
With the COVID-19 pandemic comes an increasing trend in threat groups trying to take advantage of the fear to scare people into becoming victims of phishing activity. In Ottawa, Canada, there is an ongoing phishing scam targeting residents in which emails claiming to be from a local hospital state that the recipient has been in contact with a colleague, friend, or family member who has tested positive for the COVID-19 virus.
In the email, the victim is instructed to print the attached “EmergencyContact.xlsm” file and bring it with them to the nearest testing center.
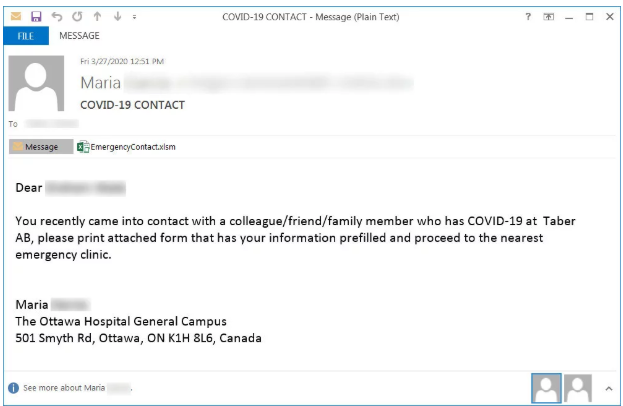
Once the recipient opens the file, they are prompted to Enable Content to view the content of the protected document, which will trigger the infection process. The malicious code is designed to steal cryptocurrency wallets and web browser cookies. It also extracts a list of programs running on the computer, looks for open shares on the network, and gets local IP address information configured on the computer.
During such trying times, it's important to be wary of coronavirus-related emails, exercise caution, and not open attachments.
Attackers usually resort to familiar, effective techniques, like phishing scams, to gain access to email accounts. A smart tool like Exchange Reporter Plus enables organizations to stay ahead of attackers by monitoring for and thwarting email-bound cybersecurity threats. Download a free, 60-day trial of Exchange Reporter Plus today.
Exchange Reporter Plus provides a host of reports that can help you locate suspicious emails, both sent and received, based on keywords in their subject or body. Often times, these malicious emails appear to be valid, tricking users into opening the emails and clicking on links embedded in them, which can cause serious damage.
With Exchange Reporter Plus, you can locate emails based on:
In addition, ManageEngine M365 Manager Plus provides an advanced Microsoft 365 mailbox content search capability that identifies phishing emails by analyzing internet message headers, subjects, attachments, and bodies of emails. With this feature, you can identify senders' email addresses, the platform used by the attackers, and the servers the emails passed through.
Start your free, 30-day trial of M365 Manager Plus today to try out all these features.
© 2025 Zoho Corporation Pvt. Ltd. All rights reserved.
You will receive weekly cybersecurity news soon!