- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Windows devices are the most popular choice in most business networks. To deal with the terabytes of event log data these devices generate, security admins need to use a powerful log management tool like EventLog Analyzer that can provide end-to-end Windows event log management by automating processes like log collection, parsing, analysis, correlation, and archival.
Check out how EventLog Analyzer handles event log management
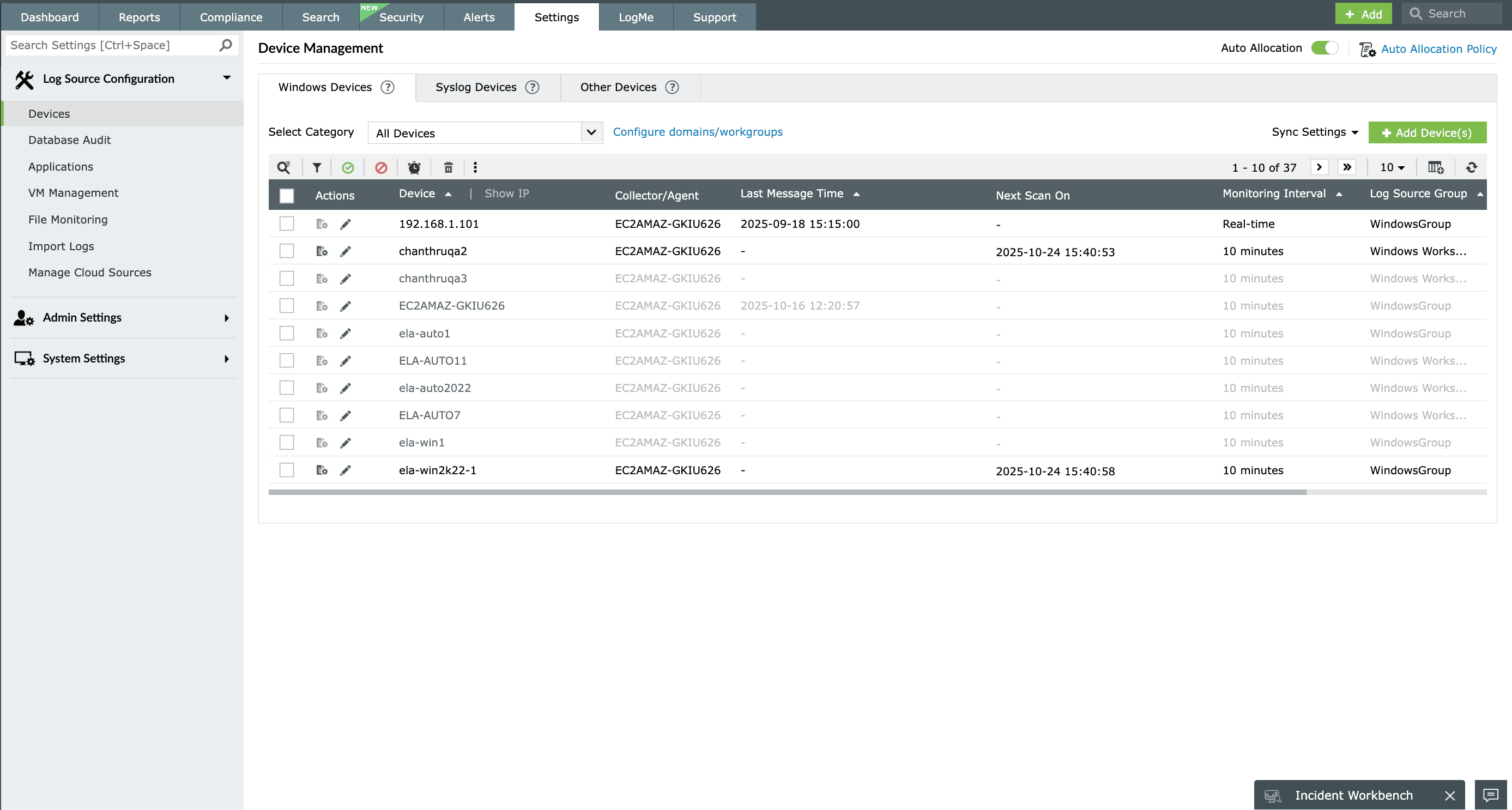
Event log collection
An important function of an event log management tool is collecting event logs from every source possible. EventLog Analyzer's event log collection capabilities are exceptional with support for both agentless and agent-based methods of log collection.
-
Agentless event log collection
This method involves collecting event logs using native mechanisms in Windows devices. EventLog Analyzer can communicate with the Windows devices in your network and collect event logs via mechanisms such as WMI, DCOM, and RPC.
-
Agent-based event log collection
For situations where native mechanisms are unable to be used for native mechanisms, EventLog Analyzer comes bundled with an event log collecting agent. This agent needs to be installed in the log source in order to communicate with and deliver event logs to EventLog Analyzer's server.
Event log filters
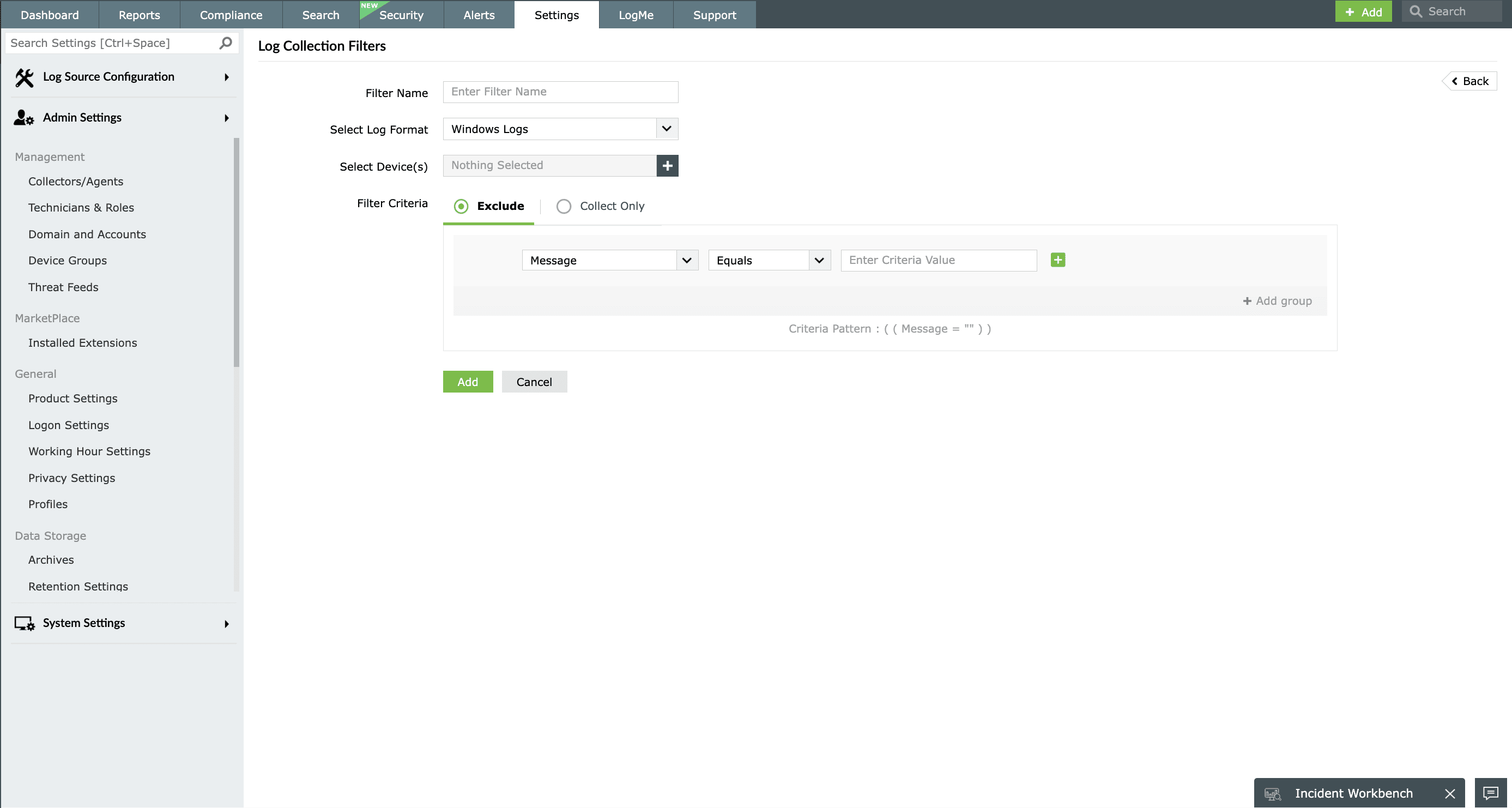
Most of the event logs generated in a network denote routine activities. This presents two challenges:
- Spotting event logs that provide security information
- Maintaining the required storage space for saving all the collected event logs
To address these challenges, EventLog Analyzer provides event log filters, which can be used to sort through the collected logs to find those that are significant from a security perspective. These customizable filters are based on the event log source, user, or components of the log. All event logs can be archived automatically for future reference through EventLog Analyzer.
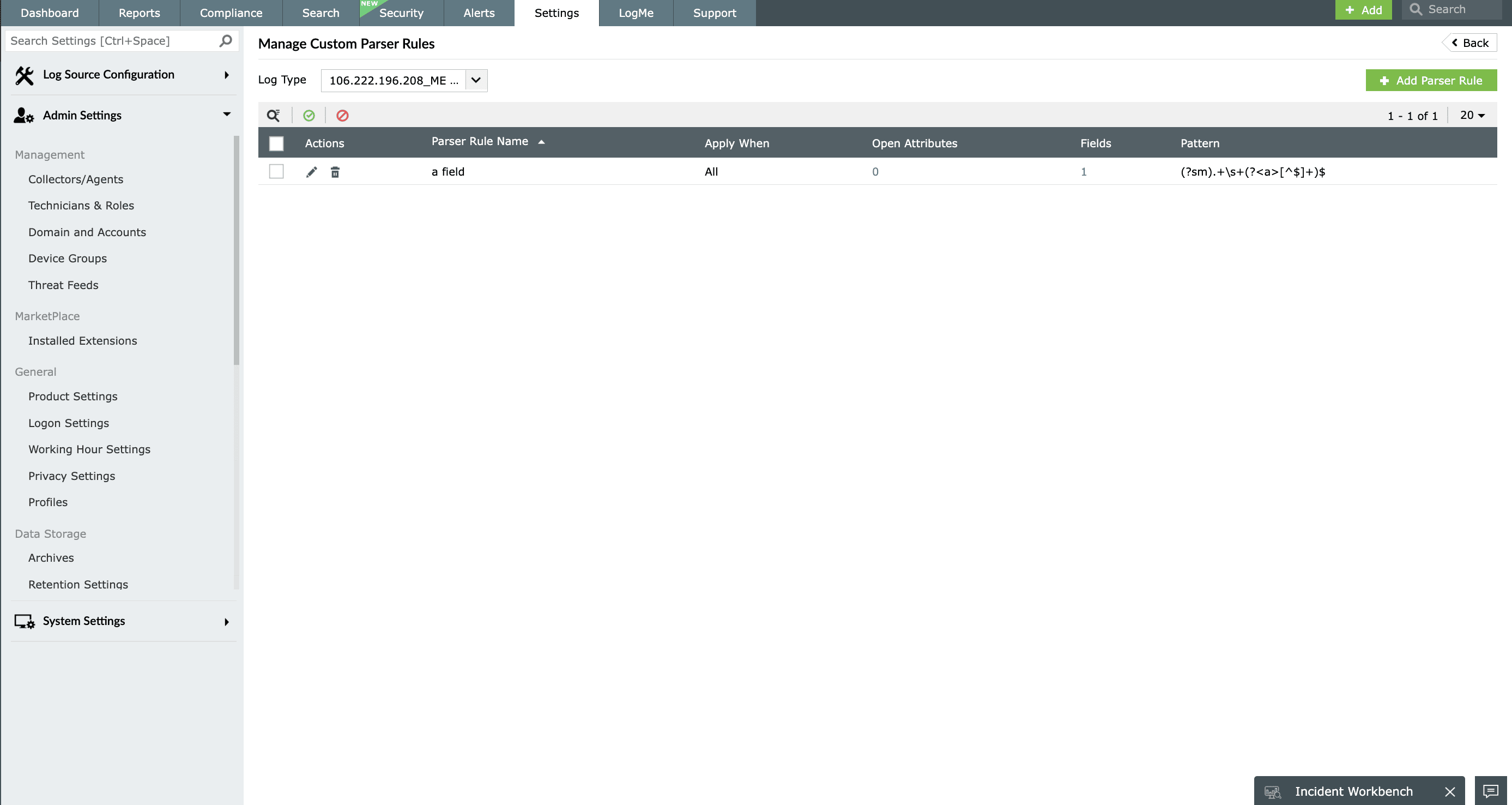
Event log parser
To gain the most from the collected event logs, it's vital for a log management tool to parse event logs. EventLog Analyzer has a built-in event log parser that can normalize, parse, and index event logs.
Understand parsing through an example
Let's take a log with a device name and username in it; while this information is readily available, it's not clear which name is for the device and which is for the user. EventLog Analyzer's event log parser breaks Windows event logs down so that different pieces of information—for this example, the device name and username—each appear as their own logs, which are then grouped into the appropriate sections.
Event log analysis and correlation
Log analysis is important for an event log management tool to perform as an efficient security tool. EventLog Analyzer expedites event log analysis with its log parser. This is further strengthened by EventLog Analyzer's correlation engine.
EventLog Analyzer's correlation engine can save you from the painstaking process of manually correlating log data by automatically retrieving Windows event logs from their database and comparing them with formatted logs from other sources. This will help with detecting any chain of events that might represent an attack on the network.
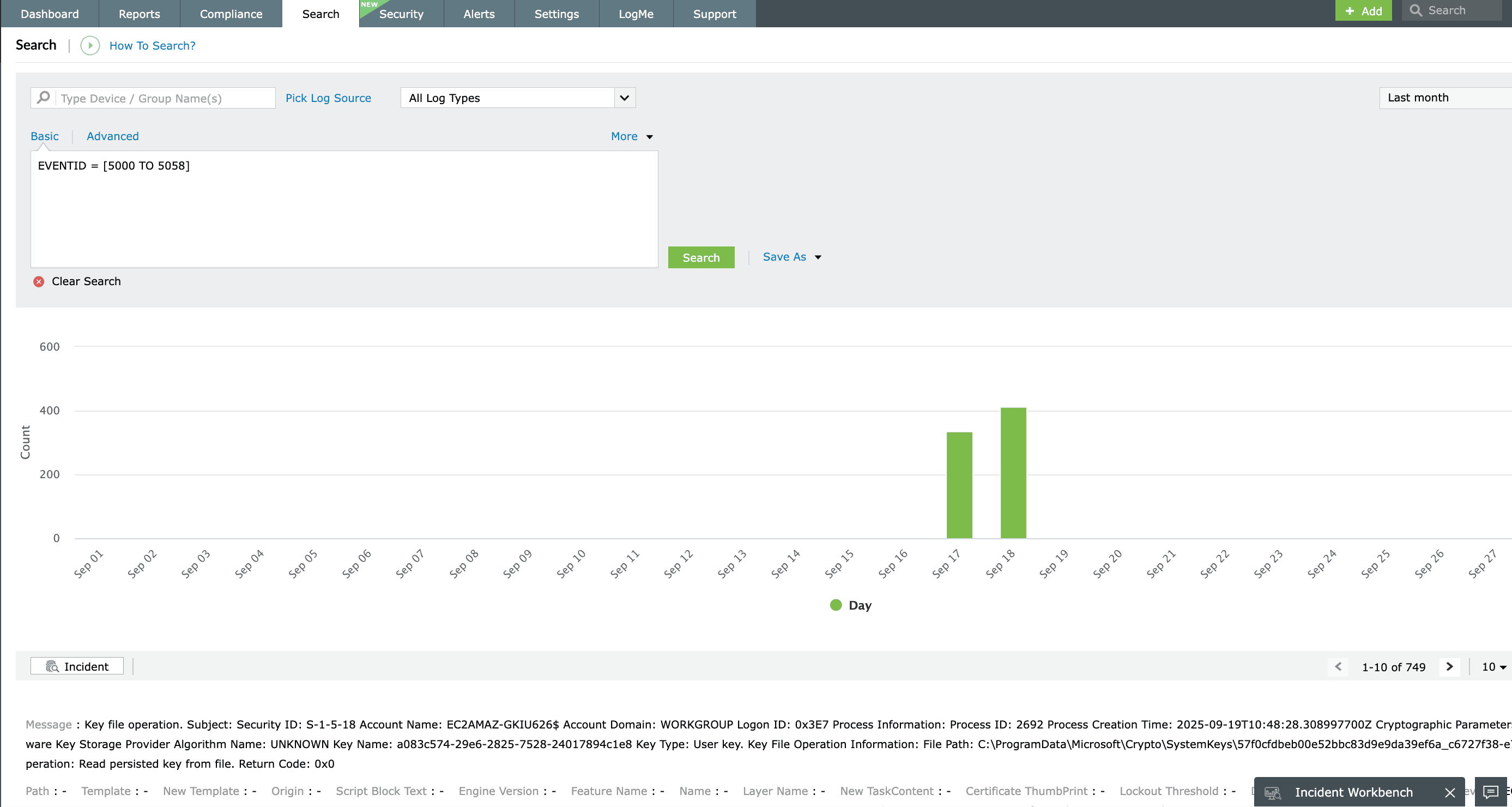
Event log search and forensic analysis
IT administrators often need to perform forensic log analysis in their organization. During forensic log analysis, administrators have to search through logs to find the information they need, but the enormous volume of Windows event logs makes searching them manually almost impossible.
EventLog Analyzer has a dedicated search module that is easy to learn and use. It supports search queries containing wildcards and Boolean operators; you can also perform grouped and range searches. To search for a Windows event log using EventLog Analyzer, you can utilize continuous prompts to frame a logical query, and this tool will render all the logs that match your query.
Event log archiving
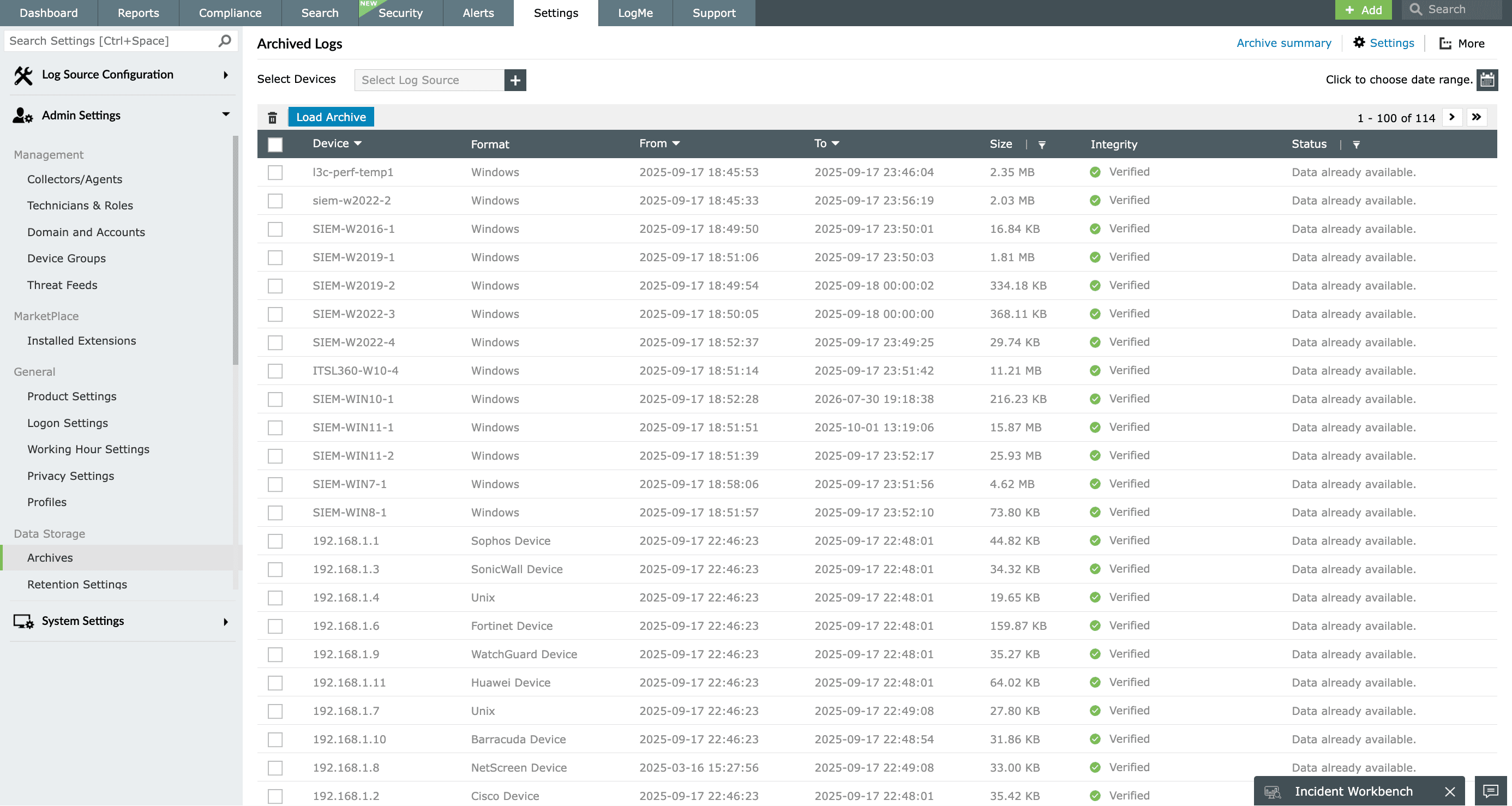
Archiving and properly disposing of collected event logs is an important part of the event log management cycle. Additionally, major IT security regulatory agencies scrutinize the process organizations have for event log archival. Most of them mandate the number of days event logs need to be stored before the logs can be permanently deleted.
By deploying EventLog Analyzer, organizations can automate event log archiving. You can designate the number of days after which the collected event logs will be moved to the archive, and customize the number of days after which the archived event logs are permanently deleted. These values can be decided based on the compliance mandates and internal audit requirements that your business needs to comply with. EventLog Analyzer's event log archival feature helps enterprises comply with all major IT mandates, such as HIPAA, SOX, GLBA, PCI DSS, and the GDPR.
Related solutions
In-depth event log audits and reports
EventLog Analyzer offers thousands of predefined audit reports and custom reporting features for Windows event logs. The exhaustive reports help you gain insights into anomalous activities, critical incidents, and persisting issues.
IIS server log management
Monitor Microsoft IIS web and FTP sever activity trends, data exchange, errors, user activities, security events, and web attacks with EventLog Analyzer's application log monitoring features.
Windows firewall auditing
EventLog Analyzer helps track changes made to Windows firewall configurations, Group Policies, and firewall rules. Additionally, the tool also detects common network flood attacks like SYN attacks, port scan attacks, and denial-of-service attacks by analyzing firewall event logs.
Advanced threat detection
EventLog Analyzer correlates logs from a wide range of network entities and third-party threat intelligence applications with data from global threat feeds to identify new and evolving attack patterns and block millions of globally blacklisted sources.
Incident response management
Automate responding to security incidents by constructing workflows. EventLog Analyzer offers multiple sets of workflow actions, like Windows actions, Active Directory actions, network actions, and logical actions. Use these actions to disable systems, delete user accounts, run scripts, disable USBs, and execute similar response measures.
Real-time event alerts
Set up alerts for critical security incidents and other events of interest with EventLog Analyzer's more than 500 predefined alert profiles. Customize the alerts, create new ones, and receive real-time notifications through SMS and email.











