Configuring Cisco Devices - FirePOWER
Configure Logging on FTD via FMC
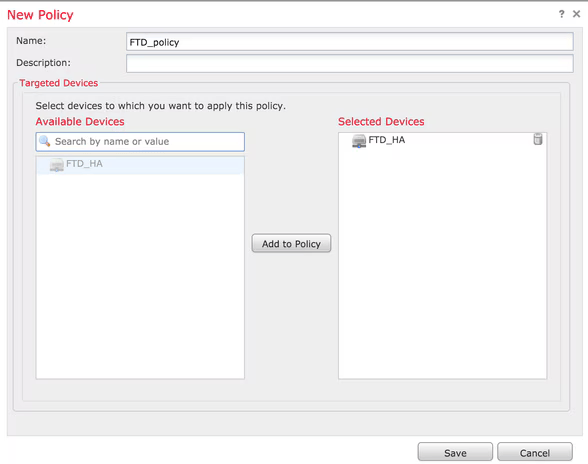
[1] Accessing Platform Settings
All logging related configurations can be accessed by navigating to the Devices > Platform Settings tab.
To edit an existing policy, click the pencil icon. To create a new policy, click New Policy and select Threat Defense Settings.
Select the appropriate FTD appliance and click Save.
[2] Logging Setup
To configure logging (Local and External):
- Go to Devices > Platform Settings > Syslog > Logging Setup.
- Enable Logging: Must be checked.
- Not required to select:
- Enable Logging on the failover standby unit
- Send syslogs in EMBLEM format
- Send debug messages as syslogs
- Click Save, then Deploy
- Choose the FTD appliance where you want to apply the changes, and click Deploy in order to start deployment of the platform setting.
[3] Event Lists
Navigate to Device > Platform Settings > Threat Defense Policy > Syslog > Event List.
Note: No event lists need to be added.
[4] Rate Limiting Syslog
Navigate to Device > Platform Settings > Threat Defense Policy > Syslog > Rate Limit.
Options available:
- Logging level
- Syslog levels
Note: Not required to add any entries in Logging level and Syslog levels.
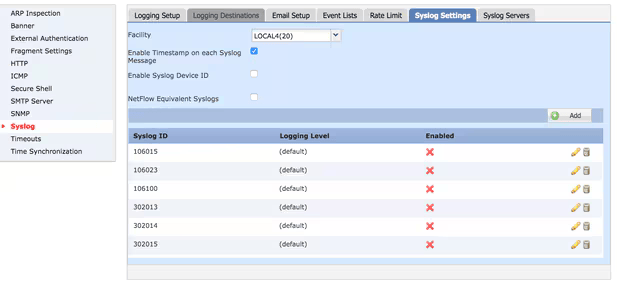
[5] Syslog Settings
Navigate to Device > Platform Settings > Threat Defense Policy > Syslog > Syslog Settings.
- Facility: A facility code is used to specify the type of program that is logging the message. Messages with different facilities can be handled differently. From the Facility drop-down list, choose the "Local7(23)" facility.
- Enable Timestamp on each Syslog Message: Check the Enable Timestamp on each Syslog Message check box in order to include the time stamp in Syslog messages.
- Enable Syslog Device ID:Check the Enable Syslog Device ID check box in order to include a device ID in non-EMBLEM-format Syslog messages.
Configure custom events list as needed.
Click Save, then Deploy the configuration to the selected FTD appliance.
Syslog IDs to Configure:
- Traffic Syslog IDs: 106015, 106023, 106100, 302013, 302014, 302015, 302016
- Security Events
- VPN Events
Configure External Logging
Navigate to Device > Platform Settings > Threat Defense Policy > Syslog > Logging Destinations.
FTD supports these types of external logging:
- FTD supports these types of external logging.
- SNMP trap: Sends the logs out as an SNMP trap.
- E-Mail: Sends the logs via email with a preconfigured mail relay server.
The configuration for the external logging and the internal logging are the same. The selection of Logging destinations decides the type of logging that is implemented. It is possible to configure Event Classes based on Custom Event lists to the remote server.
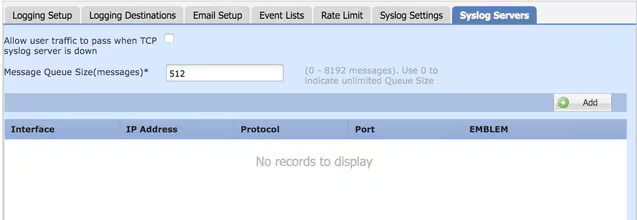
Remote Syslog Server Setup
Syslog servers can be configured to analyze and store logs remotely from the FTD.
There are three steps to configure remote Syslog servers.
- Go to Syslog Servers under Threat Defense Policy.
- Configure parameters:
- Allow user traffic to pass when TCP syslog server is down: If a TCP Syslog server has been deployed in the network and it is not reachable, then the network traffic through the ASA is denied. This is applicable only when the transport protocol between the ASA and the Syslog server is TCP. Check the Allow user traffic to pass when TCP syslog server is down check box in order to allow traffic to pass through the interface when the Syslog server is down.
- Message Queue Size: The message queue size is the number of messages that queues up in the FTD when the remote Syslog server is busy and does not accept any log messages.The default is 512 messages and the minimum is 1 message. If 0 is specified in this option, the queue size is considered to be unlimited.
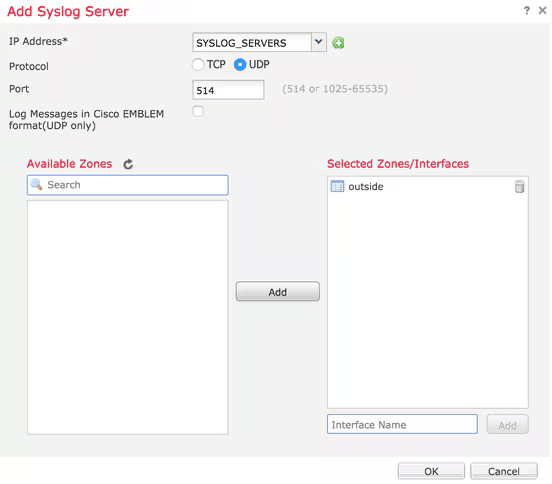
- Click Add to configure the server:
- IP Address: From the IP Address drop-down list, choose a network object which has the Syslog servers listed. If you have not created a network object, click the plus (+) icon in order to create a new object.
- Protocol:Click either the TCP or UDP radio button for Syslog communication.
- Port: 1514
- Available Zones: Enter the security zones over which the Syslog server is reachable and move it to the Selected Zones/ Interfaces Column.
- Go to ASA Firepower Configuration > Policies > Actions > Alerts.
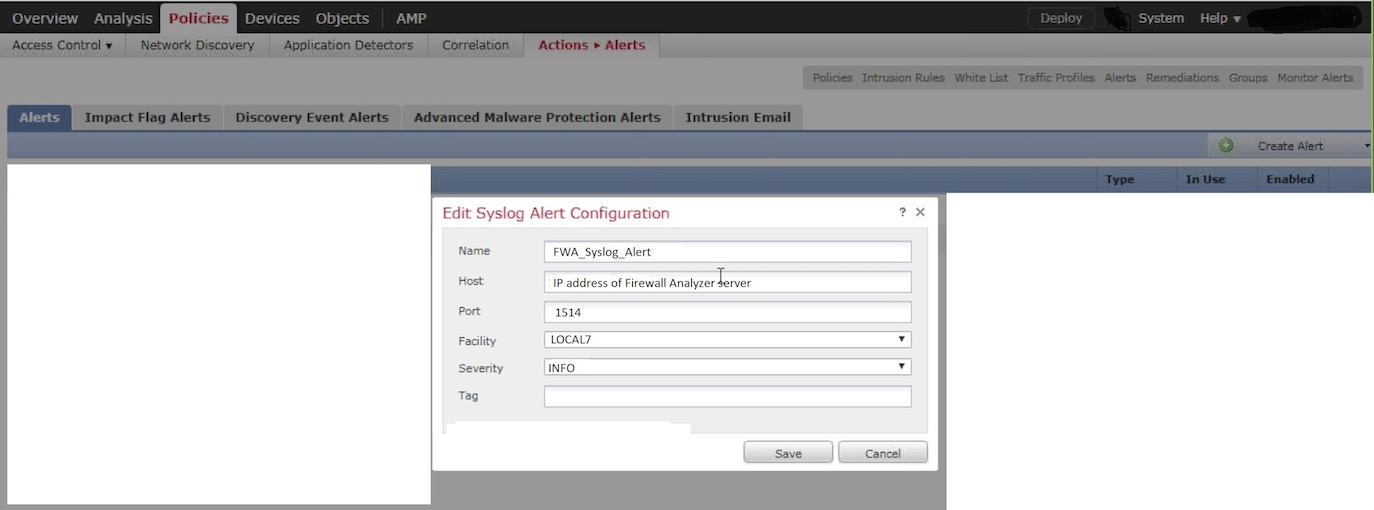
- From the Create Alert menu, choose Create Syslog Alert.
- Enter the following details:
- Name: Name of the alert
- Host: IP/hostname of the Firewall Analyzer server
- Port: 1514
- Facility: LOCAL7
- Severity: INFO
- Click Save
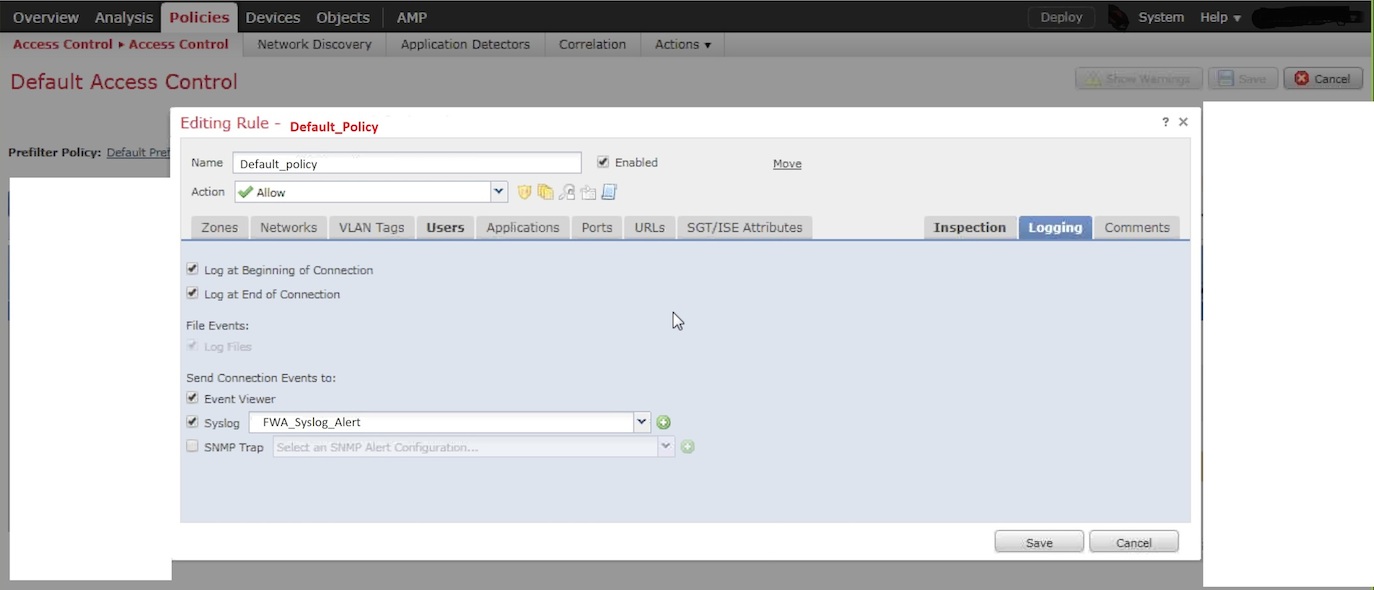
- Navigate to ASA Firepower Configuration > Policies > Access Control Policy
- Edit the desired rule and go to the Logging options.
- Select:
- Log at Beginning of Connection
- Log at End of Connection
- Send Connection Events to: Syslog, then select the Syslog Alert Response
- Click Save
Click Save in order to save the platform setting. Choose Deploy , choose the FTD appliance where you want to apply the changes, and click Deploy in order to start deployment of the platform setting.
Reference:Cisco Official Guide
Configuring Cisco ASA with FirePOWER Services
Creating a Syslog Alert Response
Configuring Logging for Traffic Events
For more details, refer to:
Thank you for your feedback!