Implementing privilege management in Endpoint Central starts with creating a robust Endpoint Privilege Management policy that governs how users can access and run applications with elevated rights. Administrators begin by defining a Privileged Application List, which includes applications that require administrative access. Once the list is curated, it is then associated with specific custom groups containing user devices that need this level of access. After association, the policy is deployed from the Endpoint Central console, allowing selected users to run approved applications with elevated privileges—while retaining standard user rights elsewhere. This structured approach ensures that privilege elevation is tightly controlled and contextually applied, reducing security risks and ensuring compliance across the enterprise.
The applications can be run with elevated privileges in the following ways:
Here is the notification shown in the endpoint when the user tries to self-elevate an application:
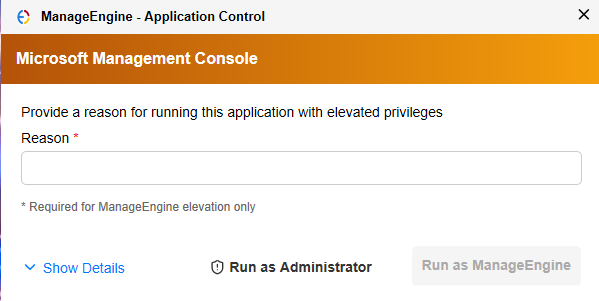
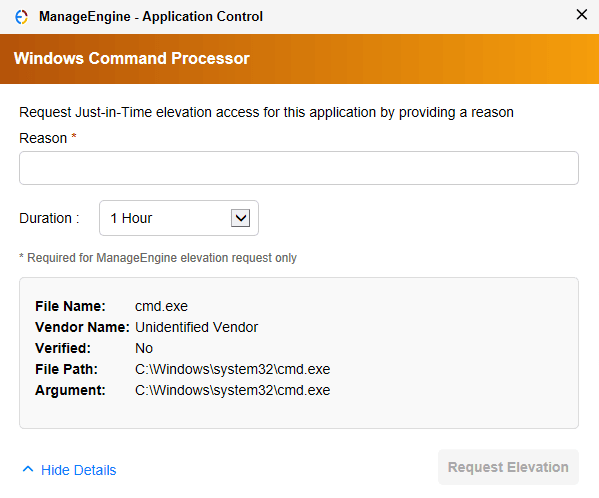
These requests will be displayed in the Just-In-Time Access tab. They can be approved or declined according to the requirement specified. Each requested elevation access will be automatically revoked on the end of the timeframe, or can also be revoked through the console.
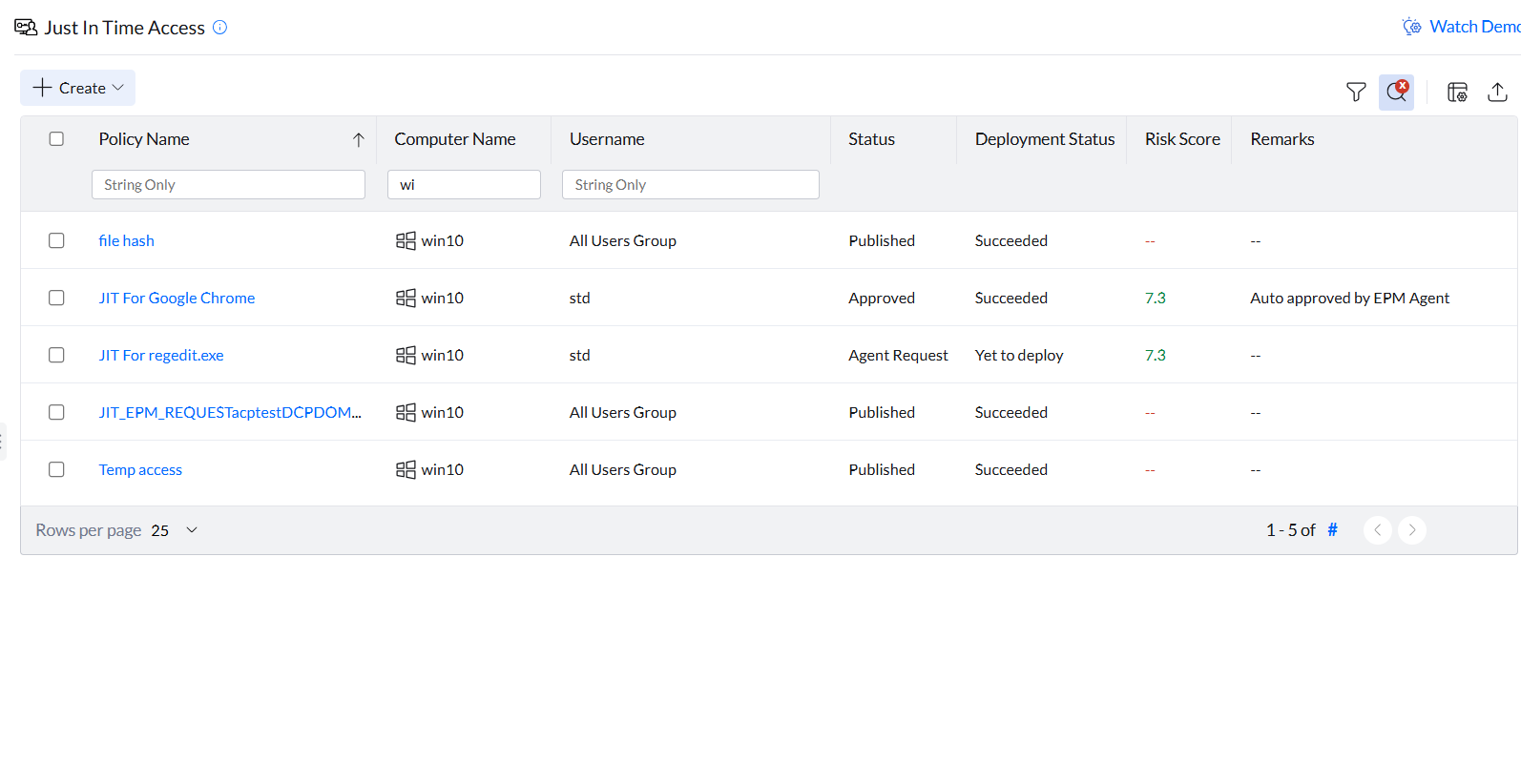
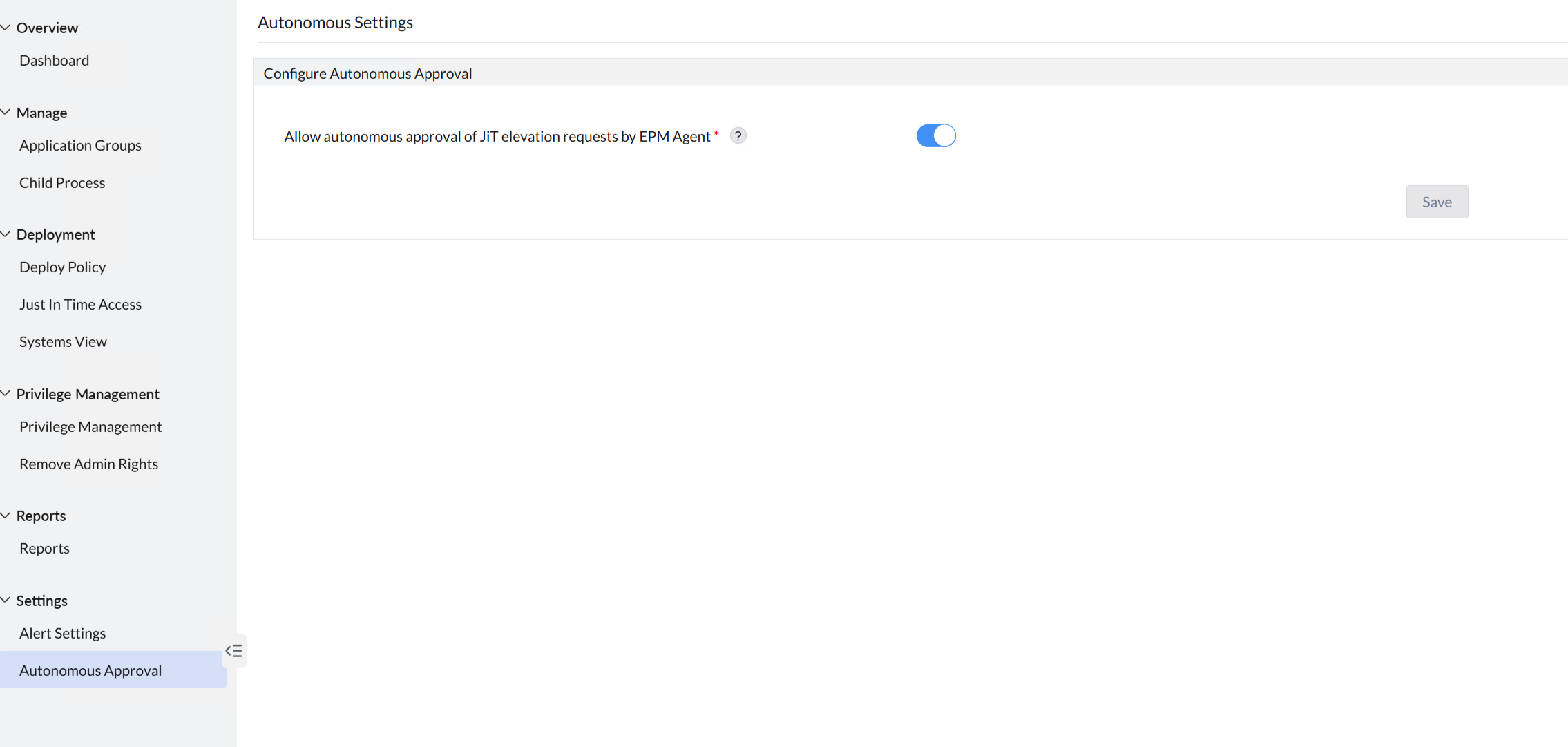
The requests can also be automatically approved, if it is enabled under Settings → Autonomous Approval.
The privilege elevation can be configured to either all allowed applications or specific applications. The Specific Applications for elevation can be added using the rule types such as Vendor, Products, Verified Executable, File Hash, CLSID, and Folder Path.
The CLSID rule type lets you control COM object elevation by referencing their unique Class IDs instead of executables or paths. This ensures elevation rules apply directly to Windows system components or registered COM objects, reducing reliance on mutable file attributes. It provides granular privilege management for built-in OS functions.
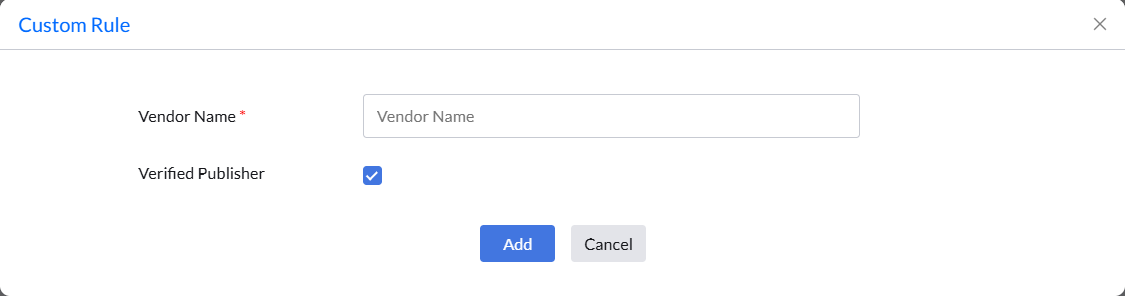
Custom rules can also be configured to define custom criteria such as the vendor, product name, verified executable, file hash, or CLSID to create application rules for those which are not detected in your network. Click Add under the specific rule type to define the custom rule.