- HOME
- Endpoint Management Analytics
- Spot and stop cyberattacks through advanced threat detection and analytics
Spot and stop cyberattacks through advanced threat detection and analytics
- Last Updated: July 1, 2024
- 355 Views
- 4 Min Read
The 2021 State of IT Operations report by Automox revealed that nearly 60% of data breaches can be traced back to a missing software patch. Streamlining patching processes will strengthen an organization's defense against cybercrime. Besides missing patches, some assets in your enterprise might have forbidden apps installed in them or include systems running without BitLocker encryption. These vulnerable devices are a threat to your organization's security layer and could serve as a gateway for attackers.
Tracking all vulnerable assets in your organization is the only way to ensure that they don't fall prey to external threats. Leveraging analytics for your endpoint management data will enable your enterprise to gain visibility into IT assets, secure them, and prevent a large-scale mishap.
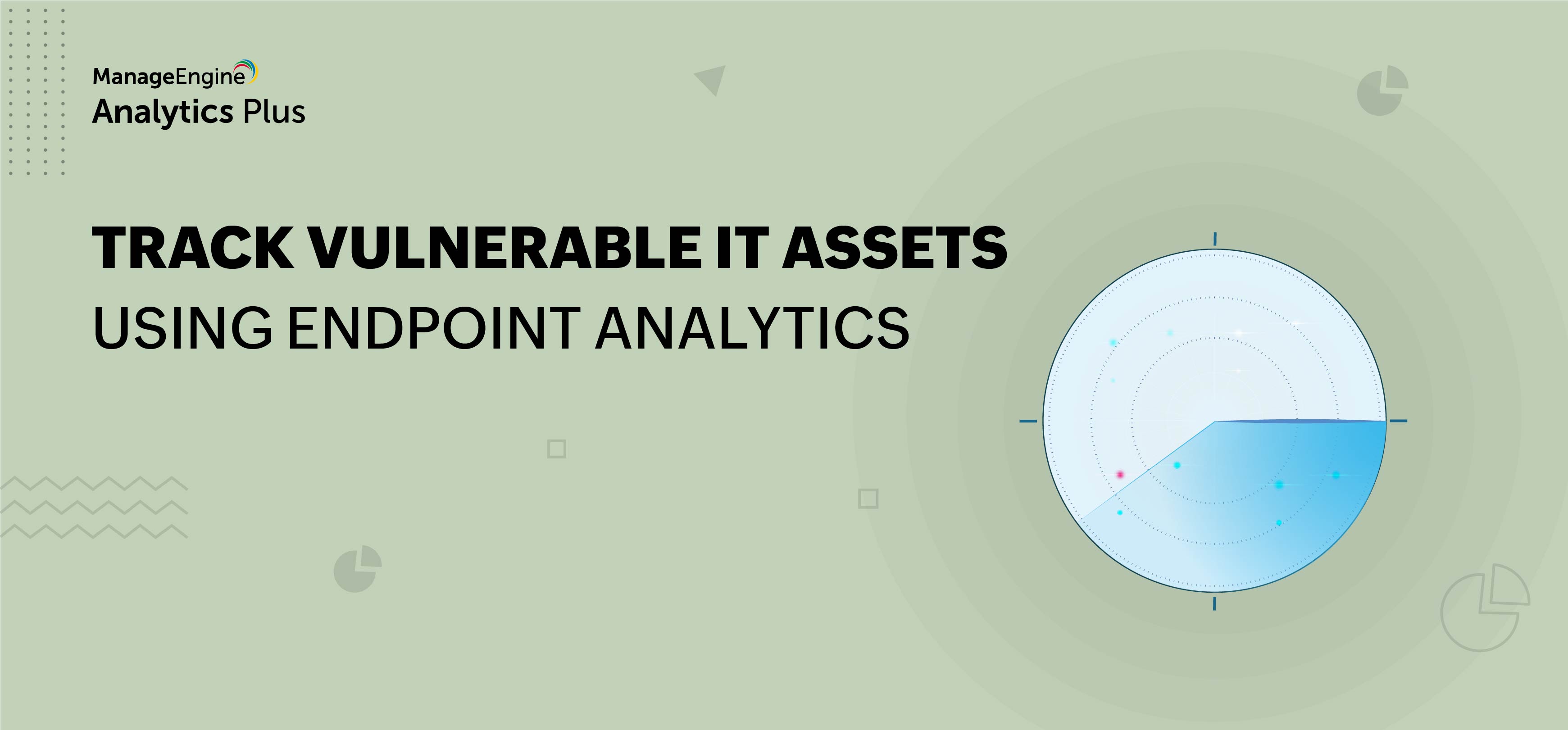
Devices with missing patches
Security patches are the bridge between data and security. With the increasing number of security threats, vendors who sell operating systems and applications, race against time to develop patches to protect their software. The responsibility is now with the organization's IT teams to apply these patches on time and secure the devices. The best way to monitor if your endpoints are patched and up-to-date is to look for assets with missing patches. A report that provides a list of systems missing patches so they are vulnerable to external threat actors is vital for proactively taking action to prevent harm to your organization.
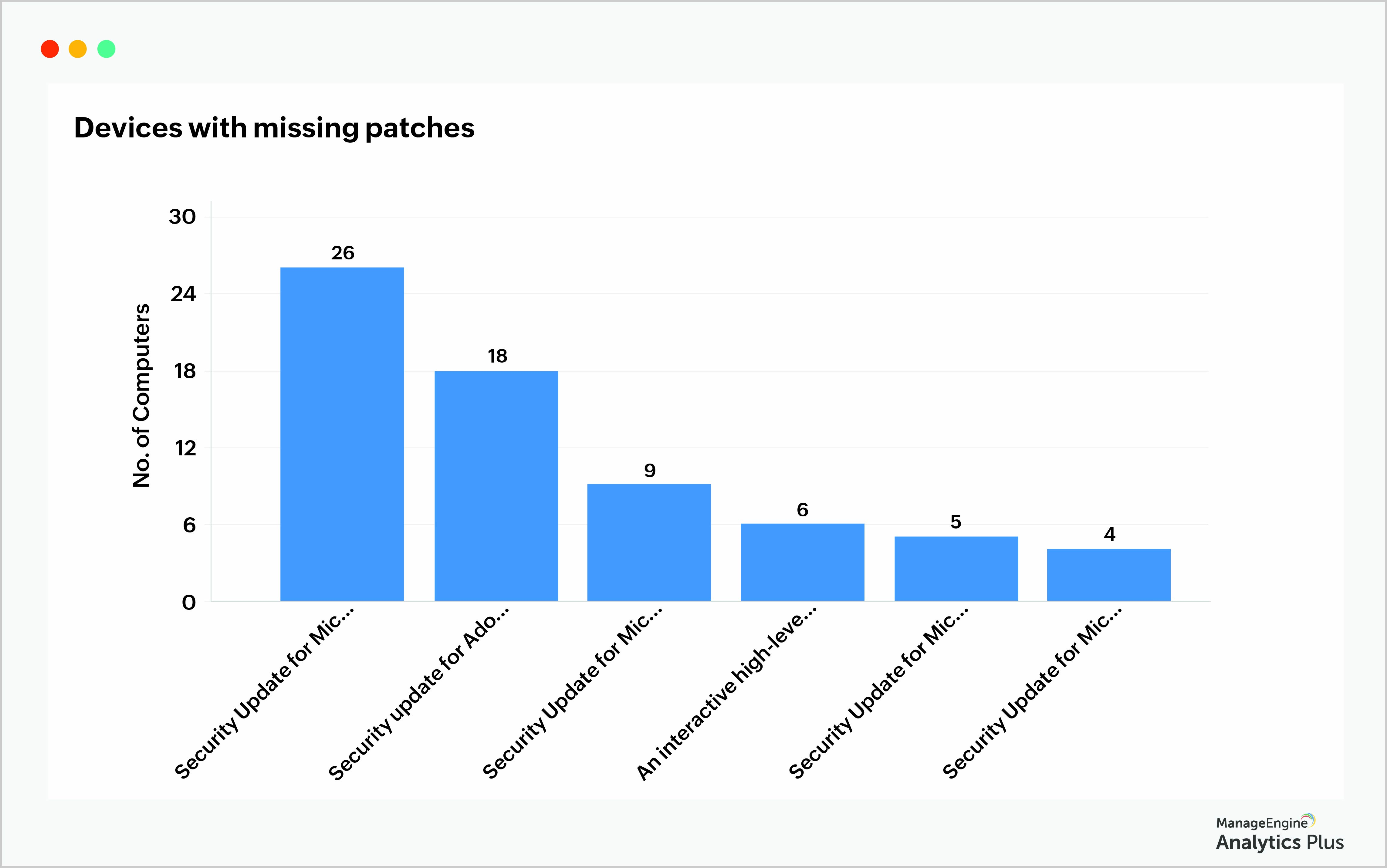
Patch management time frame
Time is of the essence when it comes to security patches. IT admins must ensure that patches are applied to all the systems without any delay. The WannaCry ransomware cyberattack in 2017 is a glaring example of what happens when patches aren't updated on time. Nearly 200,000 computers across 150 countries were exploited by hackers due to a vulnerability in the Microsoft OS that wasn't patched on time.
To determine the time taken by your IT department to apply patches, a report that shows the patch management time frame is extremely helpful. The Patch release timeframe report below gives the percentage of patches applied at three different periods since their release: within 30 days, 31-60 days, and more than 91 days. This report notes that close to 70% of patches in the organization were deployed after 91 days of their release and that indicates the organization is highly vulnerable to cyberthreats. In such cases, the next step is to deploy an automated patch process immediately for all unpatched systems.
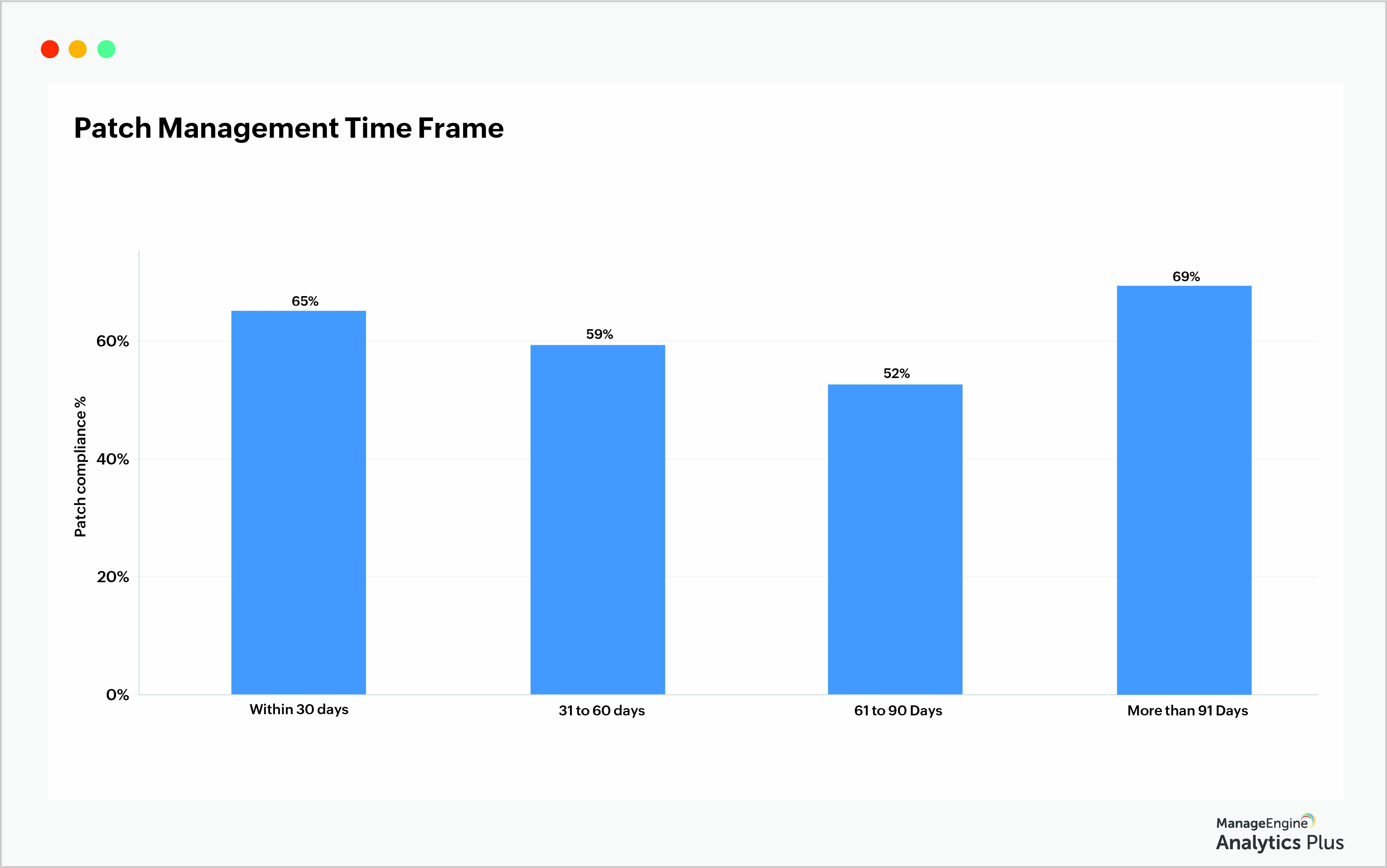
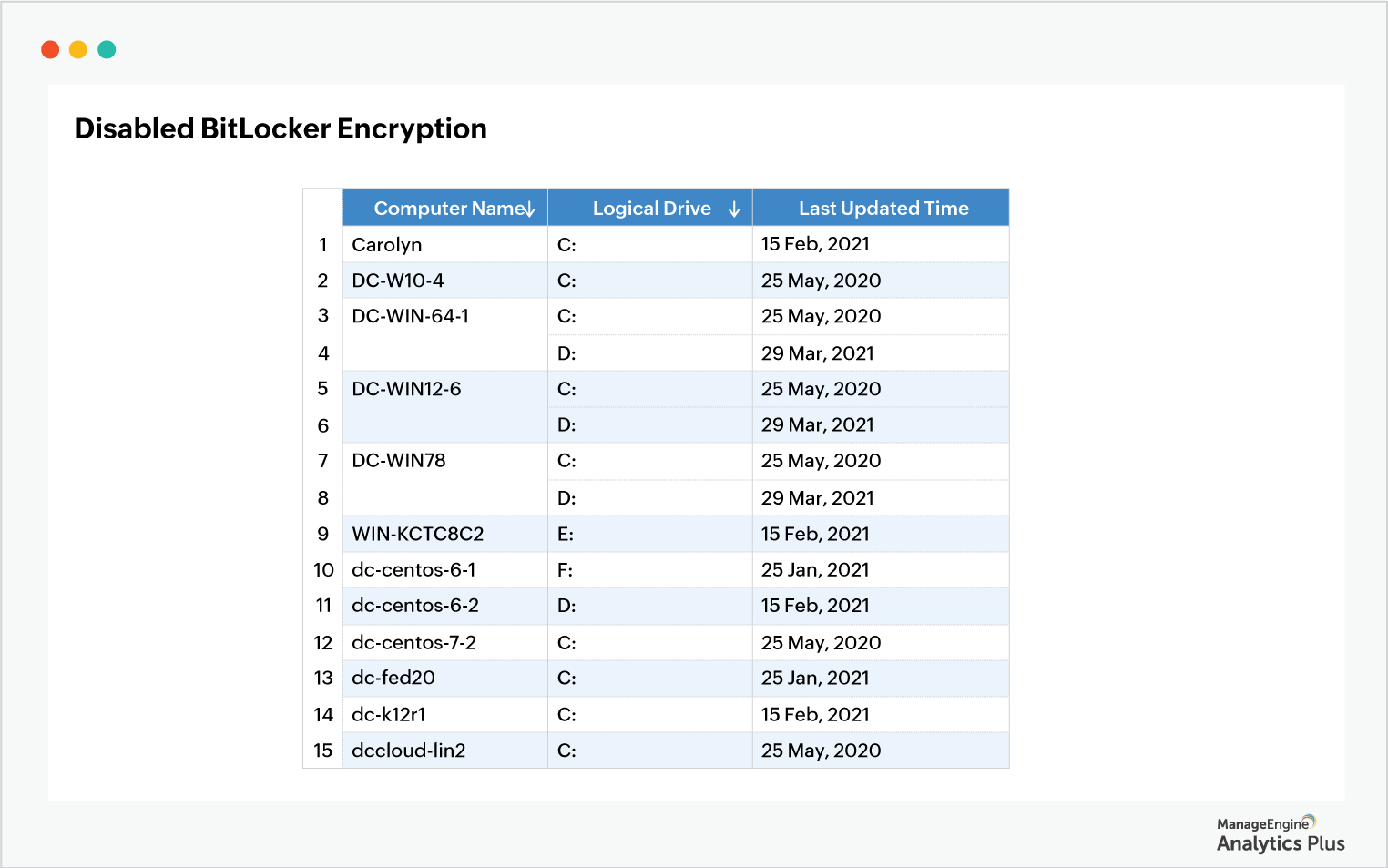
Disabled BitLocker encryption
BitLocker is a Windows encrypted file system that enables organizations to safeguard confidential data from hackers by encoding logical drives. When a file moves into a drive that has BitLocker encryption, the file will be automatically encrypted. This ensures complete data security for the files stored in a computer in the event of a breach. A report that gives you a list of devices with disabled BitLocker encryption enables the security team to identify the respective device owners and contact them immediately. This ensures that crucial enterprise data is not exposed due to lack of encryption, in the event of a cyber attack.
Devices missing critical restrictions
Devices missing critical restrictions are more likely to fall prey to a security breach as they are more vulnerable. Lack of restrictions while connecting to Bluetooth, a camera, or accessing cellular data can be fatal for the security of an organization.
For example, consider USB connections. When you plug in a pen drive to a computer which, in turn, is connected to a secure server in your organization, you can easily download data from the server onto the pen drive, which can then be used to copy crucial data.
It is difficult to detect these devices precisely when they are accessing computers in your network, but you can certainly limit their use. Start by restricting the number of computers with USB port access. The report below illustrates the number of USB-connected devices. Even though it's not necessary to consider a high number as a security hazard, it's essential to flag them for further analysis.
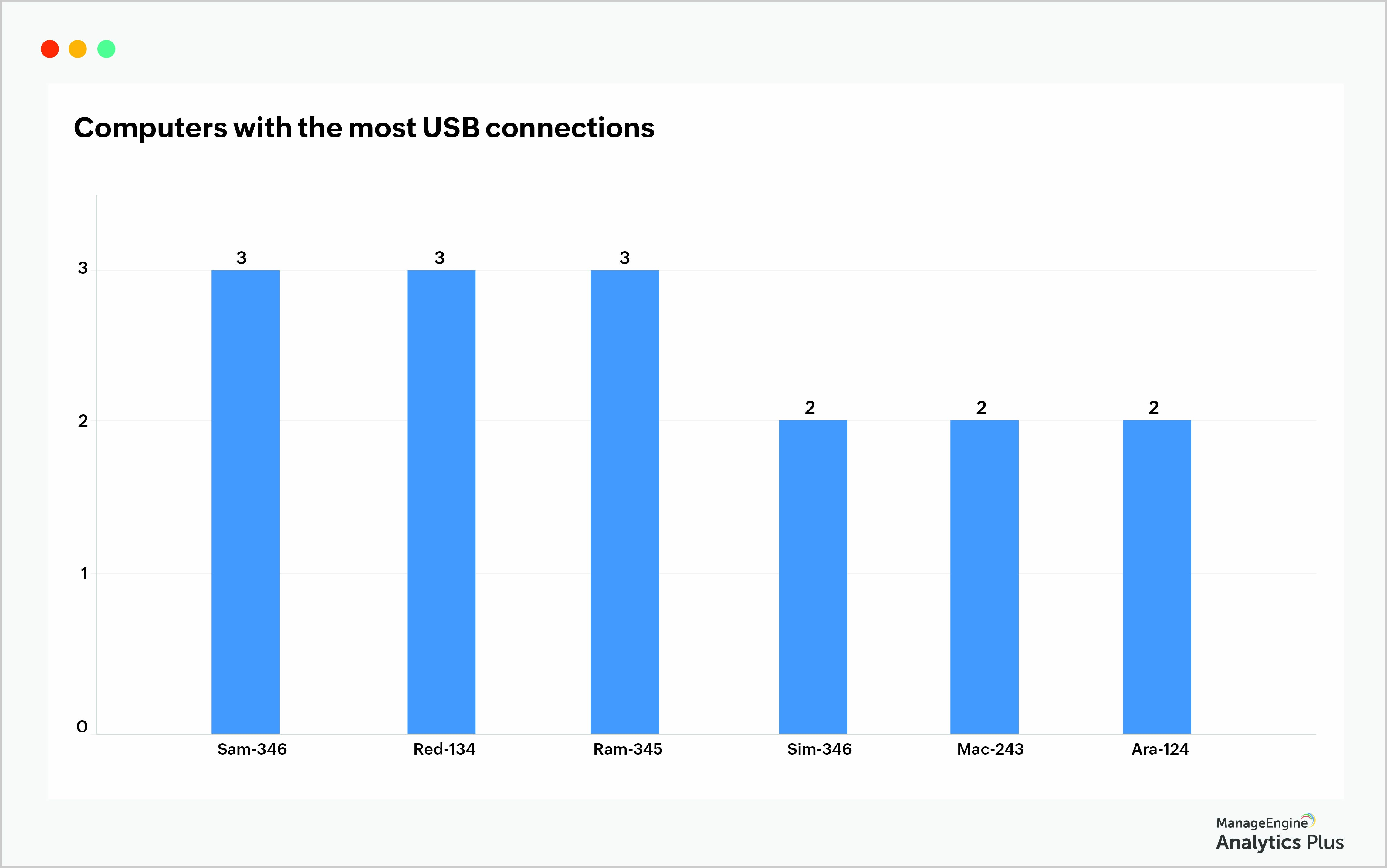
Devices using prohibited apps
Often, corporate devices such as smartphones or tablets double up as personal devices to employees as they can install applications that are not related to work. While apps such as Netflix and Spotify, might not impact security directly, it is important to track the number of prohobited applications installed by end users.
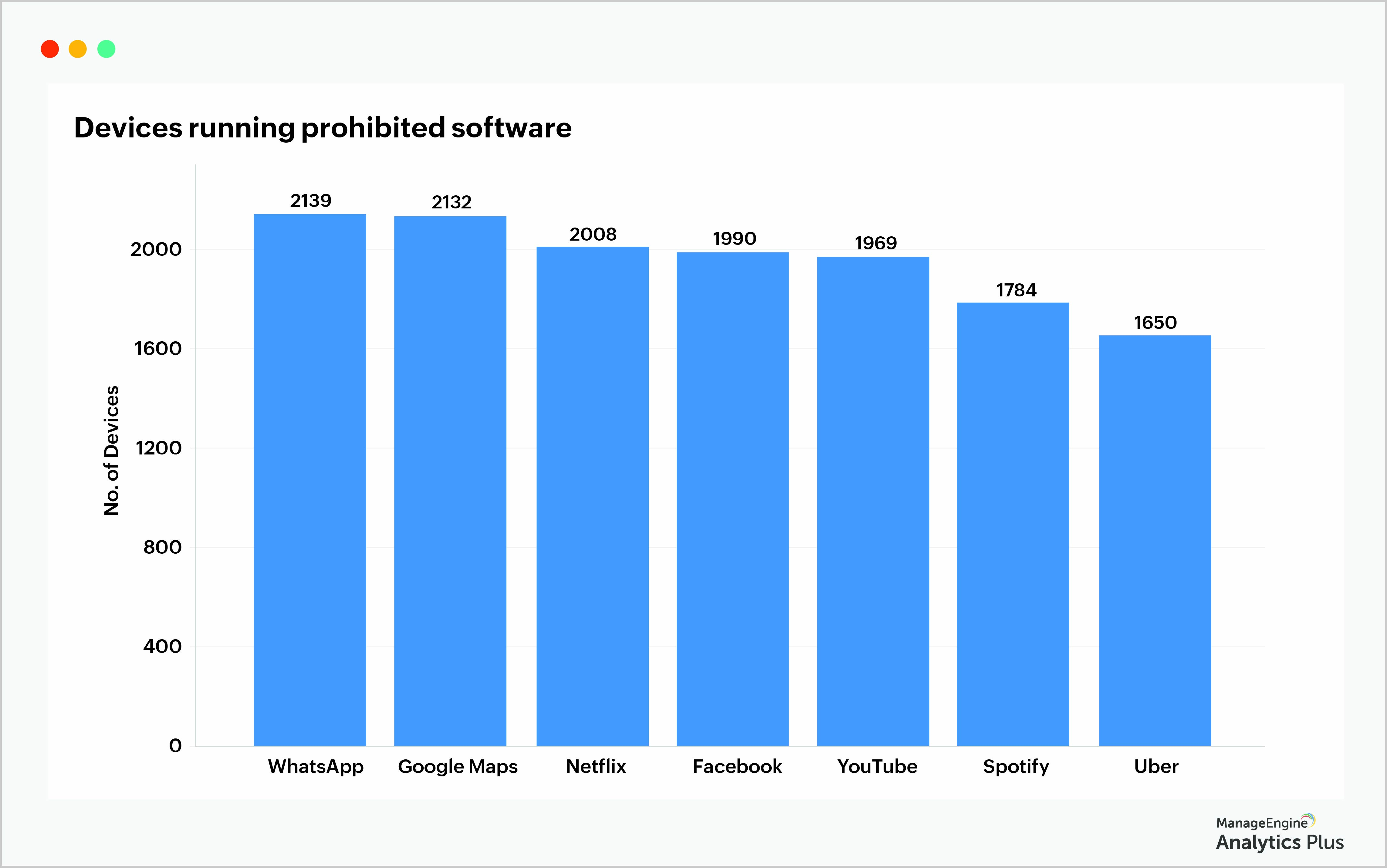
The above reports are generated using ManageEngine Analytics Plus, an AI-enabled analytics solution custom built for IT users.
Click here to explore more interesting reports and dashboards built using Analytics Plus.
Schedule a personalized demo of Analytics Plus today with one of our solution experts who can answer your product-related questions. Or try Analytics Plus for free to explore on your own this powerful business intelligence and IT analytics application.
 Sailakshmi
SailakshmiSailakshmi is an IT solutions expert at ManageEngine. Her focus is on understanding IT analytics and reporting requirements of organizations, and facilitating blended analytics programs to help clients gain intelligent business insights. She currently spearheads marketing activities for ManageEngine's advanced analytics platform, Analytics Plus.





