- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Active Directory forms the core part of the Microsoft Windows domain administration. It is a very critical component, as the failure of it may disrupt the entire network. When the directory service fails, the details are promptly recorded in the logs. If the logs are analyzed thoroughly, the root cause of the failure can be found. Any operation on the Active Directory objects has to be captured. The Active Directory operations on directory service object and replica source naming context directly affects the user accesses and operations of machines in the network. Thus, monitoring Active Directory log events is critical to ensure smooth functioning of networks.
EventLog Analyzer can monitor Active Directory logs and any specific failure incident can be tracked in real-time. With this, it can alert the network administrator instantly, so that remedial measures can be taken swiftly to avoid network failure.
It has the flexibility to create custom reports to monitor Active Directory specific events. The respective event IDs of Active Directory can be monitored.
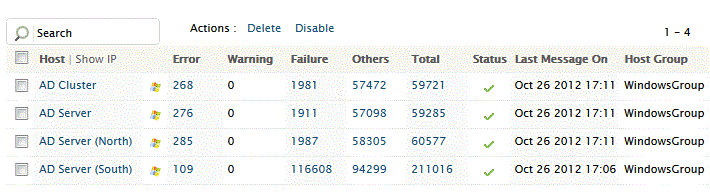
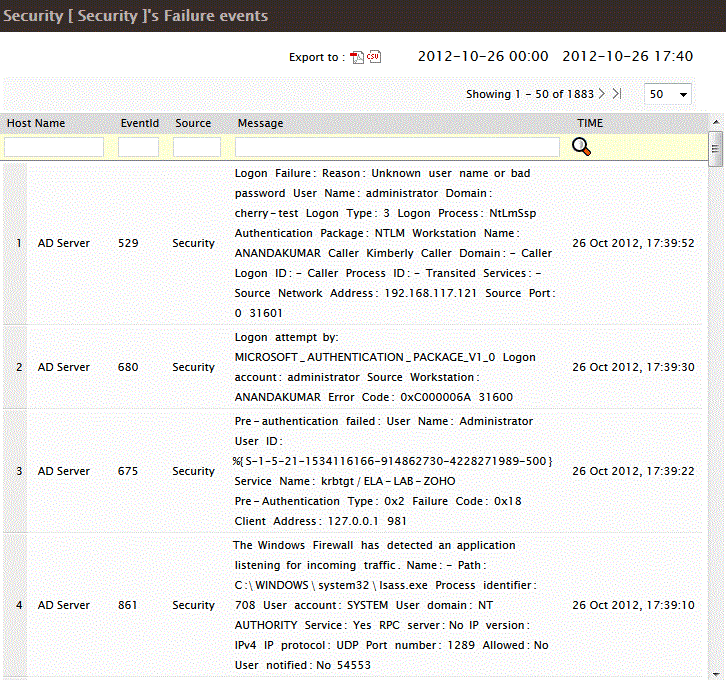
Ensure that logging is enabled for Active Directory events and it is not filtered by the event filter of EventLog Analyzer.
A short description of Active Directory
Active Directory is a directory service of Microsoft Windows domain networks. It forms part of the Windows Server operating system. Server which run Active Directory are called Domain Controllers. It provides administrators with centralized administration and security of network. It authenticates and authorizes all users and computers in a Windows network domain. It assigns and enforces security policies on all computers. It uses Lightweight Directory Access Protocol (LDAP). The logs of Active Directory is stored in the Event Viewer of Windows OS.
Active Directory related Event IDs
The Windows Server 2000 and 2003 event IDs for Directory service
- Windows 565 - Object Open (Active Directory)
- Windows 566 - Object Operation (W3 Active Directory)
The Windows Server 2008 event IDs for Directory service
- Windows 4661 - A handle to an object was requested
- Windows 4662 - An operation was performed on an object
- Windows 4928 - An Active Directory replica source naming context was established
- Windows 4929 - An Active Directory replica source naming context was removed
- Windows 4930 - An Active Directory replica source naming context was modified
- Windows 4931 - An Active Directory replica destination naming context was modified
- Windows 4932 - Synchronization of a replica of an Active Directory naming context has begun
- Windows 4933 - Synchronization of a replica of an Active Directory naming context has ended
- Windows 4934 - Attributes of an Active Directory object were replicated
- Windows 4935 - Replication failure begins
- Windows 4936 - Replication failure ends
- Windows 4937 - A lingering object was removed from a replica
- Windows 5136 - A directory service object was modified
- Windows 5137 - A directory service object was created
- Windows 5138 - A directory service object was undeleted
- Windows 5139 - A directory service object was moved
- Windows 5141 - A directory service object was deleted
Other features
Log management
Centrally manage log data from sources across the network. Get predefined reports and real-time alerts that help meeting the security, compliance, and operational needs.
IT compliance management
Comply with the stringent requirements of regulatory mandates viz., PCI DSS, FISMA, HIPAA, and more with predefined reports & alerts. Customize existing reports or build new reports to meet internal security needs.
Application log management
Analyze application log from IIS and Apache web servers, Oracle & MS SQL databases, DHCP Windows and Linux applications and more. Mitigate application security attacks with reports & real-time alerts.
Syslog server management
EventLog Analyzer collects and analyzes log data from Linux/Unix servers to provide on-the-fly reports that help detecting suspicious behaviors, anomalous syslog activities, and more.
Print Server Management
Monitor and audit print server with detailed reports on documents printed, attempts to print documents without proper permission, failed print jobs and their causes, and more.
Log forensic analysis
Perform in-depth forensic analysis to backtrack attacks and identify the root cause of incidents. Save search queries as alert profile to mitigate future threats.
Need Features? Tell Us
If you want to see additional features implemented in EventLog Analyzer, we would love to hear. Click here to continue











