Firewall Security
The frequency of hackers stealing valuable data from organizations worldwide is on the rise. Most businesses transfer critical data over the internet, making the deployment of adequate network security measures a necessity. Having sufficient network security measures in place provides your network infrastructure with a good amount of protection from hackers, malicious users, virus attacks, and data theft.
Network security combines multiple layers of protection to restrict malicious users and allow only authorized users to access the underlying network resources. This is achieved by combining network security devices and excellent network security monitoring tools.
Network security devices come in all shapes and sizes to suit your requirements and deployment. Of all the network security devices, firewalls are the most commonly used and are at the heart of network security in most organizations. Network firewall security acts as the first line of defense between your internal network and the internet.
What is a firewall?
A firewall is a core network security and network perimeter device that inspects the traffic that is entering or leaving your network. It functions on a set of rules, based on which the incoming traffic is allowed or denied access to the network, effectively acting as a filter for network traffic. A firewall can be configured to block specific IP addresses and ports, among other criteria.
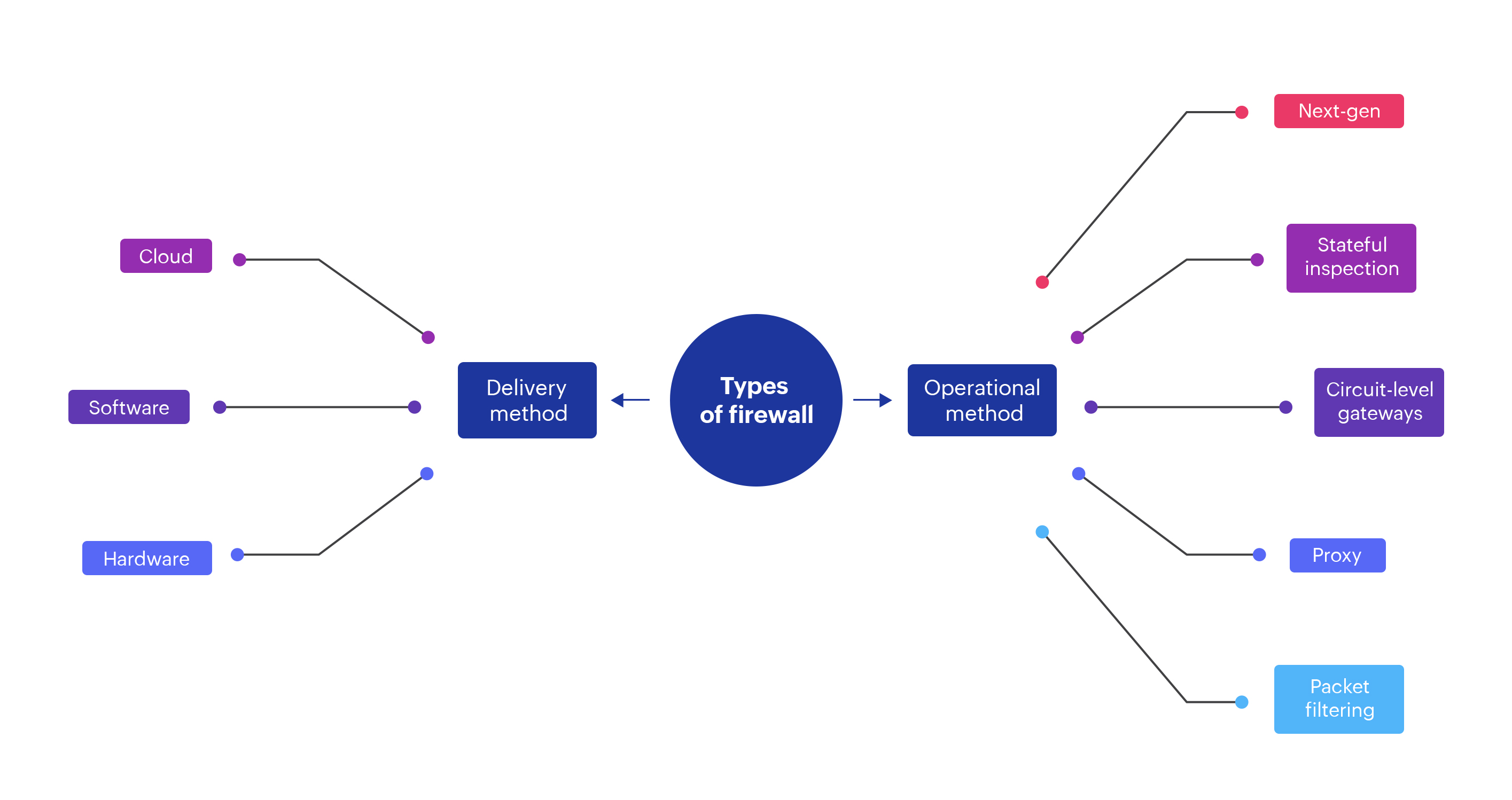
Types of firewalls
Firewall devices can be categorized based on the delivery method and operation method as follows.
Why firewall security is important
Networks without a firewall are vulnerable to incoming traffic that is trying to access your internal files. Harmful or not, it is important to vet the incoming traffic. In addition to maintaining network security, firewalls perform important logging and auditing functions, monitor network traffic, keep a record of events, identify patterns to improve rule sets, and carry out many other tasks.
Firewalls are crucial for:
- Preventing Unauthorized Access: Firewalls act as gatekeepers, preventing unauthorized access to your network, sensitive data, and critical systems.
- Mitigating Cyber Threats: They are instrumental in identifying and blocking various cyber threats, including malware, ransomware, and phishing attempts.
- Ensuring Regulatory Compliance: Firewall security is a key component in maintaining compliance with industry regulations and data protection standards.
- Protecting User Privacy: By filtering and monitoring internet traffic, firewalls contribute to safeguarding user privacy and preventing data breaches.
If you do not have an effective firewall security management tool in place, attackers can exploit the gaps and vulnerabilities in your network to cause serious damage. This includes theft of valuable customer data, personal information, credentials, and more, which impacts the organization in more ways than one, such as damage to customer businesses, a loss of customer trust, and hefty fines due to SLA breaches.
Challenges of managing a firewall
- Choosing the right type of firewall for your network: There are more than one type of firewall and choosing the right type of firewall will lay the foundation for your network security. There are several types of firewalls such as next-gen firewalls, stateful inspection, packet filter etc. The challenge is to understand the pros and cons of each firewall and selecting one that satisfies your network security requirements. For example: Small organizations can be satisfied with a stateful firewall that provides basic level of security. However, a large organization will benefit from a next generation firewall that is capable of advanced threat detections and remediation.
- Assessing the risk of a firewall policy: As businesses grow and expand, the network becomes complex leading to larger rule sets in each firewall. This increases the challenge of analyzing and identifying the risks in each firewall rule. Anomalous, overly permissive, and any-to-any rules can increase network vulnerability. To overcome this, companies have to run frequent rule risk assessment procedures. This involves reviewing file wall rules, running vulnerability assessment, and checking the impact of new rules before they can be applied on a working firewall.
- Maintaining an optimized rule set: Firewall rules decide how network traffic is filtered and allowed to flow into the network. These rules can become outdated overtime creating gaps in security. To maintain an optimized rule set, constant monitoring and rule cleanup are required. This involves frequent rule audits to identify outdated, and redundant rules. By optimizing your rule set, businesses can boost firewall performance, reduce misconfigurations, and enhance network security.
- Keeping up with compliance: Complying with industry-specific mandates greatly contributes to the overall success, security and branding of the organization. This can be challenging because the remands and requirements of the mandate can evolve and businesses must adapt their network security policies accordingly. This process only grows in complexity when the organizations contains multiple firewalls and seeks to comply with a number of mandates. To address this, organizations must deploy a comprehensive compliance management strategy including periodic assessment, and documentation of all firewall configuration changes are mandatory.
How does Firewall Analyzer help?
Firewall Analyzer, a firewall security tool at its core is a centralized log analytics and, firewall security configuration management software. It helps security admins bolster their network firewall security with its array of features. As a trusted security partner, Firewall Analyzer helps you to:
- Deep dive into your firewall configurations: Go beyond surface-level scans. Firewall Analyzer delves into the heart of your firewall, identifying inconsistencies, outdated rules, and vulnerabilities that could be exploited.
- Uncover hidden threats: Log analysis and correlation paint a clear picture of suspicious activity within your network, allowing you to address potential threats before they escalate.
- Stay ahead of vulnerabilities: Proactive vulnerability detection and patching keeps your firewall up-to-date and minimizes the risk of successful exploits.
- Simplify compliance: Pre-built reports and automated checks ensure you meet industry standards, taking the complexity out of compliance.
- Gain complete visibility: Real-time monitoring and alerts keep you constantly informed about your network's security posture, empowering you to react quickly to any threats.
Firewall Analyzer functions as a firewall security software by offering a wealth of network device security management features, including firewall rule management and optimization, firewall configuration management, out-of-the-box compliance reports, and security audit reports. It also offers strict user access control and keeps your network safe from unauthorized changes.
Interested? Download now to try Firewall Analyzer for free for 30 days. Or get in touch with our experts for a personalized demo. Schedule yours here.
Featured links
Thank you for your feedback!