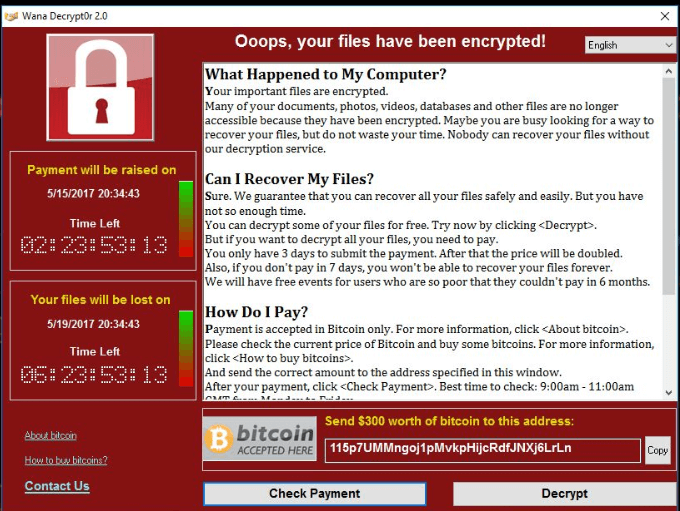
A ransomware attack is a sophisticated attack technique where the hacker takes control of a computer, locks its data, and demands a ransom from the victim promising to restore access to the data upon payment. The payment is usually demanded in the form of cryptocurrencies like bitcoin to hide the identity and location of the attacker.
Ransomware typically enters a network through a phishing email and spreads laterally throughout the network by installing malicious software.
Once ransomware finds its way into a system, it encrypts the data in that system. The attack uses simple encryption algorithms using the same encryption and decryption key. However, the strongest ransomware uses public/private key cryptography. By using separate keys for encryption and decryption, the user will not be able to recover the files unless the attacker provides it once the ransom is paid.
Once attackers gain access to the system, the malware locks access to the system and starts encrypting files. Once this happens, no security software or system restore can return them, unless the victim pays the ransom in exchange for the decryption key. Even if victims do pay up, there’s no guarantee that cybercriminals will give those files back.
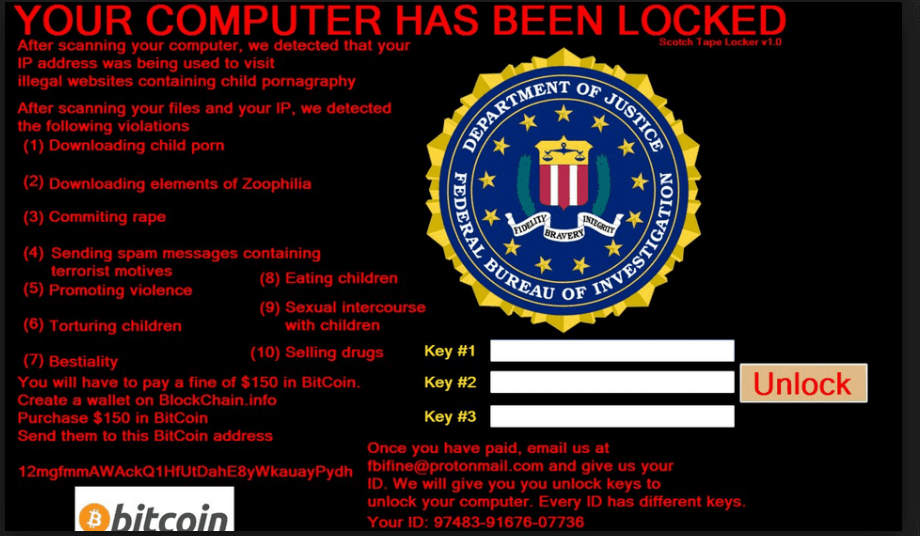
Upon starting the computer, a window will appear, often accompanied by an official-looking FBI or US Department of Justice seal saying illegal activity has been detected on your computer and that your system will remain unstable unless you pay the amount that’s demanded in the notice.
Disconnect: This is done to avoid the spread of the infection to the rest of the network. Identifying and disconnecting the infected device from the internet and any other devices is necessary for the safety of the company's network.
Cleanup: Some instances of ransomware can be removed by using antivirus or anti-malware software.
Recover data using backups: By reinstalling the operating system and restoring files from your backups, you’ll be back in business with your most important files again.
Report the crime: Contact law enforcement to report that you have been the victim of a ransomware attack. Knowing more about victims and their experiences with ransomware will help law enforcement determine who is behind the attack and how they are identifying or targeting victims.
The process of removing a ransomware infection depends on the type of ransomware that has infected the system. In the haste to reclaim access to their network, organizations resort to paying hackers an exorbitant ransom amount. However, the FBI advises against this since it could encourage the cyberthreat groups to carry out more attacks against you or other organizations.
Some measures to remove the ransomware infection include:
Isolating the infected device and identifying the type of ransomware infection
Certain strains of ransomware are designed to encrypt files within a device and infiltrate several devices within the local network without showing signs of infection. For this reason, it's crucial to isolate the affected device by disconnecting it from both wired and wireless connections in the company network and external storage devices. Seeking the help of your IT security team or a third-party cybersecurity expert to review all the systems in the network is a good place to start.
Deploying ransomware decryption tools
Based on the type of ransomware strain, how it propagates, and what types of files it encrypts, the options for removal will vary. A ransomware decryption tool can decrypt your files and data so you can access them again.
Restoring files from data backups
If decryption is ruled out, you can recover data from the latest backups. Once you format the disk and restore the clean backup, the virus is successfully removed from your system. Keeping up to date on recommended patches for the system and antivirus software will help mitigate the chances of malicious software entering your system.
There are several ways to prevent ransomware attacks from occurring.
At best, a ransomware attack may result in a downtime of services while the IT team attempts to restore the system to normalcy. Depending on the severity of the attack and the security measures the organization has in place, the extent of the damages could vary. Different consequences to consider include:
Here is a roundup of the five most popular ransomware exploits that occurred in recent years.
WannaCry first surfaced in 2017 and affected hundreds of thousands of computers in as many as 150 countries, including many systems in the National Health Services (NHS) of England and Scotland.
Petya has been active since 2016 and has infected organizations in Ukraine and Russia before spreading to companies in South America, the US, and Asia. This malware prevents users' access to the entire hard drive by encrypting the master file table (MFT) so that the file system becomes unreadable and Windows won't boot at all.
CryptoLocker was launched in late 2013. It is designed to attack the Windows operating system by encrypting all the files in the system using a public key, which can be decrypted using a unique private key. The virus will display warning screens indicating that the data will be destroyed if users do not pay a ransom to obtain the private key.
Locky is a kind of ransomware that was first released in 2016. The attackers send ransomware-infected emails demanding payment through an invoice in the form of a tainted Microsoft Word document that runs infectious macros. The malware directs the user to a malicious website where it demands the user to pay a heavy ransom to unlock the encrypted files.
TelsaCrypt was first detected in 2015; it targets files of computer games such as game saves, user profiles, recorded replays, etc. Once encrypted, the hackers demand a ransom from the victim within a time limit. When the victim pays the ransom, they can download a decryption key that will restore their files, otherwise they are permanently lost.
Ransomware is simple to create and distribute, and offers cybercriminals an extremely low-risk, high-reward business model for monetizing malware. Combine that with how most companies and people are unprepared to deal with ransomware, and it's no wonder why ransomware has become the second-most pressing cybersecurity issue worldwide.
You will receive weekly cybersecurity news soon!
© 2025 Zoho Corporation Pvt. Ltd. All rights reserved.