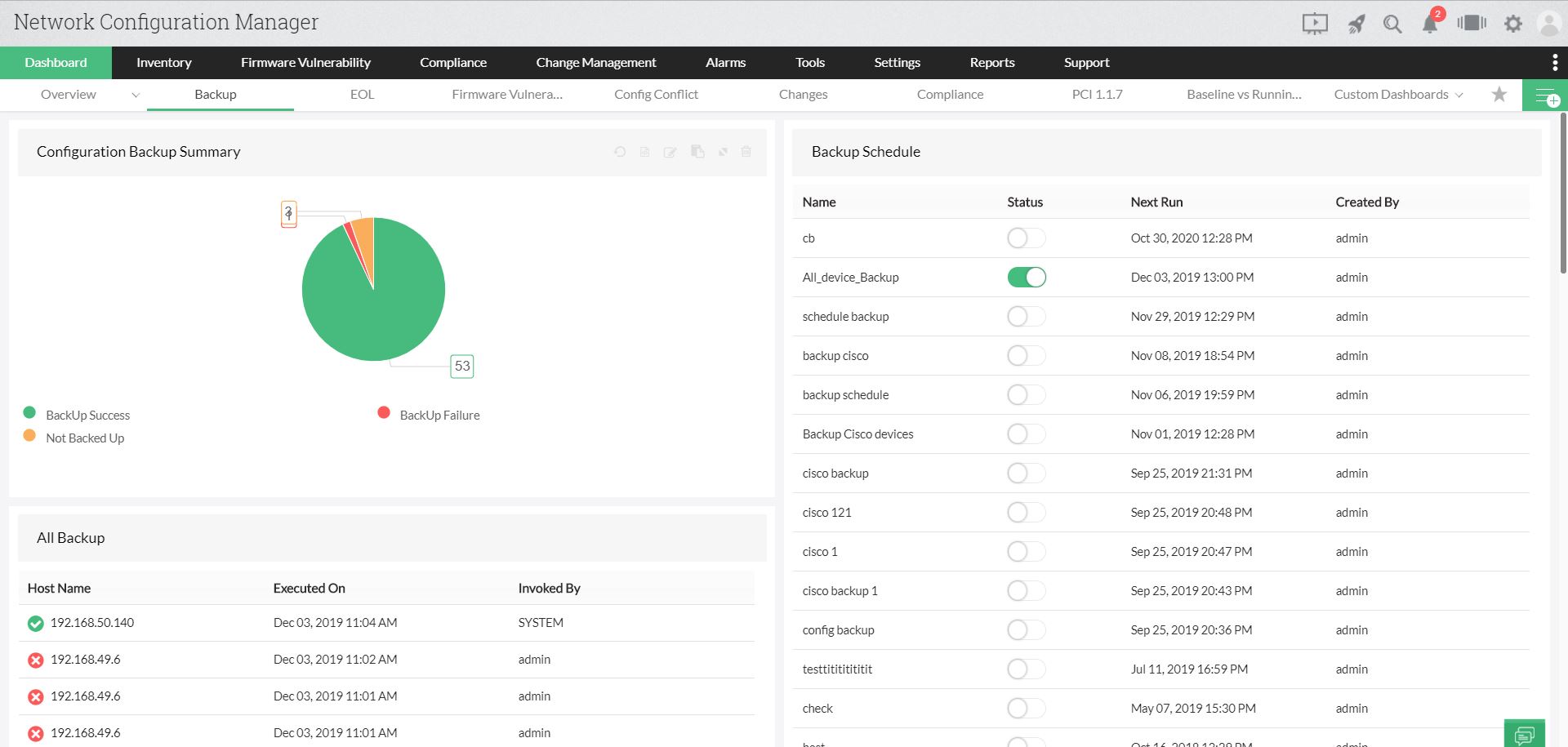
Network configuration backup
Network Configuration Manager helps back up network configurations through automated, scheduled, and one-click backup methods. In the occurrence of a network device downtime, the backed-up configuration file can be uploaded to the device to bring it back to life, and network downtime can be reduced drastically.
Role-based access control
With Network Configuration Manager's role-based access control (RBAC), you can restrict user access to network configurations and resources. In RBAC, users are assigned roles depending on the resources they need access to. All other parts of the network are rendered inaccessible to them, ensuring no unauthorized accesses or changes are made to network resources.
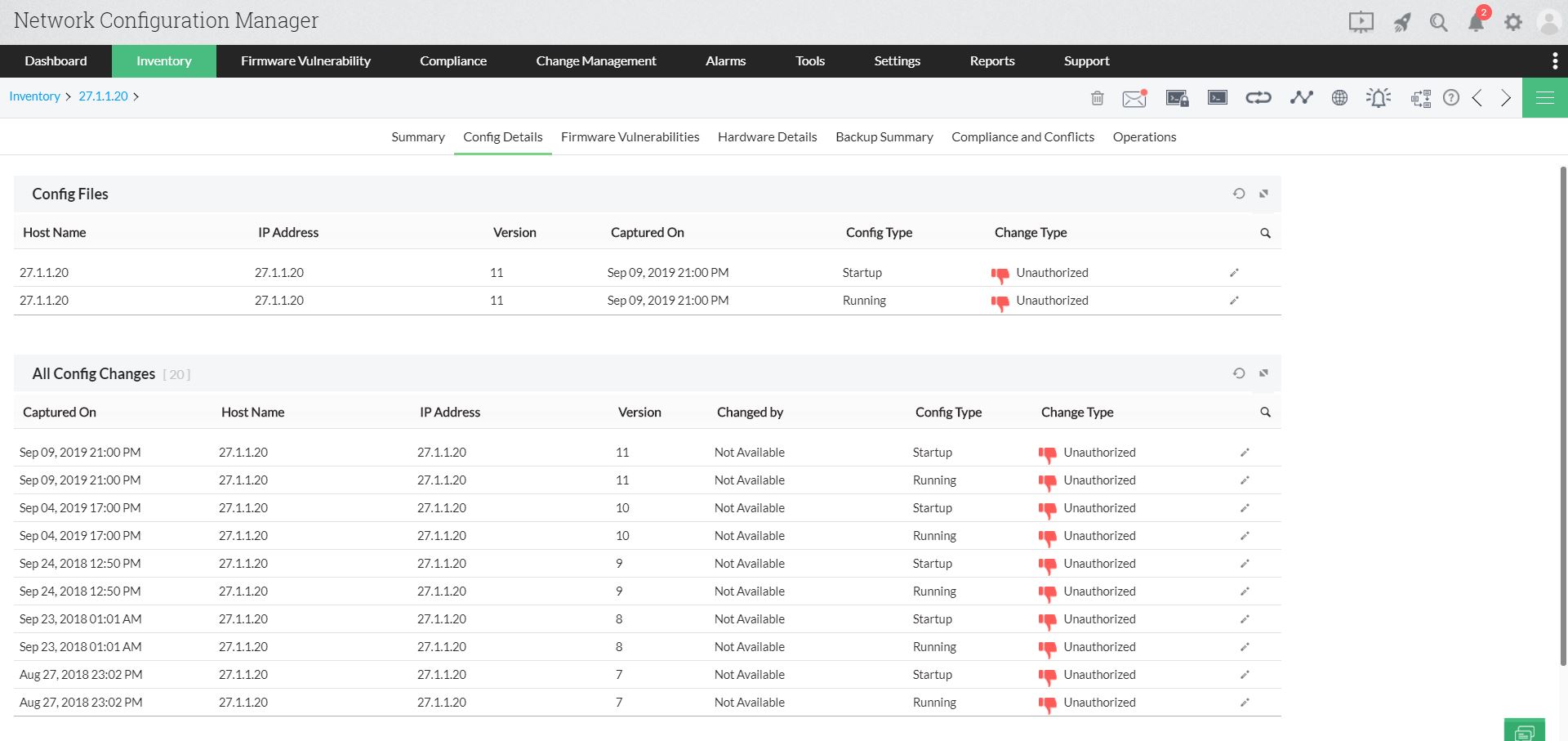
Configuration change tracking
With Network Configuration Manager, track what and when changes were made to configurations, and get notified immediately via email. You can also audit who made the change, and discover errors in the configurations by comparing the changes with previous configurations using Diff-View.
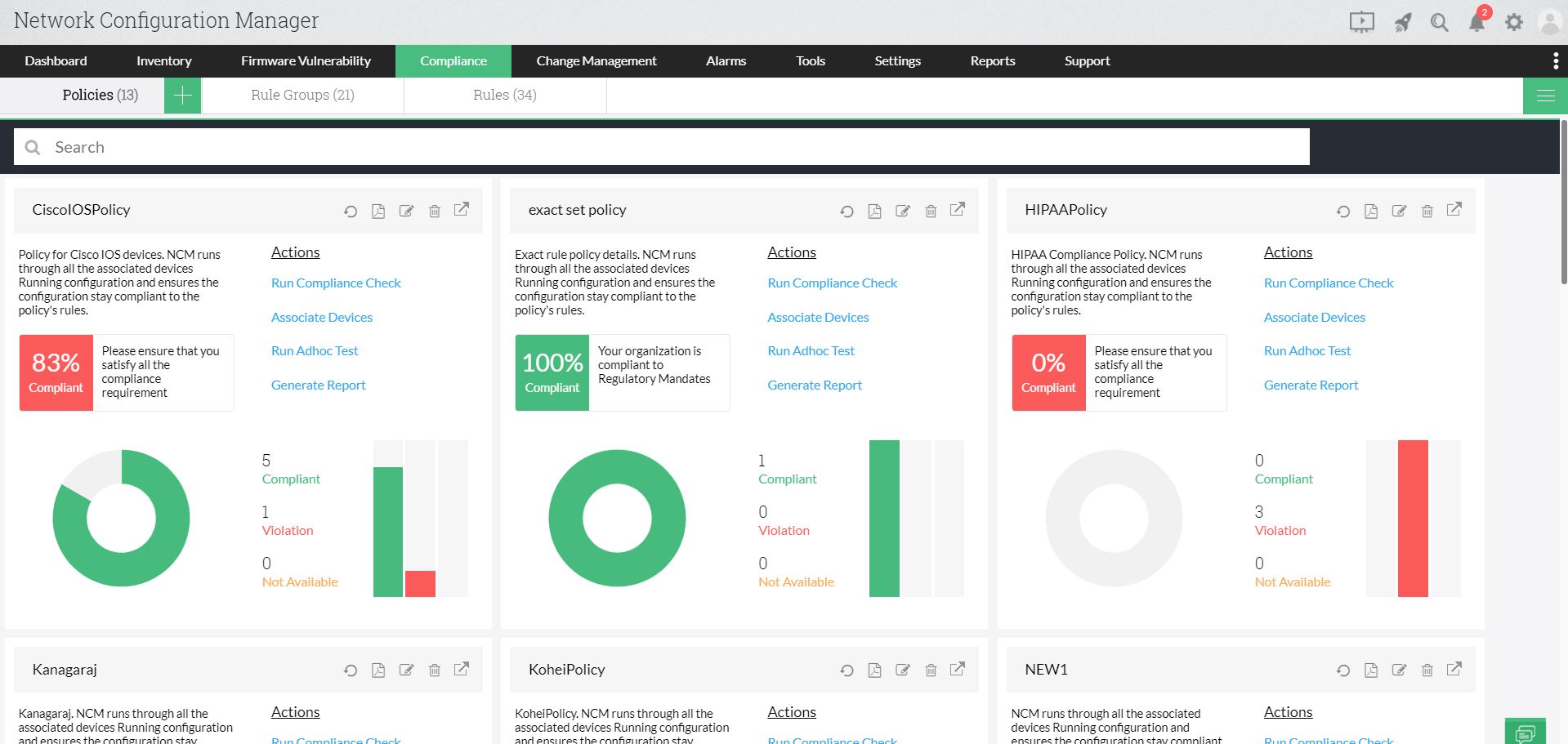
Compliance auditing
Network Configuration Manager helps you comply with CIS, SOX, HIPAA, and PCI DSS mandates, and helps you create custom policies. You can also generate reports for all rules, compliant rules, or violated rules, and enable the option to receive notifications after the compliance check when there is a policy violation.
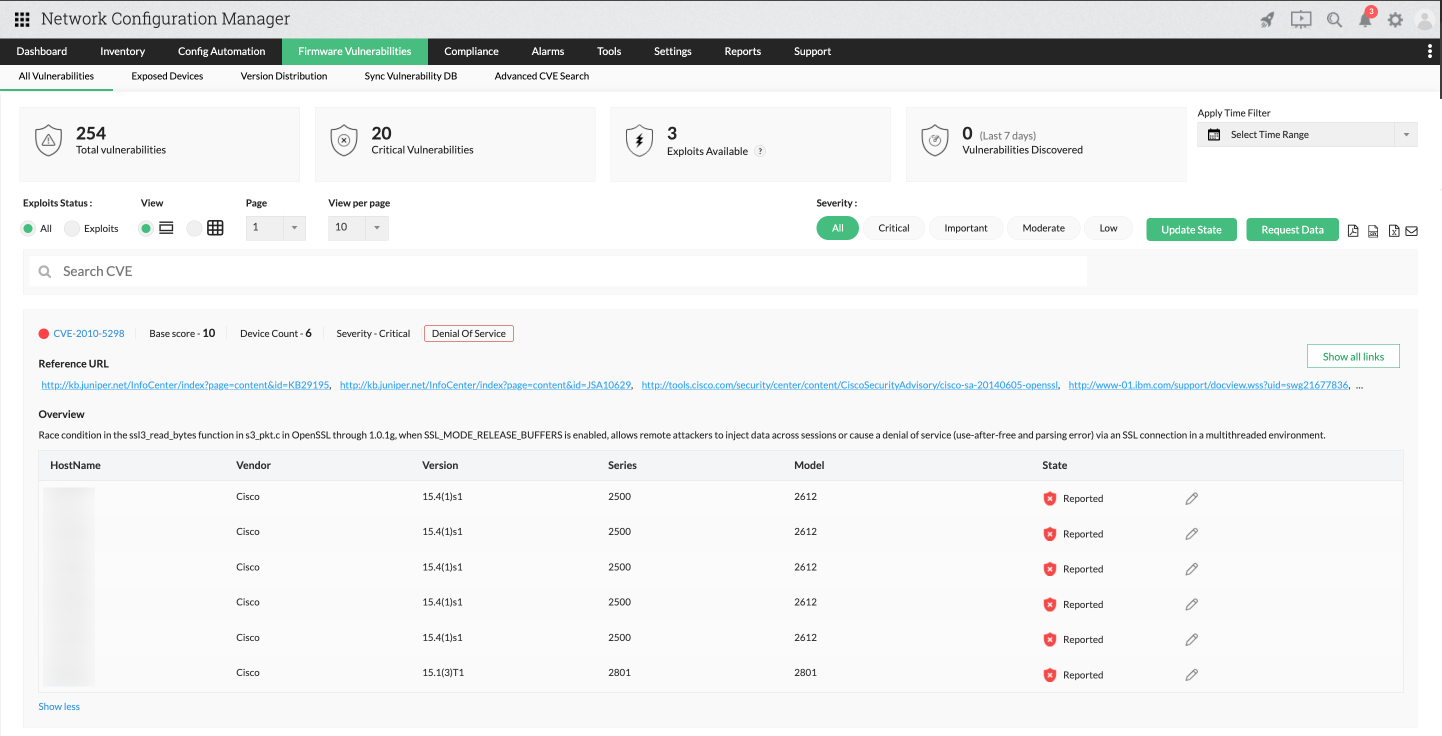
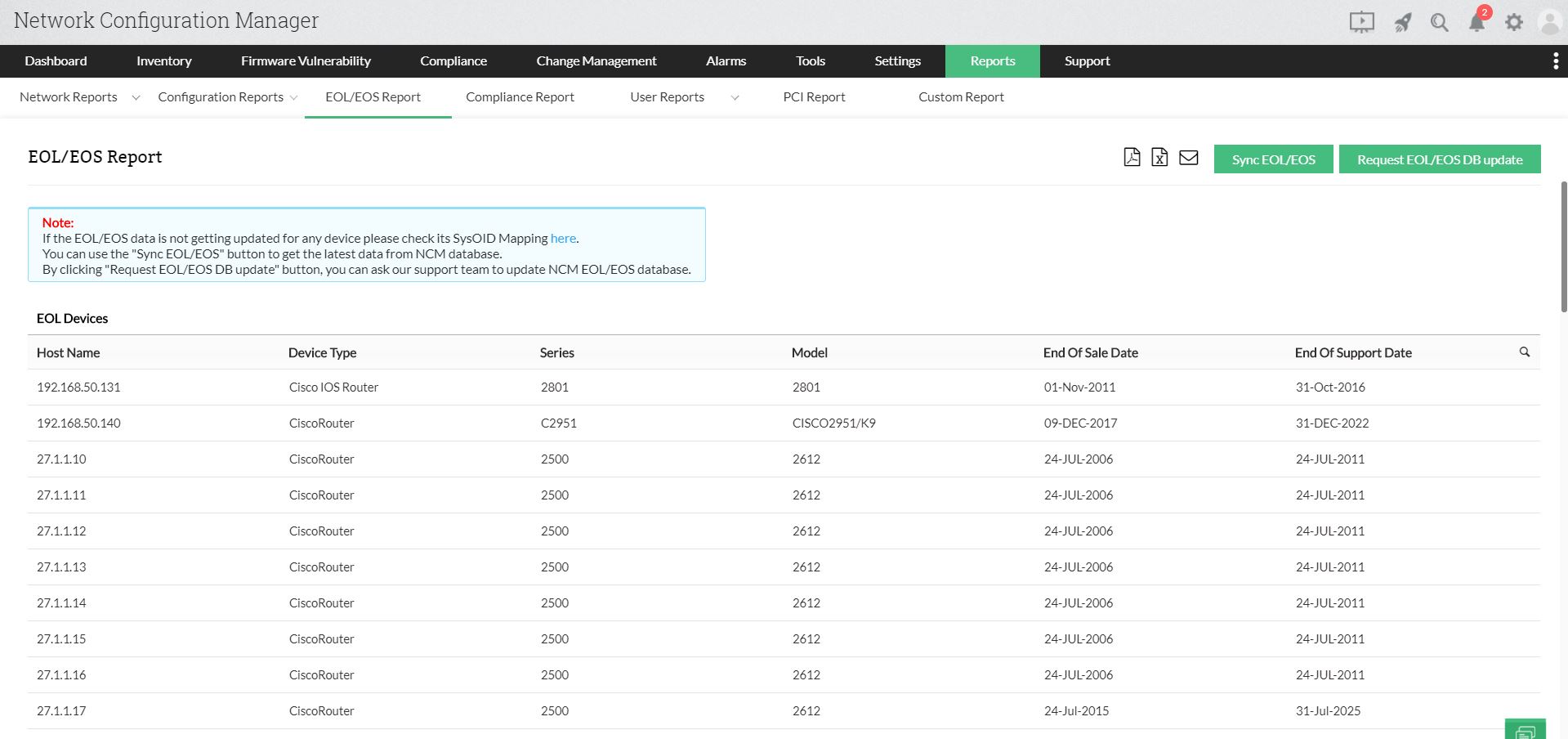
Firmware vulnerability management
With Network Configuration Manager, you can now view all the vulnerabilities in your network devices and take action. Network Configuration Manager fetches vulnerability data from the National Institute of Standards and Technology (NIST) as well as other vendors, and correlates it with the network devices present in your network environment. It also provides a suitable patch for vulnerability to enhance security.
Configuration change automation
By executing automated command scripts known as configlets, you can make changes in configurations, and push configurations across multiple network devices to save time and manual effort. On top of that, you can upload configurations to multiple network devices at once.