Of late, cyber-criminal activities across the globe have assumed such grave proportions that all enterprises - big and small, are exposed to security breaches and identity thefts of various kinds. Many sabotage were found to have been caused by the insiders of the enterprises - either disgruntled staff or greedy techies or sacked employees. As stolen identities seem to have served as the ‘hacking channel’ for many cyber-crimes, improper management of the administrative passwords is believed to be at the root of a good number of security threats. This paper discusses the causes of security incidents in detail and suggests ways to effectively tackle the challenge.
If Samuel Taylor Coleridge were alive today, he would have probably rephrased his immortal lines ‘Water, water everywhere, ne any drop to drink’ as ‘Threat, Threat Everywhere, Cyber criminals on the prowl‘! Of late, cyber-criminal activities across the globe have assumed such grave proportions that all organizations - big and small, are exposed to security breaches and identity thefts.
Let us take a quick look at some of the major cyber-crimes happened recently:
The list of cyber-crimes and security incidents will go on and on and will fill volumes, if one were to point out all. Still worse, a good number of security incidents are not revealed for fear loss of reputation. The above list however gives an indication of the magnitude of the problem. It also indicates that:
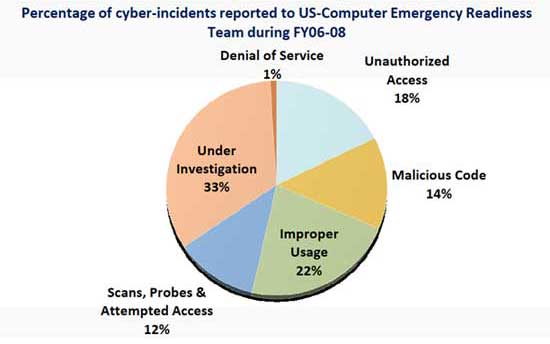
Past trends show that the exact cause of most of the security incidents goes unreported. Of course, there have been instances where the culprits had been brought to book and their modus-operandi revealed to the outer world. But, the fact remains that exact cause of most of the incidents remains a secret, unfortunately.
Traditionally, keylogger trojans (which monitors keystrokes, logs them to a file and sends them to remote attackers), cross-site scripting (which enables malicious attackers to inject client-side script into web pages viewed by other users and exploit the information to bypass access controls) and viruses have mostly acted as the security attack channels.
However, of late, as stolen identities seem to have served as the ‘hacking channel’ for most of the cyber-criminals, analysts generally believe that improper management of the Administrative Passwords, which are often aptly referred as 'Keys to the Kingdom', is at the root of many security threats.
Another harsh fact is that many a sabotage had been caused by the insiders of the enterprises. Either disgruntled staff or greedy techies or sacked employees were involved in many of the security
incidents. That means, in this hi-tech era, breach of trust could occur anywhere, anytime leading to serious consequences. Quite often, lack of well-defined internal controls and access restrictions pave the way for security incidents.
Before analyzing the causes further, let us dwell on the current scenario. How administrative passwords are being handled in enterprises?
If truth be told, even many big enterprises do not have any effective password management system in place at all. Employees follow their own, haphazard way of maintaining the passwords; there is rarely any meaningful management.
From the foregoing, it is clear that the haphazard style of password management makes the enterprise a paradise for hackers – internal or external.
Unfortunately, enterprises generally do not tend to attach importance to this crucial aspect of administrative password management until a security incident or identity breach rocks the enterprise. This negligence often proves costly.
Many security breaches like the ones discussed above might have stemmed from lack of adequate password management policies and internal controls. Analysts strongly believe that most of the security incidents are actually avoidable by placing access restrictions and well-defined password policies.
Take preventive action, safeguard your data
With cyber-threats looming large, enterprises should think of taking preventive action by strengthening internal controls. Manual processes and home-grown tools may not be able to provide the desired level of security and controls.
It is pertinent to quote here a recent research report by Gartner:
"Manual procedures for managing shared account passwords can be intrusive, interrupting normal operations and unacceptably delaying the resolution of problems. These procedures can also be fragile, failing to consistently deliver the desired level of control and accountability and exposing organizations to insider threats."
(Source : Gartner, Inc., "MarketScope for Shared-Account/Software-Account Password Management", Ant Allan, Perry Carpenter, 16 June 2009).
One of the effective ways to achieve internal controls is to deploy a Privileged Password Management Solution that could replace manual processes and help achieve highest level of security for the data.
Privileged Password Managers help enterprises safeguard their data and thereby avoid security incidents in multiple ways than one:
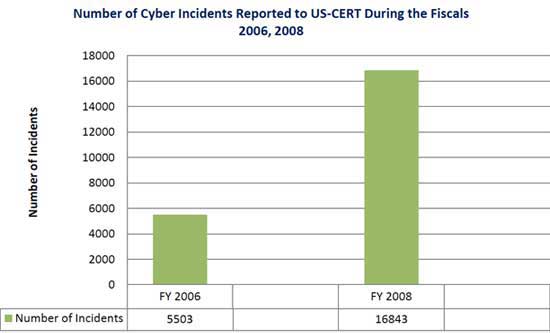
Researchers repeatedly point out that identity theft incidents are on the rise and it will only keep growing due to many reasons, including economic situation, social factors and technological advancements that make the tech-savvy criminals more creative every passing day.
Not all security incidents could be prevented or avoided; nor could privileged password management software act as the panacea for all cyber security incidents. But, the security incidents that happen due to lack of effective internal controls are indeed preventable. Enterprises should take preventive action to combat cyber-criminals. Otherwise, enterprises might end up locking the stable after the horse has bolted!
Password Manager Pro (PMP) is a web-based, secure vault for storing and managing shared sensitive information such as passwords, documents and digital identities of enterprises. It helps control the access to shared administrative passwords of any 'enterprise resource' such as servers, databases, network devices, applications etc. PMP enables IT managers to enforce standard password management practices. For more details, visit http://www.passwordmanagerpro.com