A Microsoft Azure logging tool like Log360 helps manage Azure logs from all the devices and applications in your Azure cloud infrastructure, like virtual machines (VMs) and containers, and helps detect performance bottlenecks. Capturing VM activity logs is crucial to spot the security incidents accurately. Log360 helps reduce cloud costs by identifying unused resources and right-sizing possibilities in your Azure cloud.
Log360 securely collects logs from the Azure environment with the help of Azure Monitor Logs API. The solution's REST API client request includes a query that's run against Azure Monitor to determine what data to retrieve from the Azure workspace. Once Log360 is deployed in your IT environment, the solution collects, analyzes, and securely stores Azure logs to enhance network and web security regardless of logs from a multitude of devices in your Azure cloud.
Get a clear picture of what's going on in your Azure environment by correlating the sheer volume of Azure logs across your Azure cloud infrastructure. Log360's event correlation module effortlessly correlates critical events with other events happening on the Azure resources. It also helps create a new Azure storage account for all the Azure storage services and make it accessible from anywhere via HTTP and HTTPS.
You can track all user activities and changes made to network security groups, virtual networks, DNS zones, virtual machines, databases, and storage accounts on your Microsoft Azure cloud environment with the help of Log360. Audit activities across your Azure cloud, hybrid Active Directory, and on-premises Active Directory, and monitor Windows logons, file accesses, and much more.
ManageEngine Log360 helps with load balancing traffic to specific endpoints. In a single console, it shows all created, modified, and deleted endpoints based on the data from Traffic Manager. Moreover, the solution allows you to manage permission changes and configuration changes based on Azure Traffic Manager.
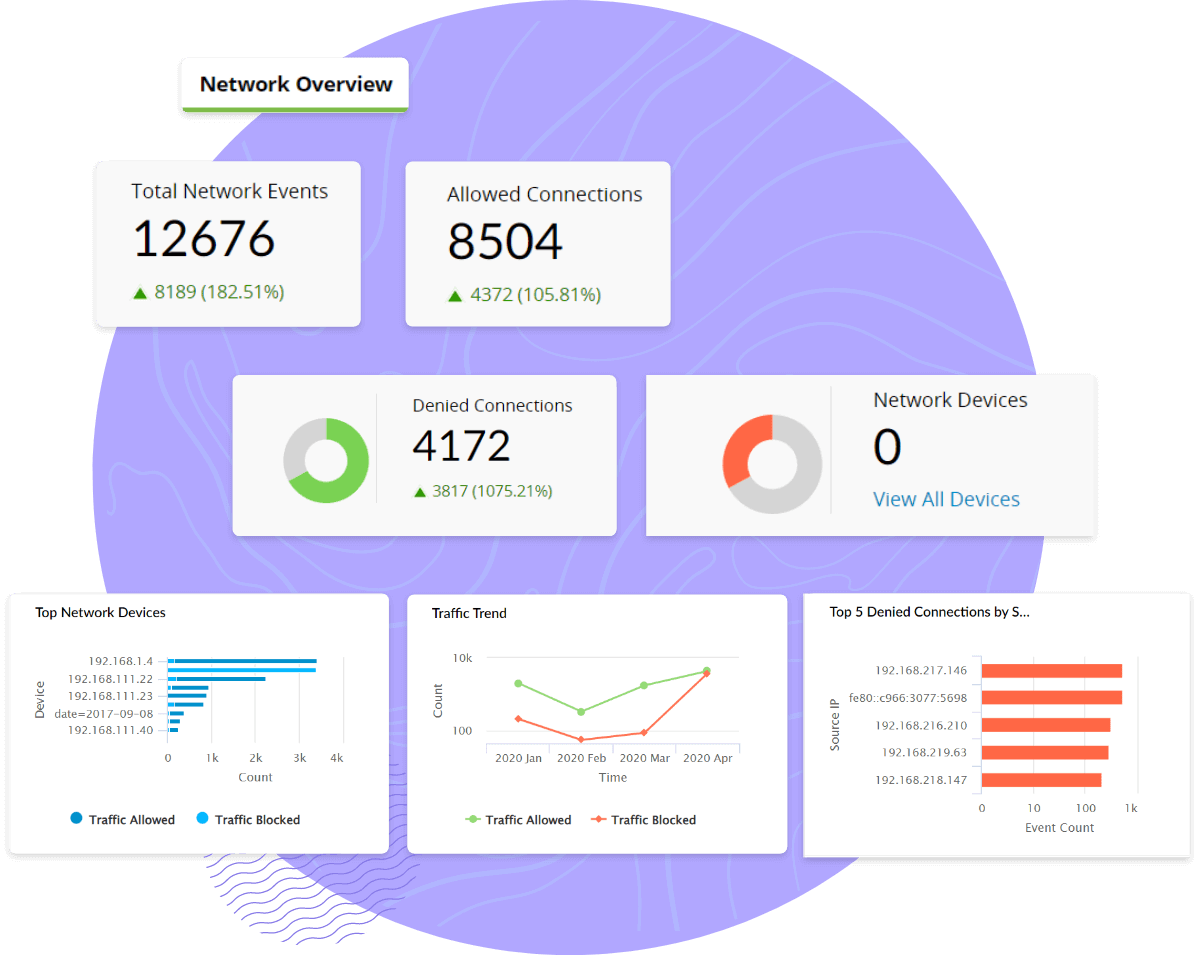
As a security professional, you're often required to perform log forensic analysis, which is a mundane and time-consuming task. Log360 helps visualize Microsoft Azure logs in a unified environment with intuitive charts, graphs, and reports to identify the root cause of an issue. Our Azure monitoring tool, Log360, helps analyze all applications deployed on the Azure cloud environment to check for performance, maximize the availability, reliability, and consumption. Log360's SIEM capability tracks all changes and identifies malicious activities happening on Azure AD logs, files, and folders residing in Azure. Log360's filter and search module helps drill down Azure AD activity logs to detect suspicious activity and act on it.
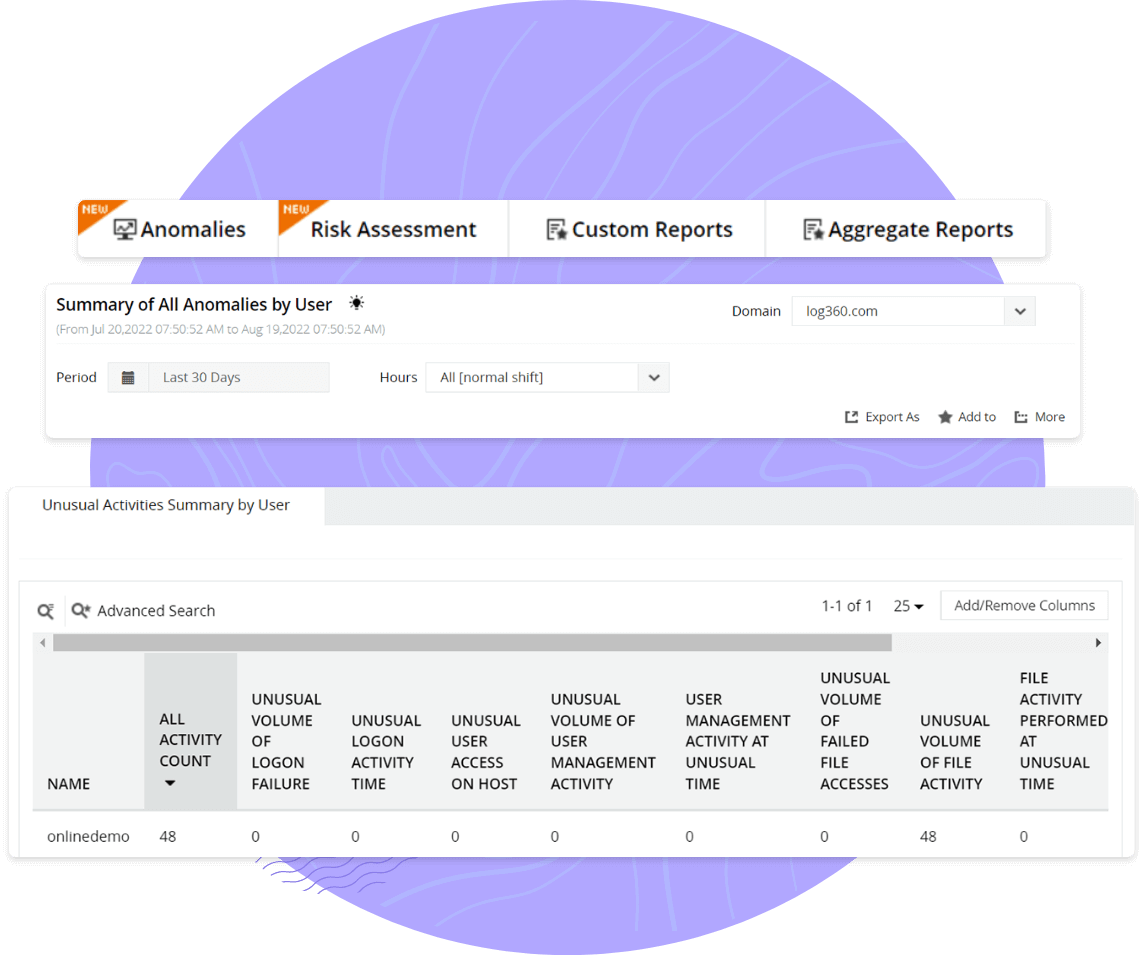
Get notified about critical changes made to AD objects, including users, computers, groups, OUs, security principals, and GPOs. It's vital to ensure Azure servers, Azure cloud applications, and Azure resources are running smoothly to reduce down time and performance bottlenecks. Log360 helps secure sensitive data in the Azure cloud and swiftly detects data exfiltration attempts.
Monitor changes made to your Azure AD environment and tackle privilege escalations. For instance, if a user accesses the system after business hours, it could be considered anomalous behavior. This is why the risk score of a particular user increases along with the corresponding severity level. Categorizing risk scores as Critical, Trouble, and Attention helps you prioritize events and swiftly take remedial action as needed.
Log360's advanced threat analytics capability blocks malicious domains, IPs, and URLs intruded to your network. Configure alert profiles to receive instant alerts when a malicious source intrudes on your network and performs suspicious user actions in your Azure AD. Based on the severity of the event, alerts are categorized and prioritized so that you can swiftly act on critical events to prevent security breaches.
Centralize Azure log collection to gain insights into configuration changes, server attacks, and security errors. Monitor changes made to your network security group, virtual machines, and virtual networks, and respond to security threats instantly. Archive and customize Azure logs for a specific time period based on your organization's needs or as per IT regulatory mandates.
Detect security threats with pinpoint accuracy by correlating your Azure logs with rest of your network logs. The solution's threat analytics capabilities help identify and block malicious IPs and URLs.
Defend against insider threats, account compromise, and data exfiltration. Spot anomalous user behavior with Log360's UEBA module.
The solution's advanced threat analytics capability accurately spots malicious actors in the Azure network and identifies their techniques and tactics to alleviate the risk of a data breach.
Automated incident response workflows with security orchestration, automation, and response (SOAR) are triggered to ensure a swift response to security threats and automatically assign tickets to security admins.
Demonstrate compliance with audit-ready reports for HIPAA, the PCI DSS, the GDPR, and more. Gain deep insights into security incidents, improve investigations, and resolve issues quickly.
Azure logs, generated by Microsoft's cloud computing platform, Microsoft Azure, are essential for monitoring, troubleshooting, and auditing the activities and performance of Azure resources and applications. Azure provides several types of logs, including activity, diagnostics, security, network, and storage, to help you gain insights into your Azure environment.
Log360 can monitor a wide range of Azure resources and environments.
This comprehensive monitoring helps maintain the security and performance of Azure resources and applications.
Log360 facilitates centralized Azure log collection for insights into configuration changes, security incidents, and more. It helps demonstrate compliance with audit-ready reports for various regulations such as HIPAA, the PCI DSS, and the GDPR, offering deep insights into security incidents and improving investigation processes.
Manual services like Azure Log Analysis, Azure Monitor, and a dedicated SIEM solution like Log360 serve different purposes and offer varied levels of capabilities for analyzing Azure logs.
| Services | Pros | Cons |
|---|---|---|
| Azure Log Analysis and Azure Monitor |
|
|
| ManageEngine Log360 |
|
|
Manual services like Azure Log Analysis and Azure Monitor are well-suited for organizations with primarily Azure-based environments and simpler log analysis needs. They offer ease of integration and basic log analysis capabilities for Azure resources.
On the other hand, SIEM solutions like Log360 are ideal for organizations with more complex environments; a mix of Azure and non-Azure resources; and a need for advanced log analysis, threat detection, and comprehensive security monitoring. They provide a broader and more sophisticated set of features but may come at an additional cost.
Ultimately, the choice of service should be made based on your specific requirements and the scale and complexity of your IT environment.